★ Zhang Yabin, Zhang Xin, Wang Linkun, Liu Yao, Institute of Comprehensive Technology and Economic Research of Mechanical Industry Instruments
★ Sun Tieliang, Huang He, Lü Feng, Oil and Gas Regulation Center of China National Petroleum and Natural Gas Pipeline Group Co., Ltd.
Abstract: In response to the challenges posed by the traditional separation of information security and functional safety in oil and gas pipeline control systems, which struggle to effectively address complex integrated security threats, this paper proposes an integrated security protection strategy that combines functional safety and information security. Key technologies such as all-time, all-domain perception, conflict resolution between information security protection and functional safety protection, and dynamic risk decision-making adaptation are introduced. This strategy achieves collaborative defense between functional safety and information security, ensuring the continuity and reliability of the oil and gas transportation process.
Keywords:Integrated security; Functional safety; Industrial control information security; Oil and gas pipeline network
1 Introduction
The oil and gas pipeline control system is a typical application of Cyber Physical Systems (CPS), which closely integrates the control of physical processes with network technology, enabling monitoring and control of oil and gas transmission, processing, and storage. The oil and gas pipeline stations involve numerous physical devices (such as oil pumps and compressor units) and complex process flows (such as filtration and separation). Any functional failure or anomaly can lead to severe safety issues, such as equipment damage, oil and gas leaks, or even explosions. Therefore, embedding safety functions into the oil and gas pipeline control system allows for real-time monitoring and prediction of potential functional failures, enabling timely measures to prevent accidents and ensuring the safety of physical devices and production processes. The control systems at oil and gas stations connect a large number of sensors, controllers, and actuators through networks, facing an increasing number of information security threats. Traditional network security measures, such as firewalls and intrusion detection systems, while providing some level of protection, are still inadequate against complex new attacks. Therefore, it is necessary to enhance the network system’s resistance to attacks through multi-layered security mechanisms, reducing system failures and production interruptions caused by network attacks. Additionally, the characteristics of CPS make functional safety and information security closely related, and the traditional separation of information security and functional safety is insufficient to effectively address complex integrated security threats. Thus, it is essential to integrate functional safety and information security to achieve collaborative defense of security mechanisms and improve the overall security level of the system.
To enhance the autonomy and adaptability of the control system’s defense security, this paper proposes an integrated security strategy for the station’s control system, which incorporates functional safety mechanisms and information security collaborative mechanisms into the control system, enabling it to possess autonomous perception, analysis, and response capabilities. This is of significant importance for ensuring the safety of physical processes and network systems in oil and gas pipeline stations, achieving collaborative defense, enhancing autonomy and adaptability, and ensuring the continuity and reliability of production processes.
2 Concept of Integrated Security Protection Strategy
The integrated security protection strategy arises from the security protection needs derived from the continuous integration of industrial control systems and physical production systems. It aims to embed information security and functional safety into the entire lifecycle of CPS systems, constructing a dynamic overall security defense system for CPS from a systematic and holistic perspective, ensuring the overall operational safety of industrial control systems and physical production systems. This strategy requires the establishment of functional safety capabilities, information security capabilities, and collaborative capabilities between functional safety and information security within the information physical system, enabling the CPS system to possess self-immunity. The characteristics of the integrated security protection strategy are summarized as follows:
(1) Overall security. Overall security refers to the capability of the security system to have layered defenses and collaborative responses. The integrated security protection strategy has self-perception and self-response capabilities for information security incidents; for cross-domain attacks on information physics, it has a synergistic effect between information security capabilities and functional safety capabilities, achieving full-domain perception, cross-domain assessment, and collaborative response to ensure the continuous safe operation of physical production systems.
(2) Conflict resolution. Conflict resolution essentially addresses the conflicts between functional safety and information security, ensuring that the architecture, configuration, and functions of information security technologies have an acceptable impact on functional safety. For optimized functional safety technologies and information security technologies, the analysis of the architecture, configuration, and functions of information security technologies on the enhancement, conflict, and synergy of functional safety is conducted; when conflicts arise, conflict risk assessments are carried out, and information security technologies are optimized based on acceptable risk standards. At this point, the protective capability level of information security technologies will still meet the risk assessment level requirements of the system.
(3) The “Three Synchronizations” principle. The “Three Synchronizations” refers to the need for synchronized planning, construction, and operation of the CPS system and the construction of integrated security protection capabilities, achieving full lifecycle management of integrated security protection, and ensuring the combination of construction and operation, as well as security perception and security response. Synchronized planning is the starting point and key of integrated security protection, emphasizing the need to advance the focus, achieving deep integration and comprehensive coverage of integrated security protection and CPS. Synchronized construction is the implementation and guarantee of the integrated security protection strategy, emphasizing the introduction of information security capabilities, functional safety capabilities, and collaborative capabilities of information security and functional safety during CPS construction. Synchronized operation refers to the life of integrated security protection, where the security capabilities formed through planning and construction need to have operational, technical, personnel, and management specifications, forming a complete system that outputs security capabilities and enhances the overall level of defense.
3 Technical Framework of Integrated Security Protection Strategy
The integrated security strategy combines the infrastructure of the oil and gas pipeline control network, based on risk-driven design and capability-oriented design principles, through all-domain situational dynamic perception, collaboration between information security and functional safety, and dynamic adaptation of risk decision-making, constructing a multi-layered, collaborative, and interactive CPS system deep defense system, as shown in Figure 1.
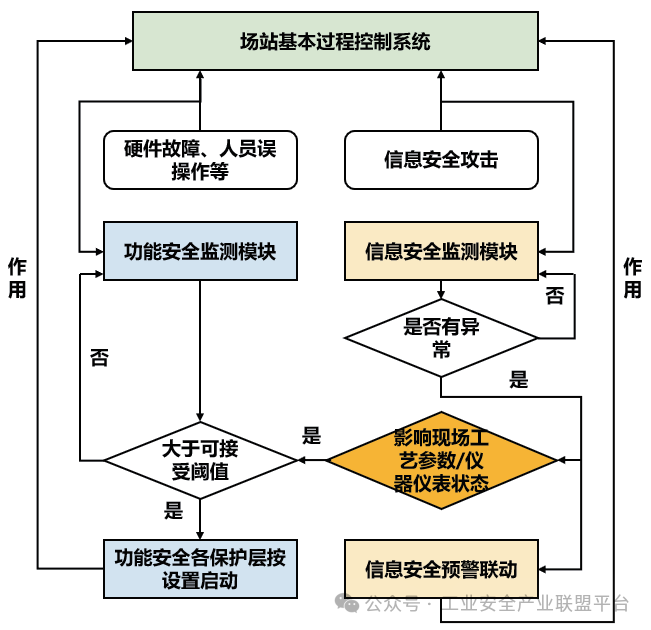
Figure 1 Technical Framework of Integrated Security Strategy for the Station
For abnormal states caused by hardware failures, human errors, etc., real-time dynamic monitoring is conducted through functional safety monitoring modules, and the abnormal state parameters are transmitted to the system. The system determines whether the current process anomaly exceeds the acceptable threshold. If the process anomaly is below the acceptable threshold, monitoring continues; if it exceeds the threshold, functional safety protection layers are activated as needed. For potential information security attacks faced by the station’s industrial control system, real-time dynamic monitoring is conducted through information security monitoring modules. If no anomalies are detected, monitoring continues. If anomalies are found, the information security early warning linkage mechanism is activated. In this process, multi-domain instruction-level comparison measures are used to analyze whether the current information security attack has affected the on-site process parameters/instrument status. If it has affected the on-site process parameters/instrument status, the impacts of functional safety and information security need to be comprehensively considered. For scenarios with high consequence levels, it is recommended to implement physical isolation between the safety instrumented system and the basic process control system (BPCS), while logical isolation can be implemented in other general scenarios.
3.1 All-time, All-domain Dynamic Perception of the Station
All-time, all-domain dynamic perception of the station refers to the comprehensive, rapid, and accurate acquisition of the safety operating status of the industrial control system and physical production system, which is an important foundation for ensuring the safe operation of the station. From the perspective of the causes of hazardous events or accidents in physical equipment facilities at the station, information security incidents, physical equipment failures, human errors, and natural environmental factors are the reasons for abnormal data transmission, business logic anomalies, and process parameter anomalies. Based on this, the monitoring of elements that lead to changes in the operational status of the production system is referred to as dynamic measurement of various uncertain factors and process variables. The perception dimensions involve network security perception, device security perception, business logic perception, process parameter perception, and user behavior analysis.
(1) Network security perception: Given the large scale and complexity of network devices, servers, and applications at oil and gas pipeline stations, a flexible combination of network intrusion detection technology and host intrusion detection technology is employed. Network intrusion detection technology monitors the entire station’s network traffic, identifying suspicious activities and known attack patterns, suitable for central management of external attacks and network traffic. Host intrusion detection system technology focuses on specific hosts, monitoring system files and logs to detect abnormal behaviors.
(2) Device security perception: This mainly includes monitoring the status of terminal devices and checking the integrity of firmware/software. Terminal device status monitoring refers to monitoring the health status of all connected devices, including sensors, controllers, actuators, etc., ensuring they operate normally and have not been tampered with. The content of device security status monitoring mainly includes communication status (i.e., monitoring the connection status between devices and the control system to ensure timely and reliable data transmission), performance indicators (such as processing speed, response time, power consumption, etc., to ensure they operate within reasonable ranges), fault detection (such as sensor failures, controller misconfigurations, etc.), and environmental monitoring. Firmware integrity checks mainly involve regularly checking whether the device firmware is consistent with the latest version provided by the manufacturer to prevent security vulnerabilities caused by undetected damage for extended periods.
(3) Business logic perception: This mainly includes monitoring the operational processes of the station and detecting dangerous messages in the control network. Monitoring the operational processes of the station focuses on monitoring key behavior indicators during production processes, setting up early warning mechanisms based on acceptable thresholds. Once abnormal situations are detected (e.g., equipment start/stop processes not conforming to specifications), alarms are automatically triggered to ensure that production processes are executed according to predetermined operational norms and standards. Dangerous message detection in the network refers to establishing models to verify the integrity of configuration messages sent and received, detecting communication behaviors inconsistent with historical (or previous) data, and promptly identifying disguised or tampered messages.
(4) Process parameter perception: Through various types of sensors, key process parameters are monitored and collected in real-time to ensure the safety, reliability, and efficiency of production operations. All this data is transmitted in real-time to the control center via communication protocols, where the control center compares historical data with real-time data to identify abnormal patterns during the operational process and provide early warnings.
(5) User behavior analysis: User behavior analysis is a key measure to protect the industrial control system and data of the station. It mainly involves establishing a baseline model of normal user behavior to detect abnormal login behaviors, privilege escalation behaviors, and unusual access patterns.
3.2 Collaboration between Information Security and Functional Safety
In the oil and gas pipeline control system, the effective collaboration between the information security protection layer and the functional safety protection layer is a crucial foundation for ensuring the system’s long-term safety and reliability. The collaboration between the two protection layers is based on integrated risk assessment, which focuses on the potential impacts of information security incidents on functional safety, such as hacker attacks disrupting the control logic of safety instrument systems. Information security protection serves as an external barrier against viruses and malicious attacks, while functional safety measures act as the immune system of the industrial control system, conducting proactive defense and response. When information security protection fails and viruses or attacks infiltrate, functional safety measures should be able to promptly detect anomalies/deviations and trigger protection (e.g., entering a safe state); at the same time, information security detection measures (such as probes) should be deployed in the industrial control system to monitor operational anomalies in real-time, analyzing system abnormal behaviors (such as deviations in process parameters, abnormal messages, etc.) to determine and issue alerts for abnormal events. Additionally, regular inspection tests should be conducted to assess the health status of the industrial control system and the state of the integrated protection system for functional safety and information security. The functional safety system operates under information security protection, and the negative impacts of information security protection on functional safety should be controlled within acceptable limits, ensuring that the industrial control system can achieve controllable risks through functional safety after information security protection fails.
3.3 Dynamic Adaptation of Risk Decision-Making
Dynamic adaptation of risk decision-making fully considers the dynamic nature of the station’s industrial control system status, adjusting risk management decisions in real-time based on risk assessment results. Dynamic adaptation of risk decision-making is essentially an online risk assessment and decision logic, comprehensively considering information security risks and functional safety risks. Independent functional safety assessments can refer to the standard IEC 61508, while separate information security assessments can refer to the standard IEC 62443. Integrated risk assessments should be conducted from the CPS perspective to evaluate risks of network-physical attacks, establishing a series of risk assessment models for network-physical attacks, such as: attackers intruding into the network, tampering with control instructions and sensor data transmitted to the physical production system; using DDoS and other means to render the control system inoperable; or altering the operational state of physical devices through control instructions, leading to equipment damage or failure.
Based on the data obtained from the all-time, all-domain dynamic perception of the station in Section 3.1, real-time identification of abnormal behaviors is conducted, serving as input for risk decision-making and emergency linkage in Section 3.3. Based on different risk assessment results, a balance is achieved among multiple objectives such as cost, benefit, and safety, adapting the optimal decision-making scheme. Based on risk assessment results and environmental changes, corresponding functional safety measures and information security measures are implemented according to the dynamic adaptation risk control strategy in Section 3.3.
4 Conclusion
In response to the challenges posed by the traditional separation of information security and functional safety in oil and gas pipeline stations, which struggle to effectively address complex integrated security threats, this paper proposes an integrated security protection strategy for oil and gas pipeline control systems. Through all-domain situational dynamic perception, collaboration between information security and functional safety, and dynamic adaptation of risk decision-making, the overall safety of oil and gas pipeline stations is ensured, achieving collaborative defense capabilities between functional safety and information security.
References omitted.
Author Profiles
Zhang Yabin (1986-), male, from Baoding, Hebei, senior engineer, PhD, currently employed at the Institute of Comprehensive Technology and Economic Research of Mechanical Industry Instruments, with research interests in key technologies and standards for intelligent manufacturing and industrial control security.
Zhang Xin (1990-), male, from Liaocheng, Shandong, senior engineer, PhD, currently employed at the Institute of Comprehensive Technology and Economic Research of Mechanical Industry Instruments, with research interests in risk assessment and other key technology research and standard development.
Wang Linkun (1974-), male, from Jiamusi, Heilongjiang, professor-level senior engineer, PhD, currently employed at the Institute of Comprehensive Technology and Economic Research of Mechanical Industry Instruments, with research interests in fieldbus and electromechanical control.
Liu Yao (1987-), female, from Taizhou, Jiangsu, senior engineer, bachelor, currently employed at the Institute of Comprehensive Technology and Economic Research of Mechanical Industry Instruments, with research interests in functional safety, industrial control information security, and integrated security.
Sun Tieliang (1967-), male, from Dezhou, Shandong, senior engineer, bachelor, currently employed at the Oil and Gas Regulation Center of China National Petroleum and Natural Gas Pipeline Group Co., Ltd., with research interests in automation control, communication, and industrial control system network security.
Huang He (1984-), male, from Yongchuan, Chongqing, senior engineer, master, currently employed at the Oil and Gas Regulation Center of China National Petroleum and Natural Gas Pipeline Group Co., Ltd., with research interests in automation control and industrial control system network security.
Lü Feng (1969-), male, from Weihai, Shandong, senior engineer, bachelor, currently employed at the Oil and Gas Regulation Center of China National Petroleum and Natural Gas Pipeline Group Co., Ltd., with research interests in automation control and industrial control system network security.
· end ·
Source | “Automation Expo” January 2025 issue
Editor | He Min

If you need cooperation or consultation, please contact the WeChat ID of the Industrial Safety Industry Alliance platform secretary: ICSISIA20140417
Recommended Readings
Heavyweight | Launch of the January 2025 issue of “Automation Expo” and the “Special Issue on Information Security of Industrial Control Systems (Volume 11)”
Must-read for the 2025 Two Sessions | These key proposals on industrial information security will rewrite industry rules
Ministry of Industry and Information Technology | Risk warning on preventing network attacks targeting DeepSeek localized deployment
Insights | Industrial Control Security Protection for Long-distance Oil and Gas Pipelines: Strategies, Practices, and Prospects
DeepSeek Analysis | Current status and future prospects of zero-trust security architecture in the industrial field
White Paper | Northeast University: 2024 Industrial Control Network Security Situation White Paper (Download Attached)
Recommended Read | The five network security technologies that are about to become obsolete
Insights | Research on encryption technology for industrial programmable control systems
Recommended Read | DeepSeek insights and reflections from the perspective of security professionals
Ministry of Industry and Information Technology | In 2024, the revenue in China’s information security field will reach 229 billion yuan
Attention | Results of security testing for key network devices (19th batch)
Power Safety | 2024 New Power System Safety Construction Guidelines Report (Download Attached)
Ministry of Industry and Information Technology and thirteen other departments | 2024 List of typical project cases for the application of cybersecurity technologies
Attention | Joint issuance of the “Implementation Plan for Improving Data Flow Security Governance to Better Promote the Marketization and Value of Data Elements” by the National Development and Reform Commission, the National Data Bureau, and six other departments