In daily life, when shopping online or mailing an item, we need to fill in both parties’ addresses, contact information, whether insurance is needed, and other details. Additionally, the courier company may have other regulations to be added to the purchase and mailing details. The purpose of this is to ensure the reliability and accuracy of the mailing process.
Similarly, in communication networks, when data packets are transmitted between different devices over the network, in order to send them reliably and accurately to their destination while efficiently utilizing transmission resources (transmission devices and lines), the data packets must be split and packaged in advance.
Additional information such as the destination address, local address, and some error correction bytes are attached to the data packets. When security and reliability requirements are high, encryption may also be applied.
This operation is called data encapsulation, and the rules followed and negotiated by both parties during the processing of the data packets are referred to as protocols. Compared to the mailing process, data packets are similar to items, while encapsulation is akin to filling out various mailing information, and protocols dictate how to fill out the information.
From the above analysis, it can be seen that data packet encapsulation is actually quite complex: to achieve reliability, accuracy, and efficiency, many influencing factors must be considered, and targeted preventive measures must be taken.
In practical applications, data encapsulation in networking is performed in layers according to functionality, with the aim of breaking down complex systems into many modules that operate independently without affecting each other. Each module (layer) is connected and interacts through interfaces, providing services to one another. This not only makes it easier to implement functions but also grants the entire system good compatibility and scalability.
Taking the common OSI model as an example, it is divided into seven layers, from bottom to top: Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer, with each layer corresponding to different functions. To achieve the corresponding functions, data is encapsulated with protocol headers and trailers according to the protocol of the current layer, and the encapsulated data is then passed to the lower layer. The data encapsulation process for each layer is shown in the figure below.
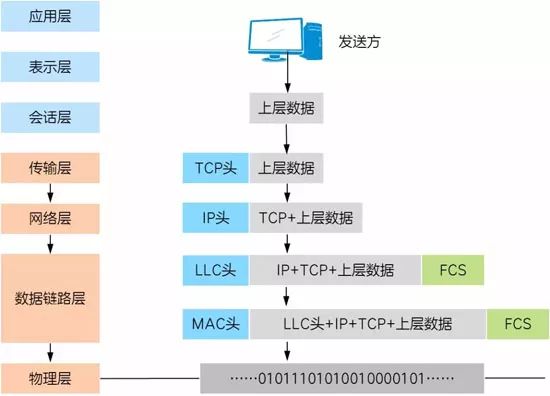
Among them:
-
In the Transport Layer, the TCP header indicates a connection with a specific application and encapsulates the data into segments.
-
In the Network Layer, the IP header indicates the network address of the connected device and can base network path selection on this information, encapsulating the data as packets.
-
In the Data Link Layer, the data is encapsulated into frames, and the MAC header provides the physical address of the device, along with functions like data verification.
-
In the Physical Layer, the data frame is converted into a bitstream for transmission over the physical link.
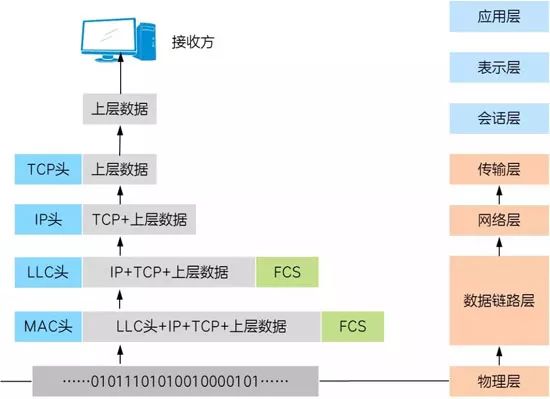
The receiving end of the data begins at the Physical Layer and performs the reverse operation of the sender, called “decapsulation,” as shown in the figure below, ultimately allowing the application layer program to obtain the data information, completing a single-direction communication between two points.
It should be noted that the currently most widely used TCP/IP protocol can be viewed as a simplification of the OSI protocol layers, divided into four layers: Network Access Layer, Internet Layer, Transport Layer, and Application Layer. The data encapsulation in each layer is similar to that of the OSI model.