Gift to Readers

Conducting research involves a profound system of thought, requiring researchers to be logical, meticulous, and earnest. However, effort alone is not enough; often leveraging resources is more important than sheer effort. Additionally, one must have innovative and inspirational points of view. I suggest readers browse through the content in order to avoid suddenly falling into a dark maze without finding their way back. This article may not reveal all the answers to your questions, but if it can clarify some of the doubts rising in your mind, it may create a beautiful sunset of colors. If it brings you a storm in your spiritual world, then take the opportunity to brush off the dust that has settled on your “lying flat” state.
Perhaps, after the rain, the sky will be clearer…


01
Overview




[Image Encryption] Using SIT for Image Encryption: A Study of a Lightweight Encryption Algorithm for Secure IoT
The Internet of Things (IoT) is a promising technology for the future, expected to connect billions of devices. The increase in communication is anticipated to generate a vast amount of data, and the security of this data may pose a threat. Devices in this architecture are generally small in size and have low power consumption. Traditional encryption algorithms are often computationally expensive due to their complexity and require multiple rounds of encryption, which essentially wastes the limited energy of small devices. However, less complex algorithms may compromise the required integrity. In this paper, we propose a lightweight encryption algorithm called Secure IoT (SIT). It is a 64-bit block cipher that requires a 64-bit key to encrypt data. The architecture of the algorithm is a hybrid of Feistel and uniform substitution-permutation networks. Simulation results show that the algorithm provides substantial security within five rounds of encryption. The hardware implementation of the algorithm was completed on a low-cost 8-bit microcontroller, and the results of code size, memory utilization, and encryption/decryption execution cycles were compared with benchmark encryption algorithms.
1. Introduction
The Internet of Things (IoT) is a highly promising technology for the future, expected to connect billions of devices and achieve a fully interconnected world. However, with the increase in communication, the generation and transmission of large amounts of data make data security a significant challenge. IoT devices are typically small in size and have low power consumption, which limits their ability to handle complex encryption algorithms. Traditional encryption algorithms, due to their high complexity and the need for multiple rounds of encryption, often incur high computational costs, which is undoubtedly a waste of energy for resource-limited IoT devices. Therefore, developing a lightweight encryption algorithm that is both secure and efficient is crucial for IoT security.
2. Research Background
The limitations of IoT devices in terms of size, power consumption, and computational capability make it difficult to directly apply traditional encryption algorithms. These algorithms typically require significant computational resources and high energy consumption, making them unsuitable for operation on IoT devices. At the same time, overly simplistic encryption algorithms may not provide sufficient security to meet the data protection needs of IoT. Therefore, there is a need for a lightweight encryption algorithm that can ensure data security while adapting to the constraints of IoT devices.
3. SIT Lightweight Encryption Algorithm
In response to the characteristics of IoT devices, we propose a lightweight encryption algorithm called Secure IoT (SIT). This algorithm is a 64-bit block cipher that uses a 64-bit key for encryption. Its architecture combines the features of Feistel structure and uniform substitution-permutation networks, ensuring both the security of the algorithm and reducing computational complexity.
Algorithm Architecture: The SIT algorithm combines the characteristics of Feistel structure and uniform substitution-permutation networks, achieving data confusion and diffusion through multiple rounds of encryption operations, thereby enhancing the security of the algorithm.
Encryption Rounds: Simulation results indicate that the SIT algorithm provides substantial security within five rounds of encryption. This ensures the security of the algorithm while reducing computational costs, making it suitable for operation on IoT devices.
Key Management: The use of a 64-bit key gives the SIT algorithm a high key space, enhancing the security of the algorithm. Additionally, key generation, distribution, and management are also important components of the algorithm’s security.
4. Hardware Implementation and Performance Evaluation
To verify the practical application of the SIT algorithm, we implemented it on a low-cost 8-bit microcontroller. By comparing metrics such as code size, memory utilization, and encryption/decryption execution cycles, we evaluated the performance of the SIT algorithm.
Code Size: The code size of the SIT algorithm is moderate, not occupying excessive storage space, making it suitable for operation on resource-limited IoT devices.
Memory Utilization: The algorithm performs excellently in memory utilization, making full use of limited memory resources to enhance the operational efficiency of the device.
Encryption/Decryption Execution Cycles: The encryption and decryption operations of the SIT algorithm can be completed within a short cycle, meeting the real-time requirements of IoT devices.
5. Conclusion
This paper presents a lightweight encryption algorithm for IoT devices—the SIT algorithm. This algorithm combines the characteristics of Feistel structure and uniform substitution-permutation networks, featuring low computational complexity and high security. Through hardware implementation and performance evaluation, we have verified the feasibility and effectiveness of the SIT algorithm on IoT devices. In the future, we will continue to optimize the algorithm’s performance and enhance its security to provide more reliable protection for IoT security.





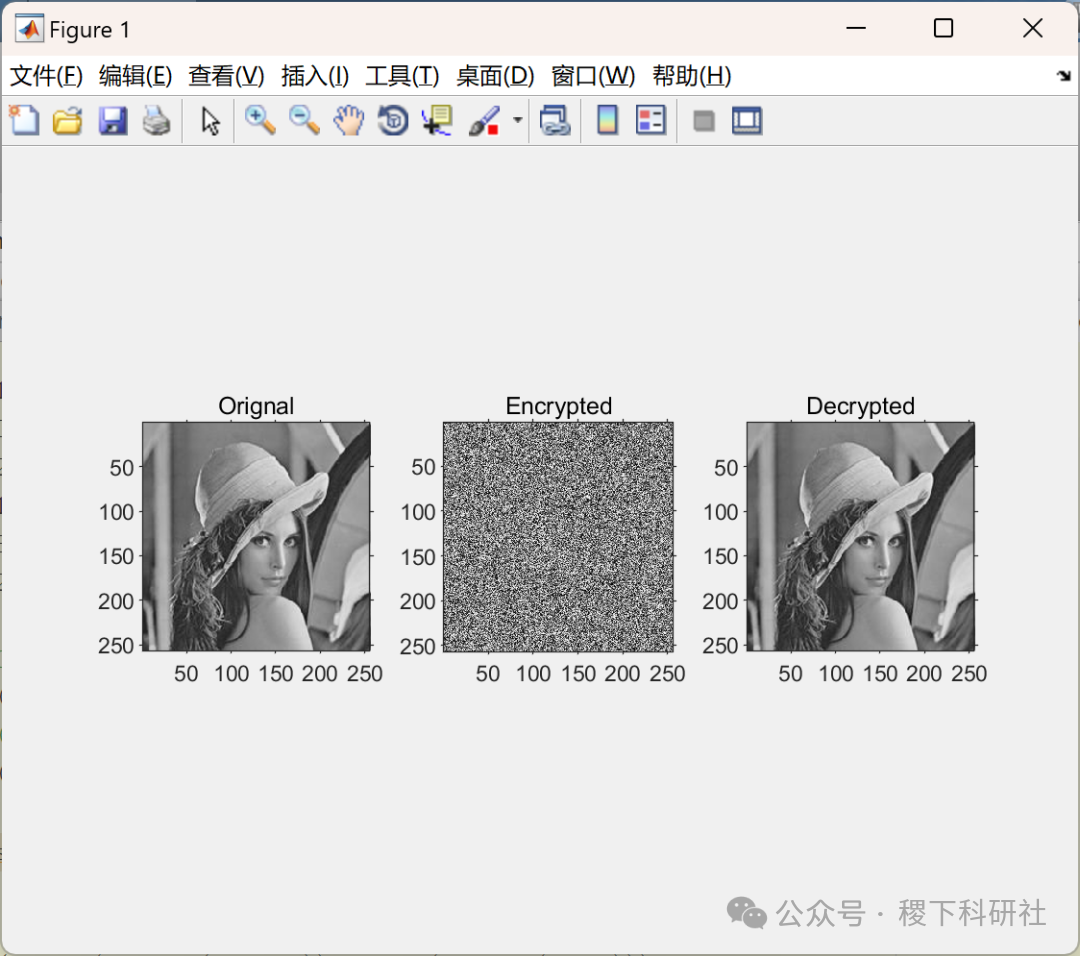
02

Running Results

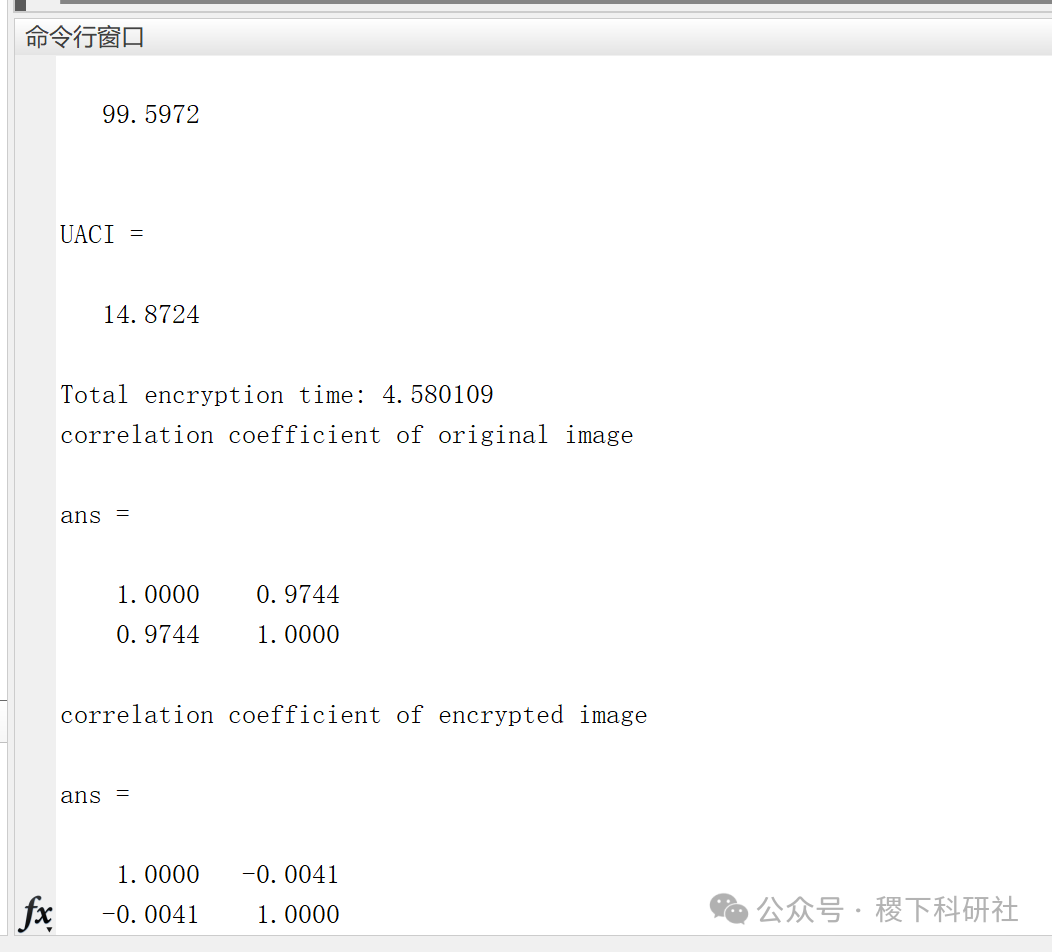



03

Partial Code


Partial Code:
% %% Results% 5 Orignal ImageOrignal=uint8(reshape(Data,[row,col]));% 6 Encrypted ImageEncrypted=uint8(reshape(encrypt_msg,[row,col]));% 7(Wrong Key Decyption(Key Sensitivity))
Decrypted=uint8(reshape(decrypt_msg,[row,col]));% %% 567figure
subplot(1,3,1)
imshow(Orignal)
title('Orignal')
subplot(1,3,2)
imshow(Encrypted)
title('Encrypted')
subplot(1,3,3)
imshow(Decrypted)
title('Decrypted')
%
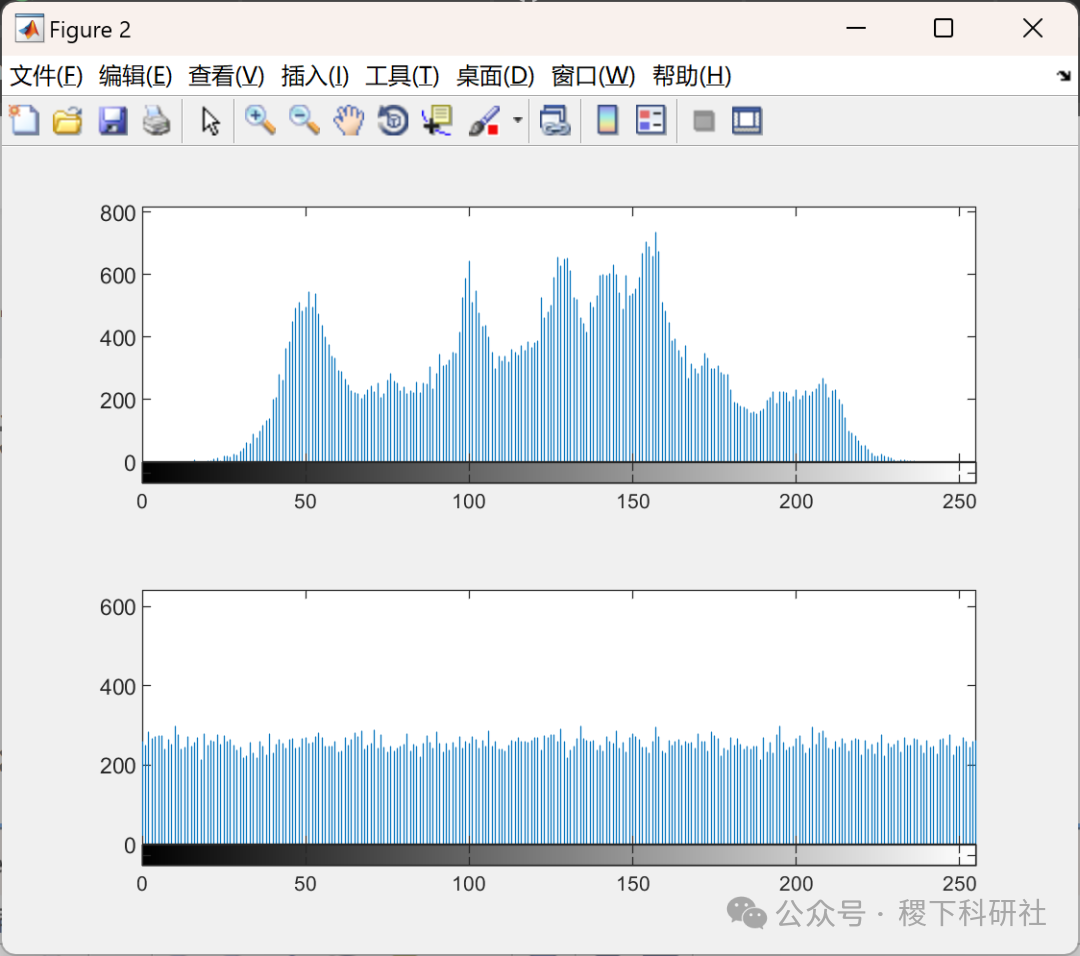
% 8 Histogram
figure
subplot(2,1,1)
imhist(Orignal);subplot(2,1,2)imhist(Encrypted);% 14 Image EntropyY=(imhist(Encrypted)+0.00001)/(row*col);%(length(Data)-padding);Y=-sum(Y.*log2(Y));X=(imhist(Orignal)+0.00001)/(row*col);%(length(Data)-padding);X=-sum(X.*log2(X));Re=[X Y]% % 9Correlation
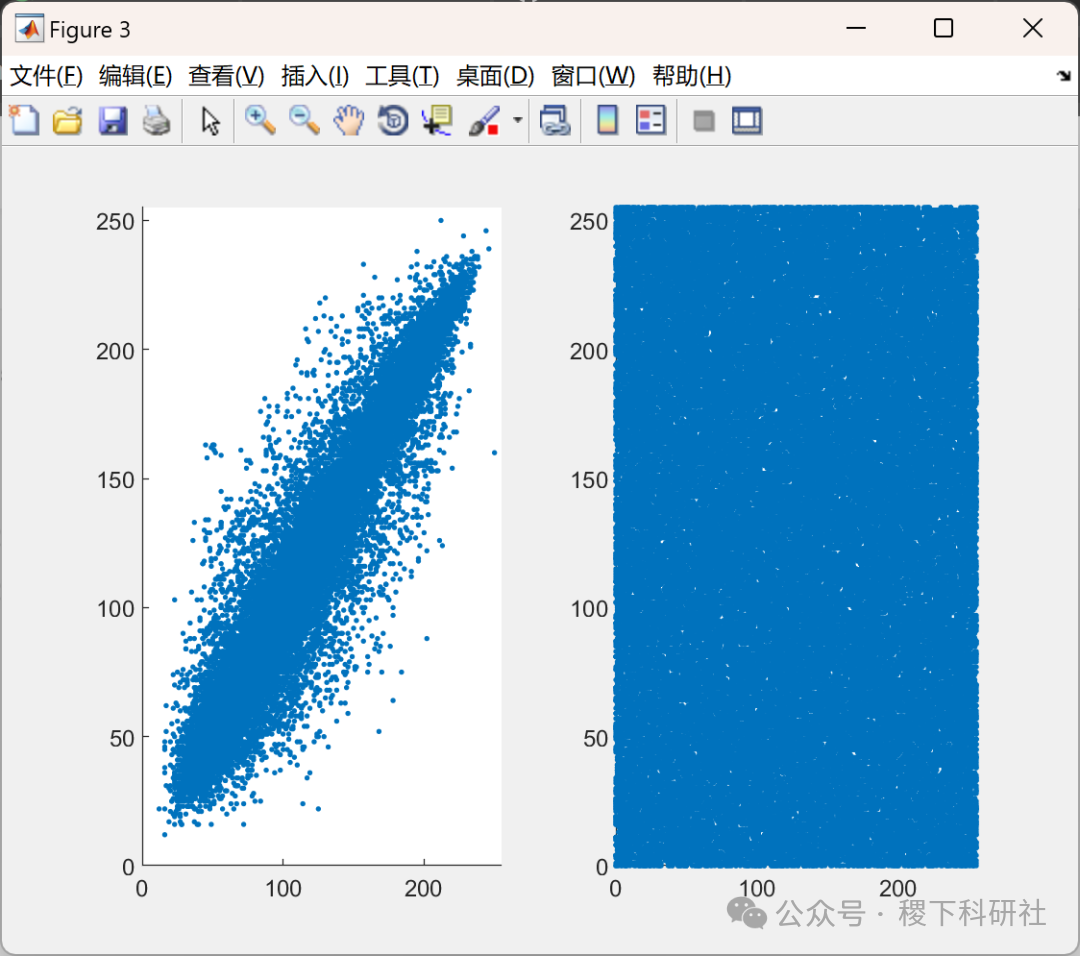
figure
subplot(1,2,1)
scatter(Orignal(1:end-1),Orignal(2:end),'.')
axis([02550255])
subplot(1,2,2)
scatter(Encrypted(1:end-1),Encrypted(2:end),'.')
axis([02550255])
%
% % 1 NPCR(%)
NPCR=sum(sum(Encrypted~=Orignal))*100/(row*col)% 2 UACI(%) UACI=sum(sum(abs(Encrypted-Orignal)))*100/(row*col*255)display(sprintf('Total encryption time: %f',sum(encryption_time)))

04

References


Some content in this article is sourced from the internet, and references will be noted. If there are any inaccuracies, please feel free to contact us for removal.
[1] Yu, Chenyun. Research on JPEG2000 Digital Image Encryption Algorithm Based on Compressed Coding [D]. Chongqing University, 2014.
[2] Yang, Kang. Design and Implementation of Image Encryption Algorithm Based on Chaotic System [D]. Henan University [2024-11-12]. DOI: CNKI:CDMD:2.1016.201909.
[3] Wu, Fan. Image Encryption Algorithm Based on Multi-Vortex Memristor Chaotic System [D]. Southwest University, 2023.





05

Download Matlab Code
