The Socket Security Team has disclosed that attackers are implementing destructive supply chain attacks through carefully disguised Go modules, with malicious code capable of completely wiping Linux system disks and causing permanent data loss.
Attack Technique Analysis
Complete Path of Malicious Modules:
-
<span>github.com/truthfulpharm/prototransform</span> -
<span>github.com/blankloggia/go-mcp</span> -
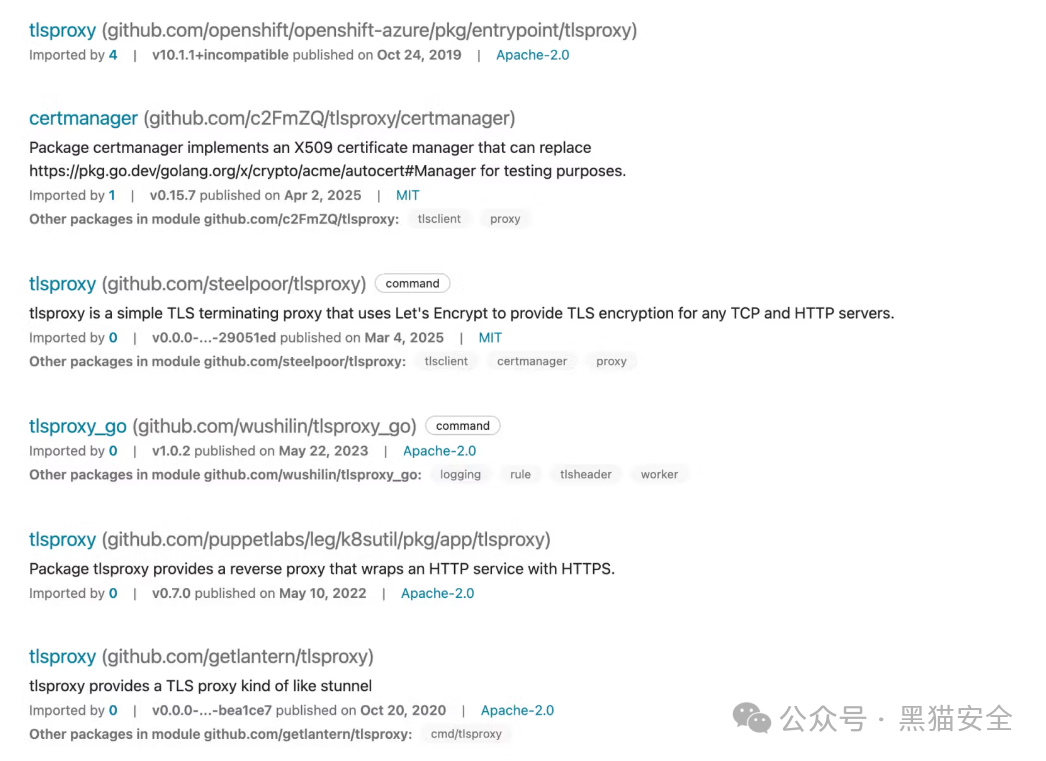
<span>github.com/steelpoor/tlsproxy</span>
1. Module Disguise
-
Imitating legitimate library names (such as
<span>go-mcp</span>,<span>tlsproxy</span>, etc.) -
Exploiting the decentralized nature of the Go ecosystem to create confusion in GitHub repository namespaces
-
Not a typical “typosquatting” attack, but rather inducing developers through semantically similar names
2. Multi-Stage Attack Chain
-
First, perform OS environment detection (effective only on Linux)
-
Pull secondary payloads from the attacker’s server
-
Execute irreversible disk overwrite (zeroing out /dev/sda)
3. Devastating Effects
-
All data on the main hard drive is overwritten with binary zeros
-
The system boot sector is damaged, leading to an inability to start
-
Exceeding conventional ransomware, directly causing permanent data destruction
Industry Warning
-
Namespace Confusion: The direct connection of Go modules to GitHub exacerbates the difficulty of distinguishing between real and fake libraries
-
Timeliness of Attacks: From dependency introduction to system paralysis can occur with a single build trigger
-
Defense Dilemma: Traditional code audits struggle to detect highly obfuscated malicious logic
Defense Recommendations
-
Establish a module whitelist system, disabling dependencies from non-authoritative sources
-
Execute CI/CD build processes in isolated environments
-
Deploy behavioral monitoring tools to detect abnormal disk operations
“The ability of such attacks to turn trusted code into devastating weapons marks a new phase in supply chain attacks. We must deeply integrate automated dependency analysis and runtime monitoring into the development lifecycle.” — Socket Threat Research Team