Catastrophic incidents may result from insecure industrial control systems. Enhancing cybersecurity across the entire system can be achieved through four steps.
Despite the fact that cybersecurity has always been a major concern for any industry, it is commonly believed that attacks only lead to loss of proprietary data, becoming victims of espionage, and facing threats of downtime. However, the 2017 Triton (also known as Trisis or HatMan) attack revealed a severe aspect of attacks: the potential for catastrophic incidents. Let’s explore common attack types, prevention measures, and improvement methods.
Traditionally, industrial control systems (ICS) were designed to operate independently on isolated control networks, with few anticipating the threats posed by cybersecurity. However, with the development of other technologies in the industrial sector—including smart sensors, wireless gateways, remote management systems, virtualization, cloud computing, smartphones, and various business intelligence demands—the likelihood of these industrial systems remaining unaffected by external interference is diminishing.
The first instance of external attacks on industrial control systems occurred in 2010 with the Stuxnet, a script designed to disrupt the scripts running on centrifuge controllers. This was followed by the 2013 Havex attack, which targeted the power grid and electric companies, collecting vast amounts of data for espionage and sabotage activities.
In 2015, two threats emerged: BlackEnergy compromised data and files on workstations, causing severe power outages in Ukraine, while IronGate was discovered on public resources with similar functionalities to Stuxnet. In 2016, Industroyer caused significant damage in Ukraine, where malware erased data and conducted distributed denial-of-service (DDoS) attacks, leading to the shutdown of the Ukrainian power grid.
The Triton attack was discovered in 2017. Its detection may have averted a serious disaster. This malware could infect Triconex safety controllers, allowing hackers to alter safety parameters. Malicious attacks could lead to the failure of safety settings for industrial equipment, potentially resulting in catastrophic events similar to chemical plant explosions.
Understanding Attack Sources
To address cybersecurity threats, the first step is to understand where attackers may originate, as they typically use reconnaissance as the first step to assess and understand target vulnerabilities over a specific period. In the long term, companies may use attack vector analysis to identify different methods that attackers might employ or systems they may prefer. All of this must be based on the risk identified in the business impact analysis of the company’s assets. Users can utilize some ready-made assessment tools to distinguish and rationalize critical assets from non-critical ones and then conduct gap assessments.
Common Entry Points for Attackers Include:
· Inbound attacks from external networks, the Internet, and remote connections through enterprise resource planning (ERP) software, gateways, data and document repositories, and online historical databases;
· Incorrectly configured firewalls and gateways;
· Users accessing business workstations and control computers through stolen or forged credentials;
· Physical attacks on production systems, which in most cases target human-machine interfaces (HMI), engineer and operator workstations, and actual process safety controllers;
· Lateral network attacks targeting control networks using industrial communication protocols to discover other devices on the network and propagate malicious code;
· Social engineering attacks, which focus on using personal identity information to deceive insiders into granting access, inadvertently opening gateways, and running scripts.
Cybersecurity Prevention Measures
Each type of attack has its own prevention measures, which can generally be categorized into the following eight types.
01
Isolation and Segmentation:
Utilizing tools and qualified personnel to conduct thorough gap assessments on control networks can often reveal many unmonitored access points, which are frequently overlooked when following standard practices to protect control networks. These threats may arise from:
· Unrestricted access to engineering/operator workstations;
· Outdated malware detection;
· Third-party applications and connectors that have not been protected or audited;
· Lack of demilitarized zones (DMZ) or data isolation when exporting data from control networks;
· Critical assets connected to public areas.
02
Managing User Access Control:
This task involves taking measures to limit unauthorized access and tracking and stopping any activities related to unauthorized access. This includes:
· Strengthening the difficulty for unauthorized personnel to gain access;
· Establishing management policies and strictly updating them as planned;
· Enabling multi-factor authentication across the enterprise;
· Whitelisting, adding pre-approved addresses, locations, and port-based alerts to identify personnel accessing the system;
· Changing all passwords and default passwords, and regularly updating user passwords.
03
Patch Frequency:
All control and security devices must be regularly updated to the latest firmware versions. While routine non-intrusive patching is a method that all critical controllers should adopt, patching should occur at least during each annual maintenance cycle.
04
Running Validation Checks:
Through programs, logic, and executable validation checks, ensure that changes to logic, code, and scripts are intentional changes made by authorized personnel. Simulated validation environments can help operators train on devices without risking the actual physical systems and can also monitor any unnecessary changes to logic and parameters. Tools can be used to automatically detect any changes at the logic level, and any such changes can be executed in a controlled environment while keeping backup copies for recovery in case the controller or system is threatened.
05
Increasing Physical Security:
In light of recent cybersecurity threats, some control system vendors now configure physical locks on their controllers to prevent any other code from being executed on the controllers without first going through the physical security layer.
06
Cybersecurity Training:
A critical part of cybersecurity threats comes from attackers, who often rely on errors made by factory personnel. Without all stakeholders in place and aware of their responsibilities, cybersecurity measures cannot be effectively implemented. This includes training personnel on how to recognize attacks, how to protect their personal identity information, and how to safeguard themselves against attacks. This training should be provided to all levels of management, executives, operational technology (OT) system administrators, and users.
07
Creating an Incident Response Plan:
Occasionally, a strange error or oversight may open the door to potential attackers; cybersecurity implementation work needs to include a viable plan for personnel to use when security is compromised or threats are detected. Once these plans are developed, they need to be practiced through regular training and provided to all responsible personnel to ensure quick action when a security incident occurs.
08
Continuously Updated Asset Registry
To reduce risks, maintain an up-to-date record of all listed operational technology assets, including switches, routers, firewalls, various web services, SCADA software, historical database servers, controllers, or any Internet Protocol (IP)-addressable devices, all of which could provide attackers with opportunities to exploit unmanaged systems. Network monitoring can be used to obtain the latest version of the asset registry, while various tools can monitor patches and any vulnerabilities.
Four Steps to Enhance Cybersecurity
Initiating a cybersecurity program for industrial systems is not as daunting a task or requires as much investment as it may initially seem. When weighing the potential damages that might occur, it becomes absurd for companies not to invest in cybersecurity.
Like any successful enterprise-wide initiative, cybersecurity also requires internal advocates to maintain its cause and help the organization adopt necessary policies and procedures. In most cases, the best approach is to define ownership of cybersecurity for the business network and control it.
Cybersecurity must be an initiative across the entire plant. It can be achieved through four phases (as shown in Figure 1):
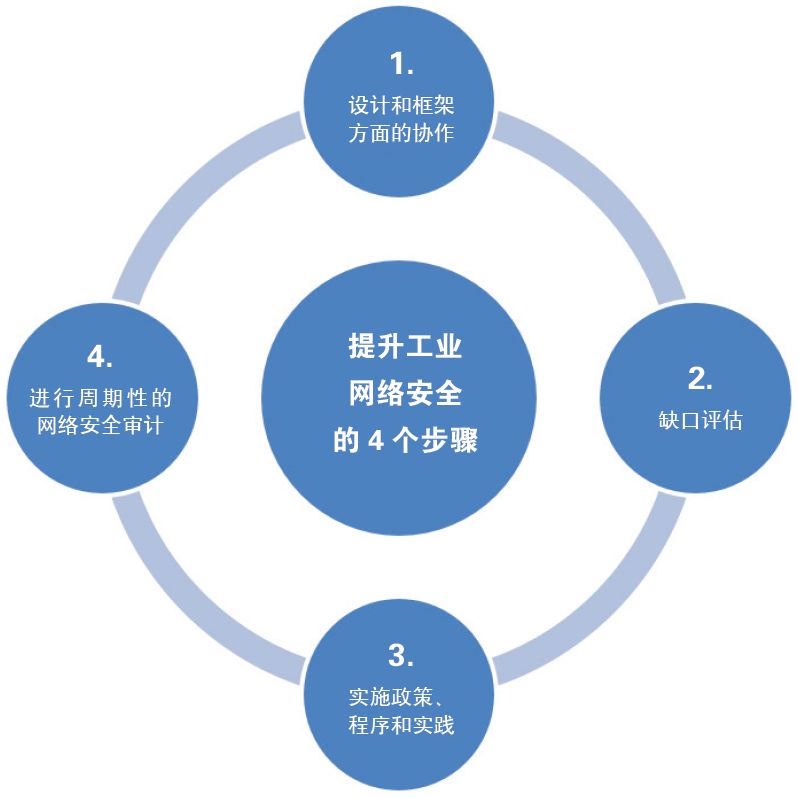
Figure 1: Industrial cybersecurity needs to become a plant-wide initiative, involving collaboration in design and framework, gap assessments, implementation, and auditing. Image source: Intech Process Automation
Phase 1: Design and Framework
Designing a cybersecurity management system is the most comprehensive phase, requiring the most time and effort. Many cybersecurity consulting firms are dedicated to helping companies design cybersecurity infrastructure, policies, and procedures. This task involves identifying all systems and personnel related to cybersecurity, defining their roles, defining their access and control permissions, and developing policies around these parameters to ensure safe operations. The design phase requires significant internal push and support from stakeholders to ensure its successful completion.
Phase 2: Gap Assessment
The assessment phase primarily involves reviewing the cybersecurity design and identifying potential vulnerabilities and risks based on business impact. Address and update identified gaps in the design. Experienced personnel and various tools can be utilized for the assessment, which can sniff network-level data packets and identify anomalies and vulnerabilities in the system.
Phase 3: Implementation
This part encompasses the implementation of cybersecurity policies, procedures, and practices. During this phase, external assistance is often helpful in expediting the implementation process and ensuring checklist compliance. The key method for implementation is system hardening.
Phase 4: Auditing
Auditing cybersecurity involves tasks such as comprehensive penetration testing to ensure that the cybersecurity implementation achieves the intended results. Professional auditing firms typically handle this work and help ensure reliable cybersecurity. For new implementation plans, this part requires the most external expertise. However, if an internal cybersecurity audit team is trained at all stages, that team can leverage its learning and expertise to audit other plants and facilities within the company.
This article is from the October 2019 issue of CONTROL ENGINEERING China, under the “Cover Story” section, originally titled: Improving Cybersecurity for Industrial Control Systems
Recommended Reading

In-Situ Calibration — The Best Method for Temperature Sensor Calibration

The Raspberry Pi Has Entered the Industrial Control Field — Raspberry Pi Industrial Control Machines Assist Renault in Connecting to Smart Grids
In-Depth Analysis: Cybersecurity of Safety Instrumented Systems (SIS)

Honeywell Showcases Next-Generation Process Control Technology: Continuous Innovation Leading the Evolution of Process Industry Automation

Case Study: Empowering Intelligent Factories — Application of APROL Factory Automation Solutions

Breaking News!
We invite you to join the Industrial Automation Circle
Starting in 2020, to enhance communication between editors and readers, and among readers, we will establish various WeChat groups for professional readers focusing on industrial automation technology.
Currently, we plan to establish the following technical category groups:

Industrial Network Group

PLC Group

DCS Group

Machine Vision Group

Robot Group

Industrial Software Group

Human-Machine Interface Group

Motion Control Group

Sensor Group

Industrial Safety Group

Instrumentation Group

AI/AR Group

Scan the QR code on the right
Send “Name + Technical Interest + City”
Add the editor’s WeChat, and after review, you will be invited to join the corresponding technical group.


