
Introduction
In industrial control sites, there exists a fundamental yet easily overlooked aspect that all devices rely on—serial ports. So, what is a serial port? Is there a risk associated with serial communication? Qi’an Technology’s classroom provides answers and details how to conduct safe offense and defense regarding serial ports.
What is a Serial Port
The serial port, fully known as the serial communication interface, is a device that can convert parallel data characters received from the CPU into a continuous serial data stream for transmission, while also converting the received serial data stream back into parallel data characters for the CPU. The circuit that accomplishes this function is referred to as a serial interface circuit.
Most network devices in industrial control sites are equipped with serial communication capabilities, and the serial port is often retained as the most basic debugging interface. Even without external serial devices, we can find serial connection pins or solder points on the PCB. If the industrial control device does not encrypt the serial port for reading, there is a possibility of sensitive data operations on the serial port.
This article will simulate the process of capturing and analyzing data during communication with hardware and serial data transmission, and send the simulated captured data to the lower machine to verify whether data can be sent directly to the lower machine through the serial port without going through the system.
Main Scenarios of Serial Ports
The serial port is a very common device communication protocol on computers. Most computers (excluding laptops) contain two RS-232 based serial ports. The serial port is also a common communication protocol for instruments and meters; many GPIB-compatible devices also come with RS-232 ports. Additionally, the serial communication protocol can be used to retrieve data generated by remote collection devices.
RS-232 (ANSI/EIA-232 standard) is the serial connection standard on IBM-PC and its compatible machines. It has various uses, such as connecting mice, printers, or modems, and can also connect to industrial instruments and meters.
Basic Serial Communication with STM32 and Communication Process
Typically, the RS232 interface (usually in DB9 packaging) is used by PCs (or upper machines), so they cannot be directly cross-connected. The RS232 interface has 9 pins (or pins), usually with TxD and RxD being level-converted. Therefore, to enable direct communication between the chip and the PC’s RS232 interface, the chip’s input and output ports must also be converted to RS232 levels before cross-connection.
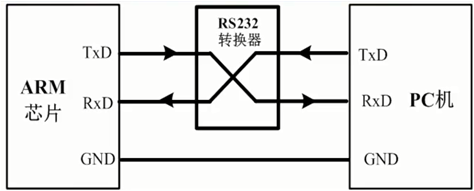
After level conversion, the chip’s serial port and the RS232 level standards are different:
Microcontroller Level Standard (TTL Level):
+5V represents 1, 0V represents 0;
RS232 Level Standard:
+15/+13 V represents 0, -15/-13 represents 1.
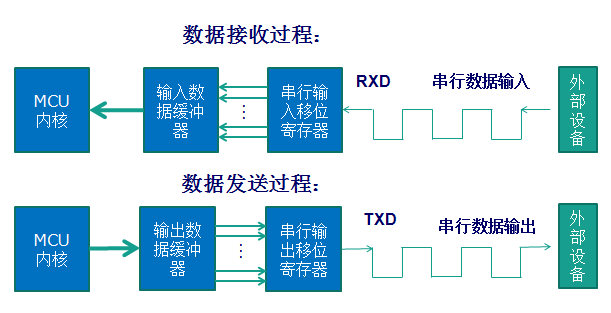
▲ Illustration of Serial Communication Process
Tools Used in Operations
🔹 Serial Port Monitor for capturing serial packets
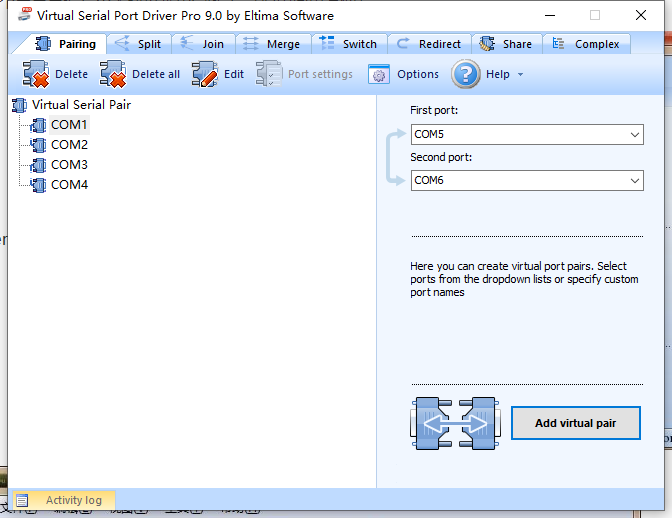
🔹 Virtual Serial Port Driver for simulating serial ports
🔹 Friendly Serial Debugging Tool, or use the Python package ‘serial’ for debugging, using tools for convenience in examples
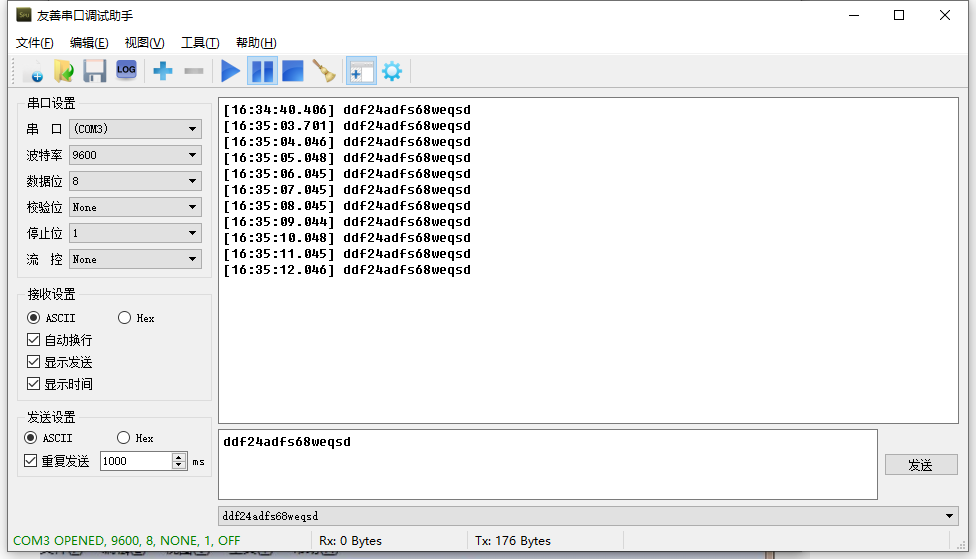
Serial Data Capture
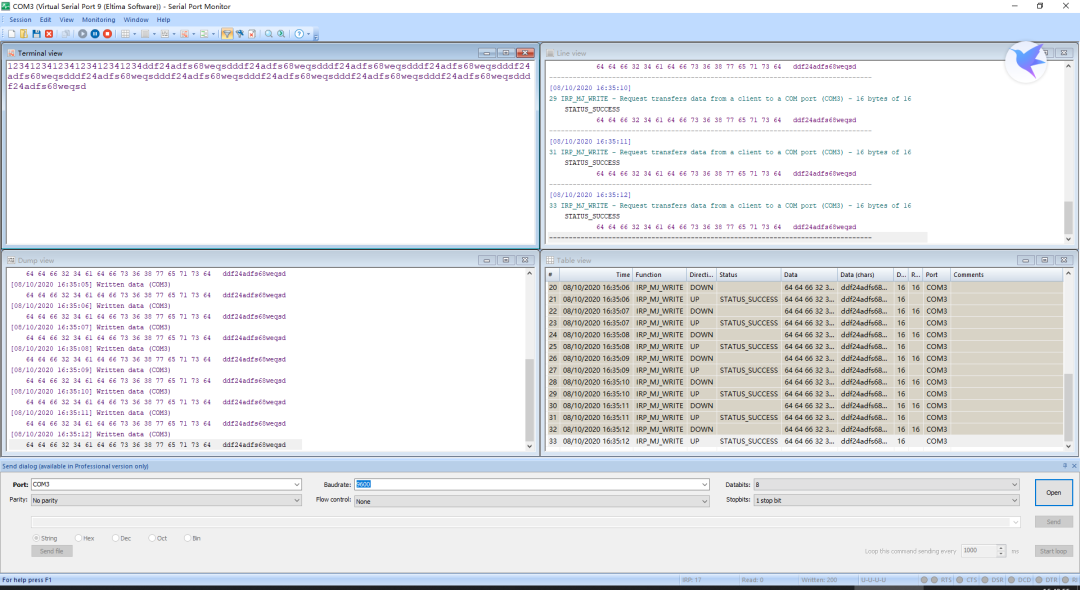
🔹 Start listening to COM port data
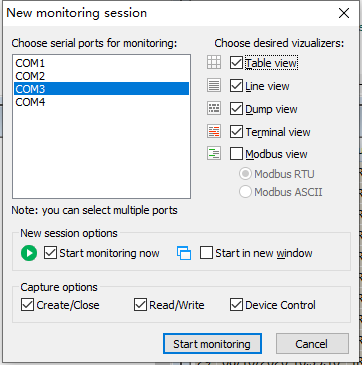
🔹 The captured data is shown in the figure
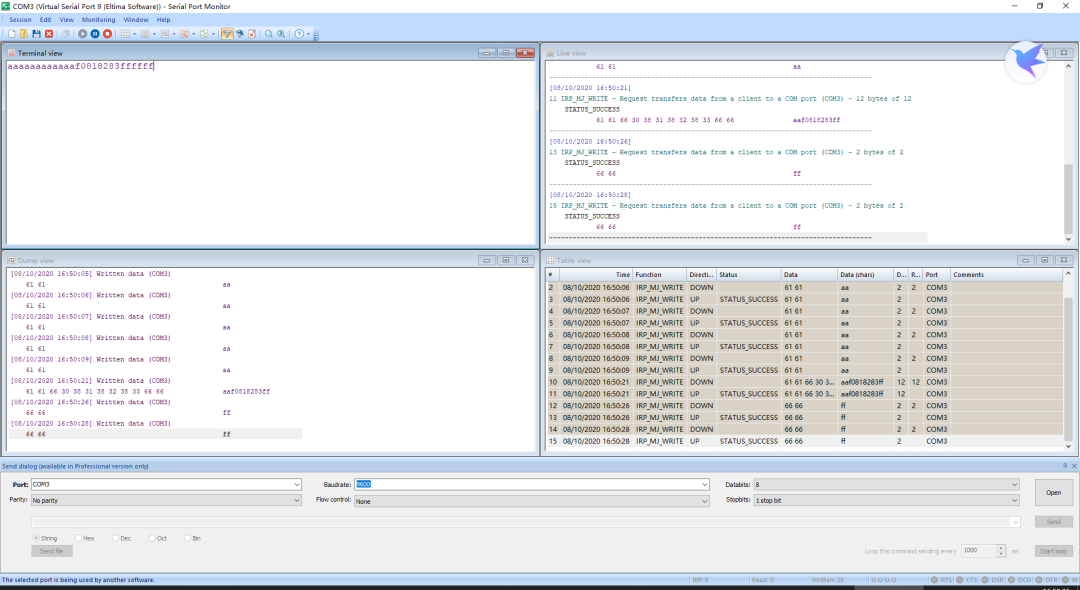
🔹 You can see the data written in the dump view window
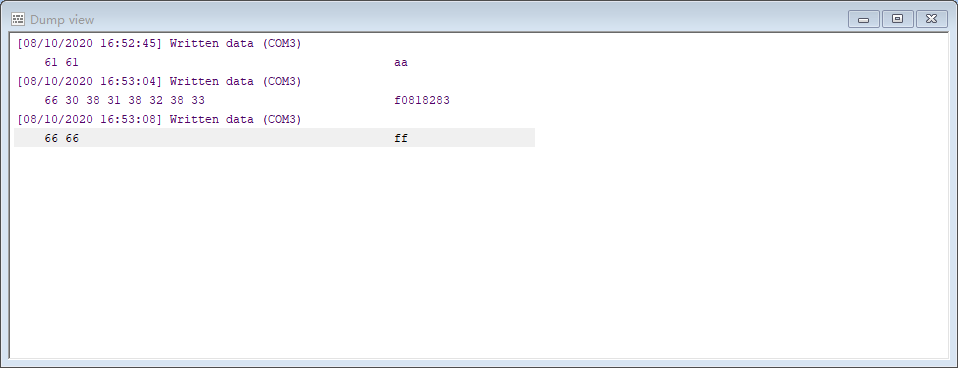
🔹 Starting with aa request and ending with ff request, with f0818283 as data in between, observe the corresponding operations performed by the industrial control machine to understand the meaning of the command.
Serial Data Communication
Finally, use the friendly serial debugging assistant to send serial data
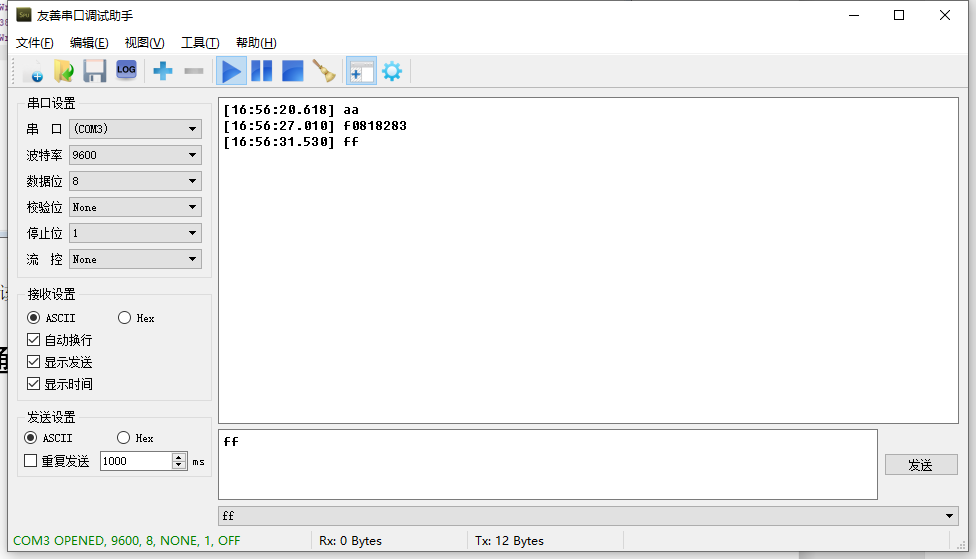
Conclusion
After testing and verification, it is possible to bypass software permission restrictions to modify and send commands to the lower machine (industrial control devices) without serial communication encryption, using an upper machine (generally referring to a PC).

Q&A After Class
Q:How can we protect serial data communication?
A:After receiving 8 bytes of data sent from external devices, you can perform encryption processing to generate a 16-byte key and tag code, and return this information through the serial port to the external device. This can prevent data leakage caused by serial port monitoring.
Q:Do most modern industrial control devices encrypt the serial port?
A:It’s relatively rare, as such operations require direct connection to the machine. However, industrial control sites are generally well protected, and after physical protection, software-level protection is often overlooked due to cost-saving considerations. However, such behavior is inadvisable. Industrial control data has very high security requirements; not implementing serial port encryption protection is equivalent to having a known security threat. Therefore, related industrial enterprises need to pay sufficient attention to better protect the security of industrial data.
Related Previous Topics
How to Conduct Weak Password Detection?
Qi’an Technology—Making Industry Safer and Security Simpler
Zhejiang Internet Association

Scan QR Code | Follow Us
0571-82257570
183 Wenhui Road, Hangzhou, 21st Floor
● Share · Share Responsibility · Create Together ●