Follow us for free subscriptions to avionics news

Abstract
This research focuses on the embedded data security technology based on Trusted Execution Environment (TEE) for avionics systems, which have high real-time requirements, limited hardware resources, and weak data and task security protections. The security reinforcement targets three stages of the data lifecycle in embedded systems: data storage, data transmission, and data usage. Utilizing the unique data isolation characteristics of the TEE environment, the proposed algorithm isolates encryption algorithms in data storage, signature verification procedures in data transmission, and sensitive data and applications during data usage from the general execution environment. This ensures that different tasks can securely and reliably process critical data while simplifying the encryption algorithms used, thus maintaining good real-time performance under hardware resource constraints. Simulation results demonstrate that the proposed algorithm has high security and reliability, outperforming previous methods in terms of failure rates.
Keywords
TEE; Embedded Systems; Data Security; Avionics Systems


1 Introduction
With the development of intelligence and openness in embedded systems, the complexity of aircraft operations has increased, and the interactive data has become more complex in terms of type, size, and security level. The data security issues and threats faced are becoming increasingly prominent. Avionics embedded systems face multiple dimensions of data security threats, with various parties holding different sensitive data. Achieving secure storage, transmission, and usage of data while ensuring data security poses a significant challenge to traditional boundary defenses primarily based on encryption. The information sharing risks faced by avionics embedded systems mainly arise from multi-machine collaborative tasks in cooperative scenarios, necessitating the trusted isolation characteristics of TEE to enhance the collaborative trust capabilities between aircraft.
To improve the security and trust capabilities of avionics embedded systems, the research on embedded data security technology focuses on two aspects: data storage and data transmission. From the perspective of data storage, Han Kang et al. designed a solution that combines encryption algorithms to reduce data computation while ensuring data security, considering the limited computing resources of avionics. Yang Shihao proposed a design method for a high-security, high-reliability data storage module for avionics, ensuring the high security and reliability of the data storage module. From the perspective of data transmission, Hao Yucuo et al. selected a compact and flexible embedded signal processing architecture, implementing cryptographic algorithms on Field Programmable Gate Arrays (FPGA) for efficient secure transmission of avionics information. Yang Jia et al. proposed security technologies applicable to core data protection against network threats during data transmission, thereby protecting the confidentiality, integrity, and availability of data.
Although the above studies have improved the confidentiality of current avionics embedded data and optimized performance, the isolation between different tasks during data usage is insufficient. Internal management issues or misconfigurations may lead to data theft or sensitive information leakage between tasks, indicating a need for enhanced security protection capabilities. Chen Senhao proposed a TEE-based security protection method from the perspective of protecting critical modules of drones, focusing on the integrity of critical modules. However, this method only addresses the security of the drone’s power module and cannot be deployed comprehensively in avionics embedded systems.
To address data security threats, this paper designs a TEE-based avionics embedded data security model, which includes the following three modules.
Data Encryption and Decryption Module. This module addresses the data storage security issue and provides the encryption foundation for the data transmission and data usage security modules. Based on TEE’s protection mechanism, a lightweight data encryption algorithm is adopted to improve encryption and decryption efficiency while saving software and hardware resources.
Data Transmission Security Module. This module ensures the security of data during transmission and provides necessary transmission functions for the data usage security module. Based on traditional key negotiation algorithms, a signature verification procedure is deployed in TEE to prevent eavesdropping and tampering risks during transmission.
Data Usage Security Module. Leveraging TEE’s isolation properties, this module implements multi-level protection of sensitive information from hardware to software, focusing on isolating sensitive data and critical interfaces in avionics embedded systems to prevent interference from other unauthorized programs or tasks during data usage, ensuring data and task isolation.
The TEE-based avionics embedded data security model ensures the security of avionics data and the isolation of critical modules, guaranteeing data security from three dimensions and undergoing system testing and validation. Compared to previous security protection technologies, this model offers high security and good real-time performance, better protecting sensitive data in avionics embedded systems.

2 TEE-Based Avionics Embedded Data Encryption and Decryption Module
2.1 Basic Design Concept
In traditional data encryption and decryption algorithms, asymmetric encryption algorithms are complex and secure but require high computational power, while symmetric encryption algorithms are the opposite. To solve the avionics data storage security issue while ensuring encryption and decryption efficiency, this paper designs a TEE-based avionics embedded system data encryption and decryption module. The basic design concept is to ensure security through the isolation environment of TEE, replacing the traditional asymmetric encryption algorithm RSA with a lightweight symmetric encryption algorithm: the access control mechanism from the Rich Execution Environment (REE) to TEE, combined with the Advanced Encryption Standard (AES), completes data encryption and decryption. The key length of the AES algorithm is set to 128 bits, and the model design structure is shown in Figure 1.
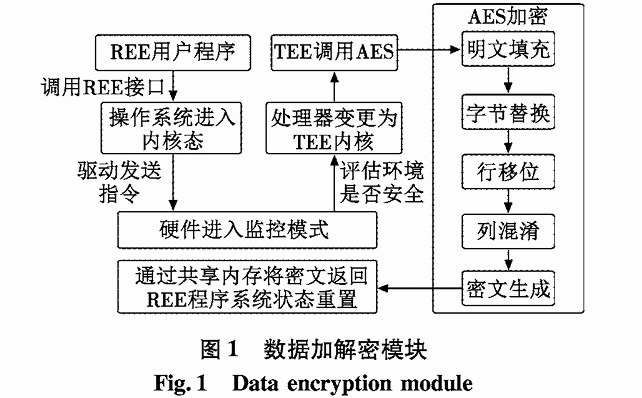
REE initiates a call to TEE through hardware evaluation, completing AES encryption and returning the ciphertext to the application on the REE side. Due to the characteristics of AES symmetric encryption, the decryption process is the inverse operation of encryption, which includes ciphertext grouping, inverse column mixing, inverse row shifting, inverse byte substitution, and padding removal. After decryption, TEE also returns the plaintext to the REE side application via shared memory.
2.2 Principle Analysis
2.2.1 Security
In the general execution environment, there is a lack of isolation between different tasks in avionics embedded systems, and keys generated using the AES algorithm or asymmetric encryption algorithm (RSA) may be illegally stolen by other tasks. While RSA avoids the risk of key cracking caused by direct transmission of symmetric keys to some extent, it still poses a risk of private key theft in a mixed execution environment. Therefore, it is necessary to deploy TEE-based encryption algorithms to protect keys. In Figure 1, the keys used for encryption and decryption are protected in the isolated environment of TEE, and access to the AES encryption module can only occur through a specific calling process, ensuring key security. Thus, it can be concluded that the security of the TEE-based AES algorithm is not lower than that of RSA.
2.2.2 Performance
In terms of time complexity, the number of rounds in the AES algorithm is fixed, so both the encryption and decryption processes of the AES algorithm have a constant time complexity of O(N), where N is the size of the data block. In contrast, the encryption and decryption processes of RSA involve large prime modulus operations, and during decryption, a large private key is used, leading to low efficiency due to the large exponent. The time complexity of RSA encryption and decryption can be approximated as O(log:N). Under the same time conditions, the decryption file size for AES is in the MiB range, while for RSA, it is only in the KiB range, resulting in a significant difference in decryption speed.
The access scheduling time from REE to TEE is influenced by hardware (processor performance, TEE implementation) and software (trusted software base, communication overhead). Generally, for data transfers under 1MB, TEE access can achieve a response time in the millisecond range, which is much shorter than the time required for a single encryption and decryption operation.
In summary, the algorithm proposed in this paper eliminates the time and resource-consuming asymmetric encryption algorithms, achieving lightweight encryption and decryption through calls and data transfers between REE and TEE. As the data volume increases, the time difference between this algorithm and traditional RSA encryption becomes increasingly evident, with a time complexity ratio of 0(N):0(10gN). Due to the security isolation characteristics of TEE, the data encryption and decryption module also ensures the security of the most vulnerable key transfer link of the AES algorithm. During decryption, the REE-side user must first apply to enter TEE through the same path to decrypt the encrypted data, ensuring the security of the entire encryption and decryption process.

3 TEE-Based Avionics Embedded Data Transmission Security Module
3.1 Design Concept
The traditional data transmission process includes three parts: establishing a connection, key negotiation, and data transmission. However, for avionics embedded systems, internal data transmission between modules typically does not require the connection establishment process. Therefore, this paper primarily focuses on the design of the key negotiation and data transmission modules.
The key negotiation mechanism allows both communication parties to establish a session key while avoiding the risk of data being intercepted during transmission. There are many methods to implement key negotiation, including: 1) using asymmetric encryption algorithms for key negotiation; 2) relying on a pre-shared “secret” between the two parties; 3) using dedicated key negotiation algorithms. Among these, method 1) takes too long to generate keys, and method 2) is not suitable for avionics platforms. Therefore, this paper starts with the Diffie-Hellman key exchange protocol (D-H algorithm) to design the key negotiation module in conjunction with TEE to ensure secure transmission.
The D-H algorithm can create a key over an insecure channel without prior information from either party. This paper designs a TEE-based platform data transmission security module, as shown in Figure 2.
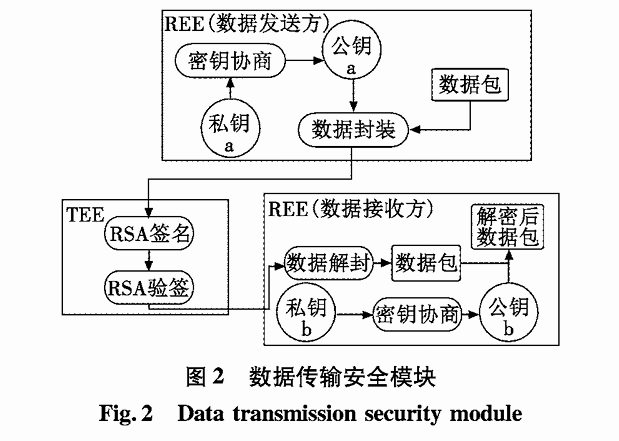 In Figure 2, the key negotiation algorithm follows the traditional D-H algorithm, where both parties generate public keys based on their private keys, with the encrypting party using its private key for encryption and the decrypting party using the public key for decryption.
In Figure 2, the key negotiation algorithm follows the traditional D-H algorithm, where both parties generate public keys based on their private keys, with the encrypting party using its private key for encryption and the decrypting party using the public key for decryption.



4 TEE-Based Avionics Embedded Data Usage Security Module
4.1 Design Concept
In the entire lifecycle of data from generation to destruction, data usage security is currently the weakest link in avionics embedded data security. This is mainly reflected in the difficulty of ensuring the security of user identity and usage environment, necessitating enhanced security protection. Based on this background, this paper designs a TEE-based avionics embedded data usage security module, as shown in Figure 3.
In Figure 3, TEE and REE are isolated through hardware and software, preventing REE from accessing the hardware-protected TEE memory. Each partition has its own operating system and resources, ensuring memory partitioning by prohibiting write access to memory areas beyond the partition. Inter-partition message passing is managed by the core operating system, implemented through messages, ports, or channels, with the mapping of ports and channels configured via XML files.
Since partitions in VxWorks653 operate on the same processor, if the core operating system is attacked (for example, by tampering with the XML configuration during memory allocation), it could lead to vulnerabilities being accessible across partitions, allowing for modifications to partition attributes, modes, states, etc. The data usage security module designed in this paper isolates at the hardware level, ensuring that applications on the REE side can only access critical data through resource access interfaces isolated within TEE, achieving true data availability without visibility.
In summary, the isolation technology based on TEE can prevent illegal intrusions and data theft between tasks, ensuring that multiple data users can access their data in an isolated environment while maintaining availability without visibility.
In summary, the isolation technology based on TEE can prevent illegal intrusions and data theft between tasks, ensuring that multiple data users can access their data in an isolated environment while maintaining availability without visibility.
5 Simulation Experiments and Analysis

5.1 Performance Testing of the Data Encryption and Decryption Module
The data encryption and decryption module designed in this paper can ensure the security of the encryption and decryption process functionally, while also extending the time for information transfer between REE and TEE, improving the computational speed of the encryption algorithm. For the entire encryption and decryption process, which includes the time for data transfer and the time for data encryption and decryption, this paper primarily compares the efficiency of encryption and decryption based on total time consumption, comparing it to the RSA encryption algorithm without TEE protection.
The size of a single data packet is set to range from 16B to 16384B, testing the number of encryptions and decryptions performed by different algorithms within 3 seconds, as shown in Figure 5. As seen in Figure 5, although the algorithm in this paper does not achieve as high an encryption efficiency as RSA for 16B data packets, starting from 64B, the number of encryptions performed by this algorithm (328) within 3 seconds exceeds that of RSA (232). As the packet size increases, the algorithm demonstrates stable performance, achieving 94 encryptions and decryptions within 3 seconds for a 16KiB data packet, while RSA can only complete one encryption and decryption under the same conditions, proving the effectiveness of the proposed algorithm.


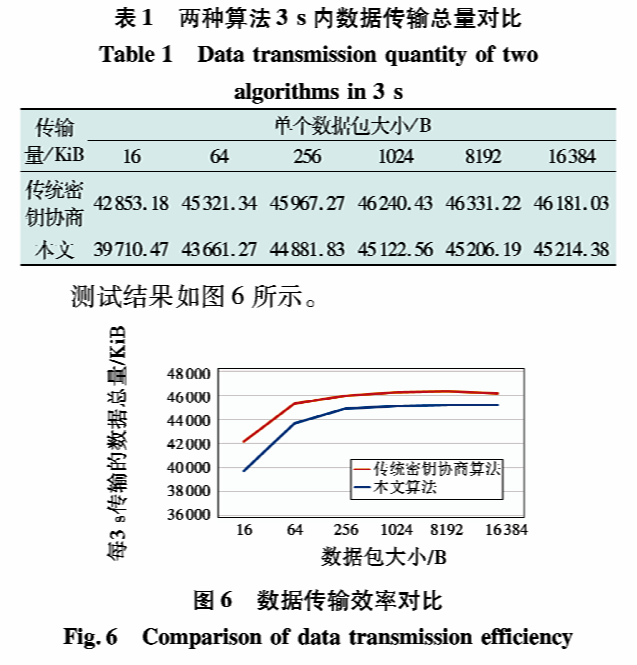 According to the tests, the total amount of data transmitted by the proposed algorithm within 3 seconds, while ensuring security, is slightly reduced compared to traditional key negotiation algorithms, with the reduction ranging from 2% to 6% as the size of the individual data packets changes. Analysis shows that as the packet size increases, the number of access transfers between REE and TEE decreases while maintaining the total data volume, leading to improved data transmission efficiency. The proposed algorithm reduces the efficiency gap with traditional key negotiation algorithms, thus concluding that it can ensure security during the transmission process without affecting the completion of routine tasks in avionics embedded systems.
According to the tests, the total amount of data transmitted by the proposed algorithm within 3 seconds, while ensuring security, is slightly reduced compared to traditional key negotiation algorithms, with the reduction ranging from 2% to 6% as the size of the individual data packets changes. Analysis shows that as the packet size increases, the number of access transfers between REE and TEE decreases while maintaining the total data volume, leading to improved data transmission efficiency. The proposed algorithm reduces the efficiency gap with traditional key negotiation algorithms, thus concluding that it can ensure security during the transmission process without affecting the completion of routine tasks in avionics embedded systems.
6 Conclusion
This paper conducts research on avionics embedded data security technology based on TEE technology. Based on TEE, three data security protection modules are designed and implemented, organically integrating TEE technology with traditional data encryption, data transmission, and data usage. First, a lightweight data encryption algorithm is realized based on the isolation of TEE, then a signature is added to the traditional D-H algorithm, and finally, the entire operating environment’s security and trustworthiness is ensured through TEE, guaranteeing the security of data and interfaces during usage. Experimental results demonstrate the effectiveness of the proposed algorithm, which enhances the security capabilities of avionics data while ensuring efficiency, allowing avionics embedded systems to complete tasks reliably and securely as scheduled.
(This article is selected from “Electronics and Control” by Zhang Meng, Chen Shuizhong, Xu Kai, Zhang Zongzheng, affiliated with the National Key Laboratory of Airborne Information Perception and Fusion, China Aviation Industry Corporation, Luoyang Electro-Optical Equipment Research Institute. This article is reproduced solely for the purpose of knowledge dissemination. If there are any copyright issues, please contact us promptly!)
