▲ Click the above Leifeng Network to follow


Proactive security, extensive enterprise deployment, LoRa’s five major advantages make it a globally applicable IoT technology.
This article is reprinted from | Network Optimization Mercenary
The IoT revolution is in full swing, with various LPWAN technologies emerging rapidly, all eager to seize a foothold.
LoRa, as one of the earliest commercial LPWAN technologies, has been deployed in 95 countries globally, with over 500 alliance members. Domestically, Alibaba has announced a comprehensive push for LoRa coverage and popularization, with Alibaba Cloud IoT collaborating with several broadcasting operators to begin building city-level LoRa full network coverage.
However, many people still find this technology unclear. This article aims to discuss the unique advantages of LoRa from the three key aspects of IoT: “application,” “connectivity,” and “security. “
Application: Rapid Popularization in Smart Cities and Communities
1. Why can LoRa rapidly popularize and land?
Customers are willing to pay.
The IoT is hotly discussed, but for customers, which applications are essential? Which are optional? Is it a timely help, or just a nice addition?
The answer is straightforward: IoT applications that help customers save money, make money, ensure personal safety, provide social convenience, and maintain social stability are certainly timely help, while convenient and fun applications are just nice additions.
Case 1: Putuo Smart City Brain. When a garbage bin is full, the gas at home is not turned off, or the manhole cover is not properly placed, the alarm device immediately reports to the relevant departments; if a vehicle is parked in the fire lane for more than 5 minutes, the magnetic sensor automatically alarms… In Putuo District, 41 IoT application scenarios and 90,000 sensors are spread across 5.5 square kilometers, collecting data to the city brain for real-time analysis and judgment, generating disposal processes, automatically dispatching orders, integrating police, traffic police, urban management, market, city appearance, and sanitation forces for timely disposal, making the city more orderly, safer, and cleaner.
Case 2: Smart Dream Town. In the Dream Town of Yuhang District in Hangzhou, a LoRa network is deployed based on Alibaba Cloud IoT’s Link WAN platform to provide urban management services. In the first phase of the delivered project, LoRa technology provides convenient services in environmental sanitation, smart parking, and manhole cover monitoring for town managers and residents.
Operators can make money.
Can isolated IoT applications make money? That is a big question mark. For operators, application providers, etc., the larger the scale of IoT connections, the greater the value, and this principle is self-evident.
Case 3: Shanghai Oriental Pearl transforms into a smart city service provider. Using LoRa technology, it undertakes the implementation and operation of smart solutions in six districts of Shanghai, utilizing LoRa technology to comprehensively sense urban firefighting, community safety, and lonely elderly people in the city, and through events, link relevant departments to accelerate disposal processes, helping the city government improve work efficiency and providing citizens with better services.
For broadcasting companies, LoRa is currently the most suitable IoT technology. On one hand, the spectrum resources of broadcasting companies can fully support LoRa networks, and the low cost, mature industry, and easy deployment characteristics of LoRa also completely meet the urgent needs of broadcasting companies to enter digital city construction across various regions. According to current public information, Beijing Gehua Cable, Oriental Pearl, Huashu Media, and Sichuan Broadcasting Network have announced deep cooperation with Alibaba Cloud IoT in LoRa network and IoT services. Both parties will quickly and cost-effectively build IoT networks based on spectrum resources and the full chain of IoT resources.
2. LoRa has unique value in becoming enterprise-level WiFi.
Like other LPWAN technologies, LoRa possesses characteristics such as wide coverage, large connections, low power consumption, and low cost, making it widely applicable in various scenarios.
What differentiates LoRa from other LPWAN technologies is its ease of deployment, autonomy, and security. Through various commercial implementations domestically and internationally, we can assert that LoRa is more suitable for enterprise users who have high demands for autonomy and rapidity, as well as continuous and deep coverage scenarios, such as parks, factories, mines, farms, logistics hubs, complexes, and residential communities.
Application is crucial, connectivity is fundamental; what is special about LoRa’s connectivity?
Connectivity: Suitable for Enterprise Private Network Deployment
Speaking of connectivity, the special feature of LoRa is its network architecture, which is innovative, simple, and flexible, and optimizes the common characteristics of LPWAN such as large connections, wide coverage, low power consumption, and low cost.
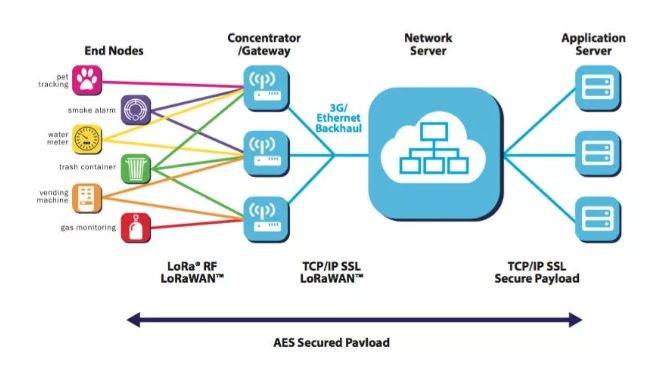
As shown in the figure, the LoRa network architecture consists of four parts: terminal nodes, gateways, network servers, and application servers.
Most networks adopt a mesh topology, which is easy to continuously expand the network scale, but the drawback is that it uses various unrelated nodes to forward messages, resulting in convoluted routing, increasing system complexity and total power consumption.
However, LoRa adopts a star topology, where gateways star-connect terminal nodes, but terminal nodes are not bound to a unique gateway. Instead, the uplink data from terminal nodes can be sent to multiple gateways.
The benefits of LoRa’s star topology are three:
1) Simple structure, flexible deployment.
The star topology structure is simple, with flexible gateway selection and deployment, and low latency. Since wireless systems are very complex and depend on the environment, deploying a network without any experience will inevitably encounter many troubles, consuming a lot of time and effort; thus, simplifying integration and flexible network deployment methods are the development trend, which is also the design intention of LoRa.
2) Optimizing performance such as power consumption, coverage, and capacity.
The star topology allows intelligent, complex, and power-hungry tasks to be handled by gateways/network servers, extending the battery life of terminals; gateways execute adaptive data rates, adapting to the rates and power of different terminal nodes to achieve maximum network capacity and longest terminal battery life; at the same time, compared to mesh topology, star topology reduces synchronization overhead and hops, further lowering power consumption.
3) When terminal nodes are in motion, no need to switch between gateways, which is beneficial for applications such as asset tracking.
From the perspective of network architecture, LoRa, in addition to having wide coverage, low cost, low power consumption, low rate, and high security like all other LPWAN technologies, also harbors a dream of being “small, fast, and flexible.” It is suitable for enterprise private network deployment, allowing for self-deployed gateways covering several kilometers, and also considers large public network deployments similar to mobile networks.
Technology: LoRa’s Five Major Advantages Make It a Globally Applicable IoT Technology
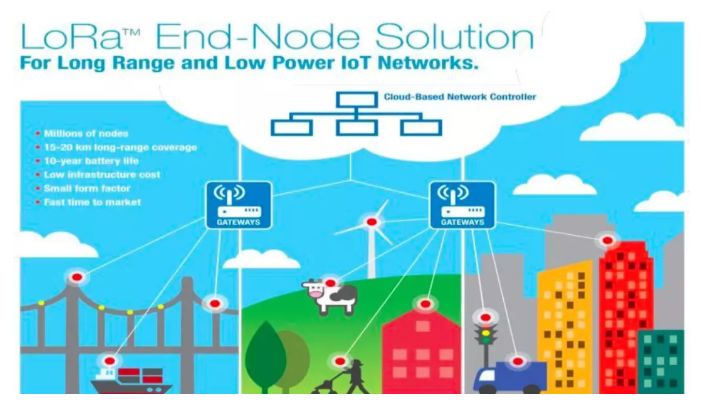
First is wide coverage. The coverage distance of a single LoRa gateway is usually within 3-5 km, and can exceed traditional cellular networks in complex urban environments, reaching over 15 kilometers in open areas, and under specific conditions can successfully cover up to 100 kilometers.
Second, low power consumption allows battery power to last for several years or even over a decade.
Third, high capacity. GSM base stations typically connect a few thousand devices, while home WiFi gateways often have less than 20 terminal connection capabilities. LoRa gateways, benefiting from the terminal’s non-connection state, can provide connections for over 20,000 terminals.
Fourth, the communication cost of the network is extremely low, while also supporting narrowband data transmission.
In addition to the above four points, this article focuses on the fifth point: security.
“Proactive Security Design” as a Technical Highlight
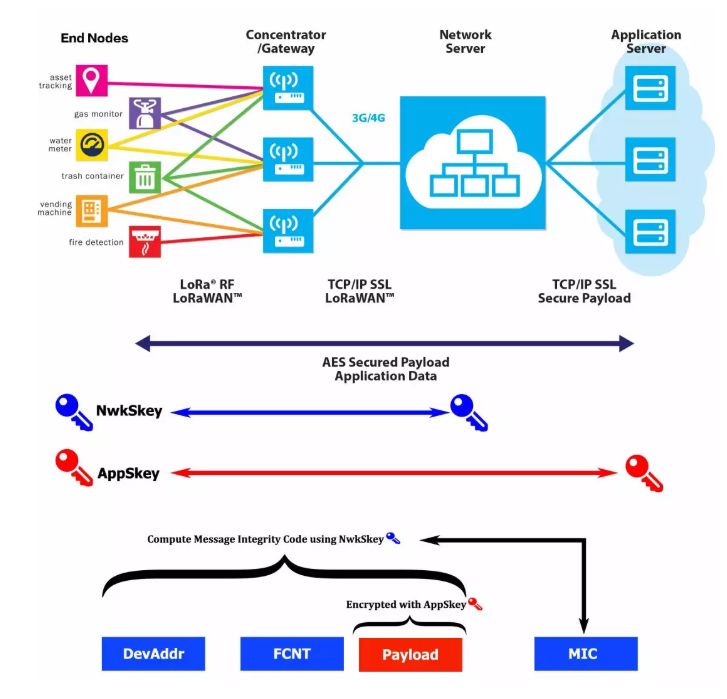
As shown in the figure, LoRaWAN has two security layers: network layer security and application layer security, using NwkSKey and APPSKey session keys to encrypt and protect all network data traffic.
• NwkSKey is used to encrypt the MAC layer payload during transmission between the terminal and the network, which is used to calculate the Message Integrity Code (MIC) to prevent fake messages and verify terminal nodes, achieving network layer security.
• AppSKey is used for end-to-end encryption of application payloads between the terminal and the application server, achieving application layer security and ensuring that network operators cannot access the application data of terminal users.
The end-to-end encryption mechanism of LoRaWAN ensures that only entities holding keys and authorized can access application data, preventing application data from being eavesdropped, protecting data integrity and privacy.
In addition, MAC also uses a frame counter (Frame Counter, FCNT) to ensure that a frame already received is not received again, which can avoid replay attacks.
How are NwkSKey and AppSKey generated? Next, we will discuss the OTAA activation process of LoRa terminals.
The OTAA activation process, also known as the network joining process, generates each device’s NwkSKey, DevAddr, and AppSKey before sending actual data.
Before understanding this process, let’s first understand a root key called AppKey. Each LoRa terminal has a unique 128-bit AppKey, from which AppSKey and NwkSKey are generated.
The process is as follows:
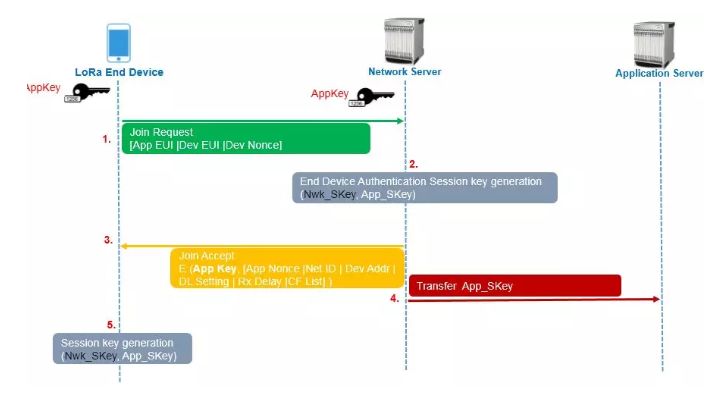
1) Join Request
The terminal device sends a Join Request message (signed with AppKey), which contains the following information: AppEUI, DevEUI, and DevNonce.
DevEUI uniquely identifies the terminal device, akin to the device’s MAC address; AppEUI uniquely identifies the application provider, such as garbage monitoring applications and smart streetlights, which each have their unique ID; AppKey is assigned to the terminal by the application program owner.
DevNonce is a random number containing 2 bytes. During a session period, the network server tracks the DevNonce value to ensure it is never reused. If the network server detects it, that Join Request will be discarded, effectively preventing replay attacks.
2) Authentication and Session Key Generation
After receiving the Join Request, the network server first performs a replay attack prevention process based on the DevNonce. If it detects a reused DevNonce value, it determines that the message is invalid, and the joining process fails; if the message is valid, the network server authenticates the terminal device using the MIC value. If the terminal device passes authentication, the network server generates AppSKey and NwkSKey.
3) Join Accept
The Join Accept message contains AppNonce, NetID, terminal address DevAddr, transmission delay RxDelay, etc. AppNonce is a random number generated by the network server for generating AppSKey and NwkSKey session keys for the terminal.
4) Transmit AppSKey
Since AppSKey is designed to protect end-to-end communication between terminal devices and application servers, it should be transmitted from the network server to the application server.
5) Session Key Generation
After the terminal receives the Join Accept message (encrypted with AppKey), it decrypts it and extracts parameters to generate session keys AppSKey and NwkSKey.
If you read it carefully again, you will find that throughout the process, no keys are sent over the air; only the missing parts needed for calculation on both sides are exchanged, ensuring that no traffic interception can generate any keys.
However, this design still has flaws; since AppSKey and NwkSKey are generated from the same AppKey, there is a risk of AppKey leakage.
However, this issue has been further addressed in the new version of the LoRaWAN protocol (1.1), which uses two different root keys (NwkKey and AppKey) to generate multiple sets of isolated session keys, ensuring encryption of both the protocol link and application link. At the same time, LoRa network service providers, such as Link WAN, use hardware encryption-based key management systems to protect keys, enhancing the security of server-side keys.
Overall, LoRa possesses features such as end-to-end encryption, two-way authentication, and integrity protection in terms of security, effectively preventing eavesdroppers and rogue devices, demonstrating comprehensiveness and foresight in security design.
However, there is no absolutely secure network; even authorized frequency band cellular networks are at risk of fake base station attacks. In this world, there are only the most economically reasonable networks, especially for IoT, where low-power connections often have T (Thing) characteristics that are price-sensitive, with low computing performance and small size, making security challenges even more daunting.
LoRa should rely on its open standards, allowing everyone to inspect and verify whether there are security vulnerabilities, just like the security of Android phones comes not only from Google’s open-source nature but also from the polishing and security enhancements provided by various mobile brands, collectively promoting a secure and inclusive intelligent interconnected era.
Finally, a Summary for the Lazy
1) LoRa has widespread applications that everyone can use. IoT applications should identify essential needs, integrate isolated systems, and leverage scale value.
2) LoRa features flexible scalability, capable of being large or small, which is needed during the growth and exploration phase of the IoT industry, making it arguably the most suitable technology for IoT.
3) LoRa is secure and reliable, with features such as two-way authentication, end-to-end encryption, and integrity protection, demonstrating comprehensiveness and foresight in security design. However, IoT security cannot be overlooked and requires continuous efforts from the industry.
– END –
◆ ◆ ◆
Recommended Reading