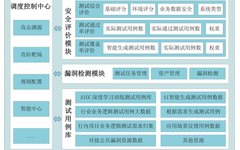
Core Technology is the National Treasure: The Development of the Cybersecurity Industry Relies on Self-Control
Global Technology Map Innovation | Frontier | Science Popularization | Information In recent years, the Central Committee of the Party and President Xi have placed great importance on the construction and development of self-controlled cybersecurity. The ZTE incident has also shown that self-control is the path for the development of China’s cybersecurity industry, and core … Read more