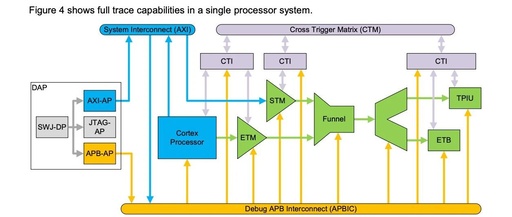
Coresight Pitfall Diary – Funnel Component
Introduction: The previous article was only half written and not published yet, so here’s a quick note. Preface Recently, while working with Coresight, I had a persistent question: how does the funnel know which trace source corresponds to the input slave port? After discussing with the FAE from the chip manufacturer today, I finally understood … Read more