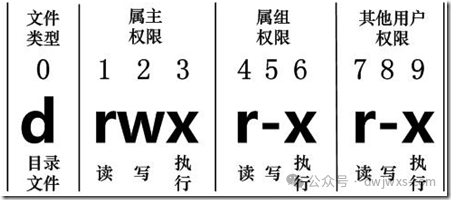
1. The “Genetic Code” of File Permissions
1. File Type Identifiers
| First Character | File Type | Typical Examples |
d |
Directory | /home, /var/log |
- |
Regular File | index.html, app.py |
l |
Symbolic Link | /usr/bin/python3 → python3.9 |
b/c |
Block Device/Character Device File | /dev/sda (disk), /dev/ttyS0 (serial port) |
2. Structure of Permission Triplets
The permissions for each user type are composed of three characters rwx, corresponding to Read (4), Write (2), Execute (1):
-
• Owner: Positions 1-3
-
• Group: Positions 4-6
-
• Others: Positions 7-9
Example Analysis:
-rwxr-xr-- 1 root dev 4096 Aug 10 config.ini -
• Permission Breakdown:
-
• Owner (root):
rwx→ 7 (4+2+1) -
• Group (dev):
r-x→ 5 (4+0+1) -
• Others:
r--→ 4 (4+0+0) -
• Numeric Representation:
754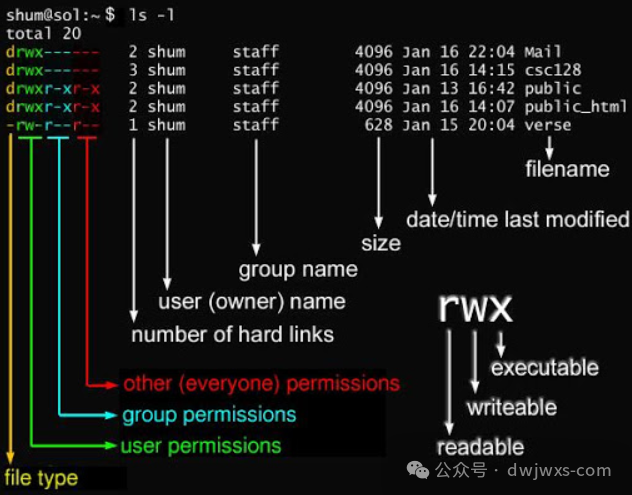
2. The Three Keys to Permission Control
1. chgrp: Change File Group Ownership
chgrp -R dev-team project/ # Recursively change the group of all files in the project directory to dev-team -
• Core Parameter:
-R(recursive operation, applicable to directories)
2. chown: Change File Owner and Group
chown alice:developers app.py # Change the owner of app.py to alice and the group to developers -
• Quick Operations:
-
• Change only the owner:
chown alice app.py -
• Change only the group:
chown :developers app.py
3. chmod: Fine-grained Permission Management
Numeric Mode (Recommended)
chmod 760 startup.sh # Owner: rwx, Group: rw-, Others: no permissions -
• Permission Quick Reference Table:
| Permission | Numeric Value | Combination Example |
| rwx | 7 (4+2+1) | Owner can read, write, execute |
| rw- | 6 (4+2+0) | Group can read, write, not execute |
| r-x | 5 (4+0+1) | Others can read, execute |
Symbolic Mode (Flexible Adjustment)
chmod u+x,go-w script.sh # Add execute permission for owner, remove write permission for group and others -
• Operator Details:
| Symbol | Target | Operation | Permission |
u |
Owner (User) | + (add) |
r, w, x |
g |
Group | - (remove) |
r, w, x |
o |
Others | = (set exactly) |
r, w, x |
a |
All | Combined use | r, w, x |
3. Practical Scenarios: Classic Cases of Permission Management
Scenario 1: Protecting Sensitive Configuration Files
-
• Goal: Prevent non-administrators from modifying
/etc/nginx/nginx.conf -
• Operation:
chown root:root /etc/nginx/nginx.conf # Ensure owner and group are root chmod 644 /etc/nginx/nginx.conf # Permissions: Owner can read and write, others read only
Scenario 2: Shared Development Directory
-
• Goal: Team collaboration on
/data/project, prevent external access -
• Operation:
chown -R lead:dev-team /data/project # Recursively set owner and group chmod -R 770 /data/project # Owner and group can read, write, execute, others no permissions
Scenario 3: Secure Script Execution
-
• Goal: Only allow the owner to execute
backup.sh -
• Operation:
chmod 744 backup.sh # Permissions: Owner can read, write, execute, others read only
4. “Forbidden Zones” of Permission Management and Cracking Techniques
1. Privileges of the Root User
-
• Rule: The root user is not restricted by file permissions (can read and write any file).
-
• Risk Warning: Misoperations may lead to system crashes, use
sudowith caution!
2. SUID/SGID Special Permissions
-
• SUID: The user inherits the owner’s permissions when executing the file (e.g.,
/usr/bin/passwd). -
• SGID: New files in the directory inherit the group (used for team collaboration).
-
• Setting Method:
chmod u+s /usr/bin/script # Add SUID bit chmod g+s /shared_dir # Add SGID bit
3. Sticky Bit
-
• Function: Restricts file deletion in the directory to only the owner (e.g.,
/tmp). -
• Setting Method:
chmod +t /public_upload # Add sticky bit
Permission Self-check Tools:
# View detailed file attributes
stat filename
# Check directory permission conflicts
namei -l /path/to/directory