Application Background
In practical scenarios, we often need to collect subdomains of target sites, usually using tools like subdomain excavators, oneforall, etc., or space search engines like fofa, shodan, and eagle map, or Google syntax. Besides the conventional methods, we can also utilize the Linux text processing tools we learned earlier to collect subdomains.
Steps
Identify Target Site
There is a publicly available web site on the internet:<span>www.megacorpone.com</span>
Get index.html
wget www.megacorpone.com
Get Subdomains
We have obtained the index.html file. Based on our knowledge of HTML (HyperText Markup Language), web page links are usually found in the <span><a></span> tag’s href attribute.
grep "href=" index.html
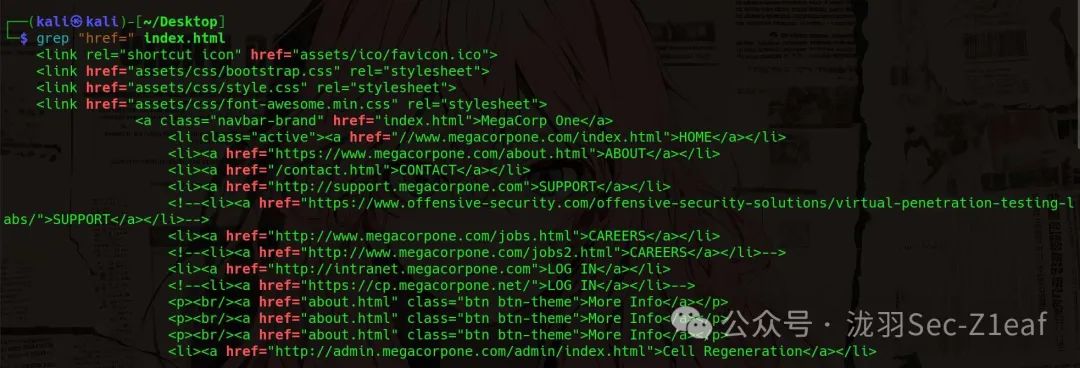
Then we find out that the main domain is <span>www.megacorpone.com</span>, and we will filter the links to find those containing <span>megacorpone</span>.
grep "href=" index.html | grep "\.megacorpone"
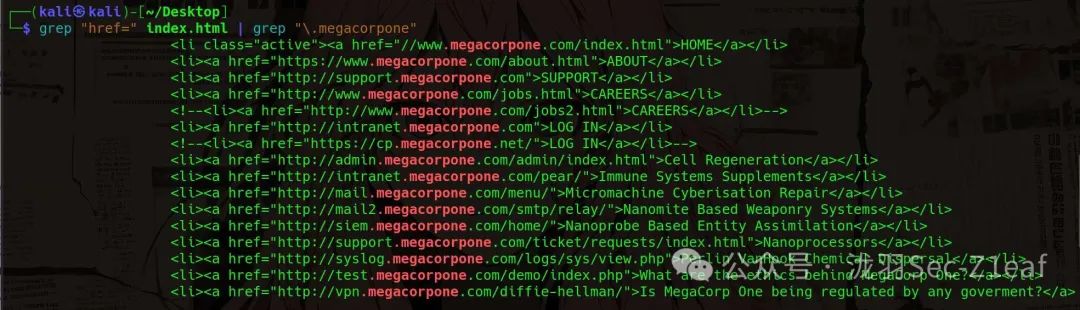
Since we need subdomains, we will filter out <span>www.megacorpon.com</span>
grep "href=" index.html | grep "\.megacorpone"|grep -v "www.\megacorpone\.com"
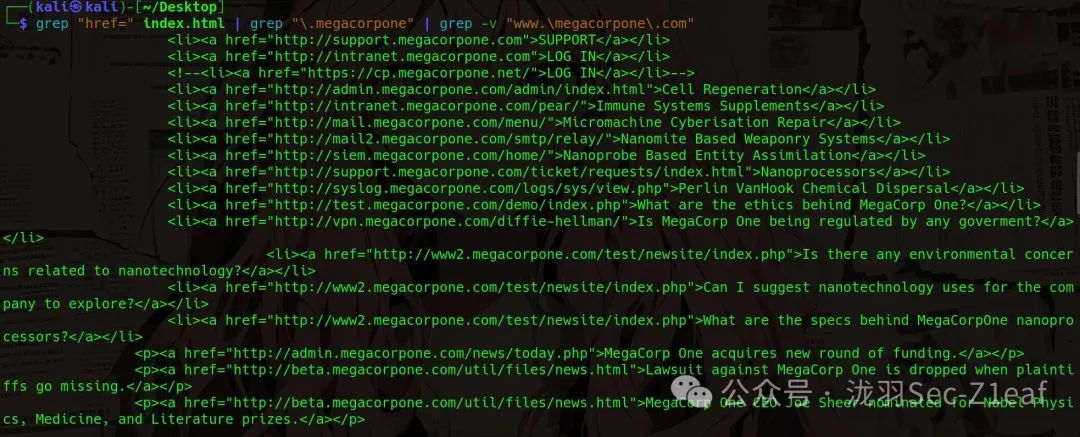
Next, we use <span>awk</span> to take the subdomain part after the <span>http(s)://</span> separator, which is <span>//</span>.
grep "href=" index.html | grep "\.megacorpone" | grep -v "www.\megacorpone\.com" | awk -F "//" '{print $2}'
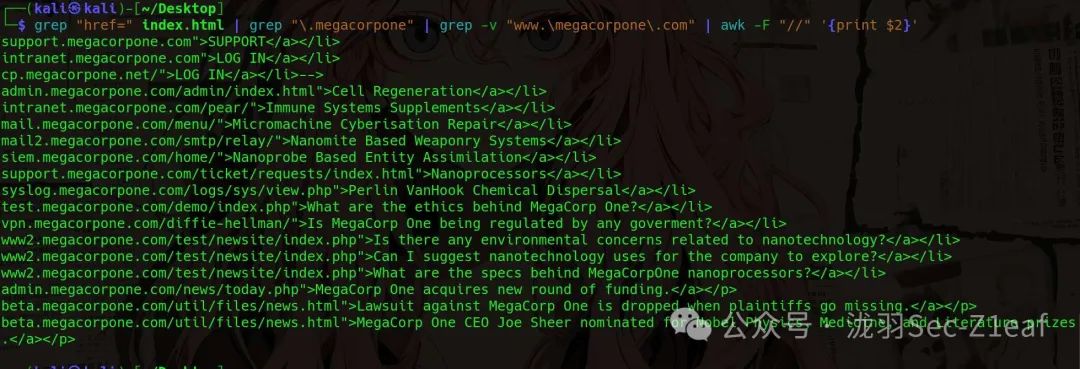
Finally, we use <span>cut</span> to remove the file paths after the subdomains.
grep "href=" index.html | grep "\.megacorpone" | grep -v "www.\megacorpone\.com" | awk -F "//" '{print $2}' | cut -d "/" -f 1 |cut -d '"' -f 1
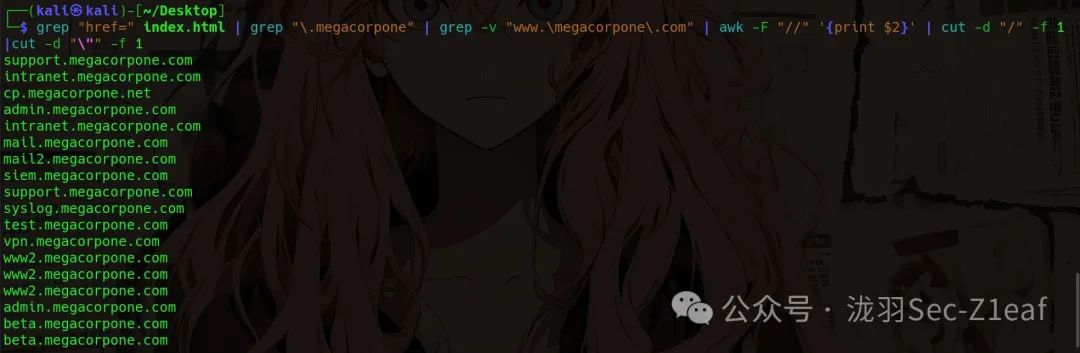
In this way, we can obtain the subdomains related to <span>www.megacorpone.com</span>.
Pros and Cons
This method allows for quick searching of subdomains, faster and more efficient than traditional subdomain search tools. However, the subdomains found using this method may not be as comprehensive as those collected by dedicated subdomain collection tools, and there is a significant chance of missing some subdomains.
Learning Sharing
FreeBuf Knowledge Community
We welcome all network security enthusiasts to join our community. It is created by real red team experts, and we regularly share tools not found online (such as Android remote control 7.4, which has now been removed, with a time limit, so make sure to check the time after joining). Currently, it is only 99 for a lifetime membership, and prices will increase as more people join.
Among the resources, there are numerous e-books on network security, and various paid network security learning materials and computer exam preparation materials collected by community members.
There are also a large number of the latest publicly available and internally organized 5000+ POC collections, high-quality penetration testing tools.

Join our community for more exciting content and quality tools.
OSCP+ Training
While you are still hesitating whether to sign up for OSCP, others have already taken action. After completing the OSCP training and Longyu Sec’s red team full-stack course, others are already earning over ten thousand a month while you are still worrying about lack of skills and job opportunities. So why not take action? If you want to sign up for OSCP, feel free to consult me. The OSCP course offers amazing benefits:
1. Sign up for OSCP training once and enjoy unlimited free learning for the next sessions until you are ready to take the OSCP exam.
2. Students looking for jobs or wanting to switch jobs can get recommendations after completing OSCP, or secure targets from Brother Long to ensure you are on the red team.
3. The 4000 fee can be paid in installments, with no interest, and students get a 500 discount.
4. Teacher Long provides live explanations of the OSCP official course, along with practical training on over 100 target machines.
Price is affordable, and the course is of high quality, only one of its kind.

Learning Group
A learning group has been created! We welcome all network space security enthusiasts to join us. If you encounter difficulties in your studies, the experts in the group will help you. Let’s communicate, learn from each other, and progress together.
The group link is on the public account homepage. If the link expires, please notify the author in the background, and I will update it promptly.