This article compares the performance of four commonly used encryption algorithms: DES, 3DES, Blowfish, and AES (Rijndael). By running several encryption settings to process data blocks of different sizes, the encryption/decryption speeds of the algorithms are evaluated and compared. The simulation is conducted using C#.
Keywords: Encryption Algorithms, Performance, Analysis, AES, DES, Blowfish, TripleDES, Cryptography
Introduction
As the importance and value of exchanging data over the Internet or other media types continue to grow, seeking optimal solutions to provide necessary protection against data theft attacks and timely service delivery has become one of the most active disciplines in security-related fields.
This article attempts to provide a fair comparison of the most commonly used algorithms in the field of data encryption. Since our primary focus is on the performance of these algorithms under different settings, the comparison considers the behavior and performance of the algorithms when using different data payloads.
Section 2 will briefly overview cryptography and its main uses in daily life; in addition, it will explain some of the most commonly used terms in cryptography and provide a brief description of each comparative algorithm to help readers understand the key differences between them.
Section 3 will present the results and conclusions from other contributions. Section 4 will introduce the installation environment and settings used, as well as the system components employed. Section 5 will outline the performance evaluation methods and selected settings for better comparison. Section 6 will provide an in-depth discussion of the simulation results, and finally, Section 7 will summarize the key points of this article and other relevant considerations.
Cryptography: Overview
This section will outline the main objectives behind the use of cryptography, as well as common terms used in the field.
Crytography is often referred to as the “study of secrets,” with the definition of encryption being of utmost importance today. Encryption is the process of converting plaintext “unhidden” into ciphertext “hidden” to protect it from data theft attacks. This process also includes a decryption part that is necessary to understand the encrypted text on the other end. Figure 1 illustrates a simple flow of common encryption algorithms.
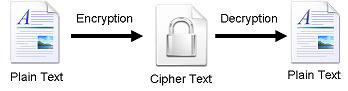
Figure 1: Encryption – Decryption Process
As defined in RFC 2828, an encryption system is “a set of encryption algorithms and a key management process that supports the use of algorithms in certain application environments.” This definition outlines the entire mechanism that provides the necessary level of security composed of network protocols and data encryption algorithms.
2.1 Objectives of Cryptography
This section introduces the five main objectives of using cryptographic techniques.
Every security system must provide a set of security features to ensure the system’s security. These features are commonly referred to as the objectives of the security system.
These objectives can be categorized into the following five main categories [Earle2005]:
Authentication: This means that the identities of both the sender and receiver should be verified before data is sent and received using the system.
Confidentiality: Generally, this feature is how most people recognize a security system. It means that only authenticated individuals can interpret the content of the message (data), while others cannot.
Integrity: Integrity means ensuring that the content of the communication data is not modified in any way between the endpoints (sender and receiver). The basic form of integrity is the checksum in IPv4 packets.
Non-repudiation: This feature means that both the sender and receiver cannot falsely deny having sent a certain message.
Service Reliability and Availability: Since security systems are often targeted by intruders, which may affect the availability and type of service for their users, such systems should provide a way to deliver the expected quality of service to users.
2.2 Block Ciphers and Stream Ciphers
One of the main classification methods for commonly used encryption techniques is based on the form of input data they operate on. These two types are block ciphers and stream ciphers. This section discusses the main functionalities of both types, namely the operation modes, and compares them in terms of security and performance.
2.2.1 Block Ciphers
Before describing the key characteristics of block ciphers, it is necessary to define ciphertext. “Cipher is the algorithm that performs encryption (the reverse is decryption)” [Wikipedia].
In this method, if the data comes in blocks, the data is encrypted and decrypted. In the simplest mode, you divide the plaintext into blocks and feed these blocks into the cipher system to generate ciphertext blocks.
ECB (Electronic Codebook Mode) is the basic form of block ciphers, directly encrypting data blocks to generate corresponding ciphertext blocks (as shown in Figure 2). More discussions on operation modes will follow.
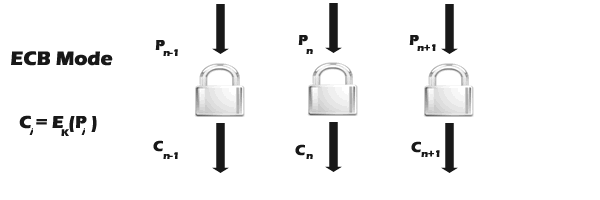
Figure 2: Block Cipher ECB Mode.
2.2.2 Stream Ciphers
Stream ciphers operate on data streams by processing them bit by bit. A stream cipher consists of two main parts: a keystream generator and a mixing function. The mixing function is usually just an XOR function, while the keystream generator is the main unit of stream cipher encryption technology.
For example, if the keystream generator produces a series of zeros, the output encrypted stream will be the same as the original plaintext. Figure 3 shows the operation of a simple mode in stream ciphers.
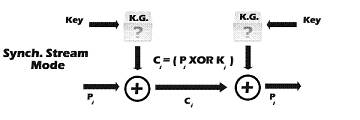
Figure 3: Stream Cipher (Simple Mode)
2.3 Operation Modes
This section explains the two most common operation modes in block cipher encryption—ECB and CBC—and briefly introduces other modes.
Block ciphers exhibit many differences, employing various techniques to enhance system security. The most commonly used methods include: ECB (Electronic Codebook Mode), CBC (Cipher Block Chaining Mode), and OFB (Output Feedback Mode).
ECB mode is where CBC mode uses the cipher block from the current encryption step as part of a chained encryption process. OFB operates on plaintext similar to stream ciphers, where the encryption key used in each step depends on the encryption key from the previous step.
Since this article primarily focuses on ECB and CBC modes, many other modes, such as CTR (Counter Mode), CFB (Cipher Feedback), or specific modes of 3DES, are not discussed in this article.
To be continued

How Papers Are Formed
How to Install the NTL Library on Ubuntu
Compiling NTL_11_3_2 Version on Windows
How to Detect Hidden Surveillance Cameras Using a Mobile Phone – Part 2
How to Detect Hidden Surveillance Cameras Using a Mobile Phone – Part 1
How to Steal Ethereum Wallet Keys – Part 3
How to Steal Ethereum Wallet Keys – Part 2
How to Steal Ethereum Wallet Keys – Part 1
NIST Lightweight Encryption Algorithm Standardization First Round Candidates
A Data-Driven Cryptocurrency Prediction Method – Part 3
A Data-Driven Cryptocurrency Prediction Method – Part 2
Welcome to Listen to the “Blockchain Talk” Program, the Most Quality Blockchain Knowledge Sharing Program in the Country.



Gemini Chain
Focusing on Cryptographic Technology on Blockchain
Long press the QR code to follow