This is the “Stablecoin Series | Part 2”, focusing on the three core underlying capabilities of stablecoins: on-chain identity, national encryption algorithms, and domestic cryptographic devices, helping you understand the secure foundation of digital currency.Stablecoins seem simple, just pegged to the US dollar?Wrong! The security system behind it is the key to whether digital currency can be implemented.
Today, we will dissect this “digital financial foundation” (the list of core concept stocks involved in this article is attached at the end), helping you understand how digital currency achieves:
Real identity verification,
Domestic encryption protection,
And secure hardware assurance.
These three technologies determine who can seize the future opportunities in digital finance.
The “stability” of stablecoins goes far beyond just pegging to the US dollar or a basket of assets.
What truly makes it a reliable, regulated, and cross-border circulating digital currency system is the hiddentechnical foundation.
Just like you see a high-speed financial train running:
It not only needs stable tracks (public chain network)
And an autopilot system (smart contracts)
High-frequency transfer stations (clearing and settlement systems)
But also relies on an invisible yet crucial “digital foundation” —
Who has the right to board?
Who can verify identity?
Is the data secure?
Is the system reliable?
This digital foundation can be imagined as the “three guardrails” of the digital world:
On-chain identity verification, like your “digital passport”, proves who you are;
National encryption algorithms, are exclusive “encryption language rules”, ensuring information security;
Domestic cryptographic devices, are the solid “security line”, protecting all critical data.
These three guardrails are like the “identity system, password system, and firewall” of digital finance,
Determining whether this system is reliable, compliant, and can be recognized by the national financial system.
Can you imagine, without these “three guardrails”, how safe would digital currency be?
In the traditional financial system, identity verification is simple — ID card, bank card, real-name system.
But in the blockchain world, everything becomes different.
Blockchain is inherently anonymous, wallet addresses can be generated as many as you want, no one cares who you are.
This brings a core question:
“Who exactly are you? Who can guarantee you have only one identity?”
This is precisely the significance of the on-chain identity system, it is the “ID card” for digital currency to enter the compliant world; without it, digital currency cannot circulate legally.
You can think of on-chain identity as a “digital ID card”,
It must be decentralized, ensuring no central control,
And must comply with regulatory requirements, ensuring authenticity and trustworthiness.
In the future, when using stablecoins for payment, the situation will be as follows:
Wallet address ≠ your real identity
But this on-chain pass has already helped you authenticate your identity
Regulatory agencies can track, verify, and audit your identity information
What is the mechanism behind this?
The core technology is the combination of DID (Decentralized Identity) + Zero-Knowledge Proof + Off-chain Real-name Binding.
In simple terms, on-chain identity is like a combination of “Alipay + Public Security Network” —
Allowing you to log in to all Web3 applications with one click,While your identity is real, unforgeable, secure, and compliant.
This is not only the foundation for on-chain credit, on-chain taxation, and on-chain insurance,But also the first threshold for compliant stablecoins.
So, who is entering the on-chain identity field?
Here are a few key companies:
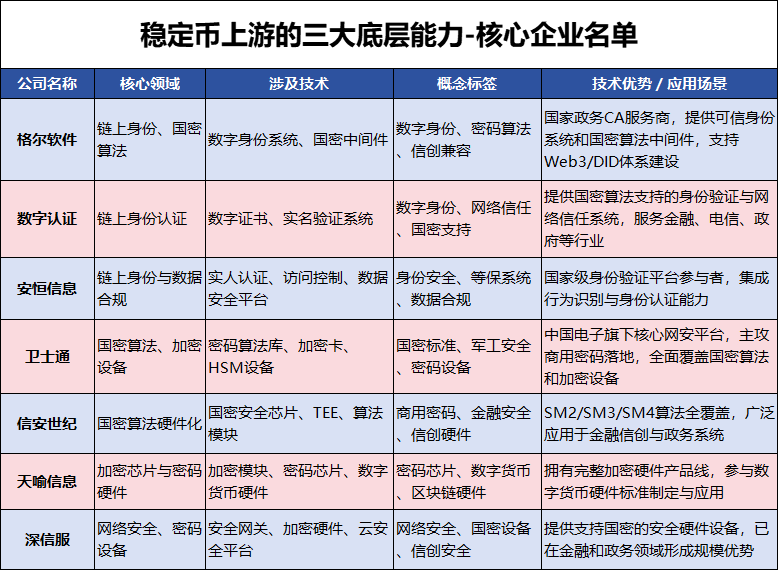
Geer Software focuses on electronic certification, CA services, and digital identity systems, providingtrusted identity authentication systems.
Core clients include national government systems, making it a natural beneficiary of the localization of the Web3/DID system.
Concept tags: digital identity, electronic certification, cryptographic applications
Digital Authentication provides identity authentication services based on national encryption algorithms,
Its products are widely used indigital certificate issuance, real-name verification, network trust systems and other critical scenarios.
Concept tags: digital identity, network security, national encryption support
Anheng Information participates in building a national-level identity verification platform,
Withreal-person authentication + behavior analysis + access control integrated capabilities, it is an important vendor for the integration of on-chain identity and security.
Concept tags: identity security, data compliance, security protection systems
On-chain identity is not only a technical challenge, but also the ticket to the future of “on-chain compliant finance”.Whoever can seize the layout first will hold the first gateway to the circulation of digital currency.
If we compare “on-chain identity” to the real-name pass for stablecoins,
Then “encryption algorithms” are its language system: who can read, verify, and decrypt determines its security boundary.
Currently, mainstream international encryption algorithms such as RSA, ECDSA, SHA, etc., are mainly controlled by the United States, making it difficult to meet China’s information sovereignty needs.
Therefore, the domestic national encryption algorithm system (SM series) has emerged.
This is not a simple “supplement”, but a fundamental guarantee for building a self-controlled digital financial system in China.
You can think of national encryption algorithms as the “official encryption language” of Chinese digital currency,ensuring data security and compliance.
Just like every country has its own language system:
🇺🇸 The United States mainly uses AES, RSA, and other algorithms
🇨🇳 China has independently developed SM2 (public key algorithm), SM3 (hash algorithm), SM4 (symmetric encryption algorithm)
Only data encrypted with national encryption algorithms can be legally recognized in China’s government, financial, and trusted innovation systems,and can be safely parsed and verified through domestic software and hardware.
For stablecoins, to access the central bank system, government applications, and even state-owned platform payment settlements,they must have “national encryption compatibility” capabilities.
This means that whether it is the underlying blockchain code or the data encryption and decryption in smart contracts,the national encryption algorithm module must be embedded.
This is a strategic high ground that domestic cryptographic manufacturers are focusing on.
So, who is laying out in the national encryption algorithm field?
Here are a few key companies:
Geer Software one of its core products isnational encryption algorithm middleware, with strong compatibility, can be embedded in blockchain, public cloud, and other systems,
It has been integrated with platforms such as Huawei and Alibaba.
Concept tags: cryptographic algorithms, trusted innovation compatibility, national encryption core manufacturers
Weishitong is controlled by a cybersecurity company under China Electronics,
It has a self-controlled cryptographic library, encryption cards, and national encryption algorithm suites, making it a main force in the commercial landing of China’s cryptographic products.
Concept tags: national encryption standards, military security, trusted innovation terminals
Xinan Century main business coverscryptographic security chips, national encryption algorithm support modules, trusted execution environments,
Core products have achieved full coverage of SM2, SM3, and SM4, with clients including multiple financial institutions and government platforms.
Concept tags: commercial cryptography, trusted innovation hardware, financial security
In the security system of digital currency, algorithms and identity authentication are just the first line of defense at the software level.
And protecting critical data from being stolen and tampered with is that indispensable “hardware shield” — domestic cryptographic devices.
You can compare your digital currency wallet to a vault:
Even if the lock is equipped with the most advanced password lock (national encryption algorithm),
If the vault door is a loose iron door, there is still a risk of being breached.
Domestic cryptographic devices are this solid physical security line, mainly including:
Encryption machines (hardware security modules, HSM)
Secure chips (trusted execution environments, TEE)
Encryption cards and USB keys
These devices are responsible for key generation, storage, encryption operations, and identity verification, ensuring sensitive data is always stored in a secure area, greatly enhancing the overall security and trustworthiness of the system.
This is like installing a “firewall + safe” for the digital financial system,
Preventing remote attacks from hackers,
And stopping malicious tampering and information leakage from internal personnel.
It can be said that the national encryption algorithm system is equivalent to building a “cryptographic defense line for Chinese blockchain access”.
It is not a “nice-to-have”, but the “underlying cryptographic permission” for stablecoins to operate legally in China’s cyberspace.
In the context of the country vigorously promoting digital sovereignty and information security, domestic cryptographic devices have become a key support direction, especially incentral bank digital currency, blockchain finance, electronic government and other fields.
These leading domestic cryptographic device manufacturers have already laid a deep foundation:
Weishitong is a leading domestic provider of cryptographic devices,
Products include HSM encryption machines, cryptographic security gateways, security authentication devices, etc., widely used in financial, government, and military systems.
Concept tags: domestic cryptographic devices, HSM, network security
Tianyu Information has been deeply involved in the information security field for many years, with independently developed encryption hardware products and cryptographic chips,
Actively participating in the standardization of digital currency and blockchain security hardware.
Concept tags: information security, cryptographic chips, digital currency hardware
Shenxinfu focuses on network security and cloud security, providing security hardware devices and cryptographic services,
Supporting national encryption algorithms, has formed advantages in the financial and government information security market.
Concept tags: network security, national encryption devices, cloud security

Domestic cryptographic devices are the “Great Wall of Steel” for the security of digital currency,
Building the last solid defense line for the compliant operation of stablecoins in China.
In summary, the three underlying capabilities of on-chain identity, national encryption algorithms, and domestic cryptographic devices together constitute the core security foundation of stablecoins, ensuring that this digital financial high-speed train can run smoothly, efficiently, and compliantly.
The underlying security of stablecoins far exceeds the simple definition of “pegging assets”.
It relies on the on-chain identity as a real-name “pass”,
On the national encryption algorithm as a self-controlled “password lock”,
And on domestic cryptographic devices as an unbreakable “Great Wall of Steel”.
These three core capabilities are interlinked, building a solid defense for digital finance.
In the future, whoever can seize this “hardcore track” of digital currency will hold the next opportunity.
In the next article, we will unveil the mystery of “on-chain payment clearing and settlement”, taking you deeper into how stablecoins achieve efficient and compliant fund circulation on-chain.
Please stay tuned, see you next time!
If you want to learn about Part 1, please click here:Blockchain Technology Behind Stablecoins
The list of core enterprises involved in stablecoins mentioned in the article has now been organized as follows for your convenience:
 Welcome to follow me! Set as a star to not miss updates.We focus on sorting out industry contexts, analyzing core concepts, and using simple language for in-depth financial science popularization.
Welcome to follow me! Set as a star to not miss updates.We focus on sorting out industry contexts, analyzing core concepts, and using simple language for in-depth financial science popularization.
📌 Disclaimer:This article’s materials are sourced from research reports, authoritative media, and publicly available online information, striving for accuracy and timeliness; if there are discrepancies, please refer to the latest official releases. This article is for academic discussion and information exchange only, and the content does not constitute any form of investment advice, prediction, or commitment. The market has risks, and investment should be cautious; related decisions should be made based on independent judgment and risk-bearing principles.