TCP/IP is not a single protocol, but a collective term for a suite of protocols. It includes the IP protocol, ICMP protocol, and TCP protocol.
Here are a few key points to note:
Internet Address: This is the IP address, generally consisting of the network number + subnet number + host number.Domain Name System: In simple terms, this is a database that converts host names to IP addresses.RFC: The standard documentation for TCP/IP protocols.Port Number: A logical number that tags IP packets.Socket: Application Programming Interface.
Working Characteristics of the Data Link Layer: 1. Sends and receives IP datagrams for the IP module. 2. Sends ARP requests and receives ARP replies for the ARP module (ARP: Address Resolution Protocol, converts IP addresses to MAC addresses). 3. Sends RARP requests and receives RARP replies for RARP.
Next, let’s understand the TCP/IP workflow:The data link layer obtains data transfer information from ARP and then gets specific data information from the IP protocol.
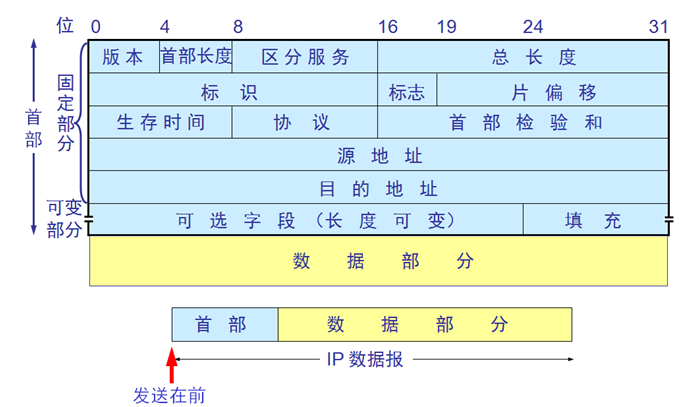
In the IP protocol, the most important field is TTL (the maximum number of network segments that IP allows to pass), which specifies how many routers the data packet can pass through before being discarded.
Routing Selection Workflow
Static Routing Selection:
-
Configure the interface to generate routing table entries by default, or manually add entries using route add.
-
ICMP messages (ICMP redirect messages) update entries.
-
Dynamic routing selection (only used between routers).
Simply put, 1. When establishing a connection, the client sends a SYN packet (SYN=i) to the server and enters the SYN-SEND state, waiting for the server to confirm.
2. The server receives the SYN packet and must confirm the client’s SYN (ack=i+1), while also sending its own SYN packet (SYN=k), i.e., a SYN+ACK packet. At this point, the server enters the SYN-RECV state.
3. The client receives the server’s SYN+ACK packet and sends an ACK to the server (ack=k+1). Once this packet is sent, both the client and server enter the ESTABLISHED state, completing the three-way handshake.
In this context, let’s introduce a key concept: SYN attack. What is a SYN attack? Under what conditions does it occur? How can it be avoided?
During the three-way handshake, after the server sends SYN-ACK and before receiving the client’s ACK,
A TCP connection is called a half-open connect. At this point, the server is in the SYN_RCVD state, and after receiving the ACK, the server transitions to the ESTABLISHED state.
A SYN attack occurs when a client forges a large number of non-existent IP addresses in a short time and continuously sends SYN packets to the server. The server replies with confirmation packets and waits for the client’s confirmation.
Since the source address does not exist, the server must continually resend until it times out. These forged SYN packets will occupy the unconnected queue, causing normal SYN requests to be discarded due to a full queue, leading to network congestion or even system failure.
A SYN attack is a typical DDOS attack. Detecting a SYN attack is very simple: when there are many half-open connections on the server and the source IP addresses are random, it can be concluded that a SYN attack is occurring. You can use the following command to check:
#netstat -nap | grep SYN_RECV
The Process of Four-Way Handshake
We denote the client as A and the server as B.
Since TCP connections are full-duplex, each direction must be closed separately.
This principle states that when one party completes its data transmission, it sends a FIN to terminate the connection in that direction.
Receiving a FIN only means that there is no data flow in that direction; it does not mean that data cannot be sent on this TCP connection until that direction also sends a FIN. The party that first closes the connection will perform an active close, while the other party will perform a passive close.
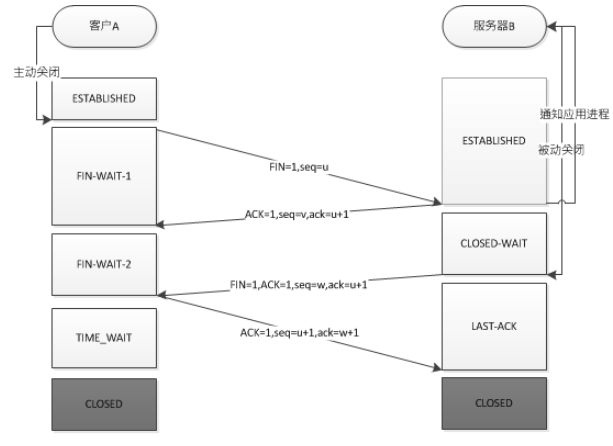
Precondition: A actively closes, B passively closes.
Some may ask why there are three handshakes for connection establishment, but four for disconnection?
This is because when the server is in the LISTEN state and receives a SYN packet for a connection request, it sends the ACK and SYN in one packet to the client. However, when closing the connection, receiving the other party’s FIN packet only indicates that the other party will not send data anymore, but it can still receive data, and the party may not have sent all its data to the other party, so it can either close immediately or send some data to the other party before sending a FIN to indicate its agreement to close the connection. Therefore, the ACK and FIN are generally sent separately.
1. A sends a FIN to close data transmission from A to B, entering FIN_WAIT_1 state. 2. B receives the FIN and sends an ACK to A, acknowledging the sequence number as the received sequence number + 1 (similar to SYN, a FIN occupies a sequence number), entering CLOSE_WAIT state. 3. B sends a FIN to close data transmission from B to A, entering LAST_ACK state. 4. A receives the FIN, enters TIME_WAIT state, and then sends an ACK to B, acknowledging the sequence number as the received sequence number + 1, and B enters CLOSED state, completing the four-way handshake.
In simple terms, 1. Client A sends a FIN to close data transmission from client A to server B (Segment 4).
2. Server B receives this FIN and sends back an ACK, with the acknowledgment number set to the received number + 1 (Segment 5). Like SYN, a FIN occupies a sequence number.
3. Server B closes the connection with client A and sends a FIN to client A (Segment 6).
4. Client A sends back an ACK confirming and sets the acknowledgment number to the received number + 1 (Segment 7).
After entering the TIME-WAIT state, A does not immediately release TCP; it must wait for a time set by the time-wait timer of 2MSL (Maximum Segment Lifetime) before entering the CLOSED state. Why?
1. To ensure that the last ACK packet sent by A can reach B. 2. To prevent “stale connection request packets” from appearing in this connection.
OK~ Does it feel difficult to understand? Let’s put it in a more relatable way.
Three-Way Handshake Process1. The client sends a request “Open the door, I want to come in” to the server. 2. The server replies, “Come in, I will open the door for you” to the client. 3. The client politely sends back, “Thank you, I am coming in” to the server.
Four-Way Handshake Process1. The client sends “It’s getting late, I want to leave” to the server, waiting for the server to see him off. 2. The server hears this and replies, “I understand, then I will see you out” to the client, waiting for the client to leave. 3. After the server closes the door, it sends “I am closing the door” to the client, then waits for the client to leave (wow~ so dramatic). 4. The client replies, “I understand, I am leaving now” and then leaves.
Add Teacher Tang on WeChat
Get the latest learning materials anytime
[Zero-Basis Training Camp] Opens tonight!
Students who haven’t joined yet have one last chance!

You might also want to read
What Exactly Is Software Testing Learning (Career Development Overview)
Tool Questions in Interviews: This One Article Is Enough
Is Taobao Bug? Is It Man-Made or Accidental Operation?
“With this certificate, there is no need for a written test, directly entering the final review!”






