ip rule manages the rules of the routing policy database in the Linux kernel. Through these rules, complex routing decisions can be made, such as routing based on source address, destination address, protocol type, and other conditions.
Command Format
ip [ OPTIONS ] rule { COMMAND | help }
ip rule [ show [ SELECTOR ]]
ip rule { add | del } SELECTOR ACTION
ip rule { flush | save | restore }
SELECTOR := [ not ] [ from PREFIX ] [ to PREFIX ] [ tos TOS ] [
fwmark FWMARK[/MASK] ] [ iif STRING ] [ oif STRING ] [
priority PREFERENCE ] [ l3mdev ] [ uidrange NUMBER-NUMBER
] [ ipproto PROTOCOL ] [ sport [ NUMBER | NUMBER-NUMBER ]
] [ dport [ NUMBER | NUMBER-NUMBER ] ] [ tun_id TUN_ID ]
ACTION := [ table TABLE_ID ] [ protocol PROTO ] [ nat ADDRESS ] [
realms [SRCREALM/]DSTREALM ] [ goto NUMBER ] SUPPRESSOR
SUPPRESSOR := [ suppress_prefixlength NUMBER ] [ suppress_ifgroup
GROUP ]
TABLE_ID := [ local | main | default | NUMBER ]
The ip rule can operate on the rules in the routing policy database (RPDB), which is used to control the routing selection algorithm.
The traditional routing algorithms used on the Internet make routing decisions based solely on the destination address of the packet (theoretically also based on the Type of Service (TOS) field, but this is not the case in practice).
In some cases, we want to route packets not only based on the destination address but also based on other packet fields (such as source address, IP protocol, transport protocol port, and even packet payload). This task is known as policy routing.
To achieve this, the traditional destination-based routing table, sorted by the longest match rule, is replaced by the routing policy database (or RPDB: routing policy database), which selects routes by executing a series of rules.
Each policy routing rule consists of a selector (selector) and an action predicate (action predicate). The RPDB is scanned in order of priority from high to low (note that a lower numerical value indicates a higher priority, as described below regarding “priority (PREFERENCE)”). The selector of each rule is applied to {source address, destination address, inbound interface, Type of Service (TOS), firewall mark (fwmark)}. If the selector matches the packet, the corresponding action is executed. The action predicate may return a successful result. In this case, it either provides a route or indicates failure, and the RPDB lookup process terminates. Otherwise, the RPDB program continues to process the next rule.
Semantically, the most common actions are selecting the next hop and output device.
At startup, the kernel configures a default routing policy database (RPDB) consisting of three rules:
-
Priority: 0, Selector: matches anything, Action: lookup local routing table (number 255). The local table is a special routing table that contains high-priority control routes for local and broadcast addresses.
-
Priority: 32766, Selector: matches anything, Action: lookup main routing table (number 254). The main table is the ordinary routing table that contains all non-policy routes. Administrators can delete this rule or override it with other rules.
-
Priority: 32767, Selector: matches anything, Action: lookup default routing table (number 253). The default table is empty. If none of the previous default rules selected the packet, it will be retained for some subsequent processing. This rule can also be deleted.
Each entry in the routing policy database (RPDB) has additional attributes. For example, each rule has a pointer to a routing table. Network Address Translation (NAT) and masquerading rules have an attribute for selecting a new IP address for translation/masquerading. Additionally, rules have some optional attributes, which are the “realms” that the route possesses. These values do not override the attributes contained in the routing table. They are only used when the route does not select any attributes.
The RPDB may contain the following types of rules:
- Unicast: This rule returns the route found in the routing table referenced by the rule.
- Blackhole: This rule silently drops packets.
- Unreachable: This rule generates a “network unreachable” error.
- Prohibit: This rule generates a “communication administratively prohibited” error.
- NAT: This rule translates the source address of IP packets to some other value.
<span>ip rule add</span> —— Insert a new rule
<span>ip rule delete</span> —— Delete a rule
Parameter Description
<span>type TYPE (default)</span>: The type of this rule. The valid type list has been provided in the previous section.<span>from PREFIX</span>: Select the source prefix to match.<span>to PREFIX</span>: Select the destination prefix to match.<span>iif NAME</span>: Select the inbound device to match. If this interface is the loopback interface (lo), this rule only matches packets originating from that host. This means you can create separate routing tables for forwarded packets and local packets, completely isolating them.<span>oif NAME</span>: Select the outbound device to match. The outbound interface only applies to packets originating from local sockets bound to a device.<span>tos TOS</span><span>dsfield TOS</span>: Select the Type of Service (TOS) value to match.<span>fwmark MARK</span>: Select the firewall mark value to match.<span>uidrange NUMBER - NUMBER</span>: Select the range of user ID (uid) values to match.<span>ipproto PROTOCOL</span>: Select the IP protocol value to match.<span>sport NUMBER | NUMBER - NUMBER</span>: Select the source port value to match, supporting port ranges.<span>dport NUMBER | NUMBER - NUMBER</span>: Select the destination port value to match, supporting port ranges.<span>priority PREFERENCE</span>: The priority of this rule.<span>PREFERENCE</span>is an unsigned integer value, where a higher value indicates a lower priority, and rules are processed in ascending order of value. Each rule should explicitly set a unique priority value.<span>preference</span>and<span>order</span>are synonyms for<span>priority</span>.<span>table TABLEID</span>: The routing table identifier to look up further if the rule selector matches successfully.<span>lookup</span>can also be used instead of<span>table</span>.<span>protocol PROTO</span>: The routing protocol that installed this rule. For example, when Zebra installs a rule, its installation protocol will be marked as<span>RTPROT_ZEBRA</span>.<span>suppress_prefixlength NUMBER</span>: Reject routing decisions with a prefix length of<span>NUMBER</span>or shorter.<span>suppress_ifgroup GROUP</span>: Reject routing decisions using devices belonging to the interface group<span>GROUP</span>.<span>realms FROM/TO</span>: If the rule matches and the routing table lookup is successful, select the corresponding “realms”. The “realms TO” will only be used if the route did not select any “realms”.<span>nat ADDRESS</span>: The base address of the block of IP addresses used for translation (for source address).<span>ADDRESS</span>can be the starting address of the NAT address block (chosen by NAT routing) or a local host address (even zero). In the latter case, the router will not translate the packets but masquerade them as that address. Using<span>map - to</span>has the same meaning as using<span>nat</span>.
Notes
Changes made to the routing policy database (RPDB) using these commands will not take effect immediately. It is assumed that after completing a batch of updates in the script, the <span>ip route flush cache</span> command needs to be used to refresh the routing cache.
<span>ip rule flush</span> —— Clear all routing policy rules and simultaneously output (dump) the list of deleted rules.
<span>ip rule show</span> —— List rules.
This command has no parameters. The options "list" or "lst" are synonymous with "show".
<span>ip rule save</span> —— Save rules.
Saves the rule table information to standard output. The behavior of this command is similar to “ip rule show”, except that its output is raw data suitable for passing to the “ip rule restore” command.
ip rule restore —— Restore rules.
Restores rule table information from standard input.
This command expects to read the data stream returned by the “ip rule save” command. It will attempt to restore the rule table information to the exact state it was in when saved. Any existing rules in the table will remain unchanged, and duplicate rules will not be ignored.
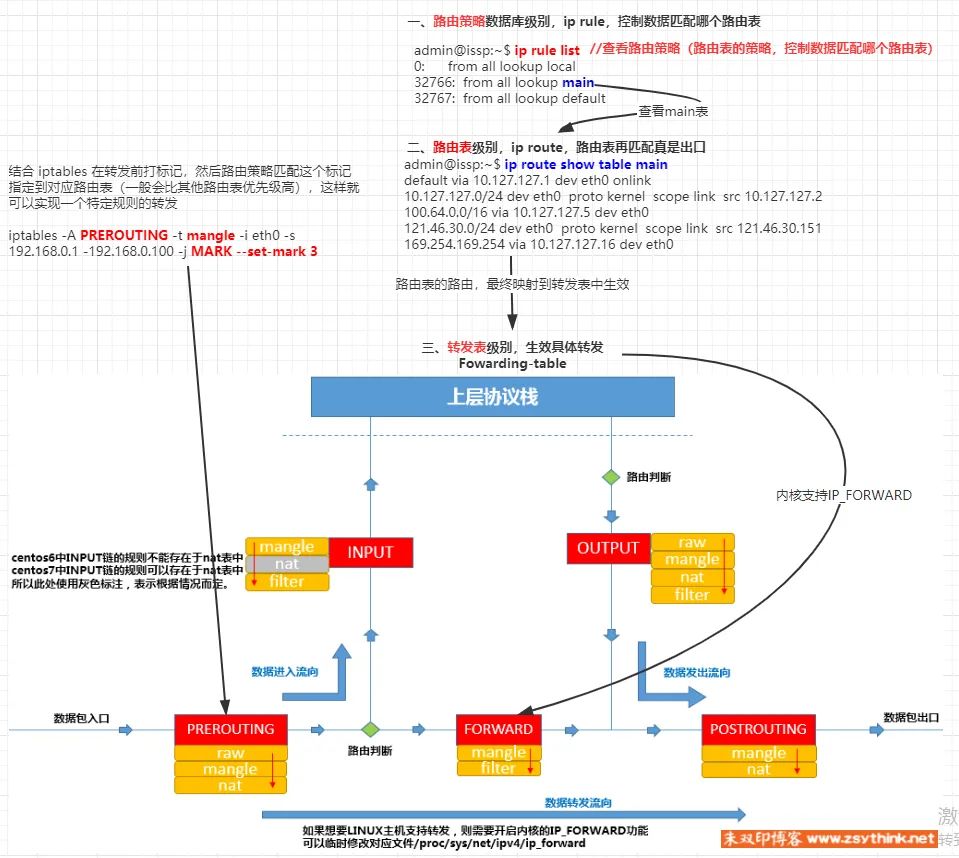
Key Diagram —— ip rule, ip route, iptables
Reference
https://www.man7.org/linux/man-pages/man8/ip-rule.8.html
https://geekdaxue.co/read/wucy@lg7gd3/eydsyh