 Coal mining has evolved from blasting and mechanized mining to intelligent mining. With advancements in technology, the Internet of Things, big data, cloud computing, 5G, and artificial intelligence have become key focal points in a new round of technological revolution and industrial upgrade. The adoption of next-generation intelligent technologies to transform traditional coal mining production methods, improve working conditions in coal mines, reduce the number of underground workers, and build safe, efficient, and green unmanned or minimally manned intelligent mines has become an important measure for coal enterprises to transform and upgrade. A certain coal mine in Shandong actively responded to the group’s call for the construction of “5G + Smart Mine” and has fully established and promoted the intelligent mining 3.0 model in the coal industry.To ensure the safe and stable production of enterprises and to keep network security construction in line with information technology development, the coal mine production system is gradually realizing the transformation and construction of intelligent mines. Therefore, during this industrial ring network renovation process, the planning, implementation, and operation of the industrial control network security protection system are being carried out simultaneously.
Coal mining has evolved from blasting and mechanized mining to intelligent mining. With advancements in technology, the Internet of Things, big data, cloud computing, 5G, and artificial intelligence have become key focal points in a new round of technological revolution and industrial upgrade. The adoption of next-generation intelligent technologies to transform traditional coal mining production methods, improve working conditions in coal mines, reduce the number of underground workers, and build safe, efficient, and green unmanned or minimally manned intelligent mines has become an important measure for coal enterprises to transform and upgrade. A certain coal mine in Shandong actively responded to the group’s call for the construction of “5G + Smart Mine” and has fully established and promoted the intelligent mining 3.0 model in the coal industry.To ensure the safe and stable production of enterprises and to keep network security construction in line with information technology development, the coal mine production system is gradually realizing the transformation and construction of intelligent mines. Therefore, during this industrial ring network renovation process, the planning, implementation, and operation of the industrial control network security protection system are being carried out simultaneously.

Project Requirement Analysis
1. The promotion of intelligent production construction in a certain coal mine has led to an increasing number of internal and external services, especially the construction of systems such as 10G industrial ring networks, monitoring and control networks, video networks, power networks, sales networks, wireless WiFi, and 5G. The industrial control system network is continuously expanding and becoming increasingly complex. The control system no longer operates on an independent network; it is interconnected with enterprise management networks and other functional systems, which increases the risk of external threats such as viruses. Once infected by malicious entities like viruses, it can lead to communication congestion in the control system or even production accidents, resulting in immeasurable losses. Therefore, it is necessary to achieve isolated access between the industrial ring network and the office network, video network, ensuring normal data transmission of the industrial control system and avoiding unknown threats affecting the industrial control system;2. Some information systems in coal mine production rely on remote maintenance by manufacturers, using remote maintenance software such as Sunflower and TeamViewer, which directly exposes the enterprise’s industrial control servers to the internet, making them vulnerable to hacker attacks and destruction, while also making it impossible to audit the operations of maintenance personnel. Therefore, it is necessary to ensure the safe operation and maintenance of the enterprise production system to avoid introducing risks to the enterprise production network during maintenance;3. To achieve intelligent and unmanned production in coal mines, the production information system plays a crucial role. If the increasingly large and complex operating environment of the production information system is infected by computer viruses or other malicious codes, it can cause the system to fail, leading to immeasurable losses for coal mining enterprises. Therefore, it is necessary to enhance the industrial host’s ability to resist malicious code attacks and control peripherals to prevent important information systems such as production control, safety monitoring, and personnel positioning from being infected by ransomware and other computer viruses, which could paralyze production systems and endanger the safety of miners;4. Currently, there is a shortage of talent in the field of industrial control system network security, and there are no relevant professional security devices to timely detect security vulnerabilities in the industrial network. In the event of a network security incident, it is impossible to quickly locate and resolve the issue. Therefore, it is necessary to improve the level of industrial control security management, regularly conduct assessments and inspections of coal mine production industrial control systems, and detect vulnerabilities in industrial equipment to timely identify and fix security vulnerabilities in the industrial control system network, reducing risks and preventing industrial control security incidents;5. Meet the compliance requirements of GB/T 22239-2019 “Basic Requirements for Network Security Level Protection” Level 2.
Solution
The industrial control system network security construction project for the smart mine of a certain coal mine is planned and designed based on the actual business needs of the client, referencing the relevant requirements of Level 2 of the security protection standard.Upon completion, it will comprehensively enhance the overall security of the enterprise’s smart mine industrial control system, ensuring the reliability and stability of equipment, systems, and networks, reducing the workload of security operation and maintenance personnel, and improving the level of safety production management, work efficiency, and management efficiency.
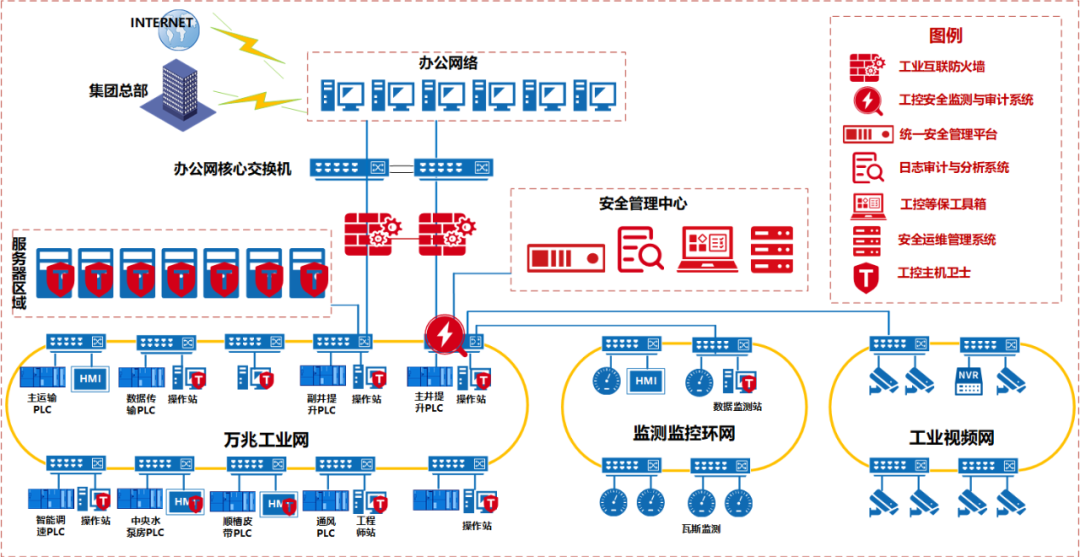
Figure 1: Schematic Diagram of Industrial Control Security Protection for this Project
Area Boundary Access Control
The on-site network architecture adopts a dual-network redundancy design, and the industrial interconnection firewall uses a dual-machine + HA configuration to ensure high availability of the network;By adding industrial interconnection firewalls between the core switches of the production industrial ring network, office network, and video core switch, a DMZ area is established. By configuring whitelist policies and enabling IPS and AV virus detection modules, the normal data transmission of the industrial control system is effectively guaranteed, avoiding unknown threats affecting the industrial control system;
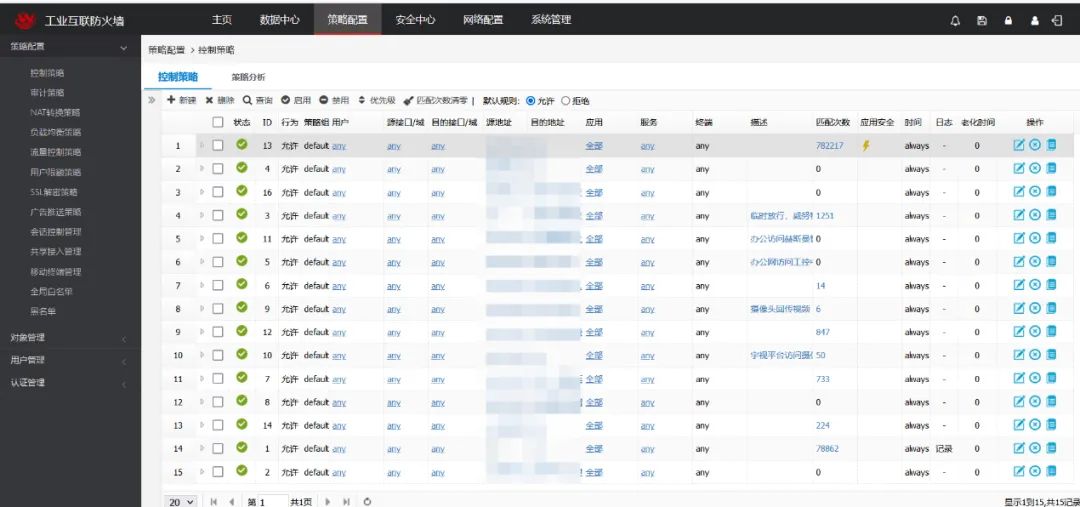
Figure 2: Boundary Access Control of Industrial Control System
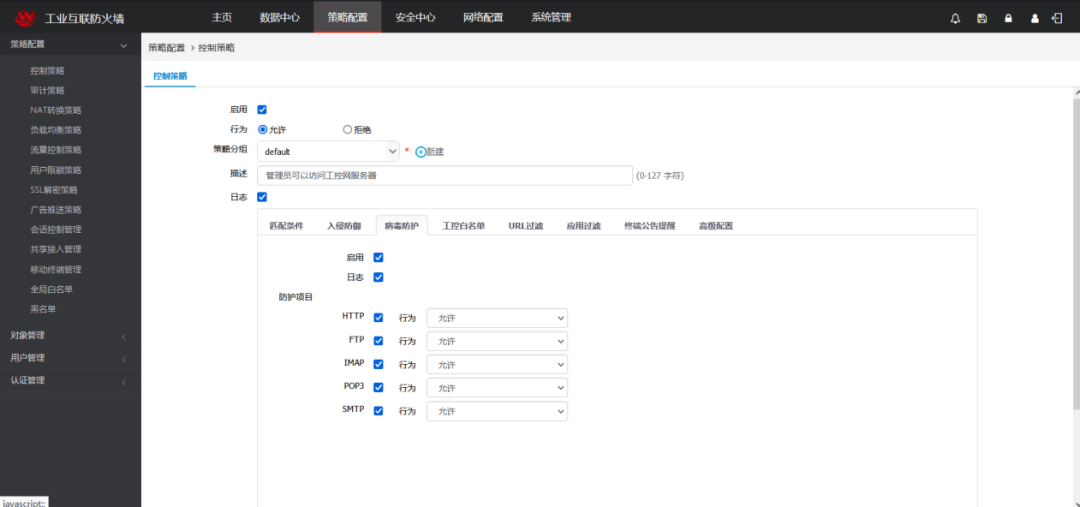
Figure 3: Boundary Virus Detection of Industrial Control System
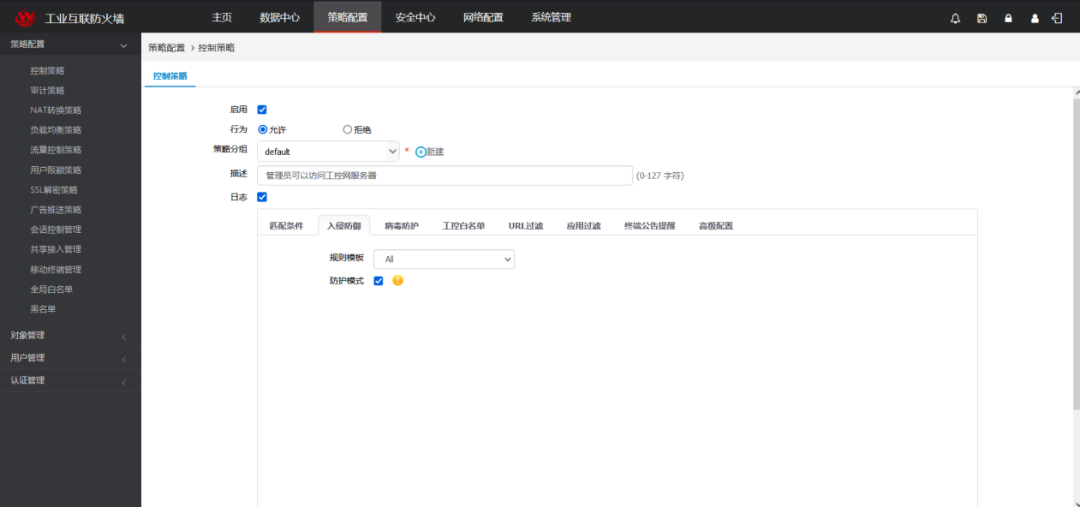
Figure 4: Boundary Intrusion Defense of Industrial Control System
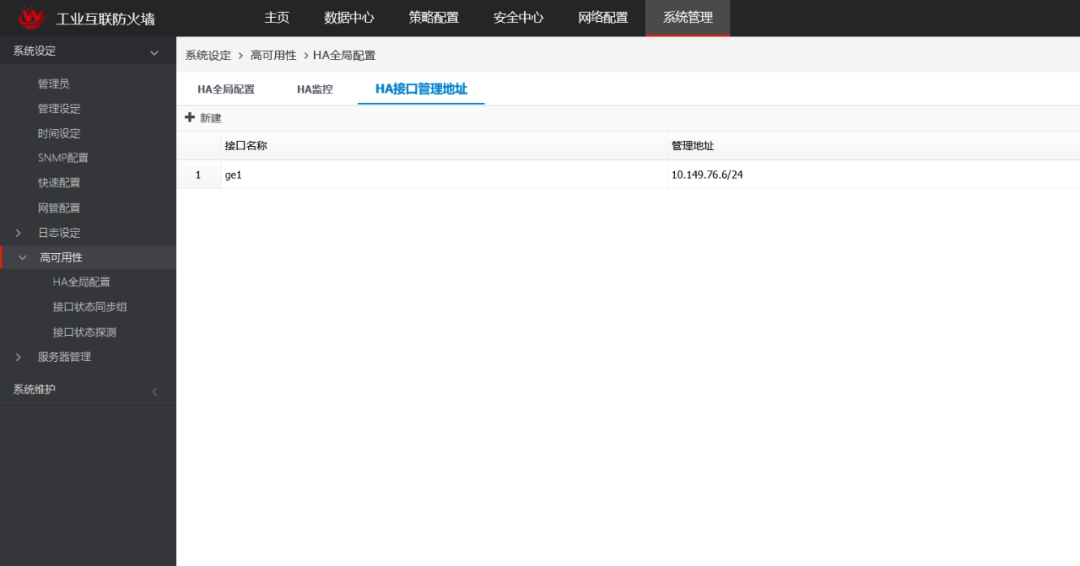
Figure 5: Dual-Machine HA Hot Backup of Security Devices
Industrial Traffic Analysis
Deploy an industrial control security monitoring and auditing system in bypass mode next to the core switch of the industrial ring network to collect network traffic data in the mining area for security auditing. By configuring monitoring strategies for industrial control protocol whitelists, real-time monitoring and anomaly alerts are provided for industrial protocol data, key control operations, and abnormal behaviors in the control network, allowing for the timely detection of violations and malicious behaviors such as hacker attacks in the industrial network;
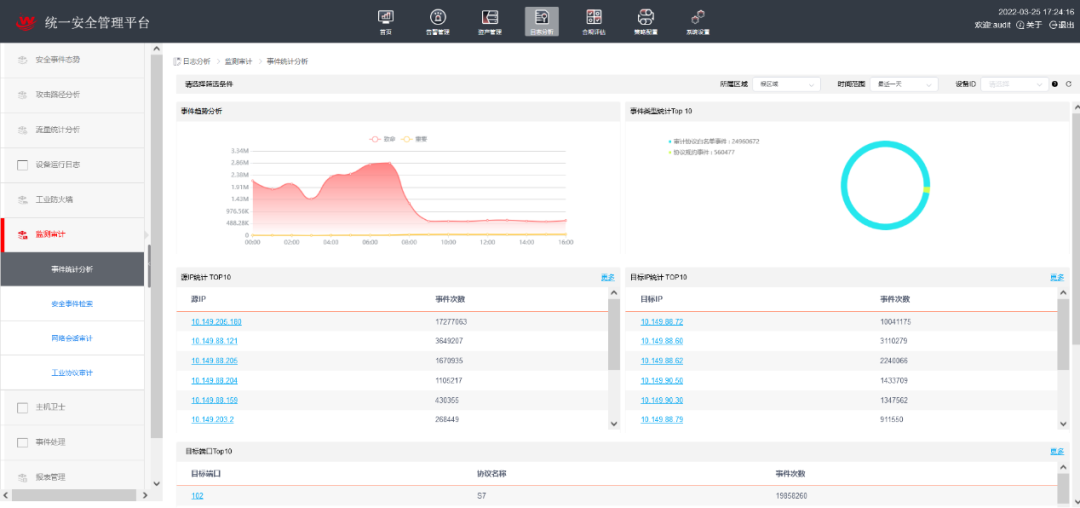
Figure 6: Industrial Control Traffic Event Analysis
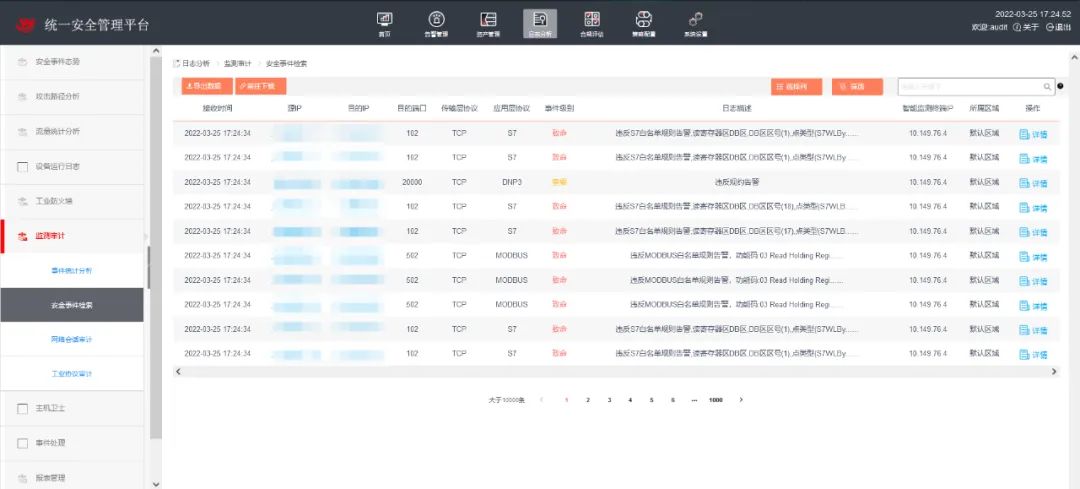
Figure 7: Deep Instruction-Level Audit of Industrial Control Protocol
Industrial Control Host Security Protection and Hardening
Deploy industrial control host guardians on the servers of the enterprise’s production and safety monitoring systems to protect against malicious code, control peripherals such as USB drives, and strengthen baseline hardening measures to ensure a secure computing environment; effectively prevent the infection, execution, and spread of malicious programs or codes, including Stuxnet, BlackEnergy, ransomware, and mining viruses on industrial control hosts;
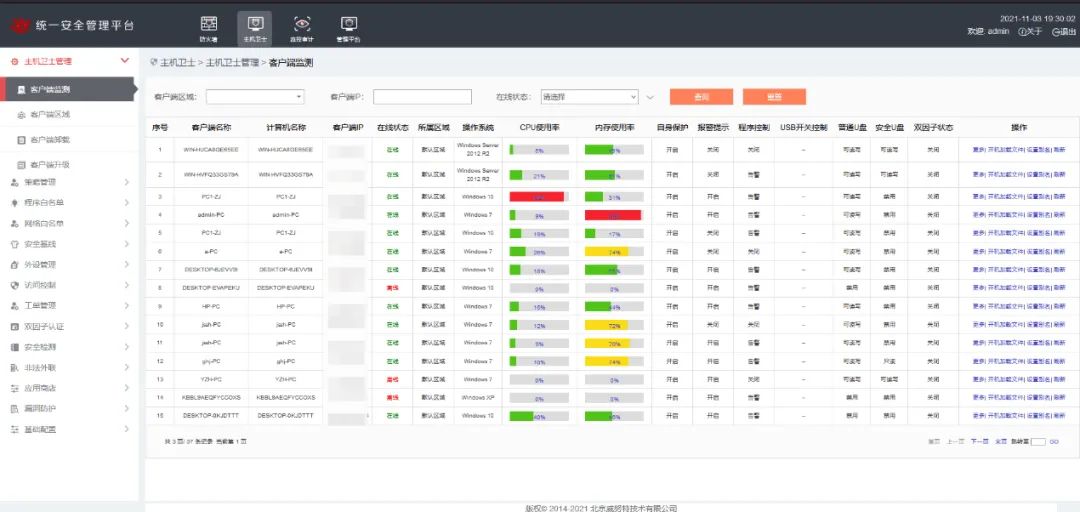
Figure 8: Unified Management of Industrial Host Protection
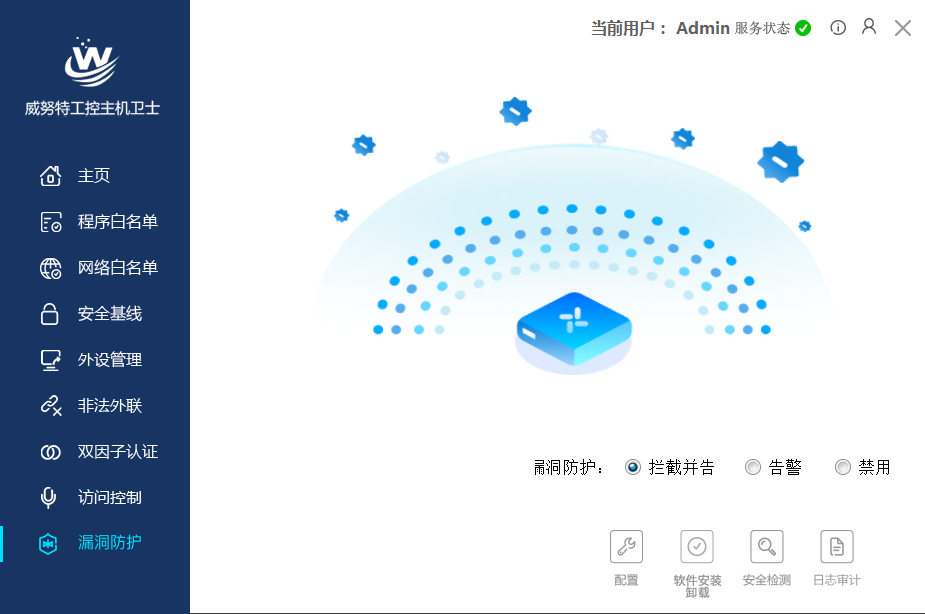
Figure 9: Virtual Vulnerability Protection of Industrial Hosts
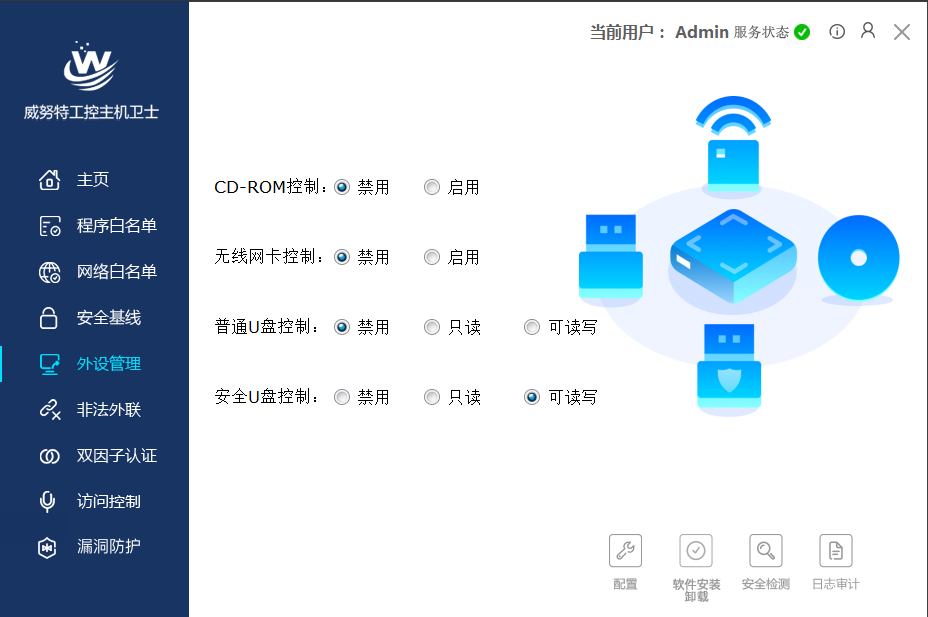
Figure 10: Control of Peripheral Devices for Industrial Hosts
Safe Operation and Maintenance of Production Systems
Deploy a security operation and maintenance management system on the core switch of the production industrial ring network to achieve refined control of operation and maintenance accounts; improve the level of system operation and maintenance management, track user operations on servers, prevent hacker intrusions and destruction, provide control and audit basis, and reduce operation and maintenance costs;
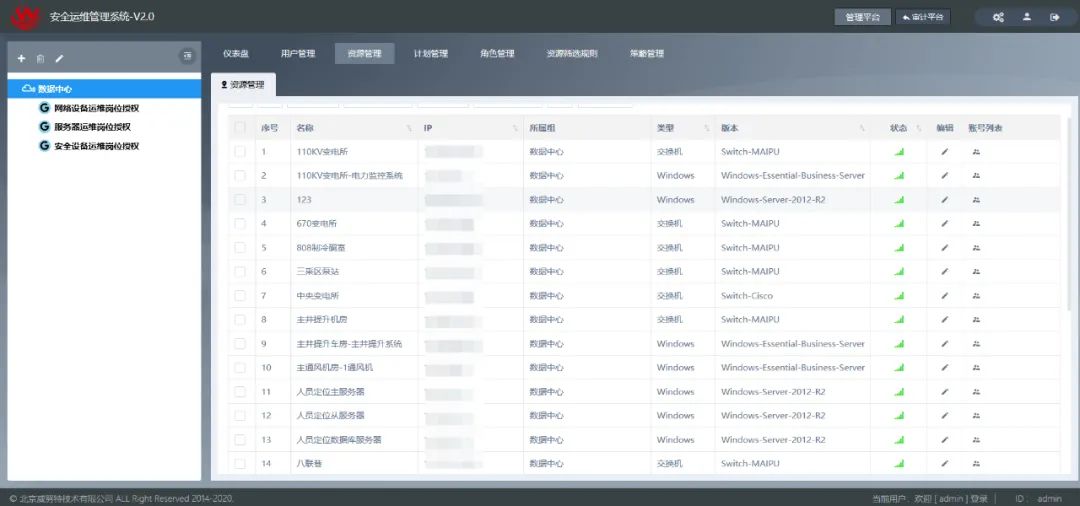
Figure 11: Control of Operation and Maintenance Permissions for Industrial Network Assets
Unified Collection and Audit of Industrial Control Logs
Deploy a log auditing and analysis system on the core switch of the production industrial ring network to collect and store logs from hosts, network devices, and security devices within the industrial control system. Perform correlation analysis on the logs to timely detect security issues within the industrial control system and respond promptly. The security event analysis module provides auditing and forensic analysis, supports internal investigations, establishes baselines, and predicts security operation trends, providing a basis for security construction decisions;
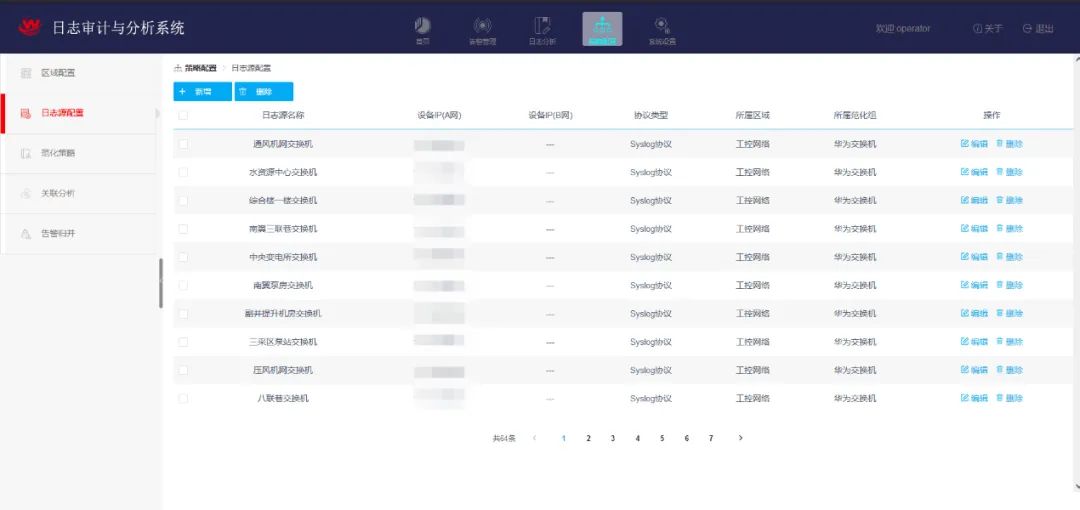
Figure 12: Log Collection of Industrial Control Network Devices
Self-Assessment of Industrial Control System Risks
Deploy an industrial control security assessment toolbox offline on the core switch of the production industrial ring network to regularly scan for vulnerabilities in the industrial control system, achieving control and management of industrial control vulnerabilities; enhance the ability to detect vulnerabilities in industrial control systems and provide effective security risk remediation suggestions and preventive measures to reduce economic risks caused by vulnerabilities;
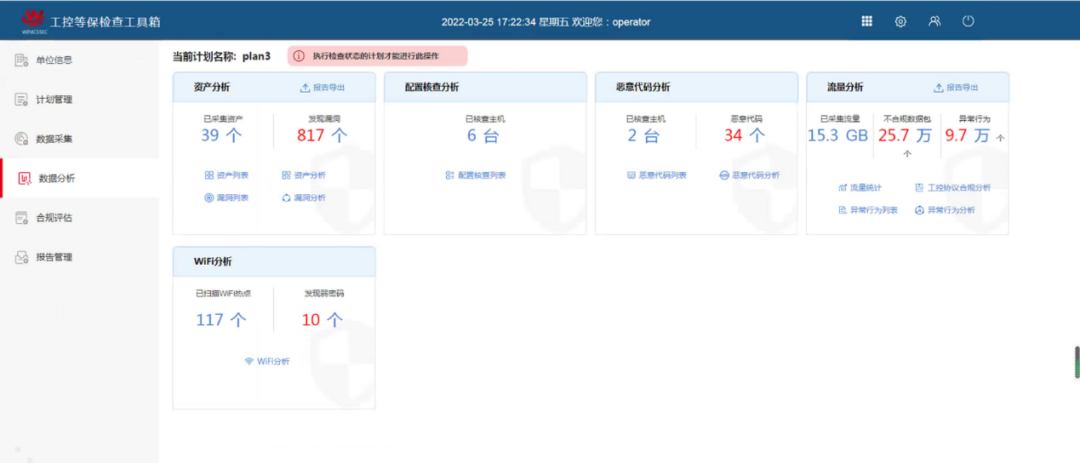
Figure 13: Data Analysis of Industrial Control Network Risk Assessment
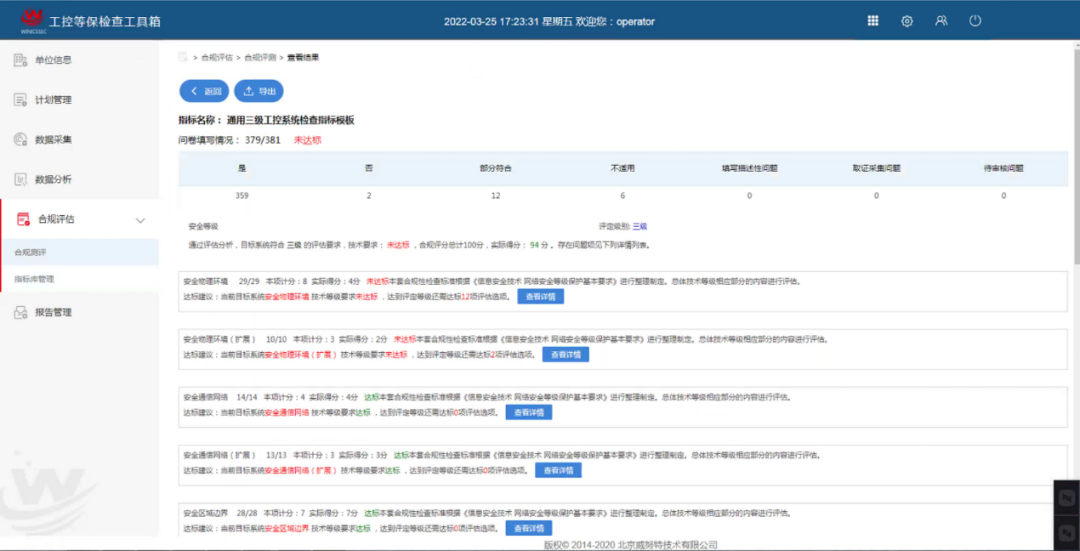
Figure 14: Compliance Assessment of Industrial Control Network
Unified Security Management
Deploy a unified security management platform on the core switch of the production industrial ring network to conduct unified security operation and maintenance of industrial network security devices, timely grasp the existing security situation, assist in improving the security protection system, reduce operation and maintenance costs, and enhance operation and maintenance efficiency.
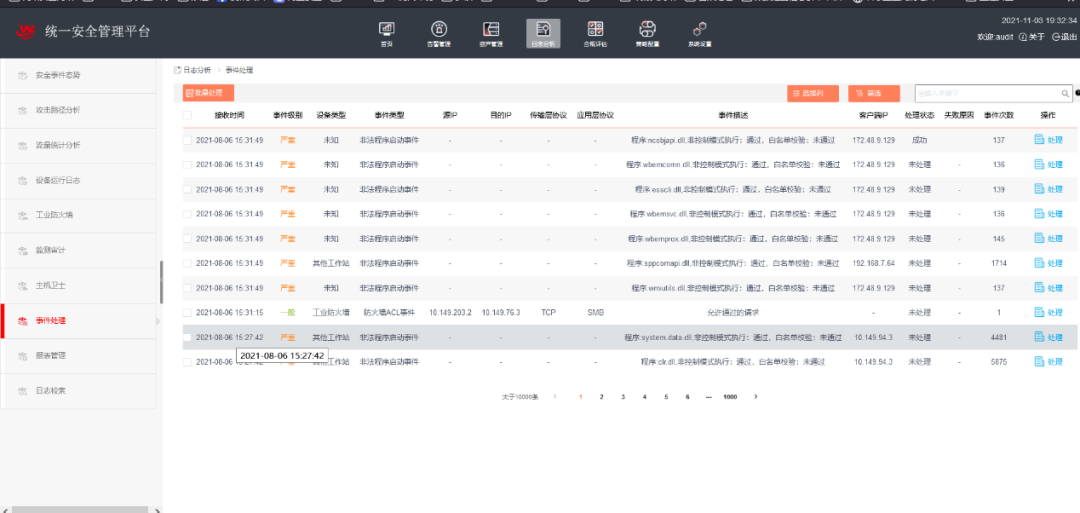
Figure 15: Unified Collection and Analysis of Security Device Logs
Customer Value
1. In terms of industrial control network security, build a “white environment” for the enterprise’s industrial control network, effectively ensuring the security of systems, communications, applications, and data at all levels within the industrial control network, improving the protection capabilities and levels of industrial control network security, comprehensively understanding the security protection status of industrial control systems, establishing a normalized detection and assessment mechanism for the enterprise’s industrial control systems, continuously optimizing and improving the security protection system, and ensuring stable operation of production business;2. In terms of compliance with security construction, meet the relevant technical requirements of GB/T 22239-2019 “Basic Requirements for Network Security Level Protection” regarding “one center, threefold protection,” addressing high-risk items in level protection, and successfully passing the Level 2 assessment;3. In terms of project promotion, this project serves as a pilot demonstration for the industrial control network security of the “5G + Smart Mine” intelligent mining 3.0 new model of a certain mining group, providing valuable experience for the promotion of intelligent production construction in other coal mines of the group in the future. Introduction to Winut
Introduction to Winut
Beijing Winut Technology Co., Ltd. (abbreviated as Winut) is a leader in the domestic industrial control security industry and a subsidiary of the Chinese state-owned capital venture capital fund. With outstanding technological innovation capabilities, it has become one of the six companies globally to receive ISASecure certification from the International Society of Automation and one of the first national-level specialized and innovative “little giant” enterprises.
Winut relies on its pioneering core technology concept of an industrial network “white environment” and a full range of independently developed industrial control security products to provide comprehensive lifecycle deep defense solutions and specialized security services for key national industries such as power, rail transportation, petroleum and petrochemicals, municipal services, tobacco, intelligent manufacturing, and military industry. To date, it has enabled over 4,000 industry clients in China and along the “Belt and Road” to achieve secure and compliant business operations.
As the national team for industrial control security in China, Winut actively promotes the construction of industrial clusters and the development of ecological circles, leads and participates in the formulation of national and industry standards in the field of industrial control security, and major activities for network security assurance, always taking the protection of China’s critical information infrastructure and cyberspace security as its mission, and is committed to becoming a backbone force in building a strong cyber power!




 Channel Cooperation Consultation: Mr. Tian 17326800322Article Cooperation: WeChat: shushu12121
Channel Cooperation Consultation: Mr. Tian 17326800322Article Cooperation: WeChat: shushu12121