In today’s world, technology is rapidly evolving, and the demand for reliable, widely covered Internet of Things (IoT) networks is increasing day by day. Low Power Wide Area Networks (LPWAN) provide a low-power, low-cost, long-range wireless communication protocol aimed at IoT devices. LoRaWAN is a subset of LPWAN that can be easily integrated into existing system architectures and has achieved success in the real world, leading to its rapid adoption.
The “Helium Network” cryptocurrency blockchain incentivizes the financial aspects to accelerate the adoption and deployment of LoRaWAN in urban and rural areas, specifically by economically incentivizing gateway owners to establish redundant networks based on their homes and businesses. In addition to ease of deployment, the Helium Network enhances security by utilizing a public blockchain ledger to verify the identities of senders and receivers, preventing packet replay and man-in-the-middle attacks. This article demonstrates the effectiveness of the integration of LoRaWAN and Helium Network technology based on a real-world case of a robust and reliable global network and advocates for the Department of Defense (DoD) to adopt this technology combination to enhance situational awareness, establish real-time tactical networks, and monitor critical infrastructure and logistics. If the DoD chooses to integrate these two technologies with its existing IoT infrastructure, it can reliably, securely, and anonymously use LoRaWAN nodes and routers as a remote and backup encrypted communication network, supporting end-to-end encryption to AES-128 (DoD secret standard), thus gaining an information advantage in both domestic and international environments. The high performance and low cost demonstrated by LoRaWAN and Helium Network technology can greatly enhance the DoD’s mission to maintain lethality and advantage in information warfare.
The Internet of Things (IoT) is becoming an evolving technological wave, replacing traditional sensor-related technologies with low-cost, low-power wireless solutions that can be applied in various environments. Commercial and industrial sectors around the world have quickly adopted and adapted IoT technology to expand their businesses and provide new capabilities to customers. However, governments worldwide have been slow to adopt or consider using IoT for military purposes, with some countries even opposing it. The U.S. military is very interested in the operational integration of new weapon systems and communication networks, but so far, its investments have been limited to supporting smart military bases, critical infrastructure monitoring, and hardened sensors in deployment environments.
IoT devices have unique requirements, such as radio coverage, scalability, and power consumption, which may make deployment challenging. Emerging LPWAN technology is the future direction of wide-area low-power wireless communication. LoRaWAN is an open standard subset of LPWAN and LoRa that operates in globally unlicensed frequency bands (see Table 1), saving licensing costs, making the technology economically feasible, and deployable globally, similar to current remote IoT wireless communication technologies.
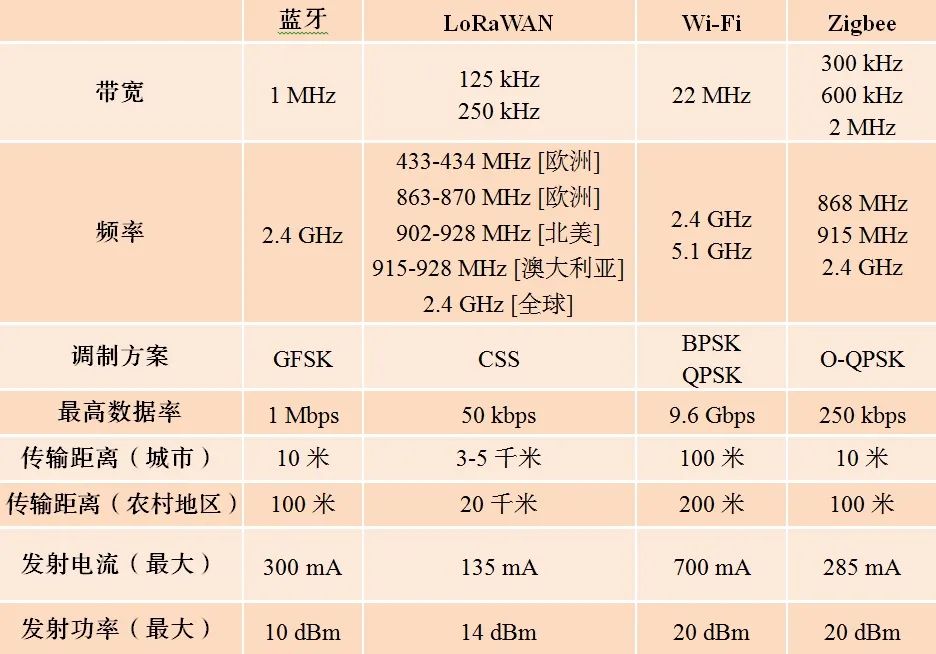
Table 1 compares several common wireless communication technologies. LoRaWAN devices have the following characteristics:
(1) Low Power: The low power consumption of the LoRaWAN protocol makes it the best candidate for supporting IoT devices. In fact, IoT devices with LoRaWAN capabilities consume much less power than devices using 4G/5G or ZigBee communication protocols.
(2) Low Cost: The low operating and manufacturing costs of LoRaWAN allow for more resources to be allocated to manufacturing IoT sensors, enabling end-users to deploy more or higher-quality IoT devices at the same net cost.
(3) Long Range: Compared to more common wireless communication protocols (such as Wi-Fi and Bluetooth), LoRaWAN has a relatively large coverage range (3-5 kilometers in urban areas, 20 kilometers in suburban areas), but requires minimal obstruction, ideally with a direct line of sight between the access point and the IoT device utilizing the network. LoRaWAN signals can be effectively reflected by a limited number of buildings, water bodies, and hills, further extending coverage.
(4) Enhanced Propagation and Signal Penetration: LoRaWAN operates in the unlicensed Sub-GHz ISM frequency band (see Table 1). Signals in this band can penetrate natural/man-made obstacles without significant signal loss, thus exhibiting enhanced signal propagation characteristics, capable of achieving sufficient coverage in urban or crowded areas.
Combining the advantages of LoRaWAN with encrypted blockchain (such as Helium Blockchain) can help people and organizations around the world achieve reliable IoT communication with high security and redundancy.
LoRa is the physical layer protocol used by LoRaWAN. LoRa is characterized by low-power operation, allowing devices to function for about 10 years on a single charge. Compared to other communication technologies, LoRa has a lower data rate, ranging from 20 to 50 kbps, depending on its modulation method. However, the communication distance of LoRa is extremely long (3-5 kilometers in urban areas, 20 kilometers in rural areas), which compensates for its low data rate. LoRaWAN networks adopt a star topology, utilizing access points, gateways, and nodes that support LPWAN, and maintain connectivity with internet servers via IP over Cellular or Ethernet. LoRaWAN uses AES-128 for end-to-end encryption, extending LoRa capabilities and adding a frame counter in the data packet for verification and to prevent replay attacks. The enhancement of security and remote capabilities makes LoRaWAN favored in remote areas where conventional access is restricted or sensitive data may be intercepted.
LoRaWAN has three different categories of devices (Class A, Class B, and Class C) that can be used for various applications and purposes:
Class A devices support bidirectional communication between terminal devices and gateways. Uplink messages from devices can be sent at any time. After uplink transmission, devices open two receive windows at Rx1 delay and Rx2 delay. The server chooses to respond in either window. Regardless of which window it chooses, the other window will be closed. Class A devices are typically battery-powered and have the lowest energy consumption compared to other types of devices. Most Class A devices operate in sleep mode, resulting in longer intervals between uplink transmissions.
Class B devices extend Class A device communication by time-synchronizing the reception windows for downlink messages from the server, and introduce multicast capabilities. Class B devices have lower latency, allowing messages to arrive at pre-set times and enabling downlink messages to be received at any time. Since such devices are accessed periodically, their battery life is shorter, and they spend more time in an active state.
Class C devices further extend Class B devices, with receive windows that remain open unless the terminal device is transmitting. This increases power consumption but allows for a reliable data stream between devices and gateways. Class C devices are typically powered by AC, as they remain active at all times, eliminating downlink latency.
As of July 2022, there are 173 network operators in 177 countries providing full LoRaWAN coverage for all three categories of LoRaWAN devices. This coverage is sufficient to meet the global operational and LoRaWAN system deployment needs of the DoD.
The security of communication systems is equally important as their availability and reliability. In light of this, the LoRaWAN standard was designed with security in mind, adhering to the principle of using standardized, rigorously reviewed algorithms and end-to-end security. Network access policies require mutual authentication before LoRaWAN terminal devices can connect to the LoRaWAN network. To prevent tampering, LoRaWAN messages undergo source authentication, integrity checks, and replay protection, and are encrypted to a maximum of AES-128 standards.
LoRaWAN networks implement multi-layer security measures at both software and hardware levels. Like most devices, the effectiveness of system security depends on the physical access of malicious actors. If devices (such as nodes, gateways, relays) are physically compromised, encryption keys are stored in secure elements (a type of tamper-resistant storage device), making them extremely difficult to extract.
The Helium Network is a wide-area network system supported by cryptocurrency, utilizing protocol tokens for data transmission.The Helium blockchain is a decentralized wireless network ledger designed to support LoRaWAN IoT devices.The Helium Network utilizes an open standardized wireless network protocol called WHIP for LoRaWAN business exchanges, earning a Helium cryptocurrency called Data Credit (DC).
When establishing bidirectional data transmission between terminal devices and the internet, DC is spent. The data transmission process is as follows: (1) Terminal devices spend DC to transmit data over the internet; (2) Gateway operators (“miners”) earn tokens for providing network coverage and supporting data transmission; (3) Miners earn Helium (HNT) tokens for verifying the coverage and data integrity of the Helium Network to avoid fraudulent proof-of-coverage (PoC) or illegal geolocation. Helium tokens can be exchanged for other cryptocurrencies or sold on cryptocurrency exchanges for fiat currency.
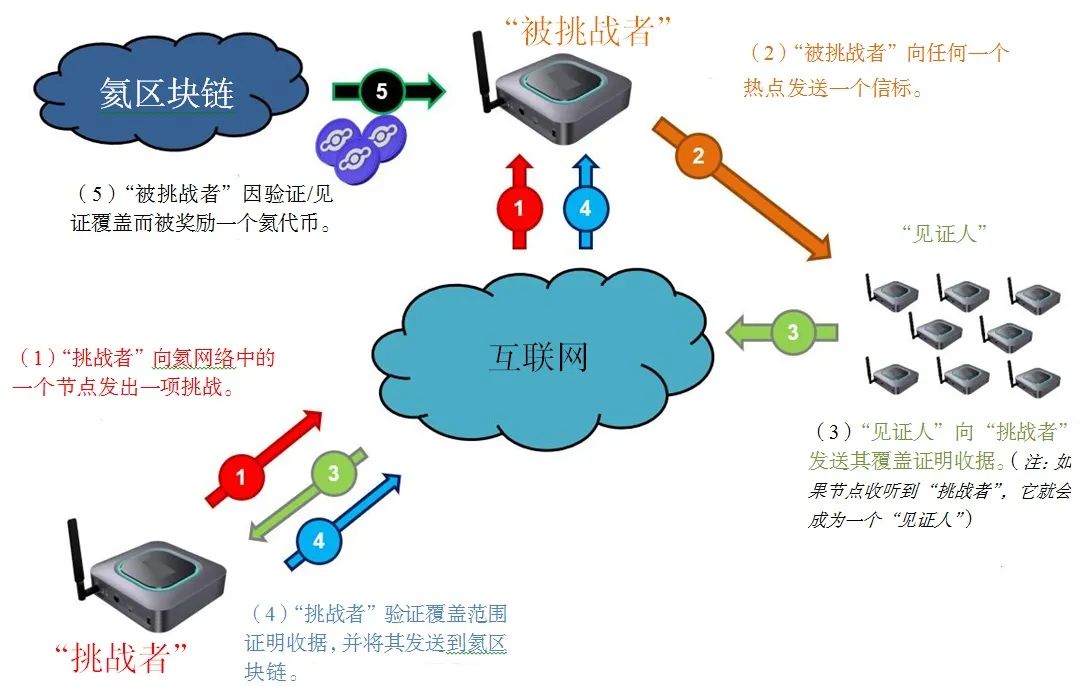
The components of the Helium Network establish network coverage proof as shown in Figure 2:
Terminal devices requesting data transmission over the internet utilize a “Challenged” (Transmitter) to test whether the Helium blockchain connection is functioning properly (ping). Another node called the “Challenger” verifies whether the “Challenged” is a reliable node on the LoRaWAN network. Nearby nodes known as “Witnesses” verify whether the “Challenger” and “Challenged” can effectively communicate. The “Challenger” issues a challenge to a node on the Helium network, and the “Challenged” sends a beacon to the “Witnesses”. The “Witnesses” then receive the beacon and send back a coverage proof receipt of the “Challenged” to the “Challenger”. The “Challenger” verifies this information and informs the Helium blockchain of success or failure. Finally, if the “Challenged” provides appropriate coverage proof, they receive Helium tokens as a reward.
For terminal devices utilizing the Helium Network for data transmission, as shown in Figure 3, the terminal devices must be able to communicate with LoRaWAN gateways and the Helium blockchain. The Helium Network operates on a paid communication model, consuming DC to use the network. Without connecting to the Helium Network, data cannot be exchanged between terminal devices and the internet.
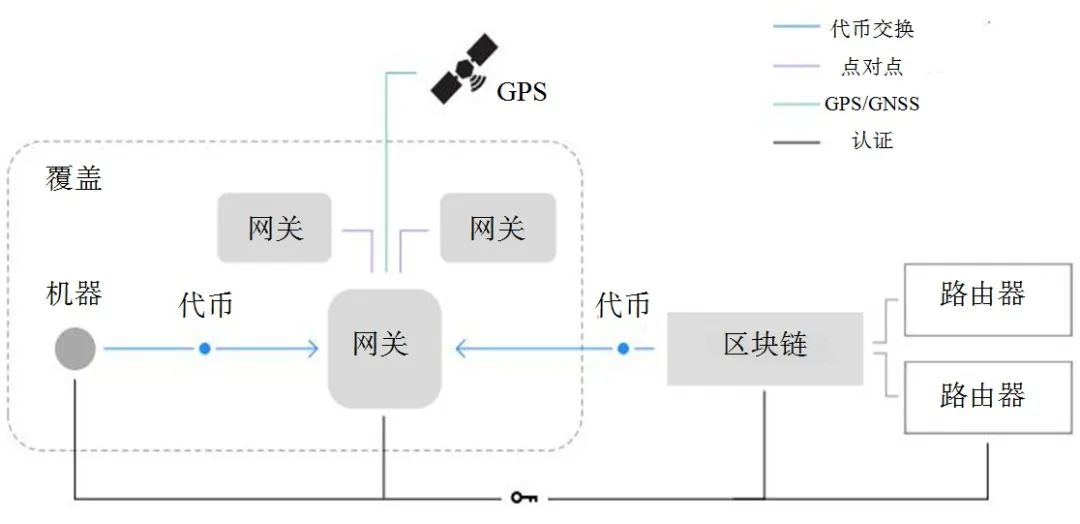
Figure 3 Helium Network Diagram
Whether in wartime or peacetime, the military is driven by information and requires timely information delivery.By introducing an IoT ecosystem supported by Helium blockchain, the DoD can create opportunities to obtain key information that has been challenging to access in the past.The DoD can apply LoRaWAN IoT devices in the following five key areas:
(1) Environmental Awareness: Accurately and timely collecting environmental data, such as real-time urban flood monitoring and early earthquake detection and monitoring using QuakeSense. Utilizing this technology allows real-time monitoring of precursor events and environmental parameters of natural disasters, assisting the DoD in timely coordinating disaster evacuations. With this additional informational capability, the DoD can effectively evacuate U.S. citizens before fatal events (such as wildfires, tornadoes, floods, and earthquakes) that impact its assets occur. Expanding the perception capabilities in the biological environment is crucial for monitoring migration patterns, weather conditions, and environmental survivability, which are critical for global operations. To ensure that the DoD’s smart bases and smart cities comply with environmental laws and policies, LoRaWAN allows them to “use public transport as mobile sensor nodes to monitor air quality in urban areas on a large scale.” Moreover, this type of monitoring can be conducted in tactical and humanitarian operations to verify information from forward teams and meteorologists, thus enhancing mission success probabilities and operational safety.
(2) Real-Time Tactical Information: The remote communication capabilities of LoRaWAN allow IoT devices to be deployed across multiple locations and various assets (such as personnel, vehicles, and buildings) to receive, transmit, and verify data. Since reliable Ethernet sources are often unavailable at deployment or training sites, satellite uplinks are needed to manage the internet uplink of these devices. When combined with other communication protocols, such as LoRaUAV using Wi-Fi and LoRaWAN, real-time information such as GPS and biometric data can be successfully transmitted and received from firefighters carrying portable LoRaWAN tags. In defense, LoRaWAN devices can be hardened and carried by deployed personnel to monitor pressure and vital signs, as well as location information, to avoid friendly fire incidents. In offense, LoRaWAN devices can be integrated into enemy infrastructure to monitor their movements and capabilities and identify potential opportunities to suppress/utilize their assets.
(3) Special care must be taken when using hardened LoRaWAN devices on the battlefield, as they risk being lost, captured by the enemy, or reverse-engineered. Hardened LoRaWAN devices require obfuscation of hardware/software modules to prevent and thwart any attempts at reverse engineering. Additionally, these hardened devices require extra encryption protocols to prevent signals from being intercepted and detected.
(4) Critical Infrastructure: The wireless signal coverage range of LoRaWAN and its ability to support multiple devices can enable effective monitoring of critical infrastructure such as electricity, gas, water, and sewage, for example, using smart infrastructure LoRaWAN to monitor access to urban sewer systems to enhance citizen response capabilities. LoRaWAN’s ability to handle Message Queue Telemetry Transport (MQTT) messages means that only minimal modifications are needed to existing IoT infrastructure; they may only require connecting a LoRaWAN antenna module. It is worth noting that the costs required for the DoD to implement this technology will be very low, and not much upgrade time is needed.
In November 2021, the DoD experienced a hazardous environmental disaster when over 14,000 gallons of jet fuel leaked from the Red Hill fuel storage facility in the underground tunnel at Joint Base Pearl Harbor-Hickam (JBPHH). During the cleanup, the jet fuel had already seeped into the JBPHH Navy water supply system. This fuel leak contaminated the drinking water systems for residents and businesses, with pollutant levels twice that of Hawaii’s drinking water health standards. The leak incident was initially unnoticed, and the contaminated water caused various health issues among military members, DoD contractors, and their families, leading to the evacuation of over 3,000 households until the problem was resolved. If LoRaWAN and Helium Network IoT sensors had been installed at the inlet and outlet tunnels and the water treatment plant, the pollutants would have been detected more quickly, and the contaminated water would have been reduced.
(5) Logistics Monitoring: LoRaWAN terminal devices and routers can also be integrated into stationary cargo aircraft and vehicles to actively generate Helium token cryptocurrency. Additionally, terminal devices can be integrated with cargo to automatically transmit logistics data to delivery and fueling locations, verifying the integrity of cargo shipments and providing accurate delivery timelines. For example, terminal devices can obtain item information for pallets and be able to send their location, loading conditions, and package item information to the aircraft’s LoRaWAN gateway or to the LoRaWAN gateway at a naval or air port. This will automate and standardize inventory management processes while ensuring accurate delivery times, proper cargo handling, and up-to-date inventory lists. Moreover, shipping logs will be automatically stored on the blockchain.
Introducing Helium Network and LoRaWAN wireless communication standards into the military domain will enhance the resilience and availability of digital communications but also increase the risks of data leakage and interception.
(1) LoRa Device Categories: Currently, there are three categories of available LoRa devices, and the DoD will be able to customize each system based on specific environments and use case models. Class A terminal devices are very suitable for environmental data collection, water resource monitoring, natural disaster early warning, and location tracking. The DoD can embed Class A devices in training environments where access is irregular and data demand is low. Furthermore, these devices can be used to detect seismic activity, such as using heavy vehicles or during explosions. Class A devices can also be used to detect and record the presence of chemical, biological, radiological, and nuclear (CBRN) agents. The challenge of using Class A devices in remote areas is the integrity of batteries and the ability to recharge or replace depleted energy. Class B terminal devices can be applied in smart bases and smart cities; these devices can wirelessly connect to the smart metering systems of major utilities while utilizing public blockchain to verify the readings and timing information of smart metering systems. This system will enhance the integrity of resource audits and provide accurate statistics to identify system failures or utility abuse. Interconnecting systems in underground and urban environments remains challenging, but the remote capabilities of LoRaWAN can address this issue. Class C terminal devices are widely used in areas where power consumption is not a concern. In addition to applying dedicated Class C devices to the IoT ecosystem, the DoD can also choose to integrate LoRaWAN modules into existing IoT and Supervisory Control and Data Acquisition (SCADA) devices. This will introduce remote monitoring and real-time configuration capabilities for critical infrastructure systems. This system integration also provides an additional communication platform while establishing a blockchain-supported recording feature to verify system changes, detect unauthorized access, and report system anomalies in real-time. This type of LoRaWAN device can connect to geographically dispersed critical infrastructure nodes that traditional wireless networks cannot reach.
(2) Integrated Use of Civilian and Government Gateways: By decentralizing network establishment and maintenance functions to gateway owners, the U.S. military can save significant amounts of money and time. As mentioned earlier, due to the sensitivity of DoD information, information augmentation (terminal encryption and covert communication) may be required to ensure security and functionality. While the Helium Network is primarily maintained by civilians and non-interested parties, the DoD cannot rule out the possibility of malicious actors conducting espionage or sabotage through hosted gateways. The DoD will be able to help improve network reliability and enhance data security by purchasing gateways and maintaining its own infrastructure. Additionally, the DoD’s communication department or other government agencies can maintain gateways to earn cryptocurrency incentives to alleviate budget constraints.
(3) Paid Communication Model: Since Class A LoRa devices typically transmit information irregularly, they can adopt a paid communication model for cost-effectiveness. The downside of this model is that if devices run out of their data credit balance (DC balance) or cannot access the Helium Network, they cannot transmit information on the network. This remains a significant barrier to integration with military systems. Appropriate amounts of DC need to be pre-allocated to terminal devices, which must then be increased as needed. Furthermore, depending on the “mining” capabilities of LoRaWAN gateways, the DoD may need to self-fund DC to maintain device operations. The paid communication model of the Helium Network requires ongoing maintenance and monitoring, which will increase the management burden on DoD personnel. Due to the above limitations, the DoD needs to establish a government-exclusive LoRaWAN network modeled on the Helium Network that only allows whitelisted devices to connect to its network without adopting the paid communication model.
(4) Hardened LoRaWAN and Sensitive Operations: In deployed or harsh environments, the DoD requires hardened LoRaWAN devices with enhanced security features. Ideally, the DoD will set up non-Helium network devices to prevent exposing the military’s presence and communication capabilities on publicly available blockchains. Since most LoRaWAN devices can operate with or without the Helium Network, it is recommended to use this network for smart military bases/cities, critical infrastructure, humanitarian missions, and non-combat expeditionary operations. Before use in combat environments, modifications to the Helium Network and LoRaWAN devices are required to prevent the inadvertent leakage of sensitive information or asset locations.
(5) Network Security Issues: Attacks on LoRaWAN include replay, eavesdropping, packet modification, ACK spoofing, and battery exhaustion. The greatest weakness of LoRaWAN terminal devices and gateways is unauthorized physical access. If an attacker gains access to nodes, gateways, or servers, and they do not employ robust hardware security strategies, the entire device or even the network must be considered compromised.
If adversaries can successfully record wireless LoRaWAN communications between terminal devices and gateways, they can retransmit malicious messages simulating the following attributes: 1) device address; 2) session key; and 3) incrementing counter values. Replay attacks can be devastating, potentially leading to denial of service and possibly exposing the configuration and location of terminal devices.
If attackers cannot successfully intercept and decode messages, they may use ACK spoofing attacks to selectively disrupt LoRaWAN terminal devices. Additionally, attackers may choose to introduce malicious terminal devices into the network ecosystem, using random or extreme wake time values to quickly exhaust the battery of the target terminal device. This attack also leads to network congestion and increases the wireless transmission coverage, making LoRaWAN transmissions easier to triangulate and intercept.
LoRaWAN is one of the few IoT networks that uses standardized AES-128 encryption algorithms, particularly AppKey, to achieve the DoD’s secret-level end-to-end encryption. This level of encryption enables the DoD to transmit sensitive data when traditional communication methods are unavailable. Furthermore, the high physical security of LoRaWAN supports the DoD’s anti-tampering missions.
LoRaWAN and Helium Network are two technologies that provide secure end-to-end encryption while also building on existing IoT communication infrastructure.The current technology combination limits the secure use of domestic infrastructure and non-sensitive operations.The DoD may explore creating its own blockchain in the future to achieve tamper-proof communication, enhance anonymity, and increase control.
Additionally, the DoD may research integrating LoRaWAN and Helium Network technology into existing communication infrastructure for personnel monitoring and critical infrastructure awareness, enhancing MQTT IoT terminal devices. Finally, the DoD may simultaneously construct a Helium Network and its proprietary blockchain-supported network to further enhance information advantages and establish partnerships with public and private entities.
To further advance the DoD’s utilization of LoRaWAN and blockchain technology, it is necessary to test the reliability of communication systems and the security of hardware and software components. While this technology is widely popular in the civilian sector, it must be emphasized that this system can continue to be used in various environments. Like any wireless communication standard, security issues related to sensitive data and sensitive operations must be studied and addressed.
The unique combination of LoRaWAN and Helium Network technology can address the IoT challenges faced by the DoD to enhance its lethality and information advantage.By appropriately constructing the IoT ecosystem, the DoD will be able to create new wireless communication standards based on existing Helium Network technology.This technological integration provides efficient solutions for emergency management, real-time battlefield information, and critical infrastructure protection and monitoring, while the DoD can efficiently deploy high-quality devices with minimal installation and maintenance costs and minimal equipment modifications, providing critical support to combat personnel and base staff.The DoD will benefit from this and will continue to harness the tremendous potential of LoRaWAN and Helium Network technology to create smart military bases, save more lives, and implement efficient monitoring of national critical infrastructure both domestically and internationally.

(This article is compiled from internet materials for reference only, and the views expressed do not represent the position of this public account)

