Abstract
The openness of wireless signal transmission enables seamless data transfer in wireless communications, but it also increases the risks of attacks, eavesdropping, and interference. In recent years, due to the randomness of physical layer channels, there is potential for it to replace traditional cryptographic encryption schemes that rely on extensive computation, and related research is actively ongoing. This article first introduces the basic theories related to wireless eavesdropping channels, information theory, and cryptography; secondly, it discusses Multiple Input Multiple Output (MIMO) technology and existing physical layer security optimization techniques, analyzing their limitations and challenges; finally, it presents the latest research progress in physical layer security for 5G/6G technologies in wireless communication networks.
The Necessity of Researching Physical Layer Security
According to estimates by the International Telecommunication Union, there were approximately 1.4 billion internet users worldwide by 2019. The security communication mechanisms based on traditional open interconnection models can no longer meet the current demands for user privacy protection, necessitating the urgent implementation of physical layer security technologies to achieve secure communication and protect private data. The robustness of the open interconnection network model relies on the principle that the computational power of attacking devices is limited, while the development of quantum computing poses a serious threat to this security mechanism. The broadcast nature of wireless communication networks also contributes to their vulnerability. Attacks on wireless communication networks can be classified into passive and active attacks. Passive attacks involve eavesdropping on transmitted data without interfering with the victim’s normal communication; active attacks disrupt normal communication through interference or intrusion, with common attack methods including denial of service attacks, routing, and node failure attacks. For the reasons of protecting user privacy and combating illegal attacks, ensuring the integrity, high reliability, confidentiality, authentication, and access control of physical layer networks has become essential.
Overview of Cryptography and Physical Layer Security
Cryptographic Security MechanismsTraditional cryptographic security mechanisms mainly include three methods: digital signatures based on hash operations, symmetric keys, and asymmetric keys. Hash encryption algorithms convert the target text into a fixed-length message digest without the need for any keys, representing a one-way encryption process primarily used for digital signatures to verify data integrity and prevent malicious tampering. Common hash encryption algorithms include MD5, SHA-1, SHA-2, etc. Symmetric encryption uses a symmetric key, with the same key used for both encryption and decryption. Common symmetric encryption algorithms include DES, 3DES, AES, etc. Asymmetric encryption involves different keys for encryption and decryption, using a public key for encryption and a private key for decryption, or signing with a private key and verifying with a public key. Common asymmetric encryption algorithms include RSA, DSA, ECC, etc. Traditional cryptographic encryption algorithms are based on the assumption that attackers have limited computational power, making decryption theoretically impossible; however, with the advancement of quantum computing, this encryption mechanism will eventually face challenges.Physical Layer Security MechanismsPhysical layer security mechanisms are based on Wyner’s information-theoretic security concept, achieving keyless secure communication through signaling and channel coding during wireless communication, effectively preventing unauthorized attackers from intercepting wireless transmission information through eavesdropping channels, thereby enhancing system reliability. When designing wireless secure transmission mechanisms, it is assumed that prior knowledge of the eavesdropping channel related to the attacker has been obtained; however, this is not always the case in practical applications, which necessitates that physical layer security be combined with upper-layer encryption algorithms to ensure the security of information transmission. With the development of technologies such as MIMO, IEEE802.11n, and LTE, physical layer security has gradually gained attention. Current research mainly focuses on enhancing security benefits by utilizing the spatial degrees of freedom of MIMO. Below is the threat model for physical layer security:
Figure 1 Physical Layer Security Threat Model
Alice: Transmitter; Bob: Legitimate Receiver; Eve: Eavesdropper
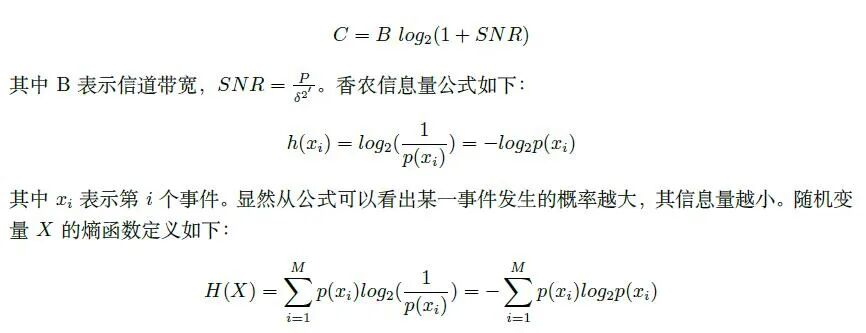
Information-Theoretic Security PrinciplesIn 1949, Shannon proposed the channel capacity model under additive Gaussian noise as follows:

To characterize the ability to transmit information without being intercepted by attackers and to reach legitimate receivers intact, Shannon modeled the eavesdropping channel as follows: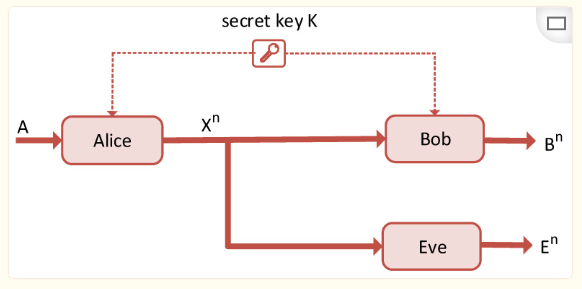

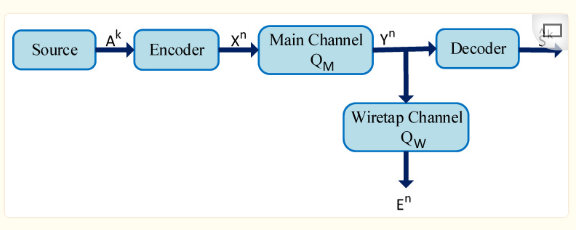
Figure 3 Wyner Eavesdropping Channel


Figure 4 Comparison of Wyner Eavesdropping Channel Transmission Rate and Eavesdropper Confusion Level
Performance Metrics for Physical Layer Security
To better evaluate the effectiveness of physical layer security mechanisms, many metrics have been proposed, such as Secrecy Rate (SR), Secrecy Outage Probability (SOP), Quality of Service (QoS)-Related Metrics, Channel State Information (CSI), and metrics in Multiple Input Multiple Output communications. Among these, CSI is a critical confidentiality metric that needs to be emphasized when designing optimal transmission strategies for physical layer security, describing the propagation of transmitted signals and their corresponding effects, such as scattering, fading, and power attenuation. CSI can be categorized into perfect CSI, which has complete knowledge of the communication link, and imperfect CSI, which only has statistical qualitative information (e.g., average channel gain, fading distribution type, line-of-sight, and spatial correlation, etc.). There are two methods for obtaining CSI information: one is pilot-based channel training, and the other is channel state feedback. The former involves the transmitter allocating time and energy for transmission, with part used for pilot symbol transmission and the other part for data transmission; the latter is based on feedback methods, sharing channel knowledge at the receiver before transmission, which can interfere with eavesdroppers using MIMO technology while minimizing leaked information.
Multi-Antenna Security Technologies
Multi-antenna technology can manipulate signals spatially, primarily applied in physical layer security in two ways: reducing the leakage of transmitted signals and enhancing the signal quality for legitimate receivers to improve security. Currently, there are four main technical approaches: beamforming, nulling, convex optimization, and artificial noise. They all utilize the principle of orthogonality to ensure that more high-quality signals are transmitted to the legitimate receiver Bob while leaking fewer signals to the eavesdropper Eve. Below are the principle diagrams of the four methods.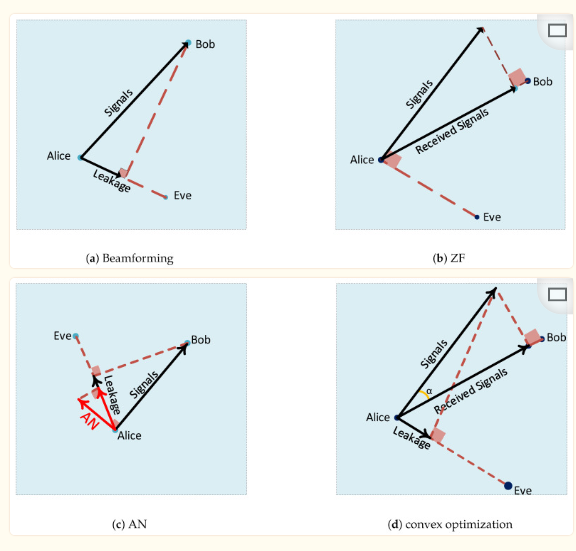
Figure 5 Secure Multi-Antenna Technology
BeamformingBeamforming, as the name suggests, controls the beam in a specified direction so that the legitimate receiver can receive a higher quality signal. Not only can the transmitting end use beamforming technology, but the receiving end can also use beamforming technology to find the desired signal direction to obtain the signal from a specified sender. Consider the following beamforming model: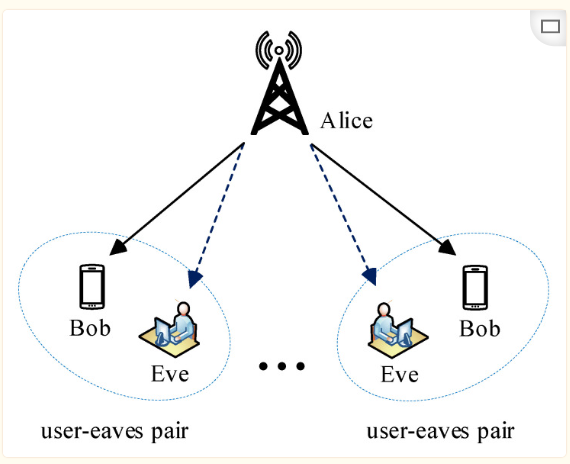
Figure 6 Multiple Input Single Output Eavesdropping Model
Beamforming problems typically involve maximizing the signal quality of the expected user, which is equivalent to minimizing the noise interference at the expected user under the condition that the SINR (Signal to Interference plus Noise Ratio) meets a certain threshold. This problem can be described in a multi-constraint quadratic optimization form as follows:
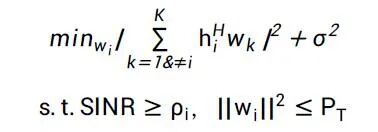
where h and g represent the channel vectors for the expected user and the eavesdropper, respectively, indicating the beamforming vector corresponding to the i-th legitimate user. The optimal solution is obtained under this optimization vector, where the expected user i receives the signal with the maximum signal-to-noise ratio. There are many explorations of beamforming technology applications in physical layer security.Artificial NoiseArtificial Noise (AN) technology actively interferes with eavesdroppers to reduce their channel communication quality, thereby enhancing the security level of physical layer communication. Under the premise of having prior knowledge of the eavesdropper’s CSI, noise is added to the eavesdropping channel based on beamforming technology to degrade its communication quality. The model for this method is shown in the following figure: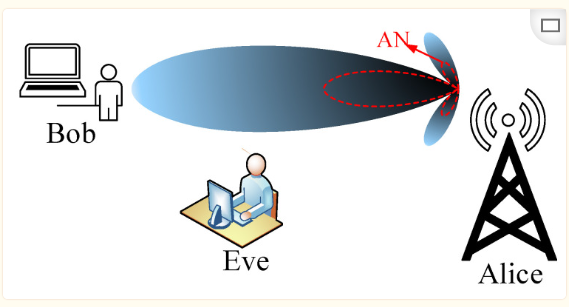
Figure 7 Confidential Beamforming with Artificial Noise
The optimization problem for the AN-based confidentiality scheme is to find an optimal power allocation method for artificial noise to ensure maximum confidentiality for legitimate transmission. Given that the AN method requires prior information about the eavesdropping channel, researchers in physical layer security are attempting to find methods to enhance information transmission security without obtaining CSI (Channel State Information).Cooperative InterferenceCooperative interference originates from cooperative relay technology, differing from cooperative relay enhancing the channel quality between the transmitter and receiver, as interference is sent to the eavesdropper to reduce the eavesdropper’s channel quality. The cooperative interference model is as follows [Wan20]: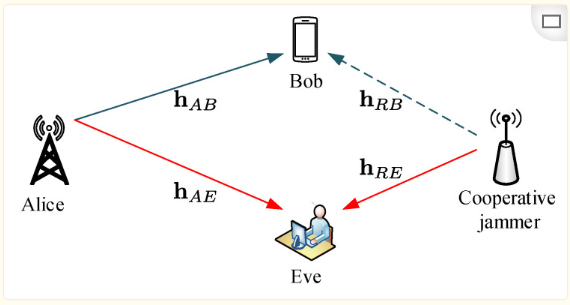
Figure 8 Cooperative Interference Model
Current research on cooperative interference in physical layer security mainly focuses on maximizing the secrecy rate of wireless communication systems with multiple coexisting eavesdroppers, downlink transmission issues, integrating it with 5G and 6G, and intelligently selecting the best cooperative nodes using edge computing devices.Space-Time CodingSpace-time coding is based on Alamouti’s space-time block code (STBC) proposed in 1998, achieving transmitter diversity by generating and applying maximum phase rotation operations to send symbols, thereby completely denying eavesdroppers access to the source information.
Challenges and Frontier Technologies in Physical Layer Security
Physical layer security is developing rapidly but faces various challenges, such as side lobe leakage issues in beamforming, eavesdroppers occupying advantageous channels, power consumption issues in AN and convex optimization algorithms, and security risks arising from the expansion of antenna scales used by eavesdroppers. Current frontier technologies that are expected to address the challenges faced by physical layer security mainly include Simultaneous Wireless Information and Power Transfer (SWIPT), machine learning-based channel estimation methods, Unmanned Aerial Vehicle (UAV) relays, Intelligent Reflecting Surfaces (IRS), Visible Light Communication (VLC), and satellite communication.
References
[1] Sanenga A, Mapunda GA, Jacob TML, Marata L, Basutli B, Chuma JM. An Overview of Key Technologies in Physical Layer Security. Entropy. 2020; 22(11):1261. https://doi.org/10.3390/e22111261
[2] L.; Wymeersch H.; Hoydis J.; Marzetta T.L. Björnson, E.; Sanguinetti. Massive MIMO is a reality-what is next? five promising research directions for antenna arrays. Digit.Signal Process., 2019.
[3] G.; Rusek F. Kapetanovi, D.; Zheng. Physical layer security for massive MIMO: An overview on passive eavesdropping and active attacks. IEEE Commun. Mag., 2015.
[4] K.; Liang T. Lu, W.; An. Robust beamforming design for sum secrecy rate maximization in multibeam satellite systems. IEEE Trans. Aerosp. Electron. Syst., 2019.
[5] H.D.; Sheng Z.; Tuan H.D.; Duong T.Q.; Vincent Poor H. Sheng, Z.; Tuan. Beamforming optimization for physical layer security in MISO wireless networks. IEEE Trans. Signal Process., 2018.
[6] F.; Hu R.Q.; Qian Y. Wang, Q.; Zhou. Energy-efficient beamforming and cooperative jamming in IRS-assisted MISO networks. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), 2020.
[7] M.; Yu H.; Luo H.; Chen W.; Member S. Zhao, P.; Zhang. Robust beamforming design for sum secrecy rate optimization in MU-MISO networks. IEEE Trans. Inf. Forensics Secur., 2015.
[8] E.; Member S.; Matthaiou M.; Wing Kwan Ng D.; Yang H.; Love D.J.; Zhang J.; Björnson E.; Matthaiou M.; et al. Zhang, J.; Björnson. Prospective multiple antenna technologies for beyond 5G. IEEE J. Select. Areas Commun., 2020.
China Confidentiality Association
Science and Technology Branch
Long press to scan the code to follow us

Author: Wang Kui, Institute of Information Engineering, Chinese Academy of Sciences
Editor: Hao Luming
Top 5 Exciting Articles of 2022 Review
Cross-Network Attacks: An Introduction to Techniques for Breaking Physical Isolation Network Attacks
Thoughts on the Top-Level Design of Smart City SecurityRevisiting Some New Issues Faced by Digital Forensics Technology DevelopmentThe Development and Challenges of Low Earth Orbit Satellite Interconnection Networks
Introduction to LaserShark Non-Contact Attack Implant Technology
Recent Exciting Article Reviews
Edge Computing in 5G
Common Security Threats in Wireless Networks
A Brief Discussion on Web Crawler Technology
Application Research on Intercepting Web Crawler Traffic Technology
Overview of Trust in the Semantic Web