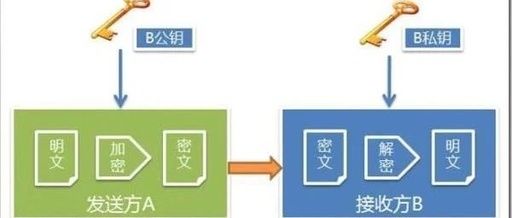
Understanding 5G NSA and SA in Simple Terms
Hello everyone, I am Xiaozao. The first official 5G standard is about to be released, and I believe everyone is eagerly looking forward to it. Previously, I introduced to everyone that back in December last year, we actually released a “half” 5G standard. That’s right, at that time it was the “Non-Standalone (NSA)” 5G standard. … Read more