Reading this article takes about 7.45 minutes.
Author: Ruan Yifeng http://www.ruanyifeng.com/blog/2012/06/internet_protocol_suite_part_ii.html This article is a supplement to the previous introduction to the TCP/IP protocol, expanding on various protocols to give everyone a global overview of network protocols.
The previous article analyzed the overall concept of the Internet, from the bottom up, discussing the design philosophy of each layer of protocols.
This was from the perspective of the designer. Today, I want to switch to the user’s perspective and see how users interact with these protocols from top to bottom.
01 A Summary
First, let’s summarize the previous content.
We already know that network communication involves exchanging data packets. Computer A sends a data packet to Computer B, which receives it and replies with a data packet, thus achieving communication between the two computers. The structure of the data packet is basically as follows:
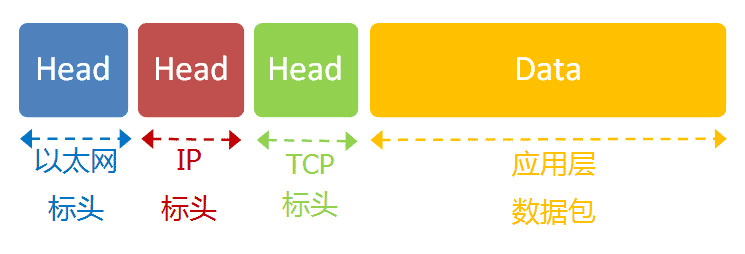
To send this packet, two addresses need to be known:
-
The MAC address of the other party
-
The IP address of the other party
With these two addresses, the data packet can be accurately delivered to the recipient. However, as mentioned earlier, MAC addresses have limitations. If the two computers are not on the same subnet, they cannot know each other’s MAC addresses and must rely on a gateway to forward the packets.
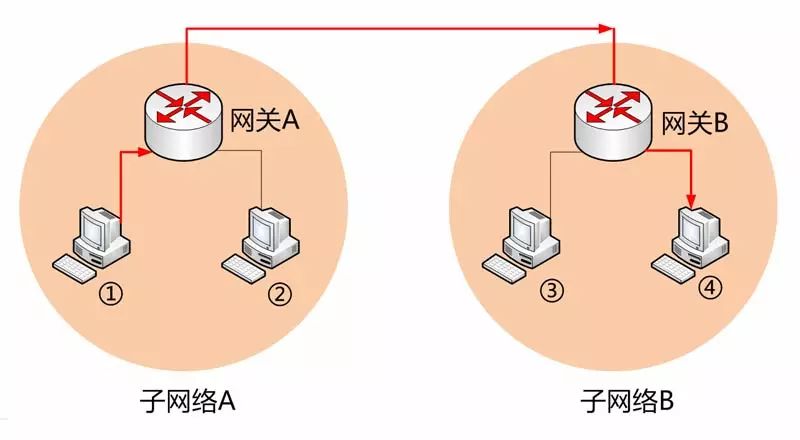
In the image above, Computer 1 wants to send a data packet to Computer 4. It first checks whether Computer 4 is on the same subnet and finds that it is not (the method for checking will be introduced later), so it sends this data packet to Gateway A. Gateway A discovers that Computer 4 is located in Subnet B through routing protocols and forwards the data packet to Gateway B, which then forwards it to Computer 4.
Computer 1 must know the MAC address of Gateway A to send the data packet to it. Therefore, the destination address of the data packet is actually divided into two scenarios:
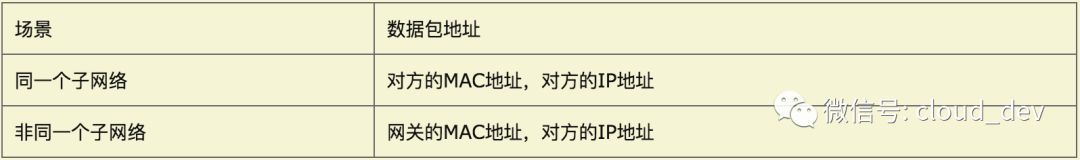
Before sending the data packet, the computer must determine whether the other party is on the same subnet and then choose the corresponding MAC address. Next, let’s look at how this process is completed in actual use.
02 User’s Internet Settings
2.1 Static IP Address
You buy a new computer, plug in the network cable, and turn it on. Can the computer access the Internet at this time?

Usually, you must make some settings. Sometimes, the administrator (or ISP) will tell you the following four parameters, and you fill them into the operating system, and the computer can connect to the Internet:
-
Local IP address
-
Subnet mask
-
Gateway’s IP address
-
DNS’s IP address
The image below shows the settings window for Windows systems.
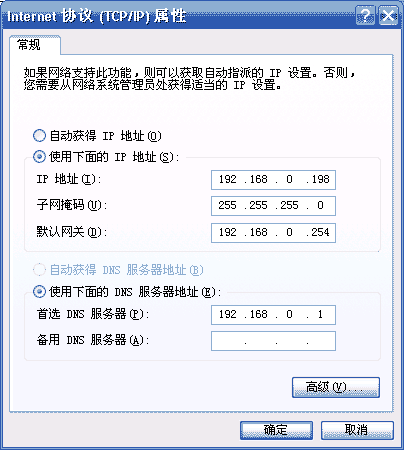
All four parameters are essential; the following sections will explain why knowing them is necessary for Internet access. Since they are given, the computer will always receive the same IP address each time it starts, so this situation is called “connecting to the Internet with a static IP address.”
However, such settings are very technical, and ordinary users find them daunting. Moreover, if one computer’s IP address remains unchanged, other computers cannot use that address, which is not flexible enough. For these two reasons, most users use “connecting to the Internet with a dynamic IP address.”
2.2 Dynamic IP Address
A “dynamic IP address” means that after the computer is turned on, it will automatically be assigned an IP address without manual configuration. The protocol used for this is called the DHCP protocol.
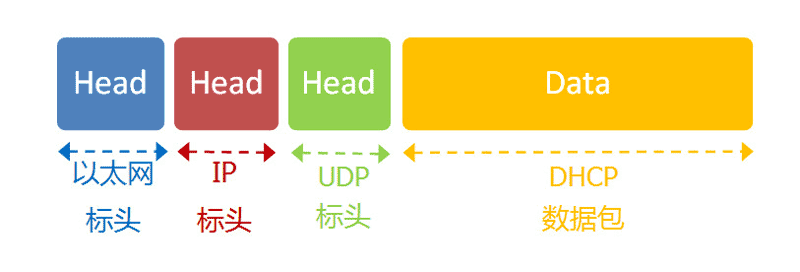
This protocol stipulates that in each subnet, there is a computer responsible for managing all the IP addresses in that network, called the “DHCP server.” A new computer joining the network must send a “DHCP request” data packet to the “DHCP server” to request an IP address and related network parameters.
As mentioned earlier, if two computers are in the same subnet, they must know each other’s MAC and IP addresses to send data packets. However, the newly joined computer does not know these two addresses; how can it send a data packet?
The DHCP protocol has made some clever provisions.
2.3 DHCP Protocol
First, it is an application layer protocol built on top of the UDP protocol, so the entire data packet is structured as follows:
(1) The “Ethernet header” at the front sets the sender (local machine) MAC address and the receiver (DHCP server) MAC address. The former is the MAC address of the local network card, and the latter is unknown at this time, so it fills in a broadcast address: FF-FF-FF-FF-FF-FF.
(2) The following “IP header” sets the sender’s IP address and the receiver’s IP address. At this time, both of these are unknown to the sender, so the sender’s IP address is set to 0.0.0.0, and the receiver’s IP address is set to 255.255.255.255.
(3) Finally, the “UDP header” sets the sender’s and receiver’s ports. This part is predefined by the DHCP protocol, with the sender being port 68 and the receiver being port 67.
Once this data packet is constructed, it can be sent. Ethernet broadcasts the packet, and every computer on the same subnet receives it. Because the receiver’s MAC address is FF-FF-FF-FF-FF-FF, which does not indicate who it is sent to, every computer that receives the packet must analyze the IP address to determine if it is meant for itself. When it sees that the sender’s IP address is 0.0.0.0 and the receiver’s is 255.255.255.255, the DHCP server knows “this packet is for me,” while other computers can discard the packet.
Next, the DHCP server reads the data content of this packet, allocates an IP address, and sends back a “DHCP response” data packet. The structure of this response packet is similar, with the Ethernet header containing the MAC addresses of both parties, the IP header containing the IP address of the DHCP server (sender) and 255.255.255.255 (receiver), and the UDP header ports being 67 (sender) and 68 (receiver), with the allocated IP address and specific parameters for the network included in the Data section.
The newly joined computer receives this response packet and thus knows its IP address, subnet mask, gateway address, DNS server, and other parameters.
2.4 Internet Settings: Summary
The key takeaway from this section is: whether it is a “static IP address” or a “dynamic IP address,” the primary step for the computer to access the Internet is to determine the four parameters. These four values are very important and worth repeating:
-
Local IP address
-
Subnet mask
-
Gateway’s IP address
-
DNS’s IP address
With these values, the computer can go “surfing” on the Internet. Next, let’s look at an example of how the Internet protocol operates when a user accesses a webpage.
03 An Example: Accessing a Webpage
3.1 Local Parameters
We assume that after the steps in the previous section, the user has set their network parameters:
-
Local IP address: 192.168.1.100
-
Subnet mask: 255.255.255.0
-
Gateway’s IP address: 192.168.1.1
-
DNS’s IP address: 8.8.8.8
Then they open a browser and want to access Google, entering the URL: www.google.com.
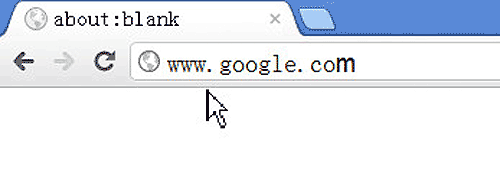
This means that the browser will send a data packet requesting a webpage to Google.
3.2 DNS Protocol
We know that to send a data packet, we must know the other party’s IP address. However, now we only know the URL www.google.com and do not know its IP address.
The DNS protocol can help us convert this URL into an IP address. Given that the DNS server is 8.8.8.8, we send a DNS data packet to this address (port 53).
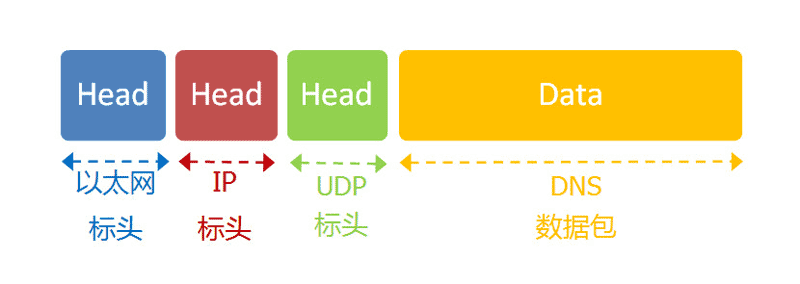
Then, the DNS server responds, telling us that Google’s IP address is 172.194.72.105. Thus, we now know the other party’s IP address.
3.3 Subnet Mask
Next, we need to determine whether this IP address is in the same subnet, which requires using the subnet mask.
Given that the subnet mask is 255.255.255.0, the local machine performs a binary AND operation with its IP address 192.168.1.100 (if both bits are 1, the result is 1; otherwise, it is 0), resulting in 192.168.1.0; then it performs an AND operation with Google’s IP address 172.194.72.105, resulting in 172.194.72.0. These two results are not equal, so the conclusion is that Google is not in the same subnet as the local machine.
Therefore, to send a data packet to Google, we must forward it through the gateway 192.168.1.1, meaning the recipient’s MAC address will be that of the gateway.
3.4 Application Layer Protocol
Browsing the web uses the HTTP protocol, and its entire data packet is constructed as follows:
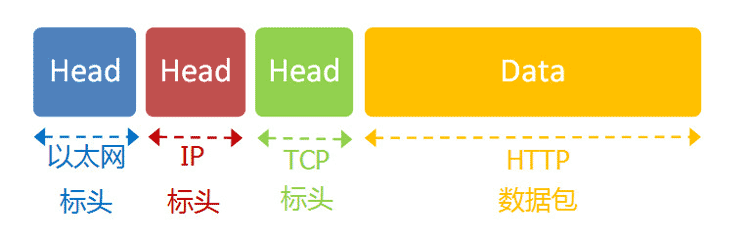
The HTTP content part is similar to the following:
GET / HTTP/1.1
Host: www.google.com
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 6.1) ......
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
Cookie: ... ...
We assume the length of this part is 4960 bytes, and it will be embedded in the TCP data packet.
3.5 TCP Protocol
The TCP data packet needs to set the ports; the recipient (Google) HTTP port is the default 80, while the sender (local machine) port is a randomly generated integer between 1024-65535, assumed to be 51775.
The TCP packet header length is 20 bytes, making the total length 4980 bytes when combined with the embedded HTTP packet.
3.6 IP Protocol
Next, the TCP packet is embedded in the IP packet. The IP packet needs to set both parties’ IP addresses, which are known: the sender is 192.168.1.100 (local machine), and the recipient is 172.194.72.105 (Google).
The IP packet header length is 20 bytes, making the total length 5000 bytes when combined with the embedded TCP packet.
3.7 Ethernet Protocol
Finally, the IP packet is embedded in the Ethernet packet. The Ethernet packet needs to set both parties’ MAC addresses, with the sender being the local machine’s network card MAC address and the recipient being the MAC address of the gateway 192.168.1.1 (obtained via the ARP protocol).
The data portion of the Ethernet packet has a maximum length of 1500 bytes, but the current IP packet length is 5000 bytes. Therefore, the IP packet must be split into four packets. Since each packet has its own IP header (20 bytes), the lengths of the four packets will be 1500, 1500, 1500, and 560 bytes respectively.
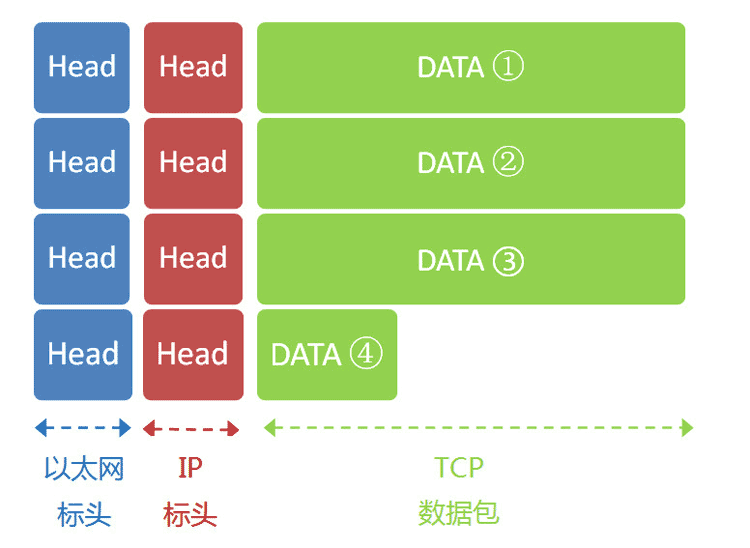
3.8 Server Response
After being forwarded through multiple gateways, Google’s server 172.194.72.105 receives these four Ethernet packets.
Based on the sequence numbers in the IP headers, Google reassembles the four packets, extracts the complete TCP packet, reads the “HTTP request” inside, and then generates an “HTTP response” to send back using the TCP protocol.
After the local machine receives the HTTP response, it can display the webpage, completing a network communication.
This example concludes here. Although simplified, it generally reflects the entire communication process of Internet protocols.
Reply “Join Group” to enter the expert group chat
Recommended Reading:
This article on TCP/IP network protocols is sufficient for an introduction
Comprehensive understanding of HTTP and HTTPS protocols, no more fear in interviews
Illustration of Kubernetes architecture
Illustration of Docker architecture
10T Technology Resources Giveaway! Including but not limited to: Cloud Computing, Virtualization, Microservices, Big Data, Networking, Linux, Docker, Kubernetes, Python, Go, C/C++, Shell, PPT, etc. Reply “1024” in the public account to get it for free!!