↑ Click on the above
“Smart Manufacturing Home”
Follow us
Source: PwC China

Members can enter the member download area to obtain more related materials~
Introduction
Hello everyone, I am Xiao Zhi, the host of Smart Manufacturing Home~
Previously, we discussed various industrial software such as PLM, ERP, MES/MOM, APS, SCADA, and also talked about the integration of OICT (OT, IT, and CT). However, many IT and CT professionals do not understand OT, and many OT professionals are not clear about the network architecture, security architecture, standards, etc., in OT systems. Today, we will have an overall discussion~
01 Typical Architecture and Current Status of Industrial Control Systems
02 Analysis of Industrial Control System Security Incidents
03 Global Industrial Control Security Standards and Compliance
04 Security Risks and Protections of Industrial Control Systems
05 The Industrial Future of Giants like Siemens, GE, and Bosch

01 Typical Architecture and Current Status of Industrial Control Systems
Typical Architecture of Industrial Control Systems
The main goal of industrial control systems is to achieve logistics control, equipment information monitoring, and diagnostic processing of industrial automation production lines. Its main functions include equipment management, task management, log management, scheduling management, diagnostic management, system simulation, etc.
Industrial control systems typically include components such as Manufacturing Execution Systems (MES), Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLC). The MES system mainly manages the production process, such as manufacturing data management, production scheduling management, and planning scheduling management. SCADA systems usually use centralized data collection and monitoring methods to control dispersed facilities. DCS systems are typically used to control production systems within a local area, such as monitoring and adjusting local factories. PLCs are usually used for specific discrete devices, providing corresponding control adjustments. Industrial control systems also involve Remote Terminal Units (RTU), Intelligent Electronic Devices (IED), and interface technologies that ensure communication between components.
Industrial control systems also include control loops, Human-Machine Interfaces (HMIs), and remote diagnostic and maintenance tools built using a variety of network protocols. Industrial control systems are widely used in various industries, such as power, energy, chemical industry, transportation, manufacturing (automotive, aerospace, and durable goods), pharmaceuticals, paper making, food processing, etc.
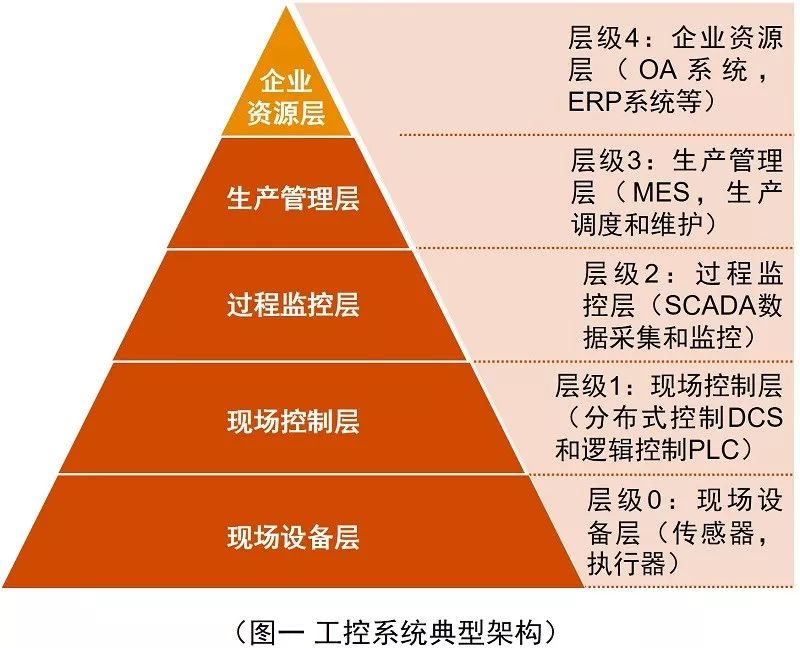
Due to the differences in the technical fields, industry characteristics, and types of business carried by industrial control systems, the architecture of industrial control systems can also vary. In a typical industrial control system, there are generally four levels: field device layer, field control layer, process monitoring layer, and production management layer (Level 0 – Level 3). The top production management layer interfaces with ERP software in the enterprise resource layer (Figure 1).
Information security vulnerabilities in industrial control systems are distributed across all levels of the industrial control system architecture. Attackers may perform unauthorized or illegal operations through sniffing, deception, physical attacks, and virus propagation, affecting normal production in enterprises:
-
Obtain and analyze information from devices at all levels;
-
Modify sensitive information stored in industrial control system components;
-
Obtain user credentials stored in industrial control system components and impersonate legitimate users;
-
Issue erroneous commands or make incorrect configurations;
-
Spread malicious code causing unnecessary system downtime and data destruction;
-
Obtain user information through social engineering.
Industrial control systems differ from traditional IT systems. Compared to IT systems, industrial control systems have the following characteristics:
-
The system has a low tolerance for delays and high reliability requirements, most needing to operate continuously throughout the year;
-
Some industrial control systems still use outdated operating systems (OS), thus requiring higher security management for such systems;
-
Due to the involvement of software, hardware, firmware, and process flows in industrial control systems, change management is more complex;
-
The system communication protocols are more mixed, including various industrial buses, industrial Ethernet, wireless access, radio frequency, and satellite, etc.;
-
The overall architecture of the system is more complex, and the enterprise’s security awareness and consciousness are relatively low;
-
From a risk perspective, in addition to traditional information security, industrial control system security also needs to pay attention to personal, environmental, production, and physical safety;
-
The system lifecycle is longer, requiring higher completeness of system design and process integration.
In summary, compared to IT systems, establishing an information security system covering all levels of industrial control systems is more complex, requiring the attention and supervision of enterprise management, as well as cross-departmental collaboration within the enterprise.
Current Status of Industrial Control System Security
Historically, enterprise information security protection measures have mainly focused on traditional IT systems, especially public-facing systems and services. Regarding the information security issues of industrial control systems, enterprises often adopt a passive approach of security by obscurity, without giving sufficient attention and importance.
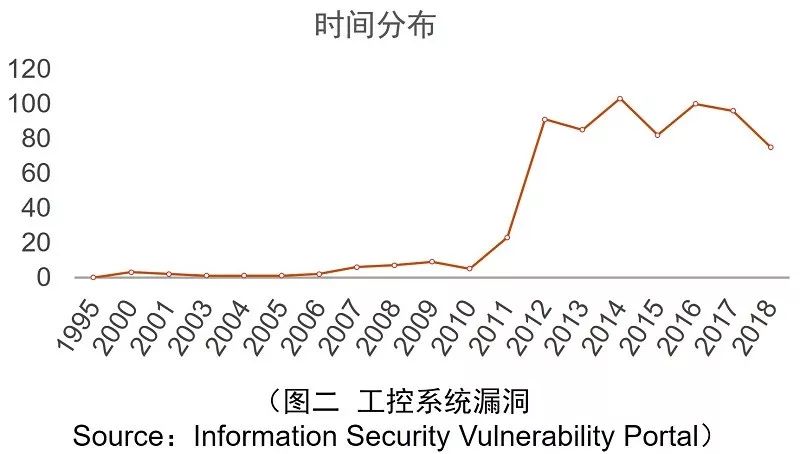
According to statistics from CVE (Common Vulnerabilities and Exposures) (see Figure 2), the number of vulnerabilities published in industrial control systems has significantly increased since 2011, and security incidents targeting industrial control systems have occurred, including significant events such as: the Stuxnet virus attack on Iran’s nuclear facilities in 2010, the large-scale power outage in Ukraine in 2015, the attack on TSMC’s production base in 2018, and the attack on Venezuela’s power grid in 2019, which caused nationwide blackouts in most areas. These incidents have resulted in severe consequences.
According to a survey conducted by the National Institute of Standards and Technology (NIST) in 2015*, the main security incidents that industrial control systems may face include:
-
Blocking or delaying the flow of information through the industrial control system network, interrupting the operation of the industrial control system;
-
Unauthorized tampering with commands, orders, or alarm thresholds, damaging or shutting down equipment, causing environmental impacts and threatening personal safety;
-
Sending inappropriate information to system administrators to cover up unauthorized changes or cause operators to take inappropriate actions;
-
Industrial control system software or configurations being modified without authorization, or software being infected by viruses or malware;
-
Interfering with the operation of equipment protection systems, endangering expensive and hard-to-replace equipment;
-
Interfering with the operation of safety systems, endangering personal safety.
(Source: Guide to Industrial Control Systems Security, 2015, NIST)
According to tracking and research by PwC China, we found that enterprises lack effective management and technical measures to ensure the security of industrial control systems, resulting in many security vulnerabilities, such as:
-
Security vulnerabilities in operating systems;
-
Control vulnerabilities for antivirus and malware;
-
Lack of control over external devices such as USB drives and CDs;
-
During equipment maintenance, laptops are randomly connected;
-
Insufficient boundary protection for industrial control system networks;
-
Weak access and contact control (including remote access and management maintenance);
-
Security management vulnerabilities in the lifecycle of industrial control software;
-
Lack of emergency response mechanisms for security incidents.
How Enterprises Should Respond
In the face of the aforementioned security threats to industrial control systems, we recommend that enterprises identify management and technical control gaps through risk assessments and gap analyses, and implement relevant corrective measures to enhance the overall security of their industrial control systems and resist security threats from both internal and external sources.
As a primary task, we suggest that enterprise management start considering the following questions:
1. What are the security risks faced by the production process—have all assets related to industrial control systems been identified? Have assets been prioritized, and have the potential consequences of damage been clarified? Can the enterprise maintain production and critical business processes after an information security incident occurs?
2. Has a security management team and responsible person for industrial control systems been established?
3. Do employees have sufficient awareness and understanding of industrial control system security?
4. Have security management systems and processes for industrial control systems been established?
5. Does the maintenance and security of industrial control systems rely on external third-party support? Is there an effective third-party management mechanism in place?
6. Is the industrial control system network connected to the enterprise network/internet, and are effective measures in place to protect its security while connected?
7. Are effective security measures implemented, such as antivirus, malware protection, and peripheral control?
8. Does the industrial control system network support remote access? Is remote access protected and monitored?
9. Has the enterprise established a security alert mechanism and emergency plan for industrial control systems?
10. Has the enterprise selected appropriate standards and established a complete security management system for industrial control systems?
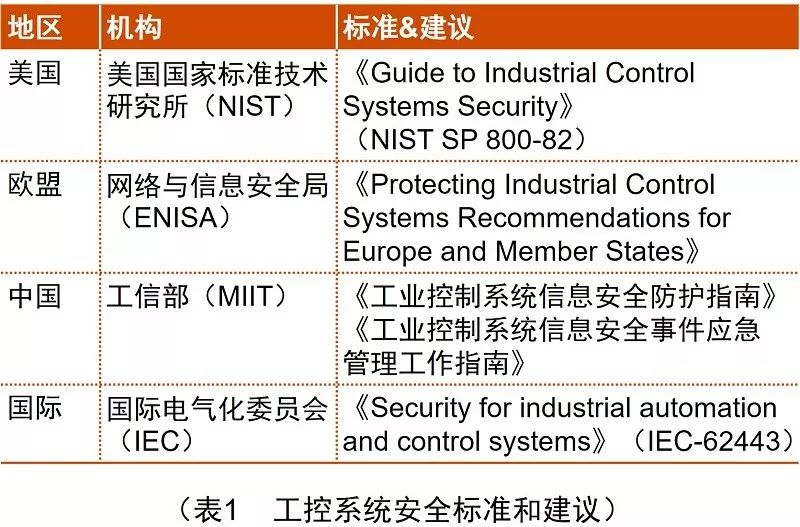
In addition, the United States, the European Union, and China have successively issued security standards and recommendations for industrial control systems (see Table 1), which can be referenced by enterprises.
PwC China continues to monitor and track industrial control security incidents, analyzing potential threats and risks. In the upcoming “Industrial Control System Security Series,” we will analyze industrial control system security incidents and introduce security standards and recommendations for industrial control systems.

02 Analysis of Industrial Control System Security Incidents
We have tracked the trends and major security incidents of industrial control systems in recent years and selected and analyzed recent industrial control security incidents, hoping to assist enterprises in further understanding the security threats and vulnerabilities of industrial control systems.
Release of Industrial Control System Vulnerabilities Increases Year by Year
In recent years, security incidents related to industrial control systems have frequently occurred both domestically and internationally. According to tracking and statistics from the National Information Security Vulnerability Sharing Platform (CNVD) (see Figure 1), since 2011, the number of vulnerabilities discovered and published in the industrial control field has shown a year-on-year increasing trend.
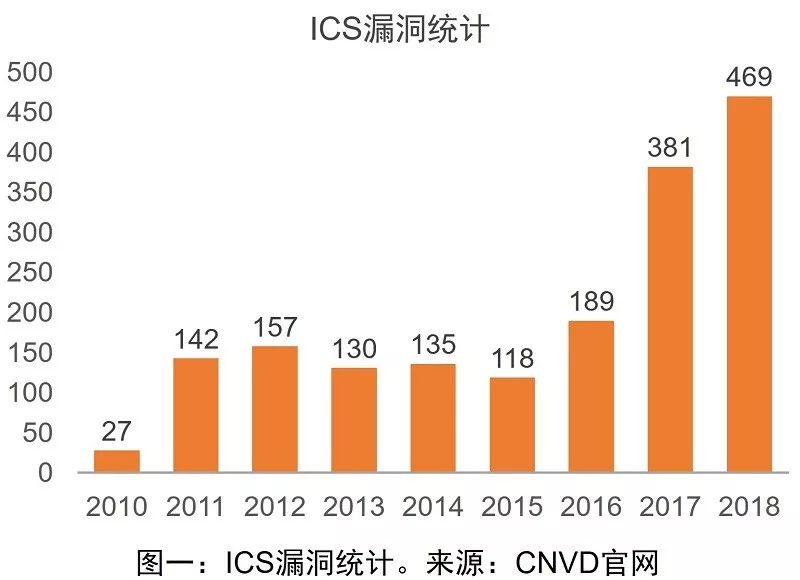
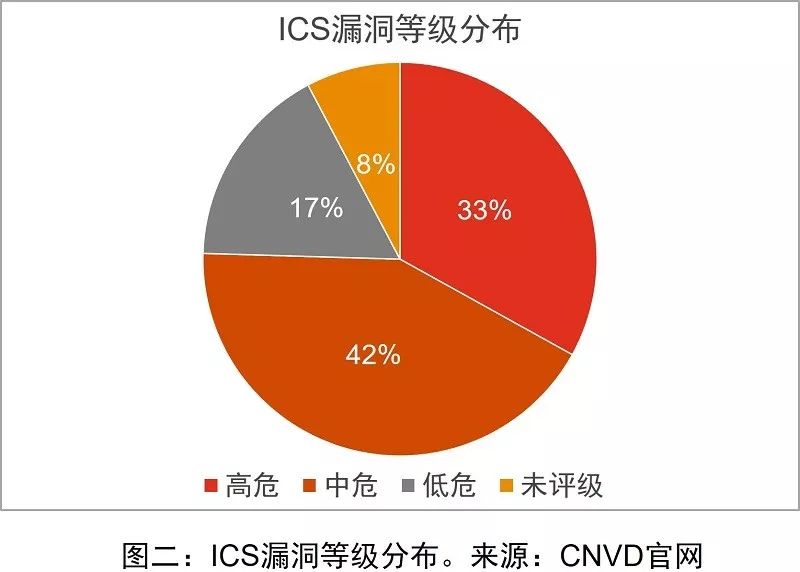
According to statistical analysis of publicly disclosed industrial control system vulnerability data by CNVD (see Figure 2), as of April 2019, 2,743 industrial control system vulnerabilities had been identified, of which 907 were high-risk vulnerabilities (accounting for 33%), and 1,163 were medium-risk vulnerabilities (accounting for 42%).
Review of Major Security Incidents in Industrial Control Systems
Stuxnet Virus Attacks Iran’s Nuclear Power Plant, Causing Uranium Enrichment Equipment to Malfunction

Iran
In June 2010, the uranium enrichment equipment at Iran’s Bushehr nuclear power plant malfunctioned, delaying Iran’s nuclear program. Investigations revealed that this was due to an attack by a new type of worm virus, which contained the characteristic word “stux” in its code, hence it was named the Stuxnet virus. Stuxnet is considered the first malicious code specifically targeting real-world infrastructure (energy).
Ukrainian Power Grid Attacked, Causing Widespread Blackouts

Ukraine
On December 23, 2015, the Ukrainian power grid experienced a power outage, causing nearly half of the households in Ivano-Frankivsk (about 1.4 million people) to experience hours of power paralysis. Investigations revealed that this incident was caused by a Trojan malware attack, which prompted broader attention to the security issues of industrial control systems due to its wide-ranging impact.
Ransomware WannaCry Rampages Globally

Global
On May 12, 2017, the WannaCry ransomware exploited the MS17-010 vulnerability to attack globally, affecting at least 300,000 users in 150 countries, resulting in losses of up to $8 billion, impacting numerous industries including finance, energy, and healthcare. Some ordinary users and enterprises in China were infected, leading to a large number of files being encrypted and unable to work normally, causing significant impact.
TSMC’s Three Major Plants Infected by Virus, Leading to Large-Scale Production Line Shutdowns

Taiwan
On August 3, 2018, some production equipment at TSMC was successively infected by a virus, leading to the shutdown of several plants in its three major production bases in Taiwan. TSMC, as the world’s largest chip foundry, has always been a key target for hackers, suffering numerous cyberattacks each year. However, this was the first time it led to such a large-scale production line shutdown.
Venezuela Power Outage Incident, Leading to Large-Scale Blackouts Lasting 6 Days

Venezuela
On March 7, 2019, a large-scale power outage occurred across Venezuela, affecting 18 out of 23 states. As of the end of April 2019, the cause of this incident had not been clearly identified.
Analysis of the Venezuela Power Outage Incident
This article selects the Venezuela power outage incident for analysis, delving into its potential causes.
Incident Review
According to Xinhua News Agency, starting at 5 PM (local time) on March 7, 2019, most areas of Venezuela, including the capital Caracas, experienced power outages lasting over 24 hours, with more than 18 states experiencing complete blackouts. The power outage caused the Caracas metro to stop operating, leading to massive traffic congestion, and schools, hospitals, factories, and airports were severely affected, with water supply and communication networks in most areas disrupted.
In the early hours of the 8th, some areas of Caracas began to restore power, and subsequently, power supply in other areas gradually resumed. However, on the noon of the 9th and the 10th, power outages occurred again, causing great panic among the people. The prolonged large-scale power failure caused severe losses to Venezuela, marking the longest and most widespread blackout since 2012.

Threat Possibility Analysis
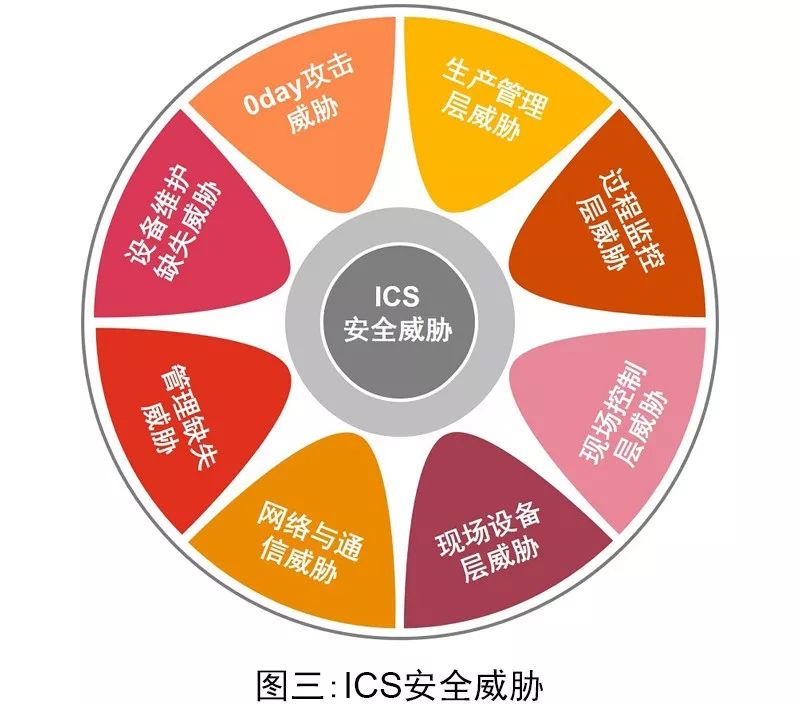
Regarding this large-scale power outage incident, there are various analytical viewpoints in the industry, and no unified conclusion has been reached. This article will analyze the potential security vulnerabilities that may have caused this large-scale power outage incident from eight aspects (see Figure 3).
1
Threats at the Field Control Layer
The control system of the Guri Hydroelectric Power Station in Venezuela is a distributed control system (DCS) designed by ABB for the power plant. ABB is a leading manufacturer in the field of power and automation technology, ranked among the Fortune Global 500. However, many high-risk vulnerabilities have been reported in ABB systems, such as (CNVD-2016-10592) ABB RobotWare remote code execution vulnerability, and (CNVD-2014-08129) multiple local code execution vulnerabilities in ABB products.
Attackers can analyze and exploit publicly disclosed vulnerabilities to write malicious code and create viruses targeting ABB control systems. Since the control equipment used by the Guri Hydroelectric Power Station in Venezuela is relatively old, if relevant security patches or other effective preventive measures are not timely upgraded, it may lead to numerous vulnerabilities being exploited by attackers, resulting in large-scale power outages.
2
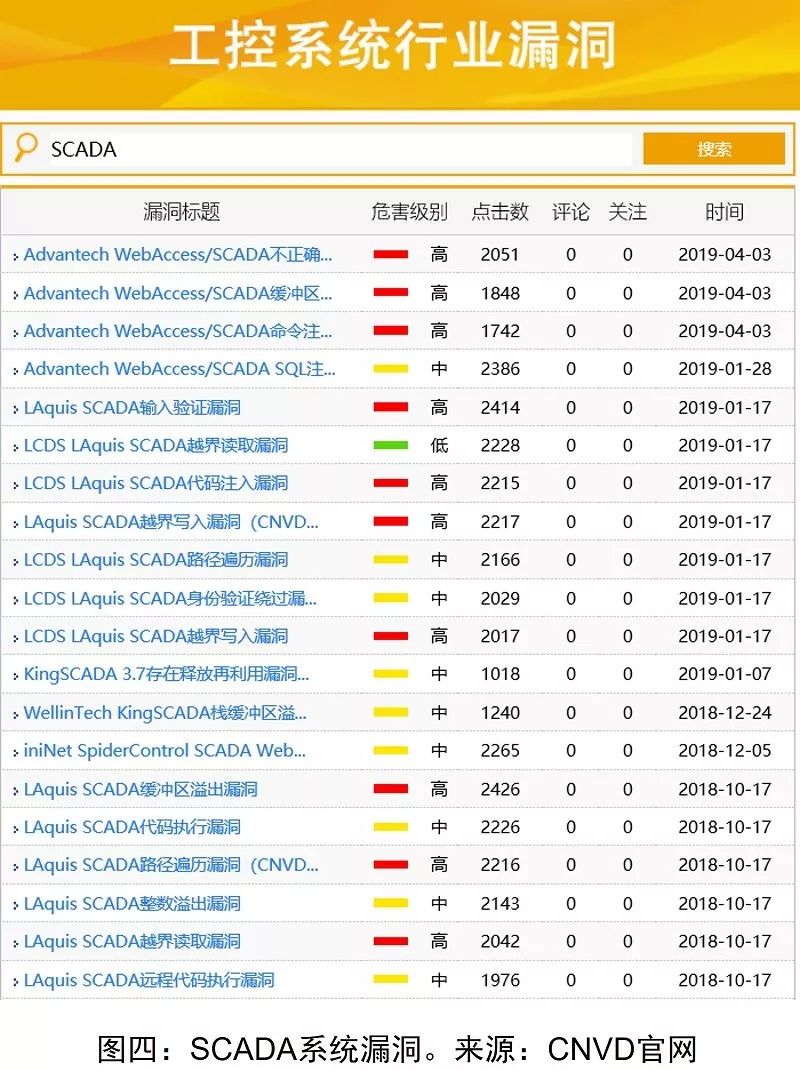
Threats at the Process Monitoring Layer
SCADA systems (Supervisory Control and Data Acquisition) are data collection and monitoring control systems within the architecture of industrial control systems. In the power system, SCADA systems are widely used. According to news reports, the Guri Hydroelectric Power Station in Venezuela currently uses SCADA systems to monitor and control the operating equipment on-site.
Many high-risk vulnerabilities have been reported in SCADA systems (see Figure 4), involving various aspects of software, hardware, firmware, etc., within the industrial control system architecture. Considering that upgrading or changing industrial control systems requires a long preparation and testing time, high personnel capability requirements, and impacts on continuous production, enterprises often adopt a conservative attitude towards vulnerability remediation, leading to these issues being hidden within SCADA systems. Once exploited by attackers, they may cause unpredictable impacts and losses.
3
Network and Communication Threats
Like other industrial control systems, the Guri Hydroelectric Power Station in Venezuela may also use different communication protocols and media. For example, the ModuleBus communication protocol is used to communicate directly with local I/O clusters via plastic optical cables. Attackers can analyze ModuleBus protocol messages, intercept control protocol messages, inject malicious code, tamper with messages, or cause accidents through malicious destruction.
4
Threats at the Production Management Layer
If the operating system where the production management system is located is not timely updated with security patches, it may have numerous risk vulnerabilities that can be exploited by attackers, leading to damage to production equipment and operations, rendering them unable to work normally. For instance, the WannaCry ransomware mentioned earlier exploited vulnerabilities in the Windows system’s SMB, causing systems to fail to operate normally. Another example is the (ms08-067) Windows Server service RPC request buffer overflow vulnerability, which attackers can remotely exploit to run arbitrary code, such as for worm attacks.
In addition, weak security awareness among operators, such as setting weak passwords, may also allow attackers to penetrate the production system environment and execute unauthorized operations, disrupting normal production order.
5
Threats from Management Deficiencies
The occurrence of such a large-scale power outage incident may also be due to deficiencies in security management. For example, the lack of a responsible person for security management of industrial control systems to supervise and manage the systems, weak employee security awareness; failure to establish effective security systems and processes for industrial control systems, leading to untimely upgrades and lack of effective protection; ineffective isolation of industrial control system networks from enterprise networks/internet; random connections of external devices, including mobile USB drives and CDs; insufficient attention to emergency response work for security incidents, and lack of effective emergency plans and drills.
6
Threats at the Field Device Layer
Given the current situation in Venezuela and the related international circumstances, there is a possibility of human sabotage. Since the power system is a critical support for modern society, it is an easy target for attackers. Additionally, the high complexity of the power system and its many exposure points increase the likelihood of being attacked, as power plants, substations, transmission and transformation equipment, and lines may all be subjected to physical, electromagnetic, and other forms of attacks.
7
Threats from Lack of Equipment Maintenance
The aging of equipment itself is also one of the hidden dangers that led to this large-scale power outage incident. According to news reports, the control equipment used in Venezuela may have been in use for decades. Without effective maintenance, it may lead to circuit short circuits, causing fires and other accidents.
8
0day Attack Threats
0day vulnerabilities refer to those that have been discovered by a few people but have not yet been publicly disclosed, and for which no official patches have been released. The security issues currently identified in industrial control systems are just the tip of the iceberg, and there are many potential unknown security vulnerabilities and threats. Therefore, this large-scale power outage incident may also have been caused by 0day vulnerabilities.

03 Global Industrial Control Security Standards and Compliance
United States
In May 2015, under the requirements of the Federal Information Security Modernization Act, the National Institute of Standards and Technology (NIST) released the “Guide to Industrial Control Systems Security” (NIST SP 800-82), providing security guidance for industrial control systems and their components (SCADA, DCS, PLC, and other terminals and intelligent electronic devices that perform control functions) to help enterprises reduce information security-related risks in industrial control systems.
The guide outlines the components and architecture of industrial control systems, identifies the threats and vulnerabilities faced by industrial control systems, and provides enterprises with reference methods, frameworks, and implementation steps in the following four areas:
-
Risk assessment and management of industrial control systems;
-
Development and implementation of industrial control system security projects;
-
Industrial control system security architecture;
-
Industrial control system security controls.
The guide is not aimed at compliance requirements for enterprises but has strong reference significance for enterprises to establish and implement industrial control system security management.
Europe
The discovery of the Stuxnet virus in 2010, which could infect industrial control systems, raised awareness of industrial control system security. To strengthen industrial control system security, the European Union Agency for Network and Information Security (ENISA) issued recommendations for protecting industrial control systems in December 2011. This recommendation outlines the security threats, risks, and challenges faced by industrial control systems and suggests that EU member states develop national-level industrial control system security strategies, establish industrial control security certification frameworks, and create best practices for industrial control security to improve existing weaknesses in industrial control systems.
Under the guidance of this recommendation, various EU countries have successively issued related security guidelines, such as the “Industrial Control System Security Compendium” published by the German Federal Office for Information Security in November 2013, which introduces industrial control systems and their components, the information security threats they face, and best practices for industrial control system security; and the “Managing Cybersecurity for Industrial Control Systems” published by the French Network and Information Security Agency (ANSSI) in January 2015, which provides support for enterprises to respond to industrial control system security risks. In September 2017, further industry-specific industrial control system practice guidelines were published—”ICS Cybersecurity: A Road Tunnel Case Study.”
EU countries have gradually established industrial control system security standards and best practices to provide guidance for enterprises within the EU to respond to industrial control security risks.
China
In October 2011, influenced by the Stuxnet virus incident, the Ministry of Industry and Information Technology of China (MIIT) recognized the severe situation of information security in industrial control systems and issued Document No. 451, “Notice on Strengthening the Management of Information Security in Industrial Control Systems,” which made a series of requirements for the connection management, network management, configuration management, equipment selection and upgrade management, data management, and emergency management of industrial control systems.
In October 2016, with the advancement of Industry 4.0, the State Council required further promotion of the integration of manufacturing and the internet. The MIIT issued the “Guidelines for Information Security Protection of Industrial Control Systems,” requiring enterprises using industrial control systems to carry out security protection work from eleven aspects, including the selection and management of security software, configuration and patch management, boundary security protection, physical and environmental security protection, identity authentication, remote access security, security monitoring and emergency plan drills, asset security, data security, supply chain management, and responsibility implementation.
In November 2016, the 24th meeting of the Standing Committee of the 12th National People’s Congress of China passed the “Cybersecurity Law of the People’s Republic of China,” which came into effect on June 1, 2017. This law clearly states that the state implements a cybersecurity grading protection system, emphasizing the security protection of critical information infrastructure.
In May 2017, under the requirements of the “Guiding Opinions of the State Council on Deepening the Integration of Manufacturing and the Internet,” the MIIT further issued the “Guidelines for Emergency Management of Information Security Incidents in Industrial Control Systems,” stating that industrial enterprises bear the main responsibility for industrial control security and should establish and improve the responsibility system for industrial control security, responsible for the emergency management of industrial control security in their units, and ensure the provision of human, financial, and material support. It also requires industrial enterprises to be able to immediately carry out emergency response for potential or occurring industrial control security incidents, striving to minimize losses. The guidelines also require industrial enterprises to formulate emergency plans for industrial control security incidents and regularly organize emergency drills.
In July 2017, the MIIT issued the “Management Measures for the Assessment of Information Security Protection Capabilities of Industrial Control Systems” (and its attachment “Assessment Methods for Information Security Protection Capabilities of Industrial Control Systems”), which regulates the assessment activities of industrial enterprises’ information security protection capabilities from the aspects of assessment management organization, assessment institutions and personnel requirements, assessment tools requirements, assessment work procedures, and supervision management, covering the evaluation of the security protection capabilities of industrial control systems at all stages of planning, design, construction, operation, and maintenance. According to relevant requirements, important industrial enterprises need to have their industrial control system security protection capabilities assessed by third-party institutions annually, while other industrial enterprises should conduct assessments at least once a year (self-assessment or third-party assessment).
In December 2017, the MIIT released the “Action Plan for Information Security in Industrial Control Systems (2018-2020),” requiring the implementation of the main responsibility of enterprises, establishing a responsibility system for industrial control security based on the “Cybersecurity Law,” clarifying the responsibilities of the enterprise’s legal representative and operational responsible person as the primary responsible person, forming management institutions, and improving management systems. The “Action Plan” also requires the establishment of a complete standard system, formulating standards for the grading of industrial control security, security requirements, security implementation, and security assessment.
On May 13, 2019, to implement the requirements of the “Cybersecurity Law,” the National Information Security Standardization Technical Committee (SAC/TC 260) jointly issued the “Information Security Technology Basic Requirements for Cybersecurity Grading Protection” (GB/T 22239-2019), which standardizes the principles and requirements for the grading protection of industrial control systems to ensure the security of system components and the overall system.
The above notifications, guidelines, and the “Cybersecurity Law” issued by the MIIT, the Ministry of Public Security, and SAC/TC260 together constitute the compliance requirements for enterprises using industrial control systems. In addition, enterprises can also refer to a series of national recommended standards issued by SAC/TC260, such as “Information Security Technology – Guidelines for Security Control Applications of Industrial Control Systems – GB/T 32919-2016,” “Implementation Guidelines for Risk Assessment of Industrial Control Systems – GB/T 36466-2018,” “Technical Requirements for Security of Industrial Control Network Isolation and Information Exchange Systems” (draft for comments), and “Guidelines for Information Security Inspection of Industrial Control Systems” (draft for comments).
International Standards
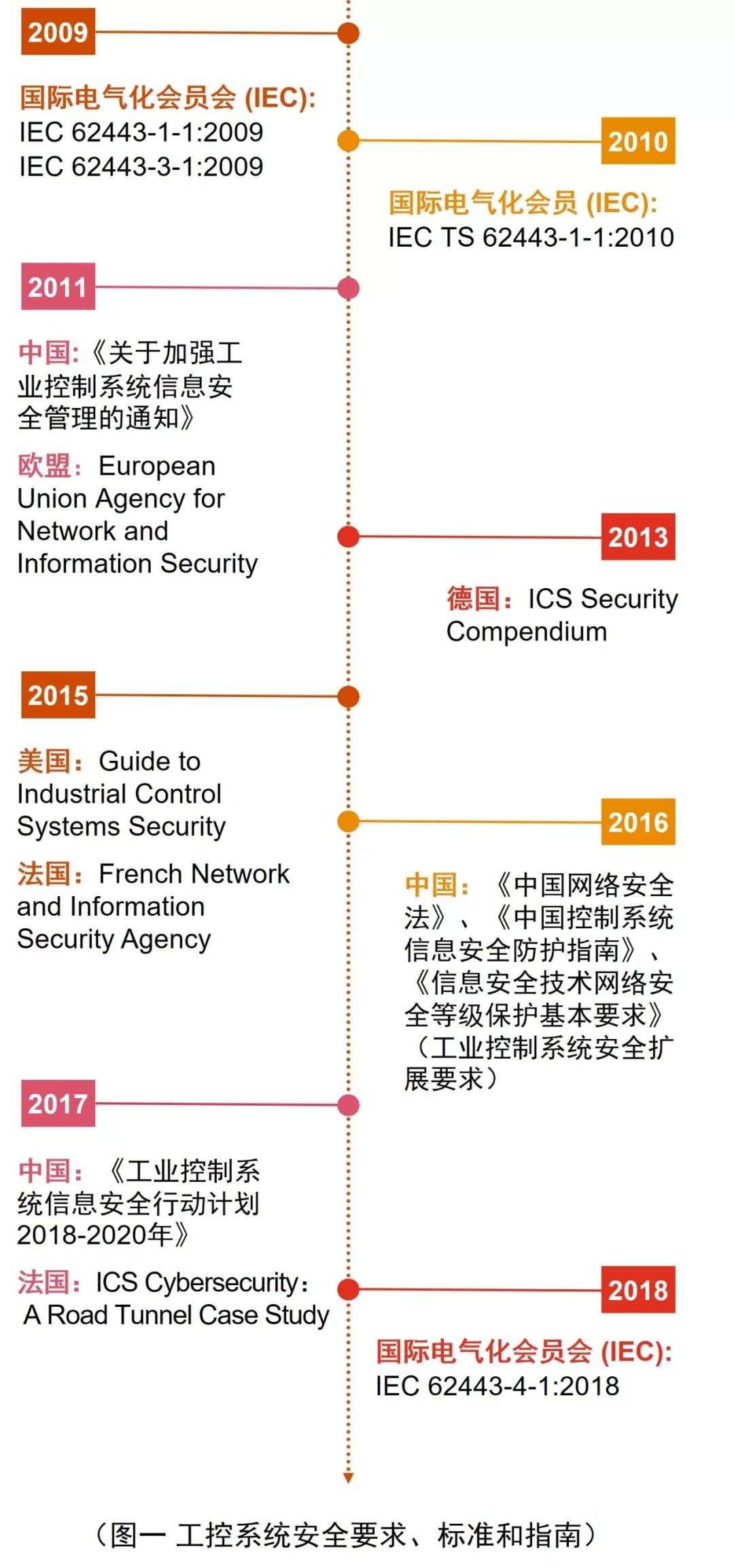
From July 2009 to January 2018, the International Electrotechnical Commission (IEC) successively released safety standards related to industrial control systems, including “Industrial Communication Networks – Network and System Security” (IEC-62443), which includes:
-
Part 1: Terminology, Concepts, and Models (IEC TS 62443-1-1:2009 Industrial communication networks – Network and system security – Part 1-1: Terminology, concepts, and models);
-
Part 2: Establishing Security Programs for Industrial Automation and Control Systems (IEC 62443-2-1:2010 Industrial communication networks – Network and system security – Part 2-1: Establishing an industrial automation and control system security program);
-
Part 3: Security Technologies for Industrial Automation and Control Systems (IEC TR 62443-3-1:2009 Industrial communication networks – Network and system security – Part 3-1: Security technologies for industrial automation and control systems);
-
Part 4: Security Product Development Lifecycle Requirements (IEC 62443-4-1:2018 Security for industrial automation and control systems – Part 4-1: Secure product development lifecycle requirements).
This standard system covers a wide range of aspects of industrial control systems and elaborates on the security requirements and corresponding security principles that enterprises can follow from risk assessment, personnel structure, system architecture, network design, security tools and software, data protection, etc. This standard system is also an important reference standard for countries to establish their industrial control system security standard systems.
Globally, the frequency of the release of standards and guidelines related to industrial control system security has been increasing in recent years. With the advancement of transformation and upgrading in major manufacturing countries, industrial control system security has been elevated to an increasingly important position. Enterprises using industrial control systems need to pay considerable attention to their industrial control system security to address the threats and challenges they face during transformation and upgrading.
Recommendations for Industrial Control System Security Systems
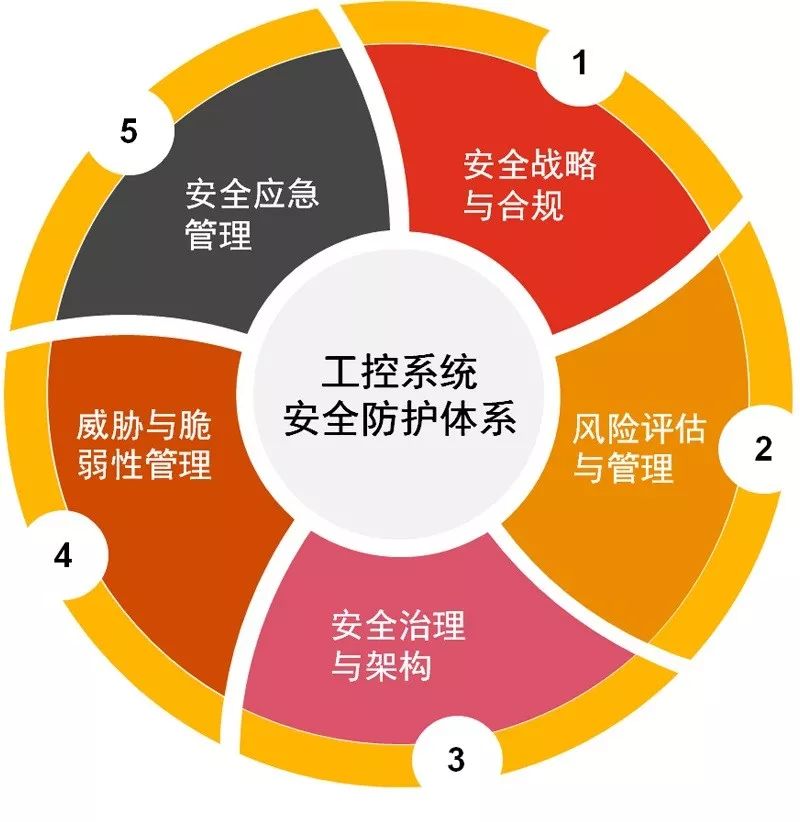
Based on the requirements, standards, and guidelines for industrial control system security issued by mainstream countries and regions as well as international organizations, PwC China recommends that enterprises using industrial control systems establish and implement suitable security protection systems to address industrial control system security risks. Enterprises can refer to the following model to establish their industrial control system security system (Figure 2).
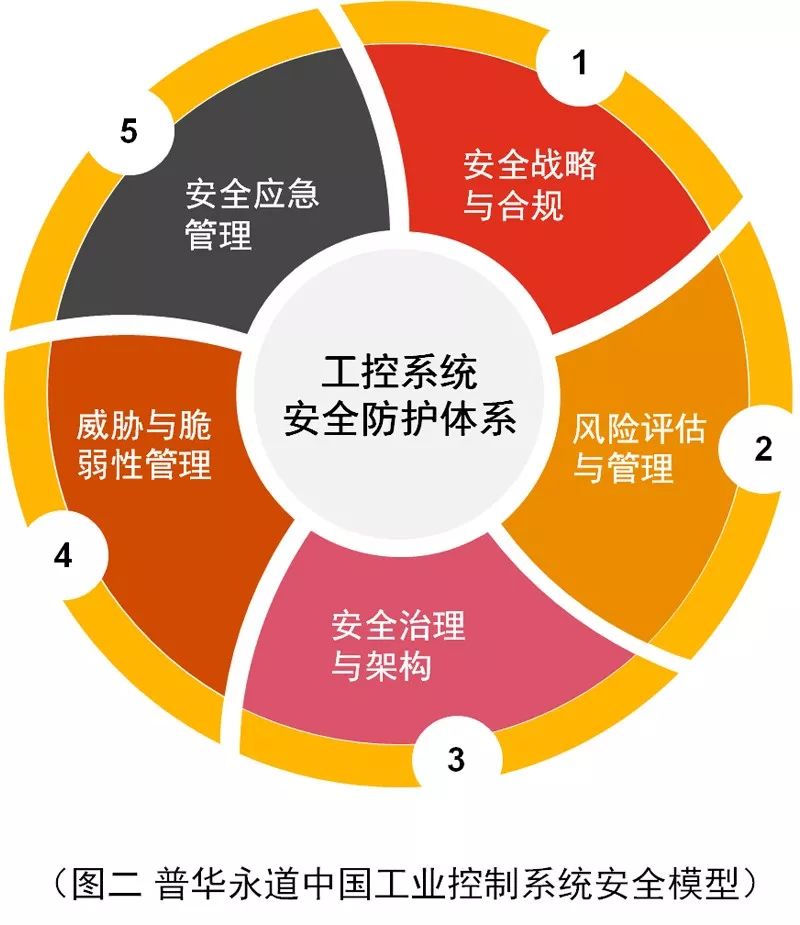

04 Security Risks and Protections of Industrial Control Systems
Vulnerabilities in Industrial Control System Security
According to the “Information Security Technology Basic Requirements for Cybersecurity Grading Protection” (GB/T 22239-2019), industrial control systems are divided into production management layer, process monitoring layer, field control layer, and field device layer, involving various components, applications, and communication protocols. If one link is not adequately protected, it may lead to the entire industrial control system being attacked, affecting production. Vulnerabilities involve both management and technical aspects:
-
Management vulnerabilities include: incomplete security policies and systems, unclear security responsibilities, weak security awareness, inadequate security publicity and training, insufficient management supervision, lack of supply chain management mechanisms, inadequate data protection and backup management, and lack of emergency response mechanisms;
-
Technical vulnerabilities include: unreasonable security architecture design, outdated operating systems, untimely security patches, inappropriate access control, inadequate virus or malware protection, insecure communication protocols, insufficient network boundary protection, inappropriate system configurations, weak physical and environmental protection, and missing or overly short log retention.
Threats to Industrial Control System Security
Threats may come from both external and internal sources, and may be malicious or non-malicious, caused by human factors or non-human factors (such as natural disasters).
Regarding human factors, external threats mainly refer to attackers exploiting vulnerabilities in industrial control systems through viruses (such as the Stuxnet virus, ransomware), phishing, etc., launching attacks (for example, Advanced Persistent Threats – APT attacks), penetrating into the industrial control system network, and performing unauthorized operations or malicious destruction. Attackers may include malware publishers, phishing or spam senders, botnet operators, criminal groups, etc.
Internal human factor threats mainly refer to disgruntled internal employees or industrial spies exploiting management or technical flaws in industrial control systems to maliciously retaliate by deleting core data of the enterprise or stealing core secrets for personal gain to sell to competitors. Additionally, due to the inherent vulnerabilities of industrial control systems, personnel may also cause damage and impact to industrial control systems due to non-malicious subjective intentions, such as operational errors.
Protection of Industrial Control Systems
To address the aforementioned vulnerabilities and threats, enterprises can establish appropriate security protection systems to reduce security risks and protect the safety of industrial control assets and normal production order. PwC China recommends that enterprises consider the following five aspects to establish and improve their industrial control security protection systems:
Security Strategy and Compliance
-
Security Strategy Planning: Plan the industrial control security strategy and objectives based on the enterprise’s own business strategy and IT strategy;
-
Security Compliance: Identify relevant regulatory requirements based on the industry and region of the enterprise, track updates, conduct gap analyses, and rectify identified issues to meet compliance requirements.
Risk Assessment and Management
-
Asset Identification: Identify industrial control-related assets such as equipment, hardware, software, data, communication protocols, documents, etc., and determine asset value;
-
Risk Identification: Identify vulnerabilities at the management and technical levels of industrial control systems, considering threats from both internal and external sources;
-
Risk Assessment: Based on the identified asset values and recognized vulnerabilities and threats, assess the likelihood and impact of risks occurring, and prioritize risks;
-
Risk Response: Based on the results of the risk assessment, plan appropriate response measures to control risks within acceptable limits.
Security Governance and Architecture
-
Organizational Structure: Establish an industrial control security management organization and responsible personnel, clarify and implement security management responsibilities, and supervise the effective operation of security management measures;
-
Systems and Processes: Develop industrial control security management systems and processes, including software and hardware management, identity authentication and access control management, data protection and backup management, configuration and patch management, network and communication management, equipment management, physical and environmental management, supply chain management, and security audits;
-
Technical Measures: Establish a comprehensive industrial control security technical architecture, including network and device monitoring, intrusion detection and protection, system configuration and updates, boundary protection, communication protection, security domain partitioning, application security, data security, log management, virus and malicious code prevention, and physical and environmental security;
-
Security Awareness: Establish an industrial control security training mechanism to enhance overall security awareness within the enterprise, including laws and regulations, enterprise security systems and processes, security incidents, and security technologies.
Threat and Vulnerability Management
-
Intelligence Collection: Continuously collect news, events, and vulnerabilities related to the security of the enterprise’s industrial control systems as references and basis for security protection;
-
Vulnerability Scanning: Use professional tools to design scanning windows, execute scans on devices, components, systems, and communication protocols within the industrial control system network to identify vulnerabilities and assess and prioritize their risks, taking corresponding response measures;
-
Penetration Testing: Through professional design, simulate real hacker attacks, attempt to breach existing security controls, and assess the system’s resistance to attacks;
-
Communication Protocol Vulnerability Analysis: Use professional tools to identify communication protocols within industrial control systems and analyze and assess their vulnerabilities.
Security Emergency Management
-
Emergency Team Establishment: Form an emergency team to manage and coordinate the enterprise’s industrial control security emergency work;
-
Risk Scenario Identification: Identify risk scenarios for industrial control security, including data loss, equipment damage, communication interruptions, production outages, natural disasters, etc.;
-
Plan Establishment: Based on the identified risk scenarios and the actual situation of the enterprise, formulate emergency plans for industrial control security incidents;
-
Emergency Drills: Conduct drills based on emergency plans and update the plans according to the drill results.
As enterprises’ business strategies, production management models, and information communication technologies continue to evolve, the industrial control security protection system should also be adjusted accordingly. Furthermore, Industry 4.0 will promote the application of emerging technologies in modern production, including IoT technology, 5G, AI, big data, and cloud computing.

05 The Industrial Future of Giants like Siemens, GE, and Bosch
Overview of Industry 4.0
Since the late 18th century, humanity has taken over 200 years to evolve industrial production from the steam age through the electrical and information ages to the intelligent era of Industry 4.0. The concept of Industry 4.0 was first proposed at the Hannover Fair in Germany in 2011, aiming to achieve intelligent production by integrating emerging technologies such as the internet, big data, cloud computing, and the Internet of Things with industrial production.
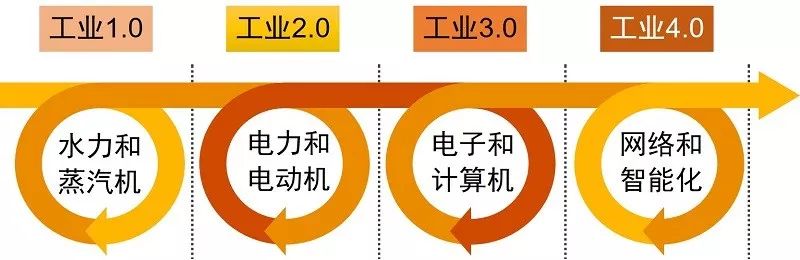
After the concept of Industry 4.0 was introduced, it attracted attention and responses from mainstream countries and regions worldwide, each formulating their own development strategies for “Industry 4.0” based on their national conditions, such as the U.S. Industrial Internet and China Manufacturing 2025.
Germany’s Industry 4.0 aims to establish intelligent production standards centered on Cyber-Physical Systems (CPS) to promote the transformation of manufacturing towards intelligence.
The U.S. Industrial Internet advocates connecting and managing people, data, and machines through IoT technologies and devices, achieving management and service throughout the entire product lifecycle, and reconstructing the value system of various links in the industrial chain.
China Manufacturing 2025 is a strategy proposed based on China’s national conditions, integrating innovation-driven, green development, structural optimization, and talent-based development strategies, promoting the integration of industrialization and informatization, focusing on the research and application of control systems, industrial software, industrial networks, industrial cloud services, and industrial big data platforms, and transforming into a strong industrial nation.
Enterprise Transformation
Some advanced enterprises globally have taken the lead in planning and formulating their own Industry 4.0 or similar development plans based on the strategies of their respective countries and regions. In April 2019, the Hannover Industrial Fair showcased over 5,000 exhibitors from more than 70 countries and regions, sharing their Industry 4.0 products and solutions, including IoT-based smart devices, smart factories, and security services.
After the concept of the Industrial Internet was proposed in the U.S., five leading companies established the Industrial Internet Consortium (IIC) in 2014, including GE, IBM, Cisco, Intel, and AT&T. The purpose is to plan development paths, empower technology, lower technical barriers, accelerate product commercialization, and promote the healthy development of the industrial internet. According to the IIC’s official website, as of April 2019, over 200 companies worldwide have joined the consortium. Here are some current transformation initiatives from leading companies in the consortium:
Siemens
-
Digital transformation of factories, utilizing emerging technologies such as Artificial Intelligence (AI) and Edge Computing to upgrade production equipment intelligently;
-
Mindsphere (PaaS) IoT open cloud platform, achieving interconnection between virtual and real, providing industrial applications and digital services;
-
IoT for industrial equipment, with its Sinamics product series, can connect frequency converters, drive chains, and machinery to Mindsphere through its communication modules, achieving interconnection between the physical and digital worlds to optimize analysis processes and maintenance strategies;
-
Industrial data services, assisting customers in implementing digital transformation.
Bosch
-
Bosch IoT Suite provides services such as device access, device management, access control, software upgrades, third-party integration, and IoT data analysis;
-
Its subsidiary Escrypt provides embedded security products and solutions.
GE
-
At the end of 2018, GE announced plans to establish a new company focused on developing industrial IoT software and related businesses, aiming to integrate GE’s industrial IoT solutions, including the Predix platform, Asset Performance Management (APM), Historian, automation (HMI/SCADA), Manufacturing Execution Systems, and Operational Performance Management.
Intel
-
Enterprise intelligent solutions help industrial enterprises apply big data, promote the integration of Information Technology (IT) and Operational Technology (OT), and address information security threats.
In addition, companies such as IBM, Amazon, Microsoft, and Hitachi have also successively launched IoT-related solutions.
In summary, we can see that under the environment of Industry 4.0, enterprises are developing towards intelligent production, smart factories, smart products, and digital transformation services, promoting the deep integration of industrial manufacturing and internet technologies. At the same time, with the expansion of IoT strategies, IoT security issues will also become more complex and severe, requiring enterprises to invest more time and effort to ensure the secure operation of intelligent production.
Domestically, under the guidance of the Ministry of Industry and Information Technology (MIIT), in February 2016, over a hundred units from the industrial, information communication, and internet sectors jointly initiated the establishment of the Alliance of Industrial Internet (AII), aiming to promote communication and deep cooperation among relevant entities, facilitate supply-demand matching and knowledge sharing, form complementary advantages, and effectively promote the development of the industrial internet industry, addressing practical issues faced by enterprises. Since its establishment, the number of members has exceeded 900, engaging in work across top-level design, technology research and development, standard formulation, and industrial practice, releasing multiple research results to support government decision-making and industrial development.
Future Industrial Outlook
With the rapid development of industry, emerging technologies such as Big Data Analysis, Cloud Computing, Edge Computing, 5G Networks, IoT Technologies, AI, and 3D Printing Technologies will also be widely applied in the industrial field.
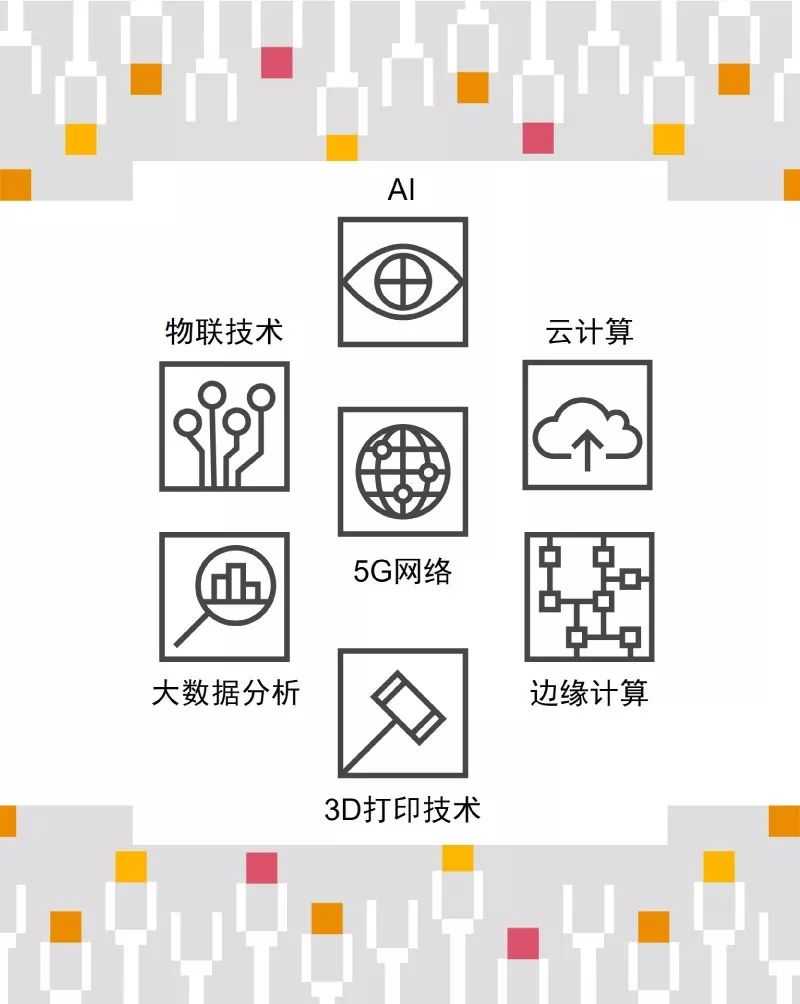
In traditional industrial system architecture, OT and IT devices are independent, and information is separated. In the future, Industry 4.0 will promote the realization of interconnectivity between things, interconnection of OT and IT information, and the integration of OT, IT, and CT (Communication Technology), greatly optimizing factory resource allocation.
In this process, IoT technology will become an indispensable part. Currently, IoT technology is widely applied in the consumer field, and many security vulnerabilities have been identified, such as exploiting security vulnerabilities in Tesla’s onboard IoT devices to achieve remote control of driving status and door locks. Therefore, while IoT technology brings many conveniences, it also introduces numerous security risks. Compared to the consumer field, the more complex industrial intelligent production field should pay more attention to the security issues of IoT technology and devices.
Countries are researching or have issued compliance requirements and management guidelines for IoT technologies and products. For example, the U.S. submitted the IoT Cybersecurity Improvement Act of 2019 for congressional review, and the China Academy of Information and Communications Technology issued the “IoT Security White Paper” in 2018, while the 2019 version of the multi-level protection scheme (MLPS 2.0) in China added IoT security extension requirements, indicating that global attention to IoT security is continuously increasing.
PwC China believes that in addition to the digital transformation of production and products mentioned above, Industry 4.0 will also drive transformations and changes in enterprise management concepts, organizational structures and functions, management systems, and processes. For instance, with the integration of OT and IT, the IT and OT departments will deepen collaboration in information security work; with the launch of smart products, security controls will be incorporated into the entire product lifecycle management, such as security design during the product development phase, security testing before market launch, and security upgrades during use; as leading enterprises advance their digital transformation, they will leverage their own experiences and technological accumulations to offer services to the market, assisting other enterprises in accelerating their digital transformation.
Humanity will enter an era of interconnectedness, and collaborative IoT security will be a long-term area of focus in the future.
References
1) NIST Special Publication 800-82—-Guide to Industrial Control Systems (ICS) Security
2) “Guidelines for Emergency Management of Information Security Incidents in Industrial Control Systems”
3) “Guidelines for Information Security Protection of Industrial Control Systems”
4) “Information Security Technology Basic Requirements for Cybersecurity Grading Protection” (GB/T 22239-2019)
5) “Industry 4.0 – The Future That Is Happening” by Xia Yanna and Zhao Sheng
6) Hannover Industrial Fair —- https://www.hannovermesse.de/en/news/key-topics/industrie-4.0/
7) Industrial Internet Consortium —- https://www.iiconsortium.org/members.htm
8) Siemens —- https://www.industry.siemens.com.cn/topics/cn/zh/future-of-manufacturing/Pages/future-of-manufacturing.aspx
9) Bosch —- https://www.bosch-iot-suite.com/
10) GE —- http://newsroom.ge.com.cn/
11) Intel —-https://www.intel.cn/content/www/cn/zh/manufacturing/manufacturing-industrial-overview.html
Hardcore Collection
ERP/PLM/MES/SCADA/PLC/Industrial Software Research Reports
Informationization, Digitalization, Intelligent Manufacturing, Industrial Internet Solutions
Automation, Informationization, Digitalization, Industrial Networks, Simulation and Virtual Debugging Introduction
WinCC Technology | Industrial Networks | MES Technology Related| Industrial Giants Strategic Layout | Industrial Communication Cases
Simulation and Virtual Debugging | Career Insights, Cognitive Improvement | Automation Control Standards Collection

2021 China Smart Manufacturing Industry Chain Research Report
2021-08-25

Industrial Data Collection (MES\