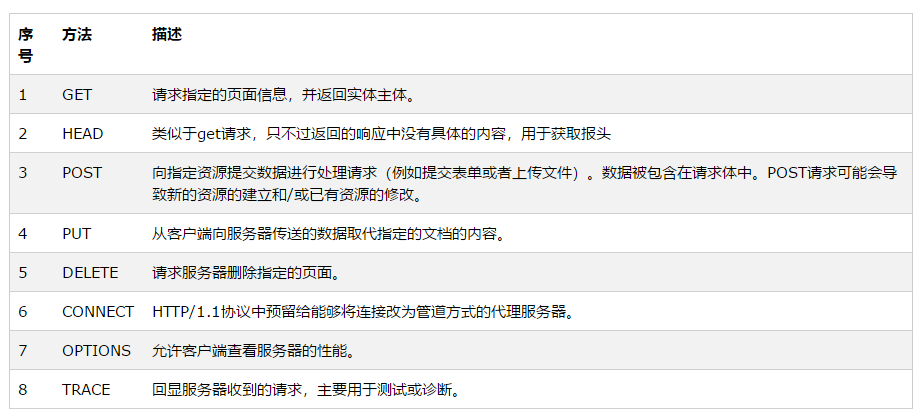
1. What is an HTTP Packet
What is HTTP
HTTP: (HyperText Transfer Protocol) is the protocol used for transferring hypertext from World Wide Web (WWW) servers to local browsers.
HTTP is a protocol based on the TCP/IP communication protocol for transmitting data (HTML files, image files, query results, etc.).
HTTP is an application layer protocol, and due to its simplicity and speed, it is suitable for distributed hypermedia information systems.
What is a Packet
A packet is the basic unit of transmission in a computer network. It is transmitted using the TCP/IP protocol stack.
A packet contains the content of the data as well as relevant information for transmitting and processing the data (such as the addresses of the sender and receiver).
A packet can be transmitted along different paths in one or more networks and reassembled at the destination. That is, the sender divides the data into appropriately sized packets and sends them over the network to the receiver. Upon receiving the packets, the receiver parses and processes them based on the header information, extracting the payload data and performing corresponding actions, such as display, storage, processing, etc.
2. HTTP Request Methods
The HTTP/1.1 protocol defines eight methods (sometimes called “actions”) to indicate different operations on the resource specified by the Request-URL.
HTTP/1.0 defined three request methods: GET, POST, and HEAD.
HTTP/1.1 added five new request methods: OPTIONS, PUT, DELETE, TRACE, and CONNECT.
GET Request Packet
It sends a request to obtain a certain resource on the server, with parameters passed after the URI. This request method allows you to see the request parameters directly in the browser’s URL bar:
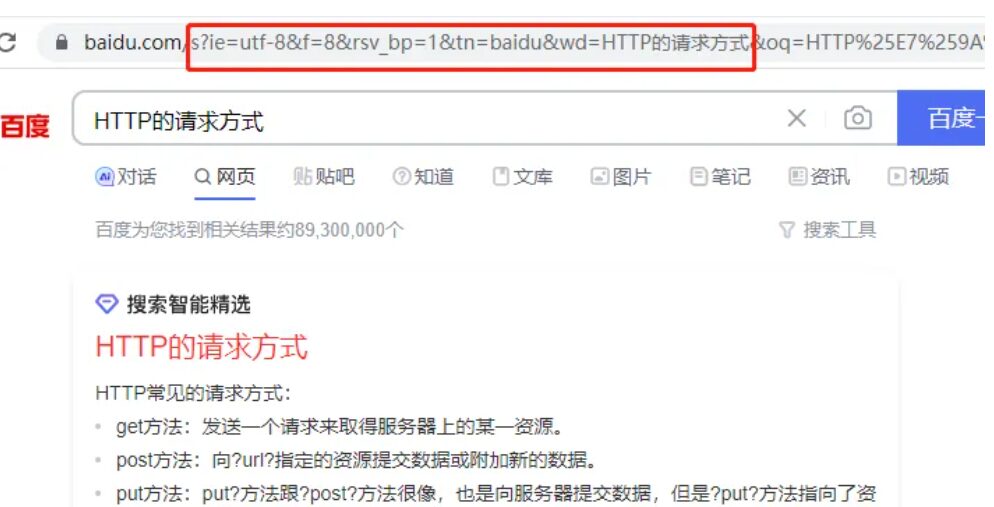
The presentation of the HTTP packet is as follows:
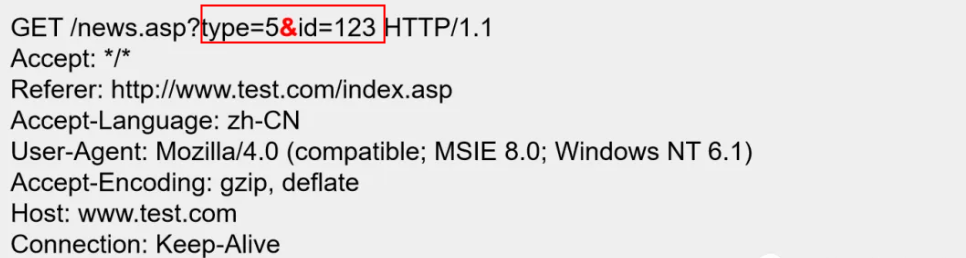
Parameters tpye=5 and id=123 were passed to news.asp
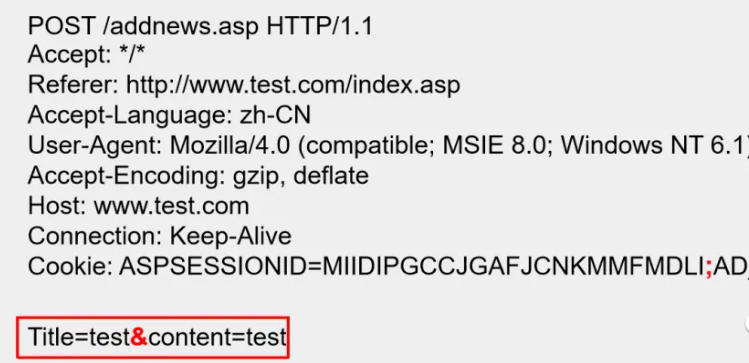
POST Request Method
When requesting resources using the POST method, the parameters are passed in the body of the packet rather than after the URI.
The presentation of the HTTP log is as follows:
This packet refers to passing two parameters: Title=test and content=test to addnews.asp.
Encoding and Encryption
In HTTP packets, various types of encoding and encryption are often seen. Therefore, it is necessary to understand some common encryption methods to better understand them.
For example, a POST parameter named ghost was found in a certain packet, which has encoding as follows:
Some web log:
ghost=%40eval%01%28base64_decode%28%24_POST%5Bz0%5D%29%29%3B&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOzskRj1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JFA9QGZvcGVuKCRGLCJyIik7ZWNobyhAZnJlYWQoJFAsZmlsZXNpemUoJEYpKSk7QGZjbG9zZSgkUCk7O2VjaG8oInw8LSIpO2RpZSgpOw%3D%3D&z1=RDpcXEFQTVNlcnY1LjIuNlxcd3d3XFxwaHBNeUFkbWluXFxjb25maWcuc2FtcGxlLmluYy5waHA%3D
This encoded data packet needs to be decoded before the specific request can be seen. Before that, let’s understand some common encoding and encryption methods in packets.
Recommended decoding website: https://gchq.github.io/CyberChef/
3. HTTP Packet Analysis (Practical)
Objective
Understand the structure of HTTP request and HTTP response messages and the meanings of related fields.
Topology Detection
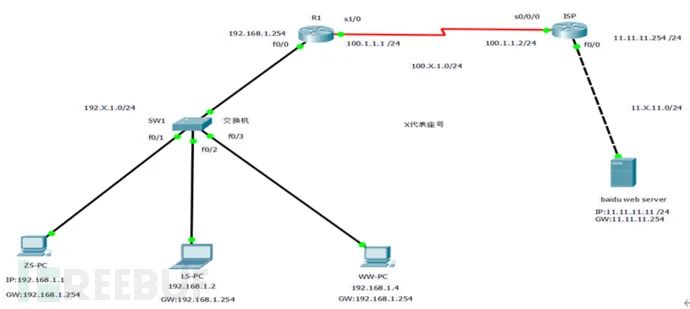
Experiment Tools
Cisco Packet Tracer
Experiment Steps
1. Configure the IP addresses, subnet masks, and default gateways for PC and Server. (1) ZS-PC (Zhang San)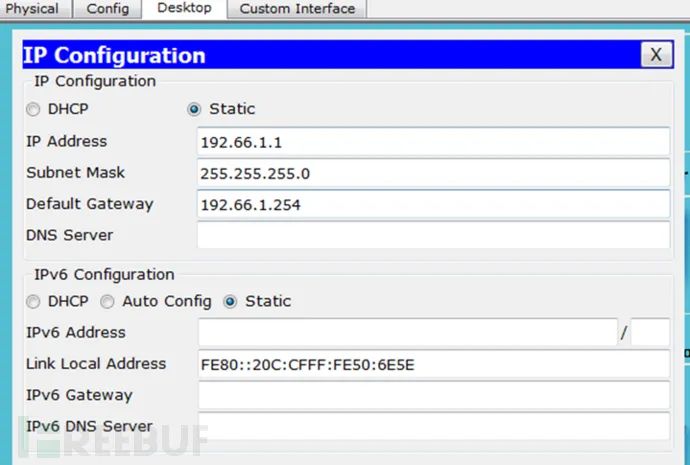 (2) LS-PC (Li Si)
(2) LS-PC (Li Si)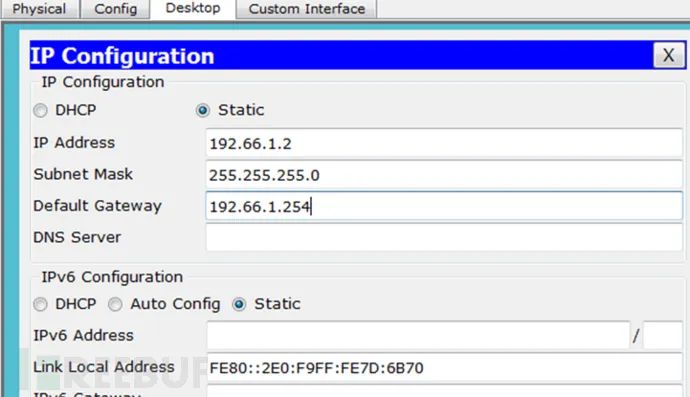 (3) WW-PC (Wang Wu)
(3) WW-PC (Wang Wu)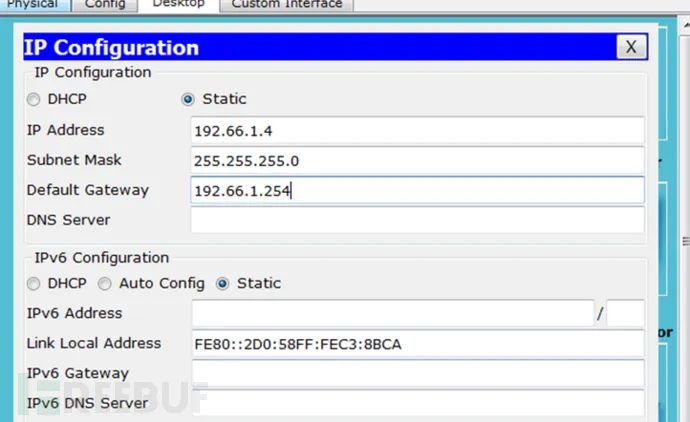 (4) Baidu Webserver
(4) Baidu Webserver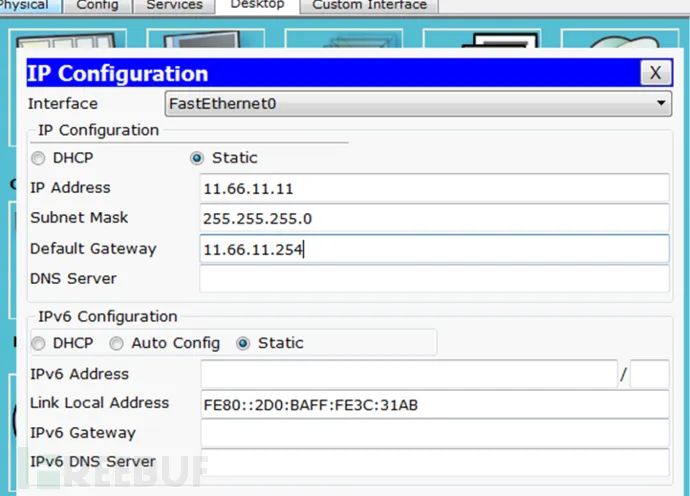 2. Configure the IP addresses for router R1 and router ISP. (1) R1
2. Configure the IP addresses for router R1 and router ISP. (1) R1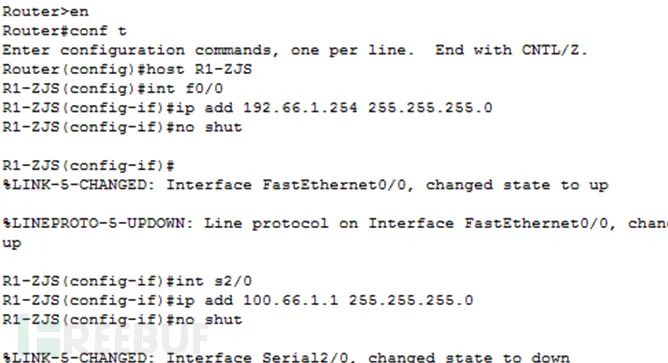 (2) ISP
(2) ISP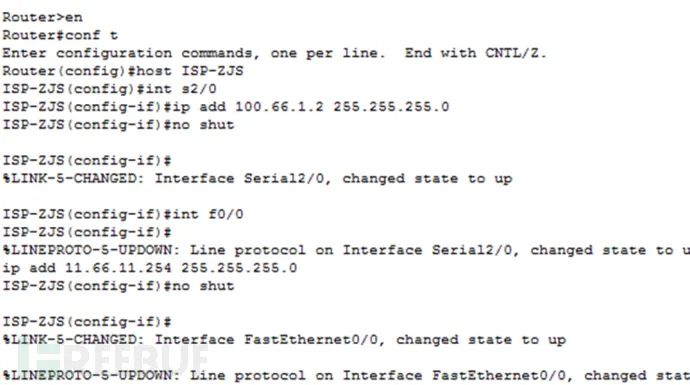 3. Configure the default routes for router R1 and router ISP. (1) R1
3. Configure the default routes for router R1 and router ISP. (1) R1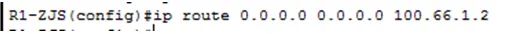 (2) ISP
(2) ISP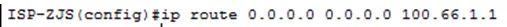 4. Test connectivity from ZS-PC to Baidu Webserver.
4. Test connectivity from ZS-PC to Baidu Webserver.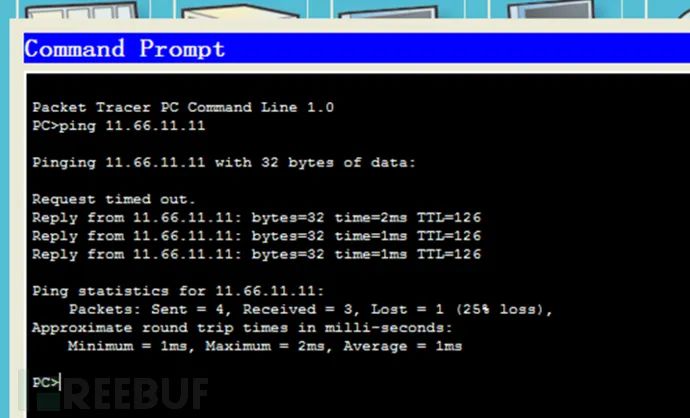 5. Configure Baidu Webserver.
5. Configure Baidu Webserver.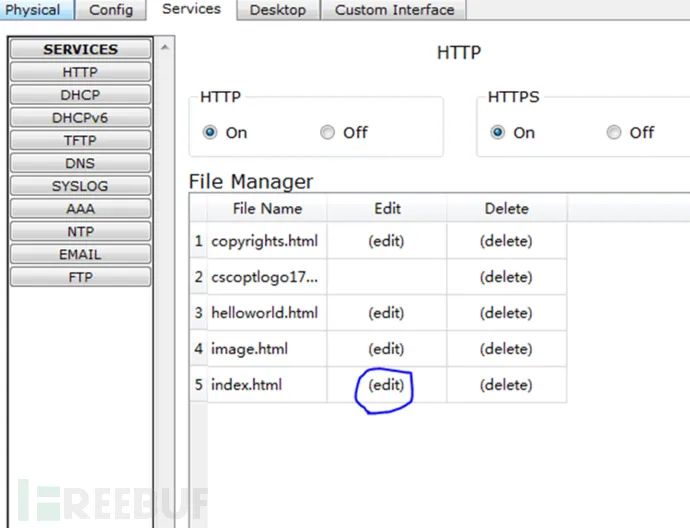
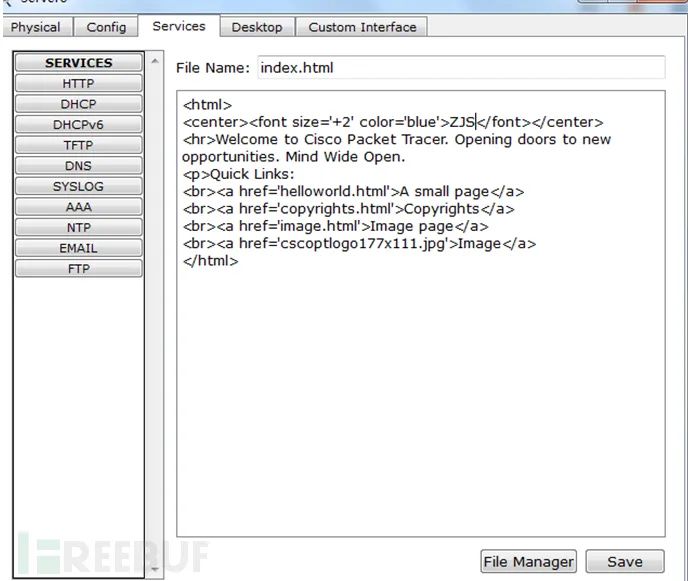 6. Access the Baidu Webserver webpage from ZS-PC and take a screenshot.
6. Access the Baidu Webserver webpage from ZS-PC and take a screenshot.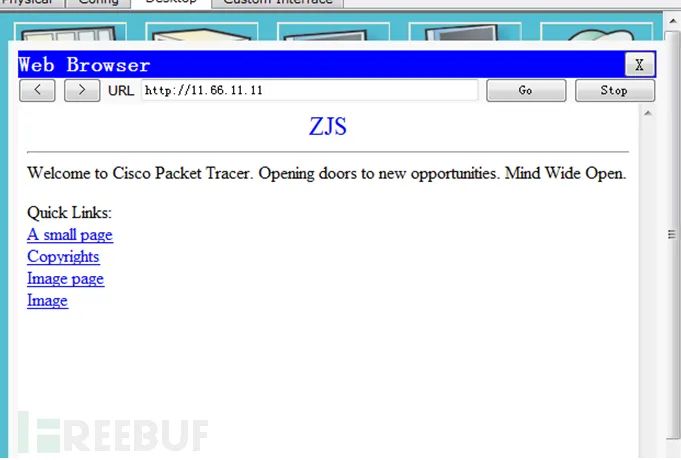 7. Switch to simulation mode, then access the Baidu Webserver webpage again from ZS-PC, capturing the TCP protocol packets (the three-way handshake) and HTTP protocol packets (HTTP request and HTTP response).
7. Switch to simulation mode, then access the Baidu Webserver webpage again from ZS-PC, capturing the TCP protocol packets (the three-way handshake) and HTTP protocol packets (HTTP request and HTTP response).
1) TCP three-way handshake packets (1) First handshake packet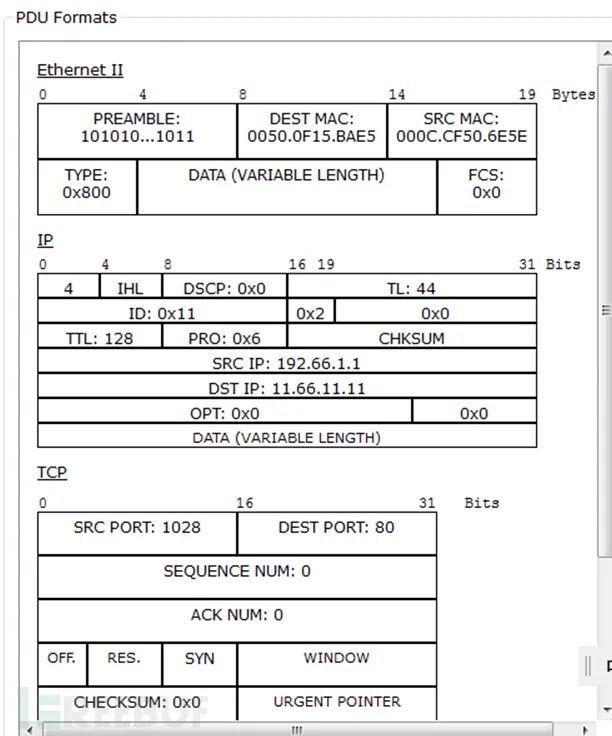 (2) Second handshake packet
(2) Second handshake packet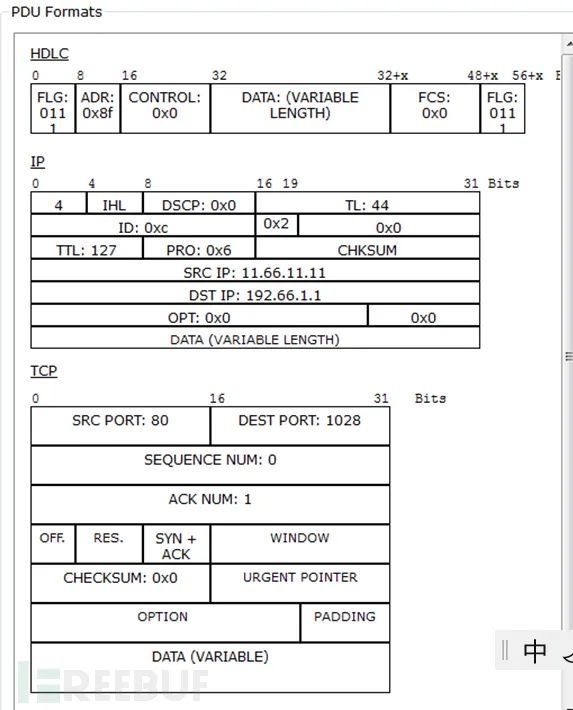 (3) Third handshake packet
(3) Third handshake packet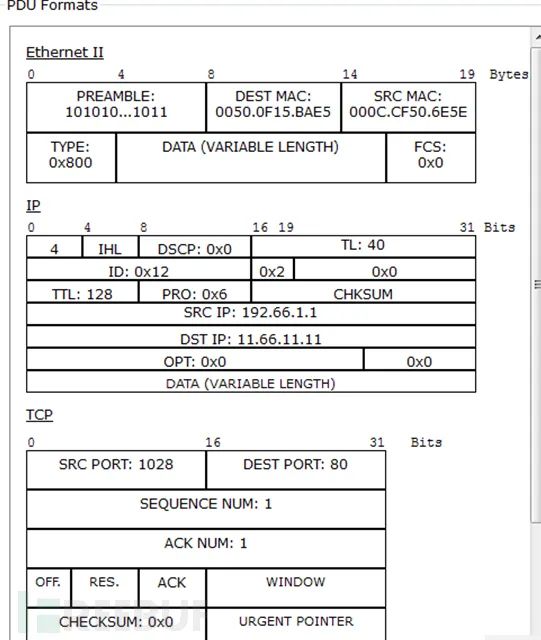 2) HTTP packets (1) HTTP request packet
2) HTTP packets (1) HTTP request packet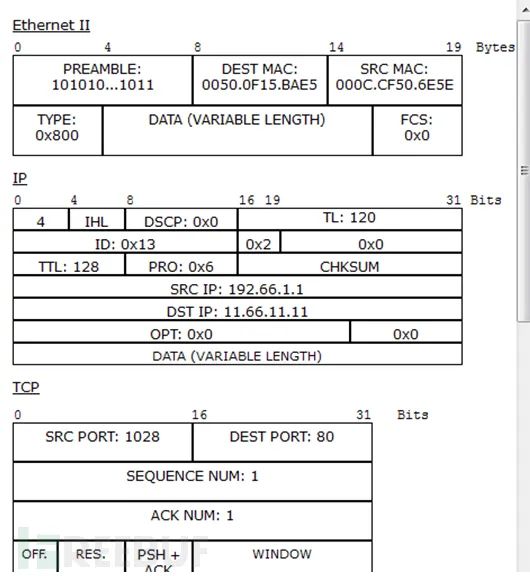
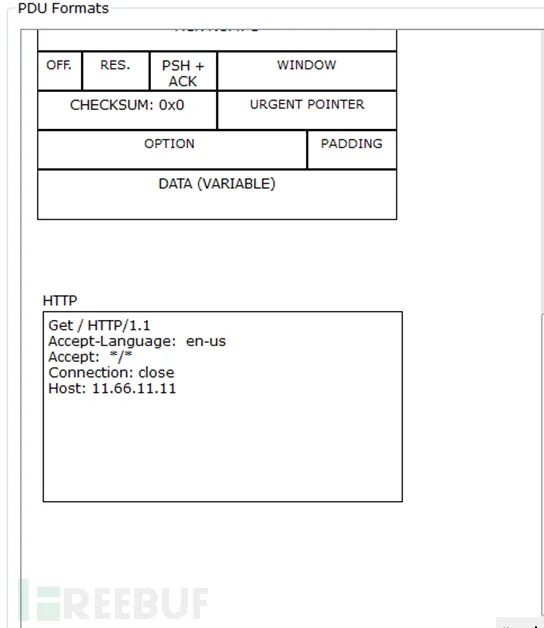 (2) HTTP response packet
(2) HTTP response packet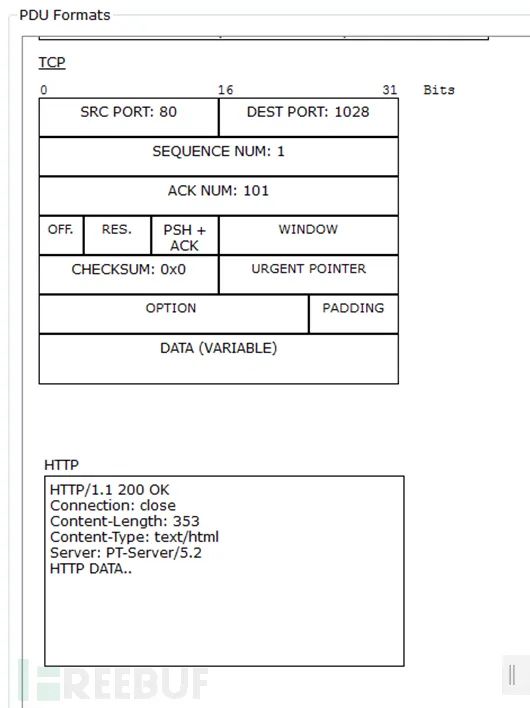
Video Tutorials
Hundreds of episodes from beginner to advanced complete video tutorials (including red-blue confrontation, CTF, network protection, and other technical points)
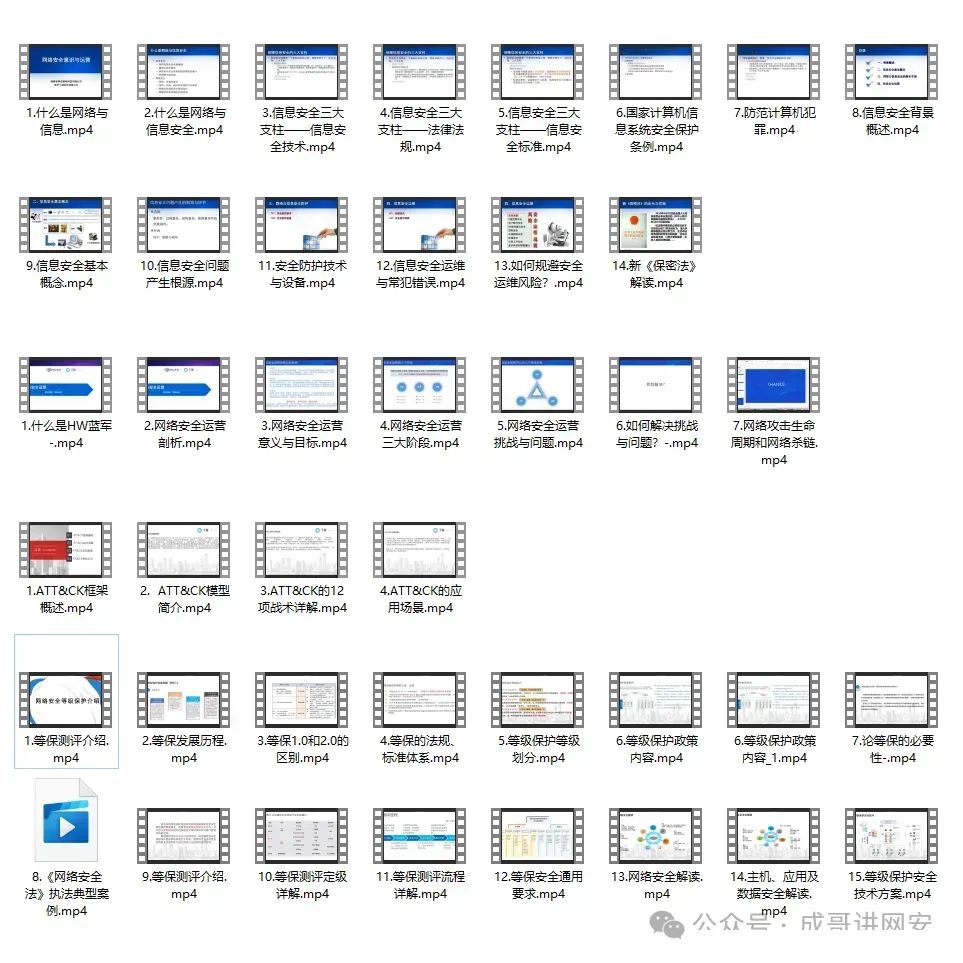
Learning Path
Complete Hacker/Cybersecurity Learning Path
If you want to learn hacking techniques, as a beginner, you must follow the roadmap to study, otherwise your efforts will be in vain. For students who have never been in contact with hacking techniques/network security, I have prepared a learning roadmap and planning from zero to proficiency. It can be said to be the most scientific and systematic learning path; following this roadmap will surely lead to success.
PDF Books
Essential books and articles for learning hacking techniques in PDF format
There are indeed too many technical books on the market; these are carefully selected by me


Installation Packages/Source Code
All tools installation packages and project source code involved in the video tutorials, etc.
Interview Questions/Experience
Due to space limitations,
only part of the materials are displayed,
and they are stillbeing updated…
How to receive them?

👆🏻Add me on WeChat and I will send it to you
After studying for a month or two, you can start finding vulnerabilities and earn bounties. After three or four months, you can reach the technical level of CTF competitions. After that, you can become a white hat hacker like me or a red hat hacker to protect the country’s network, depending on yourself.
I have been in the cybersecurity industry for many years, finding many vulnerabilities in large websites and systems, from being a white hat in big companies to leading many students in numerous network attack and defense competitions, achieving first and second places. You can hardly imagine that I also learned through self-study; this material is an accumulation of my years of continuous cybersecurity experience, covering various video tutorials and tool resources from beginner to advanced, which can definitely help you become an excellent white hat hacker, whether you are a beginner or have some technical foundation.

👆🏻Add me on WeChat and I will send it to you