Consideration: What Functions Should an IoT Gateway Have?What Functions Should an IoT Security Gateway Have?

Part One: Functions That an IoT Security Gateway Should Have
★ Basic Functions:
1、Southbound heterogeneous device access. Ensure the network can accommodate sensing devices using different protocols.
2、Northbound multi-path transmission. Support various connections to the cloud, including Ethernet, 4G/5G, etc.
3、Application layer protocol support. Support protocols such as MQTT, CoAP, HTTP, XMPP, etc.
4、Unified management. Management platform for overseeing all security gateways, including gateway upgrades, configurations, etc.
★ Security Functions:
1、Access control. Identify legitimate sensing devices accessing the platform. (It’s important to distinguish between access and admission; access refers to communication attributes, while admission pertains to security attributes, such as using sensor data characteristics and behavioral habits for access control)
2、Transmission encryption. Provide professional transmission encryption capabilities, such as national cryptography algorithms. Most IoT sensing devices or gateways do not implement professional encryption during data interactions; some may use simple encryption operations.
3、Intrusion detection. Provide intrusion detection capabilities.
4、Vulnerability scanning. Gateways periodically scan sensing devices for security vulnerabilities.
5、Firewall. Basic access control and firewall functions.
6、Protocol recognition. Support analysis capabilities for various IoT protocols.
7、 Self-security. Ensure the security of the system itself, firmware security, functional security, trusted boot, etc.
★ Advanced Functions:
1、AI analysis. Provide edge computing and decision-making capabilities, supporting cloud-edge coordination.
2、 Data storage. Provide local video storage capabilities in video scenarios.
3、Video processing. Provide video codec capabilities in video scenarios.
4、Active honeypot. Provide IoT security honeypot functions. (Can be specialized devices mixed within the gateway)
5、Intelligent networking. Support SD-WAN, cognitive routing, self-healing networking, etc.
6、Blockchain privacy protection. Use blockchain to retain historical records of smart devices, utilizing smart contracts and cryptocurrency transactions to enhance the security and trust of message delivery, protecting privacy.
7、Visual analysis. Management platform provides visualizations of raw data and other components to detect anomalies, offering situational awareness to network operators.
8、Decision support. Management platform provides guided intelligent decision-making based on multi-party data analysis.
9、Microservices. Support microservice models for rapid iteration of gateway functions.

Part Two: About Solution Models
Currently, most vendors providing IoT business solutions have IoT gateways, but these gateways primarily handle data and command interactions. Some gateways possess edge computing capabilities, and these gateways are directly managed by the IoT business platform, with relatively lacking security functions. There are several reasons for this:
First, vendors providing IoT business solutions generally have relatively little research on security, focusing mainly on connectivity and management, as well as enabling business.
Second, integrating security capabilities increases the cost of solutions, and the threshold for security research is relatively high.
Third, customers currently have relatively weak awareness of IoT security, and business vendors are unlikely to guide customers to consider security.
For IoT security vendors, historically, security and business have followed a loosely coupled model, resulting in vendors providing IoT security solutions struggling to find applicable scenarios. They can only wait for IoT business vendors to first set up the framework and then guide customers to pay attention to security.
The resultant construction model, in terms of solutions, is that the IoT access gateway is followed by the IoT security gateway.
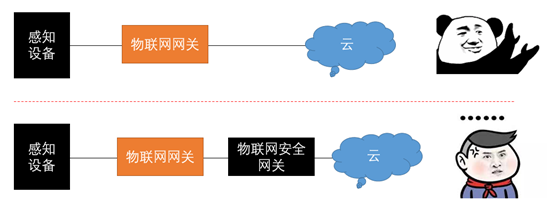
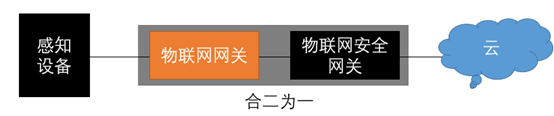
In fact, the functions of the IoT access gateway can be entirely provided by the IoT security gateway, i.e., the IoT security access gateway. However, the challenge lies in that the IoT security access gateway is provided by security vendors, while IoT solutions are usually provided by IoT business vendors, and they must have a “gateway” in their solutions, which they can provide at a low cost.
How to resolve this contradiction?
The best way is for security vendors and business vendors to collaborate at the solution level. This requires security vendors to proactively take the first two steps to have a chance for successful cooperation, as business vendors can completely place security in a relatively small position, and they will also provide security keys such as ProductKey, Product Secret, etc., allowing them to thrive.
However, another problem arises: security vendors are reluctant to take too much initiative because even if the cooperation does not succeed, security vendors still have a legal sword – compliance, which can drive customers to upgrade or transform their previously built or ongoing IoT systems, allowing them to thrive as well.
Ultimately, the ones who may feel troubled are the customers, who may ask:
Why wasn’t security considered during the initial construction?

Part Three: Discussion
What do you think of this situation? Feel free to leave a comment for discussion.