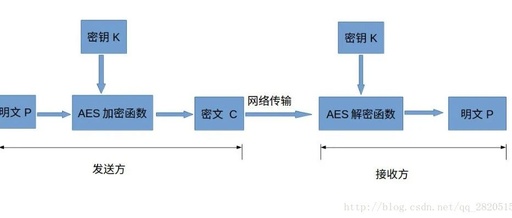
Advanced Data Encryption in Excel: Implementing RSA Algorithm and Digital Signatures
Hi, Excel enthusiasts! Today I want to share with you a super cool advanced application of Excel—data encryption. That’s right, today we are going to implement the RSA encryption algorithm and digital signatures in Excel! Sounds impressive, right? Don’t worry, I will explain each step in an easy-to-understand way. Through this article, you will learn … Read more