The Purdue model enhances ICS security through network segmentation and defense in depth to protect critical information infrastructure.
Explanation of the Purdue Model
What is the Purdue Model?
The Purdue model, also known as the Purdue Enterprise Reference Architecture (PERA), is a foundational framework for industrial control system (ICS) security. Developed by Purdue University in the 1990s, this layered model divides complex ICS environments into different zones or levels, each with specific security considerations. This structured approach simplifies network design, management, and communication among teams, enhancing the security and resilience of industrial operations.

Why is the Purdue Model Critical for ICS Security?
The Purdue model is indispensable for ICS security due to its multifaceted advantages:
- Defense in Depth: The model’s layered architecture creates multiple security checkpoints, making it harder for network threats to penetrate critical systems.
- Risk Mitigation: Isolation of critical components minimizes the likelihood of unauthorized access and accidental damage, ensuring operational integrity.
- Enhanced Visibility: The clear segmentation provided by the model aids in comprehensive monitoring and threat detection, enabling proactive incident response.
- Regulatory Compliance: Alignment with industry standards such as IEC 62443 ensures adherence to best practices and regulatory requirements.
- The Purdue model’s compatibility with industry standards like IEC 62443 promotes compliance with best practices and regulatory requirements.
- Synergy with IEC 62443 and other industry standards fosters adherence to best practices and regulatory requirements.
By adopting the Purdue model, organizations establish a robust cybersecurity foundation for their industrial environments.
The relevance of the Purdue model in today’s evolving cybersecurity landscape
Despite the rapidly changing nature of cyber threats, the Purdue model remains a cornerstone of industrial control system (ICS) security. Its adaptability and scalability make it suitable for organizations of various sizes, laying a solid foundation for protecting critical infrastructure.
In the face of technological advancements and evolving attack vectors, such as Advanced Persistent Threats (APT), ICS malware, and ransomware, the core principles of the Purdue model—segmentation, defense in depth, and risk management—are still crucial for mitigating cyber risks in industrial environments.
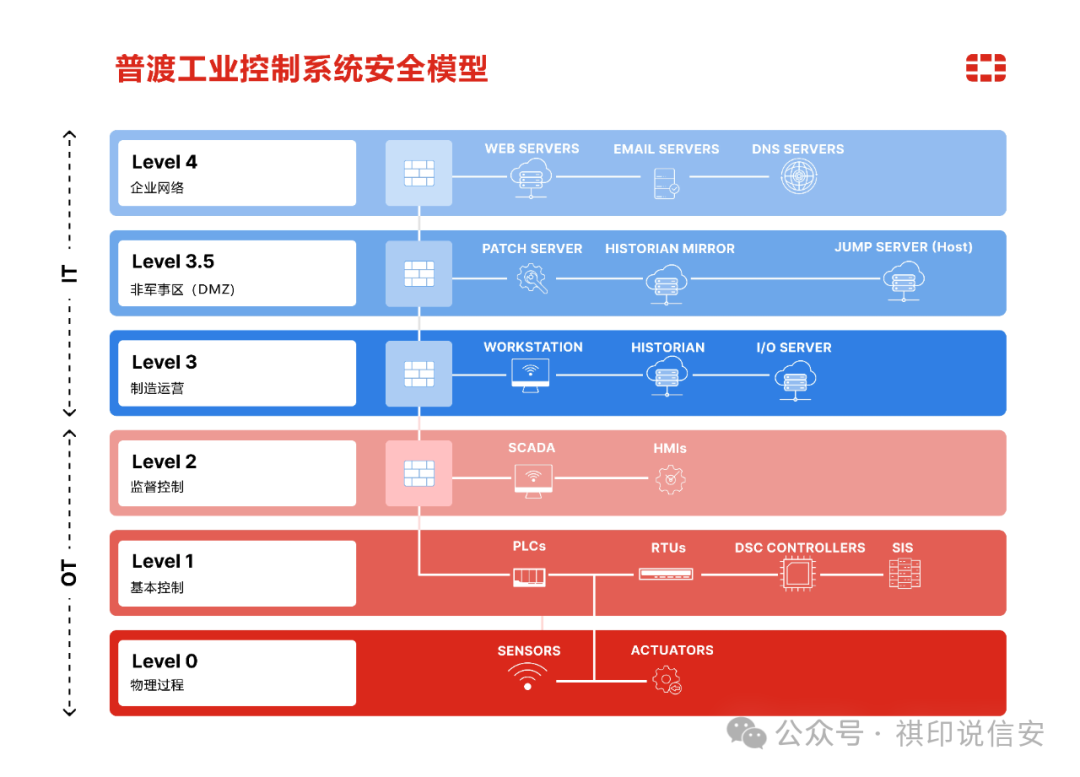
Layers and Zones in the Purdue Model
The strength of the Purdue model lies in its layered architecture, which systematically organizes industrial control system networks into different levels. Each layer represents a specific level of operational and information control, allowing for clear delineation of focus areas and facilitating precise security measures. The Purdue model’s cybersecurity framework is particularly important in defining these layers to guard against potential cyber threats.
Different Levels of the Purdue Model
The Purdue model consists of 5 levels, each with its unique roles and security considerations:
- Level 0: Physical Process:
- The foundational layer includes physical processes and devices. These devices are sensors, actuators, and field devices that interact directly with the physical world.
- Level 1: Basic Control:
- This layer includes controllers and Programmable Logic Controllers (PLC), responsible for automating various processes by converting sensor data into actionable commands.
- Level 2: Supervisory Control:
- This layer includes SCADA systems and Human-Machine Interfaces (HMI), aggregating data from controllers for process monitoring and control.
- Level 3: Manufacturing Operations:
- This layer includes Manufacturing Execution Systems (MES) and historical stations for managing and optimizing production processes, connecting enterprise systems and the shop floor.
- Level 3.5: Demilitarized Zone (DMZ):
- The DMZ acts as a security buffer between the ICS network and external networks, housing security devices such as firewalls and Intrusion Prevention Systems (IPS).
- Level 4: Enterprise Network:
- The enterprise network layer encompasses a broader IT infrastructure, including business applications and internet connectivity.
How the Purdue Model Segments Networks into Secure Zones
Network segmentation is fundamental to industrial control system (ICS) security, and the Purdue model creates different security zones within the ICS environment. This approach provides a defense-in-depth strategy that limits the impact of vulnerabilities and prevents attackers from moving laterally within the network.
Benefits of Network Segmentation:
§Containment: By isolating critical systems and processes, the Purdue network model helps prevent the spread of cyberattacks.
§Reduced Attack Surface: Limiting connections between zones reduces potential entry points for adversaries.
§Granular Access Control: Implementing access controls at each zone boundary restricts unauthorized access to sensitive areas.
Implementing Purdue University’s ICS Security Model
Adopting the Purdue reference model involves a systematic approach to network segmentation and security control implementation. By following its principles, organizations can protect their infrastructure and achieve operational resilience.
Key steps include:
- Conduct a Comprehensive Risk Assessment: Identify vulnerabilities, threats, and potential consequences to inform the selection of segmentation and security controls.
- Define Security Zones Based on Purdue Model Levels: Align network segments with the functional layers of the Purdue model, maintaining appropriate isolation and access control.
- Establish Secure Pipelines Between Zones: Implement firewalls, Intrusion Prevention Systems (IPS), and unidirectional data gateways to regulate and monitor communication between zones.
- Deploy Appropriate Security Controls at Each Level: Implement measures such as device hardening, access control, vulnerability management, and intrusion detection at each level of the Purdue model.
- Continuous Monitoring and Improvement: Regularly assess the effectiveness of security controls, conduct vulnerability assessments, and adjust security measures based on evolving threats.
Challenges Facing the Purdue Model and Modern Security Practices
While the Purdue model is foundational for industrial control system security, it is not without challenges. The ever-evolving threats necessitate the adoption of modern security practices to maintain its effectiveness.
Common ICS Security Challenges and How the Purdue Model Addresses Them
ICS environments face numerous security challenges, including:
- Legacy Protocols and Systems: Many ICS environments rely on legacy protocols and systems that were not designed with security in mind. These systems lack fundamental security features such as encryption, authentication, and access control, making them more vulnerable to cyberattacks.
- Limited Visibility and Patch Management: Due to the critical nature of industrial control system (ICS) operations, downtime required for patching or updating systems is minimized. This leads to limited visibility of vulnerabilities, delayed patch cycles, and exposes systems to potential threats.
- IT and OT Convergence: The increasing convergence of IT and OT networks has created new attack vectors. Attackers can exploit vulnerabilities in IT systems to access OT networks and disrupt operations, raising concerns about OT security.
How the Purdue Model Helps Address These Challenges
- Isolating Legacy Systems: By segmenting the network into zones, the Purdue model helps isolate legacy systems, limiting their exposure to potential threats and minimizing the impact of vulnerabilities.
- Enhancing Visibility: The model’s layered approach encourages the implementation of monitoring and logging in each zone. This can improve visibility into network activity and aid in threat detection.
- Securing External Connections: The secure pipelines and DMZ defined by the Purdue model create controlled access points for external connections, reducing the attack surface and allowing inspection of incoming and outgoing traffic.
- Controlling Access and Limiting Damage: The inherent granular access control and segmentation of the Purdue model can limit unauthorized access and mitigate potential damage from internal threats.
By leveraging the Purdue model, organizations can effectively address these common ICS security challenges and strengthen their overall cybersecurity posture.
Integrating Zero Trust with the Purdue Model
The Zero Trust security model is built on the principle of “never trust, always verify” and complements the Purdue model to enhance the security of industrial control systems (ICS). The Purdue model provides a structured framework for isolation and control, while Zero Trust adds an extra layer of protection by eliminating implicit trust and enforcing continuous verification.
By integrating Zero Trust principles, organizations can:
- Strengthen Network Micro-Segmentation: Implement granular access controls based on user identity, device health, and context to further restrict lateral movement, even within established Purdue model zones.
- Enhance Threat Detection and Response: Continuously monitor and analyze network traffic at each zone boundary, utilizing behavioral analysis and machine learning to identify anomalous activities indicative of potential threats.
- Achieve Secure Remote Access: Utilize strong authentication mechanisms, such as Multi-Factor Authentication (MFA), and enforce the principle of least privilege to minimize risks associated with remote connections to ICS environments.
Key Technologies for Enhancing ICS Security within the Purdue Model Framework
Implementing robust security measures at each level of the Purdue model requires a multifaceted approach, leveraging technologies specifically designed to address the unique challenges of ICS environments.
1.Robust Cybersecurity Tools
- Next-Generation Firewalls (NGFW): These advanced firewalls go beyond traditional packet filtering, providing deep packet inspection, intrusion prevention, and application control to defend against complex threats.
- Intrusion Prevention Systems (IPS): Dedicated systems for real-time proactive detection and prevention of network-based attacks.
- Virtual Private Networks (VPN): Securely connect remote users and sites to the ICS network, ensuring confidentiality and integrity of transmitted data.
- Security Information and Event Management (SIEM): SIEM platforms aggregate and analyze security logs from various sources, providing centralized visibility into network activity and facilitating incident response.
2.Effective Endpoint Security Measures
- Antivirus and Anti-Malware: Basic tools to protect endpoints from known threats.
- Endpoint Detection and Response (EDR): Advanced solutions that utilize behavioral analysis and machine learning to detect and respond to zero-day threats and sophisticated attacks.
- Host-Based Intrusion Prevention Systems (HIPS): Systems that actively monitor system activity and block malicious behavior in real-time.
- Application Whitelisting: Restrict the execution of unauthorized applications to prevent malicious code from running on critical systems.
3.Enhanced Access Control and Authentication
- Multi-Factor Authentication (MFA): Requires multiple forms of authentication to verify user identity and prevent unauthorized access.
- Role-Based Access Control (RBAC): Assigns permissions and access rights based on user roles and responsibilities, limiting access to sensitive data and systems.
- Privileged Access Management (PAM): Controls and monitors privileged accounts to minimize the risk of abuse and misuse of access.
4.Efficient Patch Management and Segmentation
- Vulnerability Management Solutions: Tools that scan for vulnerabilities and prioritize remediation efforts to keep systems up to date and prevent attacks on known vulnerabilities.
- Network Segmentation: Utilize VLANs, firewalls, or Software-Defined Networking (SDN) to create isolated zones within the network, limiting lateral movement of threats.
- Micro-Segmentation: Apply granular access controls based on individual workloads and applications to provide better isolation and protection.
5.Continuous Monitoring and Incident Response
- Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate incident response workflows, enabling faster and more effective threat containment.
- Threat Intelligence: Utilize threat intelligence sources to identify emerging threats and proactively update security policies and controls.
- Security Awareness Training: Educate employees on security best practices and the importance of adhering to security policies.
— Welcome to Follow Previous Reviews —2025 Collection Update of the White Paper Series from the Institute of Information and Communications (665 items) Download—— Level ProtectionTo achieve level protection, data classification and grading must be prioritizedDiscussing the relationship between important data identification and level protectionLevel protection is moving towards stricter regulation, clarifying the responsibilities of both parties in the evaluation process (mind map download)How to carry out level protection classification filing under the new situationLatest requirements from the Ministry of Public Security’s Cybersecurity Bureau for level protection work in 2025Public Network Security Document [2025] No. 1846: Clarification of risk hazards and work planPublic Network Security Document [2025] No. 1846: Clarification of data surveyPublic Network Security Document [2025] No. 1846: Clarification of fifth-level network systemsPublic Network Security Document [2025] No. 1846: Latest clarification on classification filingDiscussion on the clarification of the Ministry of Public Security’s Cybersecurity Bureau regarding level protection filing in 2025Public Network Security Document [2025] No. 1846: Further explanation of matters related to cybersecurity level protectionHas the new level protection evaluation really canceled scoring? A brief discussion!The new classification filing template clearly incorporates data security into the level protection systemThe new requirements and changes in the level protection classification filing template for 2025Discussion on how evaluation institutions can better meet local cybersecurity supervisionCybersecurity level protection: the relationship between level protection work, graded protection work, and password management workNew regulations in Henan Province regarding evaluation and budget for commercial confidentiality have been further reducedCalculation methods for budget evaluation in Sichuan Province for level evaluation and commercial confidentialityWhat is the budget for level evaluation and commercial confidentiality in Guangxi Zhuang Autonomous Region?What is the budget for level evaluation and commercial confidentiality in Heilongjiang Province?Discussing the “Opinions on Strengthening Information Security Assurance Work” with DeepseekDiscussing the “Implementation Opinions on Cybersecurity Level Protection Work” with DeepseekDiscussing the necessity of conducting level evaluations with Deepseek!—— Data Security
Interpretation of the “Regulations on Cyber Data Security Management”
The State Administration for Market Regulation issued the “Interim Measures for the Management of Compliance Data Reporting in Online Transactions”
Data Security Knowledge: What is Data Security?
Understanding Enterprise Data Catalogs
Cyber Police Reminder | March 31 World Backup Day: Pay Attention to Your Data Security
Cyber and Data Security Compliance: 15 Departments Issued Guidelines to Assist SMEs in Full Compliance
Data Security for Digital Copiers: A Guide for Enterprises
Legal Obligations Regarding Data Security Protection in the “Data Security Law”
—— Industrial Control SystemsOverview of Industrial Control System Security IEC 62443 StandardsUnderstanding the Emergency Plan for Data Security Incidents in the Industrial and Information Sector (Trial)Cybersecurity Knowledge: What is Industrial Control System (ICS) Cybersecurity?—— Errors and PenaltiesJiangsu Lianshui Rural Commercial Bank fined 1.145 million for violating cybersecurity and data security management regulationsHubei Xianning Rural Commercial Bank fined 53,100 for “violating credit security management regulations; data security management regulations”Two illegal enterprises in Beijing were legally investigated for unauthorized access vulnerabilities and other issues!China Construction Bank Anyang Branch fined 507,000 for multiple cybersecurity issues, including failure to implement level protection work and emergency plansSuixian Rural Credit Union fined 640,000, involving cybersecurity and data securityThe internet is not a lawless place! Pang Donglai wins the lawsuit, Duan is fined 400,000, both parties do not appeal for the time beingCybersecurity is no small matter! A certain enterprise was legally investigated for negligence in protectionJiangsu Guannan Rural Commercial Bank fined 975,000 for violating data security management regulations
Cybersecurity “insider” steals 208 million personal information
Three companies in Zhengzhou failed to fulfill cybersecurity protection obligations and were interviewed by the Cyberspace Administration
In 2025, two new companies in Zhengzhou violated the “Cybersecurity Law” and were administratively punished by the Municipal Cyberspace Administration
The Zhengzhou Municipal Cyberspace Administration legally interviewed relevant responsible units regarding cybersecurity issues
Two banks fined for data security-related issuesBaoding City, Hebei Province, interviewed the website responsible person according to lawGuigang City Cyberspace Administration published two typical cases of cybersecurity violationsPublic security organs severely crack down on crimes infringing on citizens’ personal information, with 10 typical cases publishedChongqing Cyberspace Administration recently conducted multiple interviews and penalties regarding enterprises’ illegal activitiesXinhua News Agency: China Telecom, China Mobile, and China Unicom collectively respond!
Chongqing Cyberspace Administration conducted a joint interview with public security regarding an enterprise system attacked by foreign organizations
—— Others
Discussing the “Four Laws, Four Regulations, Four Measures, and One Opinion” in relation to the Shandong Digital Government Construction Reform PlanHighlights: Qi Yin discusses cybersecurity before 2024Qi Yin discusses cybersecurity in 2024: A Year in ReviewCyber Police Reminder | March 31 World Backup Day: Pay Attention to Your Data SecurityCybersecurity Knowledge: What is Technical Debt?Cybersecurity Knowledge: Analysis of Cyber Threat IntelligenceFrom May 1, the “Regulations on National Secret Classification Management” will officially come into effectTop Ten Weak Passwords for Hacking Remote Servers