Follow+Star Public Account Number, don’t miss out on exciting content
Compiled by | strongerHuang
WeChat Public Account | Embedded Column
Today, we will summarize the commonly used symmetric encryption algorithms DES and AES, and the asymmetric encryption algorithm RSA.
Embedded Column
1
DES Encryption Algorithm1. Meaning of DESDES stands for Data Encryption Standard, which is a block algorithm that uses a key for encryption. It was established as a federal standard by the National Institute of Standards and Technology (NIST) in 1977 and authorized for use in non-classified government communications. Subsequently, this algorithm became widely adopted internationally.DES is a common symmetric encryption method, which is a block algorithm that uses a secret key for encryption. The key length is 64 bits, and any bits beyond this length are ignored. Symmetric encryption means that the encryption and decryption keys are the same. Symmetric encryption typically divides the string to be encrypted into blocks of fixed length. If the last block is not complete, it is padded with special characters.Common padding modes include: ‘pkcs5’, ‘pkcs7’, ‘iso10126’, ‘ansix923’, ‘zero’, including DES-ECB, DES-CBC, DES-CTR, DES-OFB, DES-CFB.2. Principles of DES AlgorithmThe input parameters for the DES algorithm are: Key, Data, Mode.The Key is 8 bytes, totaling 64 bits, and is the working key for the DES algorithm;The Data is also 8 bytes, 64 bits, and is the data to be encrypted or decrypted;The Mode is the working mode of DES, which can be either encryption or decryption. 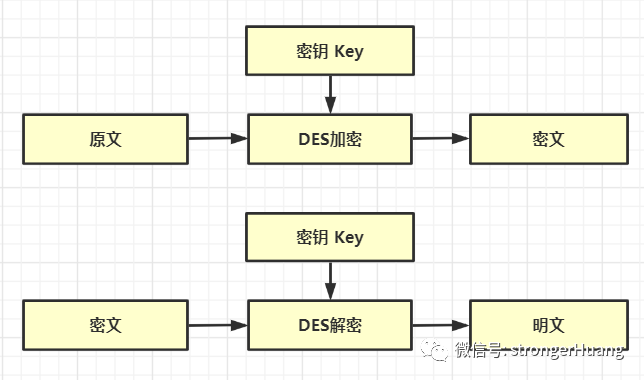 3. DES Encryption PrinciplesDES uses a 56-bit key along with an additional 8-bit parity bit, resulting in a maximum block size of 64 bits. It is an iterative block cipher that employs a technique called Feistel, where the encrypted text block is divided into two halves.A subkey is applied to one half using a round function, and the output is then XORed with the other half; the two halves are then swapped, and this process continues, except for the last round where no swap occurs. DES uses 16 rounds, employing XOR, permutation, substitution, and shifting operations as its four basic operations.4. Characteristics of DES AlgorithmShort block size, short key length, short password lifecycle, and relatively slow operation speed.
3. DES Encryption PrinciplesDES uses a 56-bit key along with an additional 8-bit parity bit, resulting in a maximum block size of 64 bits. It is an iterative block cipher that employs a technique called Feistel, where the encrypted text block is divided into two halves.A subkey is applied to one half using a round function, and the output is then XORed with the other half; the two halves are then swapped, and this process continues, except for the last round where no swap occurs. DES uses 16 rounds, employing XOR, permutation, substitution, and shifting operations as its four basic operations.4. Characteristics of DES AlgorithmShort block size, short key length, short password lifecycle, and relatively slow operation speed.
Embedded Column
2
AES Encryption Algorithm1. Meaning of AESAES, or Advanced Encryption Standard, also known as Rijndael encryption, is a block encryption standard adopted by the U.S. federal government. This standard was established to replace the original DES and has been widely analyzed and used globally.Strictly speaking, AES and Rijndael encryption are not exactly the same (although they can be used interchangeably in practice), as Rijndael can support a wider range of block and key lengths: AES has a fixed block length of 128 bits, and key lengths can be 128, 192, or 256 bits;while Rijndael allows key and block lengths to be multiples of 32 bits, with a minimum of 128 bits and a maximum of 256 bits. This includes AES-ECB, AES-CBC, AES-CTR, AES-OFB, AES-CFB.2. AES Encryption PrinciplesThe AES encryption process involves four operations: byte substitution, row shifting, column mixing, and round key addition. The decryption process involves the corresponding inverse operations. Since each step is reversible, the plaintext can be restored by performing the inverse operations in reverse order. The keys for each round of encryption and decryption are derived from the initial key expansion. The algorithm represents the 16 bytes of plaintext, ciphertext, and round keys as a 4×4 matrix.3. Characteristics of AES AlgorithmFast operation speed, high security, and low resource consumption.
Embedded Column
3
RSA Encryption Algorithm1. Meaning of RSAThe RSA encryption algorithm is an asymmetric encryption algorithm that is highly reliable; the longer the key, the harder it is to crack. According to disclosed literature, the longest RSA key that has been cracked is 768 binary bits.This means that keys longer than 768 bits are currently uncrackable (at least no one has publicly announced otherwise). Therefore, a 1024-bit RSA key is considered reasonably secure, while a 2048-bit key is extremely secure.2. Principles of RSA AlgorithmBefore understanding the principles of the RSA algorithm, it is important to understand the process of asymmetric encryption:Asymmetric encryption is achieved through two keys (public key – private key) for data encryption and decryption. The public key is used for encryption, while the private key is used for decryption. The reason why different keys can be used for asymmetric encryption and decryption is a mathematical issue. Different asymmetric encryption algorithms apply different mathematical principles. Now, let’s see how the RSA algorithm encrypts data. Below is a flowchart of the RSA encryption algorithm:
Below is a flowchart of the RSA encryption algorithm: 3. Characteristics of RSA Algorithm
3. Characteristics of RSA Algorithm
-
No need for key exchange, enhancing security
-
Can perform digital signature authentication
-
Encryption and decryption efficiency is not high, generally suitable for processing small amounts of data (e.g., keys)
-
Vulnerable to small exponent attacks
This concludes the summary of several common encryption algorithms. If you are interested in the specific processes of encryption, you can look up more algorithm knowledge online~Disclaimer: The materials in this article are sourced from the internet, and the copyright belongs to the original authors. If there are any copyright issues, please contact me for removal.———— END ————
Reply in the background with 『Software Algorithms』『Basic Knowledge of Embedded Software』 to read more related articles.
Welcome to follow my public account, reply “Join Group” to join the technical exchange group according to the rules, reply “1024” to see more content.Welcome to follow my video account:

Click “Read the Original” to see more shares, and feel free to share, bookmark, like, and view.