
Industry is the lifeblood of a nation’s economy and a reflection of its comprehensive national strength. Currently, China is at a critical juncture in its transition from “Made in China” to “Intelligent Manufacturing in China.” Industrial Control Systems (ICS), as the core of the industrial system, are widely used in fields such as power, aerospace, water conservancy, and wind power, with over 60% of critical facilities employing ICS for automation. ICS can be divided into two conceptual domains: Information Technology (IT) and Operational Technology (OT), which are an organic combination of the two. The IT side consists of software, servers, and databases that run the system, while the OT side includes Programmable Logic Controllers (PLC), Supervisory Control and Data Acquisition (SCADA) systems, and data transmission units, among other lower-level and dedicated devices.
In recent years, with the development of industrial Ethernet and wireless interconnectivity technologies, ICS systems have gradually transitioned from a closed and isolated state to an open and interconnected one. The market share of traditional ICS systems, which relied on independent networks, proprietary hardware, and software control protocols, is shrinking, replaced by new ICS systems that utilize Ethernet and various network communication protocols such as Modbus, IEC-104, and PROFINET. However, as the level of openness increases, various network security issues have also emerged, with ransomware being a representative example of network attacks on industrial control systems. According to data from the National Industrial Information Security Situation Awareness Platform, in 2021, nearly 7 million low-protection connected devices were reported nationwide, with IoT and industrial control system devices accounting for over 80%.
This article studies ransomware attacks on ICS systems, briefly introducing the principles of ransomware and attack incidents. It then focuses on the classification, characteristics, and detection methods of ransomware, and discusses virus protection for ICS systems, aiming to provide a reference for network security protection in industrial enterprises.
1. Classification of Ransomware
After infiltrating the victim’s host, ransomware executes different attack strategies to achieve various objectives, either by encrypting the victim’s files, rendering them inaccessible, or isolating the device from the user, preventing normal usage. In recent years, ransomware attacks have shown an increasing and diversifying trend. Based on the functionality of ransomware, it can be classified into file encryption type, device locking type, system encryption type, and server encryption type; based on the system it invades, it can be classified into Windows system viruses, Linux system viruses, VMware ESXi system viruses, and Android system viruses; based on whether it is double extortion, it can be classified into double extortion, where the attacker threatens to disclose the victim’s sensitive information, and non-double extortion; based on whether it uses Ransomware as a Service (RaaS), it can be classified into viruses that provide customized ransomware services for a commission and those that do not use the RaaS model.
(1) Classification by Virus Functionality
File encryption type viruses: These viruses, upon entering the victim’s system, use various algorithms to encrypt files, specifically targeting critical files related to industrial enterprises, such as data, images, audio, video, compressed files, folders, and databases. Currently, most file encryption ransomware uses a combination of AES and RSA algorithms, encrypting the victim’s files with AES and using RSA to encrypt the AES key, allowing the attacker to retain the RSA private key, thus isolating the decryption key from the victim. Due to the characteristics of AES and RSA, which can only be broken through brute force, existing computational power cannot crack them in a short time, leaving the victim with no choice but to pay the ransom. File encryption type viruses are the main type of ransomware today. Typical examples include Play and Lockbit3.0, which operate on similar principles, encrypting files while also deleting shadow backups, controlling system processes, setting auto-start items, and using black and white lists to determine which files to encrypt and which to leave unencrypted.
Device locking type viruses: These viruses lock devices, preventing the victim from using them normally. In ICS systems, such viruses may target the IT side, locking the screen and displaying ransom messages, rendering the host unusable; or they may target the OT side, exploiting vulnerabilities and weak passwords in industrial control devices to gain control over PLCs, SCADA, and other critical industrial control devices, causing them to malfunction. Ultimately, the victim can only pay the ransom to unlock the device. EnkripsiPC is a device locking type virus that locks the victim’s screen by creating entries in the Windows registry for persistence, ensuring it starts automatically with each boot, making it unavoidable. Similar viruses include NBB and Nibiru.
LogicLocker is a device locking type virus that targets industrial PLC systems, scanning for vulnerable devices in the ICS using API interfaces, and infecting and bypassing security mechanisms to modify PLC code and lock devices, primarily targeting power plants or water treatment facilities. System encryption type viruses: These viruses encrypt system-level content, such as the master boot record and volume boot record. The master boot record is a sector that must be read when the computer accesses the hard drive after booting. Ransomware can encrypt the hard disk file allocation table and alter the computer’s master boot record, interrupting normal startup, as seen with the Petya virus. Another type of disk-level encryption virus, such as THT, encrypts and unmounts the disk using legitimate disk encryption software Best Crypt Volume Encryption after gaining control of the host.
Server encryption type viruses: These viruses encrypt files on network servers. They typically exploit known vulnerabilities in content management systems to conduct RDP attacks on publicly accessible enterprise computer server ports, rendering all software and files connected to the server unusable. Examples include mkp and master. In ICS systems, IT layer servers are generally connected to multiple devices, and the boundaries between industrial networks and communication networks are blurred, lacking network isolation. Most viruses possess worm-like capabilities, allowing them to replicate and spread across networks from IT servers to OT production networks and then to industrial control devices, ultimately affecting all devices connected to the network with communication capabilities.
(2) Classification by Invasion System
Windows system viruses: These viruses attack Windows systems by exploiting various vulnerabilities within the Windows operating system for initial infiltration, using built-in RDP and Windows Management Instrumentation (WMI) to access and control the operating system, applications, and device information. Windows systems are the primary target for ransomware infiltration. According to security assessment agency AV-Test, attacks targeting Windows systems account for approximately 95% of all attacks, which is 36 times more than the second most targeted Linux systems. Viruses targeting Linux, VMware ESXi, and other systems often have variants targeting Windows systems as well. Linux system viruses: Due to the open-source, free, customizable, and well-isolated nature of Linux systems, they are widely used in embedded systems, making Linux ransomware a key focus for industrial control system security. Unlike the diverse distribution strategies of Windows system viruses, Linux system viruses typically distribute payloads through RDP and vulnerability exploitation to obtain legitimate credentials from public services.
After infiltrating the system, Linux system viruses exploit vulnerabilities to escalate privileges, gaining root access on the victim’s host to encrypt more victim files. Unlike Windows system viruses, Linux system viruses primarily target web and cloud servers. A typical Linux ransomware example is Sodinokibi, which exploits outdated VPN devices or weak RDP passwords to infiltrate systems, using Salsa20 and RSA-2048 algorithms to encrypt files in the victim’s network and demand ransom. Other Linux ransomware includes Erebus, QNAPCrypt, and KillDisk. VMware ESXi system viruses: Due to the higher resource processing efficiency of VMware ESXi virtual machines, enterprises use ESXi to store data and host critical applications. These viruses specifically encrypt VMware ESXi virtual machines, deploying payloads through known vulnerabilities and executing them manually to gain complete management privileges or access credentials for the virtual machine monitor. After infiltrating the virtual machine, the virus moves laterally within the network to seek more victims, killing system processes and shutting down the virtual machine before encryption.
ESXi system viruses encrypt virtual machine metadata files, including files with specific extensions such as .vmdk, .vmem, and .vswp. The encryption algorithms and ransom strategies are similar to those of Windows ransomware. Cheerscrypt, ESXi Args, and fcker.py are typical ransomware targeting VMware ESXi systems. Currently, common ransomware does not limit itself to a single system for attacks but develops various targeted variants, such as LockBit and Play, which have variants for Windows, Linux, and ESXi systems.
Android system viruses: These viruses target Android smart devices, which allow users to download open-source applications through third-party platforms. Therefore, Android ransomware can launch attacks by disguising themselves as legitimate software. In addition to encrypting files, these viruses perform the following operations based on the characteristics of Android system devices: first, locking the device’s desktop screen; second, using trojans to steal critical data, such as Anubis, which obtains sensitive information through phishing pages and can block user information and remotely control devices; third, using unauthorized permissions, such as using SYSTEM_ALERT_WINDOW to display over other applications; fourth, resetting the device PIN to prevent the victim from accessing the device, as seen with Lockerpin. Similarly, CovidLock uses BIND_DEVICE_ADMIN to gain complete control over the device.
(3) Other Classifications
Based on whether it is double extortion, viruses can be classified into double extortion, where the attacker threatens to disclose the victim’s sensitive information, and non-double extortion. Double extortion emerged in 2019, referring to the practice of encrypting the victim’s files for ransom while also threatening to publicly disclose the victim’s sensitive information for additional ransom, thereby pressuring the victim to pay a higher ransom. If the victim fails to pay the ransom within the specified time, the hacker will sell and publish this sensitive information. Victims are often well-known enterprises, and from a business and reputational perspective, they are more likely to pay the ransom compared to single extortion methods. Maze was the first virus to adopt double extortion, with victims including South Korean electronics giant LG and American company Xerox, both of which refused Maze’s ransom demands, resulting in the source code for multiple LG products and Xerox customer service data being publicly disclosed.
Based on whether it uses Ransomware as a Service (RaaS), viruses can be classified into those that provide customized ransomware services for a commission and those that do not use the RaaS model. RaaS is a new commercial operation model where ransomware developers are responsible for developing and maintaining software tools and facilities, while subscribers without development capabilities pay a rental fee to directly use the ransomware for extortion. This model has greatly propelled the evolution of ransomware from a singular, simplistic approach to a modular, industrialized one.
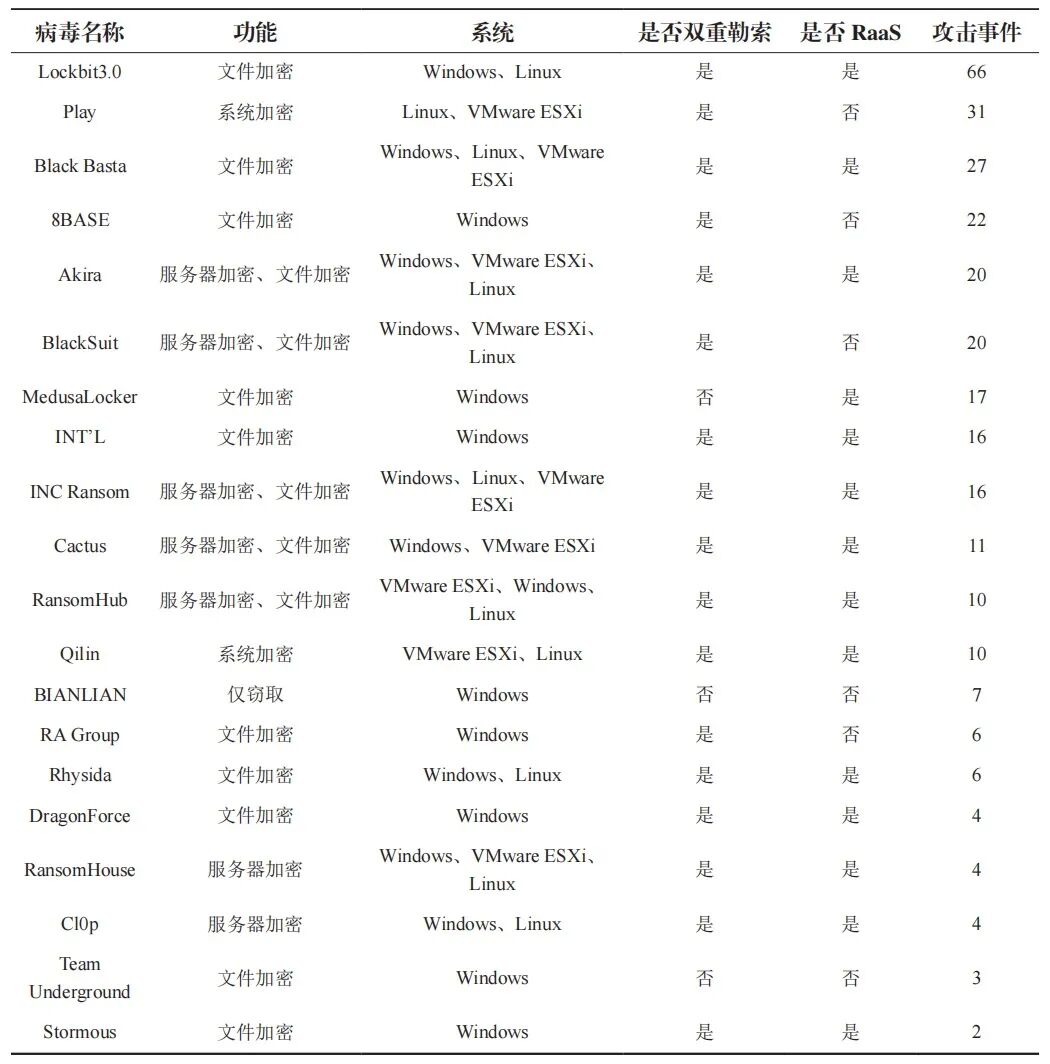
According to Dragos data, in the second quarter of 2024, there were 312 attacks against industrial enterprises involving 29 organizations. Although the ransomware recorded during this period did not specifically target the OT processes of ICS systems, it focused on attacks on the IT side, but the disruption of communication networks also affected the OT side. This article categorizes the 20 most frequently occurring ransomware attacks during this period, as shown in Table 1.
Table 1: Ransomware Attacks and Their Classifications in the Second Quarter of 2024
2. Characteristics of Ransomware in ICS Systems
(1) High Targeting and Destructive Capability
Ransomware attacks targeting ICS systems often victimize large industrial enterprises or service sectors with substantial data assets. Compared to traditional ransomware attacks targeting individual victims and non-industrial IT systems, ransomware attacks on ICS systems exhibit a strong directional focus. During the distribution phase, traditional IT ransomware primarily spreads through non-targeted phishing emails, while ICS system viruses utilize customized vulnerability tools to distribute payloads. Furthermore, traditional ransomware targets documents, photos, and other data files for encryption to demand ransom; ICS system viruses not only encrypt but also lock devices such as PLCs and RTUs or conduct logic bomb attacks to halt operations. Given that ICS systems are closely related to production, equipment and personnel safety, and public services, the damage caused by ICS ransomware is significantly greater, potentially halting industrial production, causing irreversible damage to equipment, and affecting public services such as water and electricity supply. Data from Dragos indicates that in the second quarter of 2024, major victims included internet service provider Frontier Communications (operational disruption) and the Gijón Bioenergy Plant (SCADA encryption and leakage, disruption of waste and energy management processes).
(2) Complex Encryption Algorithms and Difficult System Recovery
ICS ransomware employs increasingly complex encryption algorithms to pursue speed and quality of encryption, broadly categorized into symmetric and asymmetric encryption algorithms. Symmetric encryption algorithms use the same key for both encryption and decryption, offering advantages such as low computational load, speed, and good adaptability, but they also have the drawback of potential key leakage. AES, 3DES, and RC4 are typical symmetric encryption algorithms, with AES being the most widely used.
AES is an encryption standard adopted by the U.S. government in 2002, with key lengths of 128, 192, and 256 bits. If a 256-bit key is used, the number of possible combinations is 2^265. Even using the world’s fastest supercomputer, Frontier, with a peak performance of 1.206EFlop/s, it would take 2.629×10^51 years to compute, making AES effectively unbreakable by brute force. Asymmetric encryption algorithms use different keys for encryption and decryption, typically involving a public key for encryption and a private key for decryption. Their advantages include high security and ease of management, while their drawbacks include high computational load. Common asymmetric encryption algorithms include RSA and ECC. The principle of RSA involves multiplying large prime numbers, which is relatively easy, but its reverse factorization is extremely difficult. Due to limitations in computational resources and technical barriers, RSA, like AES, is currently unbreakable. Additionally, there are other encryption algorithms: hash algorithms, also known as hash functions, are one-way functions that take an input message and output a digest, ensuring different files produce different outputs for identification. Common hashes include MD5 and SHA; Base64 is a method of encoding bytes, converting plaintext into base64 encoding for encryption. To make encrypted files difficult to recover, ransomware employs a strategy of combining symmetric and asymmetric encryption algorithms, often using three or more encryption algorithms in combination. Well-designed viruses may also include integrated encryption modules that can switch encryption algorithms based on object and process characteristics, linking to encryption libraries such as Crypto++, MbedTLS, and libntri to select appropriate encryption algorithms for attacks.
(3) Wide Attack Paths and Diverse Attack Methods
ICS ransomware not only conducts traditional encryption attacks on communication and industrial control networks but also targets field devices, including PLCs, RTUs, and SCADA, locking devices to halt operations or launching physical attacks, such as logic attacks that damage facilities or modify parameters to deceive maintenance personnel. Additionally, it may attack communication protocols used in ICS systems, such as Modbus, PROFINET, and ZigBee, exploiting differences in security mechanisms for data integrity and availability to conduct data injection and DoS attacks, or leveraging the lack of request limits in ZigBee networks to perform flood attacks.
In recent years, many new attack methods and tools have emerged, such as off-ground attacks and supply chain attacks. Off-ground attacks utilize the target victim’s own resources, such as scripts, software, and payloads, to launch attacks, representing a no-payload deployment attack that reduces traces of the attack, making detection and defense more challenging. Supply chain attacks refer to infections of services or products provided by upstream suppliers, leading to ransomware infiltration in downstream enterprises. Compared to isolated security attacks, supply chain attacks are larger in scale and have more severe impacts. In 2023, a supply chain attack targeting Progress’s MOVEit tool led to ransomware affecting three major industrial controller manufacturers across 32 countries and over 2,000 enterprises. It is also important to note that as attack methods and tools evolve, the techniques for virus reverse analysis and evasion have also improved, with common anti-analysis and evasion techniques such as code obfuscation and packing, polymorphism and metamorphism, anti-virtualization, anti-debugging, and anti-API hooking complicating the detection and protection of ICS system viruses.
3. Detection and Identification of Ransomware Attacks on ICS Systems
The existing security mechanisms for ICS systems are reactive, but due to the heterogeneous nature of ICS systems and the continuous enhancement of ransomware reverse analysis and evasion techniques, many industrial enterprises are unaware of potential hidden attacks within their systems. Their security devices and confidential data may be unknowingly compromised and leaked, thus raising the requirements for detection and identification methods for ransomware. Existing methods include: (1) signature-based static detection, which identifies unique signatures that can identify viruses by extracting static parameters such as keywords and suspicious function calls from virus samples; (2) behavior-based dynamic detection, which analyzes and identifies the behavioral characteristics of viruses during their execution, utilizing behavioral features such as file types and malicious IPs. Both methods are passive and cannot obtain complete information about the attack. Model-based attack identification methods can take proactive measures, allowing for a comprehensive understanding of both the attacker and the attack, effectively nipping virus attacks in the bud. Such methods include the Pain Pyramid, Diamond Model, Cyber Kill Chain, and ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework, with the ATT&CK framework being the most widely used and technically detailed.
(1) Signature-Based Detection
This method analyzes static features of local ransomware programs that can be obtained without execution, including:
Keywords in virus files, such as “ransomware” and “encrypt”; suspicious functions related to file encryption and decryption, process control; malicious domain names and IP addresses; MD5 hashes. This detection method scans for these static features to generate unique signatures and compares them with signatures in a database to identify the category of ransomware. The advantages of this method are speed and efficiency, but it requires prior capture of complete virus samples, and if the samples use code obfuscation techniques, it can make feature extraction difficult, limiting its application scenarios and frequency compared to other methods.
(2) Behavior-Based Detection
Behavior-based detection refers to detecting the behavioral characteristics of virus programs during their execution, identifying the type of ransomware. This detection is typically conducted on honeypots or virtualized platforms, utilizing detection tools to analyze the behavior of virus samples during execution and extract behavioral features, which are then classified using machine learning algorithms. Usable dynamic behavioral features include four categories.
First, files: The type, extension, and content of files will change before and after the virus runs; second, abnormal traffic: including analyzing data interactions between the system and external C&C servers or detecting a large number of DNS queries generated by DGA (Domain Generation Algorithm); third, CPU resources: samples running will consume a large amount of CPU resources, analyzing average CPU utilization, RAM usage, etc., to determine if an infection has occurred; fourth, API calls: for example, API functions that capture information from windows, such as GetWindowDC. The difficulty of behavior-based detection lies in defining behaviors and the similarity and differences in feature extraction and identification.
(3) Attack Identification Based on the ATT&CK Framework
ATT&CK is a security knowledge base proposed by MITRE that includes network attack strategies, techniques, and procedures (TTPs). The ATT&CK framework integrates existing APT (Advanced Persistent Threat) attack strategies and techniques, forming a common language and abstract knowledge base framework to describe hacker behavior, observing real-world network attacks from the attacker’s perspective. The ICS-specific ATT&CK framework emerged in 2020, summarizing and analyzing common industrial attacks based on the principles and characteristics of the monitoring layer, field control layer, and physical layer of ICS, identifying 12 strategies and 94 tactics, including initial access, execution, persistence, privilege escalation, defense evasion, discovery, lateral movement, collection, command and control, suppression of response functions, damage to process control, and impact. The ICS ATT&CK matrix is shown in Figure 1.
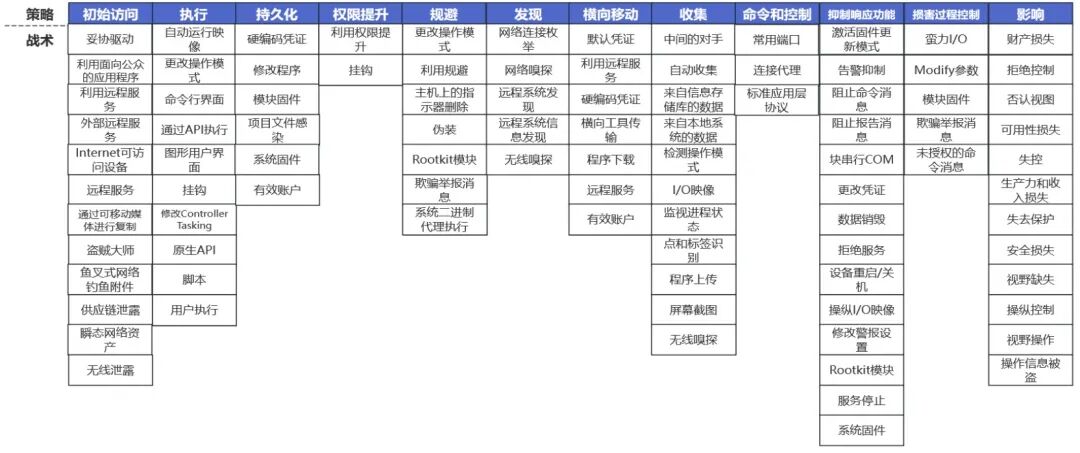
Figure 1: ICS ATT&CK Framework
Using ATT&CK allows for a comprehensive analysis of the entire lifecycle of ransomware attacks on ICS systems.
(1) Initial Access: The virus deploys payloads to the victim’s host;
(2) Execution: Executes the code carried by the virus attachment, such as PowerShell, CMD, and other system components;
(3) Persistence: Maintains access and control permissions to the target host within the ICS environment;
(4) Privilege Escalation: The virus gains higher privileges at this stage, including system-level and administrator privileges;
(5) Defense Evasion: Utilizes system tools to evade antivirus software;
(6) Discovery: The attacker gathers information about the target network topology, discovering more servers and devices;
(7) Lateral Movement: Moves between servers and devices to expand the infection target;
(8) Collection: Gathers more high-value data and asset information from the victim;
(9) Command and Control: Establishes network communication and remote interaction with the ICS system;
(10) Suppression of Response Functions: Prevents the victim from responding to ICS system or device failures, dangers, or unsafe conditions;
(11) Damage to Process Control: The virus negatively impacts the controlled processes by disrupting control logic and manipulating response information;
(12) Impact: The ICS system, data, or environment is controlled, interrupted, or destroyed.
Based on the TTPs employed by the aforementioned 20 ransomware types, statistics on ATT&CK strategies and techniques are shown in Figure 2. Frequently used techniques include “Exploitation of Public-Facing Applications” (T0819), “Phishing” (T0865), and “Scripting” (T0853). Specifically, the TTP attack profile of a ransomware targeting Siemens S7 PLC (PLC-Blaster) is illustrated in Figure 3. PLC-Blaster first halts the user program being executed on the target, copies itself into the target (T0858); then maintains its original code on the target (T0821) and uses functional blocks to destroy TCP connections with other systems (T0834); PLC-Blaster copies itself into various program organization units on the device (T0889) for persistence; scans for other Siemens device targets within the system (T0846), utilizing PLC communication and management APIs for lateral movement (T0843); ultimately executing DoS attacks (T0814) and manipulating any outputs of the PLC (T0835) for extortion.
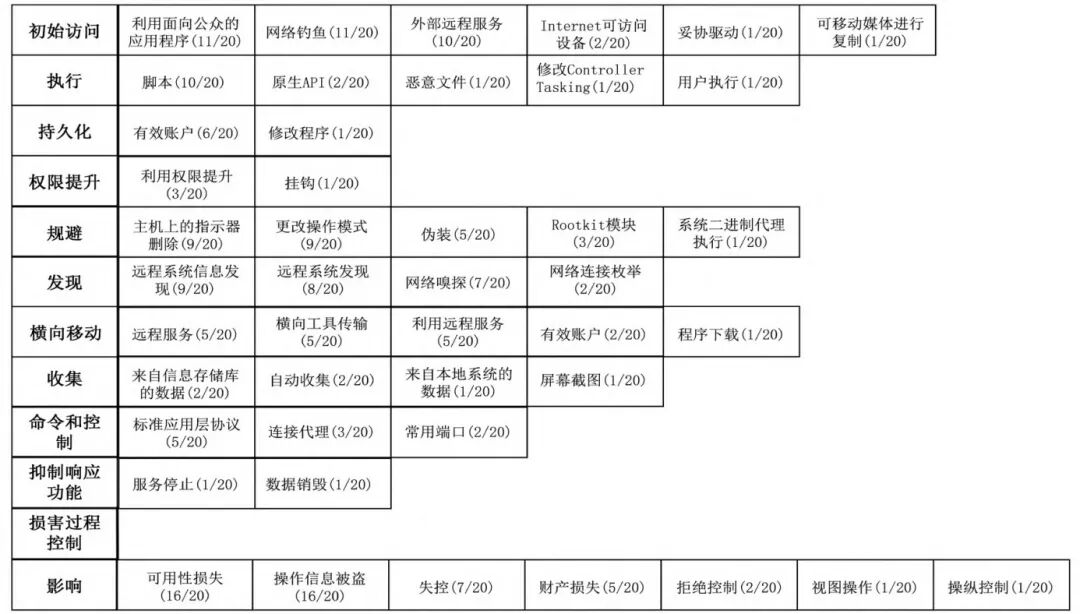
Figure 2: Strategies and Techniques Used by 20 Types of ICS Ransomware
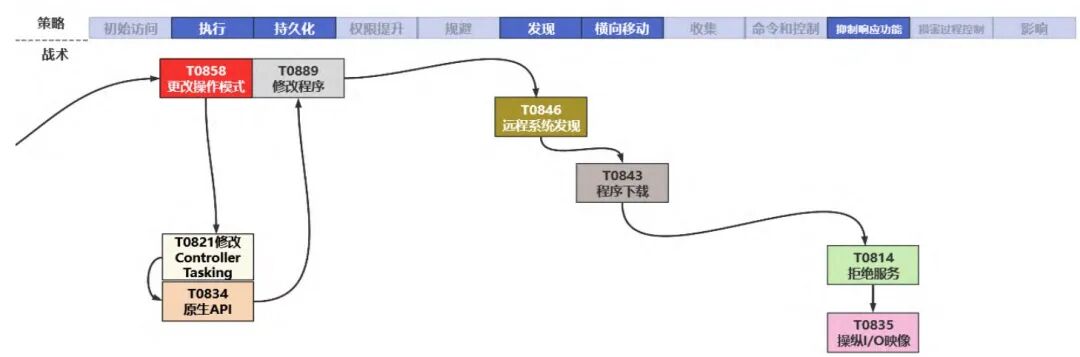
Figure 3: PLC-Blaster Attack Profile
From the above, it is evident that utilizing the ATT&CK framework for identifying ransomware attacks on ICS systems allows for a comprehensive analysis of the attack chain, covering the entire lifecycle of virus attacks from identification to invasion and implementation. This method of abstractly describing virus behavior to characterize network attacks enables the analysis of the features of the entire attack lifecycle and the identification of the techniques and methods employed by attackers, which is not achievable with the aforementioned two detection methods. Among the four model-based methods, the Pain Pyramid struggles to obtain high-value IOCs (Indicators of Compromise); the Diamond Model, while simple in appearance, has a complex modeling and solving process; the Cyber Kill Chain model exhibits asymmetry and unevenness in offense and defense. Although the ATT&CK framework also faces issues with tactical and strategic matching lacking linear, grouped, or hierarchical structures, it is widely applied due to its excellent unified architecture and detailed technical characterization.
4. Protection Against Ransomware in ICS Systems
(1) Current Protection Status
As the openness of ICS system networks continues to expand, the network security issues present in traditional IT systems are increasingly evident in ICS systems. Ransomware can launch attacks through the IT side of ICS enterprise networks, servers, OT side communication networks, and devices, making it difficult to defend against. Currently, ICS systems face the following security issues: first, weak protection capabilities, with over 80% of low-protection ICS system devices; second, insufficient isolation, leading to lateral movement of viruses and blurred IT/OT boundaries, resulting in inadequate boundary protection; third, numerous vulnerabilities, with difficulty maintaining them due to economic and security considerations; fourth, flaws in industrial protocols, with data transmission lacking authentication, authorization, and encryption protection mechanisms. These shortcomings make it challenging for ICS systems to withstand ransomware attacks.
Traditional general methods for protecting ICS systems against viruses include backups, avoiding weak passwords, regular security training, disabling unnecessary shared ports, and planning and clarifying response strategies and responsibilities.
(2) Protection Recommendations
Based on the analysis of ransomware functionality, characteristics, and detection methods in ICS systems, this article proposes some systematic protective measures to address the low protection, weak isolation, and numerous vulnerabilities in industrial control systems.
(1) Enhance Authentication: Implement multi-factor authentication and strong password verification for external maintenance devices, internal servers, industrial control devices, and edge gateways at all levels and endpoints of the ICS system.
(2) Implement Boundary Protection: Divide the ICS into different isolated zones for management, such as segmenting it into five areas based on the Purdue control layer model, then deploying firewalls, static routing, and establishing security domains with unified trust levels and execution policies through network segmentation to minimize access to sensitive information and prevent widespread virus propagation.
(3) Implement Vulnerability Management: Set maintenance windows and prioritize vulnerability maintenance based on asset priority to balance production and security needs, with priorities ranked from highest to lowest as follows: industrial firewalls, industrial switches, servers, engineering workstations, and HMI servers.
(4) Effective Monitoring: This includes monitoring system status and critical traffic. Monitor for abnormal processes, patches, and key logs, establish black and white lists for IPs and domains, and analyze sensitive traffic to ensure control over this critical information.
(5) Proactive Threat Identification: This includes assessing potential vulnerabilities and threat vectors, constructing risk scenarios, simulating virus intrusions, and obtaining threat intelligence to ultimately eliminate viruses in their infancy.
5. Conclusion
The network security of ICS systems is crucial for the normal operation of critical infrastructure, affecting not only the safety of relevant personnel but also public services for residents. Among these, ransomware poses the most severe cybersecurity threat to ICS systems. As ICS systems increasingly connect to the internet, the boundaries between the IT and OT sides are becoming more blurred and vulnerable, facilitating ransomware attacks. The complex and variable nature of ransomware can target all levels of ICS systems, including IT, PLC, SCADA, and communication protocols, raising higher and more comprehensive requirements for ransomware detection and protection. The MITRE ICS ATT&CK framework provides a well-descriptive tactical approach with a wide application range, applicable to the detection and identification of ransomware attacks throughout the entire lifecycle of ICS systems. Furthermore, ATT&CK can also be applied to virus threat hunting and cybersecurity management, integrating detection and protection, which is one of the future development trends.
Original article published in “Digital Transformation” Issue 2, 2025. Authors: Mo Xiaolei, Miao Yong, Tong Yong, Tong Zhiming, Sui Tianju
Reprinted from: New Industrial Network




Annual Review of the Linyi Industrial Internet Association is here!



Showcase of Benchmark Enterprises in the Digital Transformation of Linyi Manufacturing Industry



Service List of the Linyi Industrial Internet Association