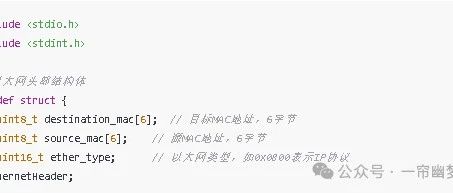
Open Source Projects and Resources Related to Embedded Systems
Follow+Star Public Account, Don’t Miss Exciting Content Source | Embedded Miscellaneous One of the hardest things at the beginning of learning is finding study materials. This post carefully compiles some resources related to embedded systems, including but not limited to programming languages, microcontrollers, open-source projects, the Internet of Things, operating systems, Linux, and more. It … Read more