
Basic Concepts

HTTP (HyperText Transfer Protocol) is an application layer protocol used for distributed, collaborative, and hypermedia information systems. In simple terms, it is a method for publishing and receiving HTML pages, used to transfer information between web browsers and web servers.
HTTP operates by default on TCP port 80, and websites accessed with http:// are standard HTTP services.
The HTTP protocol sends content in plaintext and does not provide any means of data encryption. If an attacker intercepts the transmission between the web browser and the web server, they can directly read the information. Therefore, HTTP is not suitable for transmitting sensitive information such as credit card numbers, passwords, and other payment information.
HTTPS (Hypertext Transfer Protocol Secure) is a transmission protocol for secure communication over a computer network. HTTPS communicates via HTTP but uses SSL/TLS to encrypt data packets. The main purpose of developing HTTPS is to provide authentication of the web server and to protect the privacy and integrity of exchanged data.
HTTPS operates by default on TCP port 443, and its workflow generally follows these steps:
-
1. TCP three-way handshake
-
2. Client verifies the server’s digital certificate
-
3. DH algorithm negotiates the symmetric encryption algorithm key and hash algorithm key
-
4. SSL secure encrypted tunnel negotiation is completed
-
5. Web pages are transmitted in an encrypted manner, using the negotiated symmetric encryption algorithm and key to ensure data confidentiality; the negotiated hash algorithm is used for data integrity protection, ensuring that data is not tampered with.
As of June 2018, 34.6% of the top 1 million websites ranked by Alexa used HTTPS as the default, with 43.1% of the 141,387 most popular websites on the internet implementing secure HTTPS, and 45% of page loads (according to Firefox records) using HTTPS. In March 2017, only 0.11% of registered domain names in China used HTTPS.
According to Mozilla statistics, since January 2017, more than half of website traffic has been encrypted.

Differences Between HTTP and HTTPS

-
HTTP transmits data in plaintext, making it less secure, while HTTPS (SSL + HTTP) encrypts the data transmission process, providing better security.
-
Using the HTTPS protocol requires obtaining a certificate from a CA (Certificate Authority). Generally, free certificates are rare, so there is usually a cost involved. Certificate issuing authorities include Symantec, Comodo, GoDaddy, and GlobalSign.
-
HTTP page response speeds are faster than HTTPS because HTTP uses a TCP three-way handshake to establish a connection, requiring the exchange of 3 packets, while HTTPS requires 12 packets in total (3 for TCP and 9 for SSL handshake).
-
HTTP and HTTPS use completely different connection methods and ports; the former uses port 80, while the latter uses port 443.
-
HTTPS is essentially HTTP built on top of SSL/TLS, which means that HTTPS consumes more server resources than HTTP.

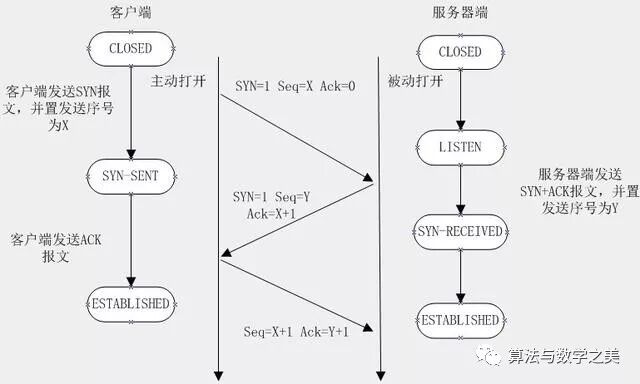
TCP Three-Way Handshake

In the TCP/IP protocol, the TCP protocol establishes a reliable connection through a three-way handshake.
-
First handshake: The client attempts to connect to the server by sending a SYN packet (Synchronize Sequence Numbers), syn=j, and the client enters the SYN_SEND state waiting for server confirmation.
-
Second handshake: The server receives the client’s SYN packet and acknowledges it (ack=j+1), while sending a SYN packet (syn=k) back to the client, forming a SYN+ACK packet. The server then enters the SYN_RECV state.
-
Third handshake: The client receives the server’s SYN+ACK packet and sends an acknowledgment packet ACK (ack=k+1) back to the server. Once this packet is sent, both the client and server enter the ESTABLISHED state, completing the three-way handshake.
In summary:

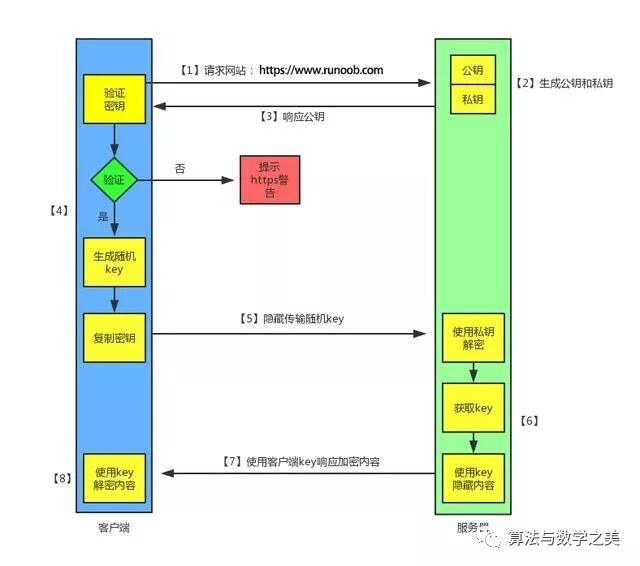
Working Principle of HTTPS

We all know that HTTPS can encrypt information to prevent sensitive data from being accessed by third parties. Therefore, many banking websites and high-security services such as email use the HTTPS protocol.
01
Client initiates an HTTPS request
This is straightforward; the user enters an https URL in the browser and connects to the server’s port 443.
02
Server configuration
Servers using the HTTPS protocol must have a digital certificate, which can be self-signed or obtained from an organization. The difference is that self-signed certificates require client validation to continue access, while certificates from trusted companies do not prompt warning pages (startssl is a good choice, offering 1 year of free service).
This certificate is essentially a pair of public and private keys. If you don’t understand public and private keys, think of them as a key and a lock. Only you have the key, and you can give the lock to others. They can use this lock to secure important items and send them to you, as only you can unlock it with your key.
03
Certificate transmission
This certificate is essentially the public key, containing various information such as the issuing authority and expiration date.
04
Client parses the certificate
This part is handled by the client’s TLS, which first verifies the validity of the public key, such as the issuing authority and expiration date. If any issues are found, a warning box will pop up indicating a problem with the certificate.
If the certificate is valid, a random value is generated and encrypted with the certificate, similar to locking the random value with a lock. Unless someone has the key, they cannot see the locked content.
05
Transmission of encrypted information
This part transmits the random value encrypted with the certificate, allowing the server to receive this random value. Future communication between the client and server can be encrypted and decrypted using this random value.
06
Server decrypts the information
The server uses the private key to decrypt the random value sent by the client. It then uses this value for symmetric encryption, meaning that the information and private key are mixed together using a specific algorithm. Unless someone knows the private key, they cannot access the content. Since both the client and server know this private key, as long as the encryption algorithm is robust and the private key is complex, the data remains secure.
07
Transmission of encrypted information
This part contains the information encrypted with the server’s private key, which can be decrypted on the client side.
08
Client decrypts the information
The client uses the previously generated private key to decrypt the information sent by the server, thus obtaining the decrypted content. Throughout this process, even if a third party intercepts the data, they are powerless.
END
∑ Edited by | Gemini
Source | International Education
More Exciting Content:
☞ Harmonic: How to Conduct Mathematical Research
☞ Mark Zuckerberg’s 2017 Harvard Commencement Speech
☞ Applications of Linear Algebra in Combinatorial Mathematics
☞ Have You Ever Seen the Real Phillips Curve?
☞ The Story of Support Vector Machines (SVM)
☞ Is the Mathematics in Deep Neural Networks Too Difficult for You?
☞ How Much Mathematics Knowledge is Needed for Programming?
☞ Shing-Tung Yau – What is Geometry?
☞ A Brief Overview of Various Dimensionality Reduction Algorithms
☞ The Theory of Surfaces
☞ What is the Significance of the Natural Base e?
☞ How to Explain Support Vector Machines (SVM) to a 5-Year-Old?
☞ Chinese-American Mathematical Genius Terence Tao’s Self-Description
☞ Algebra, Analysis, Geometry, and Topology: The Three Major Methodologies of Modern Mathematics

We welcome submissions to the WeChat public account “The Beauty of Algorithm Mathematics”
Submissions should involve mathematics, physics, algorithms, computer science, programming, and related fields. Accepted submissions will be rewarded.
Submission email: [email protected]