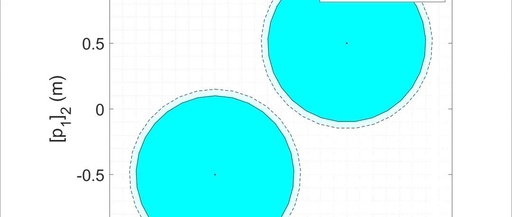
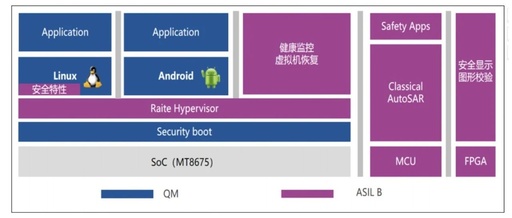
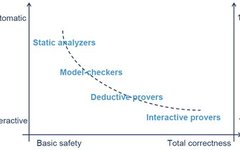
Research on Continuous Control of Safety-Critical Multi-Agent Systems Based on Quadratic Programming under Uncertainty
[Image]Gift to Readers[Image] Conducting research involves a profound system of thought, requiring researchers to be logical, meticulous, and diligent. However, mere effort is not enough; often leveraging resources is more important than hard work. Additionally, one must have innovative ideas and inspirations that look up to the stars. It is recommended that readers browse through … Read more