✅ Author Profile: A research enthusiast and Matlab simulation developer, skilled in data processing, modeling simulation, program design, complete code acquisition, paper reproduction, and scientific simulation.
🍎 Previous reviews, follow the personal homepage:Matlab Research Studio
🍊 Personal motto: Seek knowledge through investigation, complete Matlab code and simulation consultation available via private message.
Intelligent Optimization Algorithms Neural Network Prediction Radar Communication Wireless Sensors Power Systems
Signal Processing Image Processing Path Planning Cellular Automata Unmanned Aerial Vehicles
Physical Applications Machine Learning Series Workshop Scheduling Series Filtering and Tracking Series Data Analysis Series
Image Processing Series
🔥 Content Introduction
Images, as important carriers of information, play a crucial role in modern society. However, with the widespread use of the internet and rapid development of information technology, the security of images faces severe challenges. Unauthorized access, tampering, and dissemination can lead to privacy breaches, economic losses, and even national security issues. Therefore, image encryption technology has emerged as an important means to protect image information security. This article will delve into the image encryption and decryption technology based on symmetric key algorithms, analyzing its principles, advantages, shortcomings, and exploring future development directions.
The symmetric key algorithm, also known as the secret key algorithm, is characterized by using the same key for both encryption and decryption. Due to its fast computation speed and high efficiency, it is widely used in the field of image encryption. The basic principle is to transform the image data into an unrecognizable form using a specific encryption algorithm and the key, thereby protecting the image. The decryption process uses the same key and corresponding decryption algorithm to restore the encrypted image back to its original form.
Common symmetric key algorithms include Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), Advanced Encryption Standard (AES), as well as Blowfish and Twofish. Each of these algorithms has its characteristics and applicable scenarios in image encryption.
-
Data Encryption Standard (DES): Although the DES algorithm is relatively outdated and has a short key length (56 bits), making it susceptible to brute-force attacks, it was widely used historically. In image encryption, DES can be implemented through different modes of operation (such as Electronic Codebook ECB, Cipher Block Chaining CBC, Counter CTR, etc.). However, due to its insufficient security, DES is no longer recommended for direct use in image encryption.
-
Triple Data Encryption Standard (3DES): To enhance the security of DES, the 3DES algorithm was developed. It effectively extends the key length by performing DES encryption three times, improving resistance to attacks. While 3DES is more secure than DES, its computation speed is relatively slow, which may present performance bottlenecks in high-efficiency image encryption scenarios.
-
Advanced Encryption Standard (AES): The AES algorithm is currently one of the most popular symmetric key algorithms. It offers high security, fast speed, and strong flexibility, supporting key lengths of 128, 192, and 256 bits, allowing users to choose an appropriate key length based on security needs. AES performs excellently in image encryption and is widely used in various image encryption applications.
-
Blowfish and Twofish: These two algorithms are also representatives of symmetric key algorithms, known for their speed and security. The Blowfish algorithm was designed to replace DES and offers higher security. Twofish is an improved version of Blowfish, performing well in competition with AES and is also a secure and reliable choice for image encryption.
The specific implementation process of symmetric key algorithms in image encryption typically includes the following steps:
-
Key Generation: Select an appropriate symmetric key algorithm and generate a key that meets the algorithm’s requirements. The length of the key directly affects the security of the encryption; generally, the longer the key length, the higher the security, but the computational complexity will also increase accordingly. Key generation should use a secure random number generator to ensure the randomness and unpredictability of the key.
-
Image Preprocessing: Depending on the encryption algorithm and image format, preprocessing of the image may be required. For example, for bitmap images, pixel data needs to be converted into a one-dimensional array; for color images, the RGB channels need to be separated and encrypted individually. The purpose of preprocessing is to convert the image data into a form suitable for processing by the encryption algorithm.
-
Image Encryption: Use the generated key and the selected encryption algorithm to encrypt the image data. The encryption process typically includes steps such as grouping, padding, and round function operations. Different encryption algorithms use different round functions, and the complexity of the round function directly affects the security of the encryption algorithm.
-
Image Decryption: Use the same key and corresponding decryption algorithm as in the encryption process to decrypt the encrypted image data. The decryption process is the inverse of the encryption process, restoring the ciphertext image back to the original image through the inverse operation of the same round function.
-
Image Postprocessing: Perform postprocessing on the decrypted image data to restore it to the original image format. For example, converting a one-dimensional pixel array back to a two-dimensional image, and merging the separated RGB channels into a color image.
⛳️ Running Results
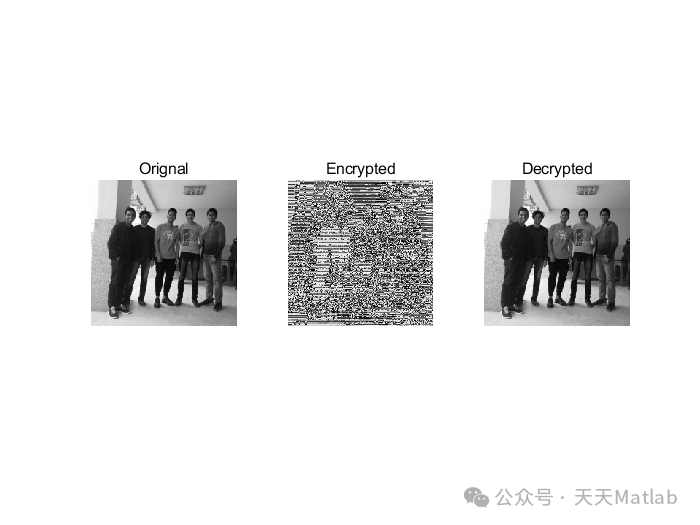
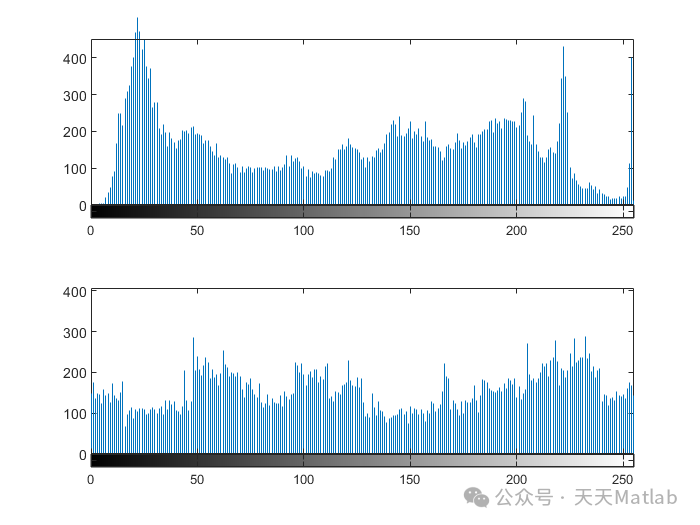
🔗 References
📣 Partial Code
🎈 Some theoretical references are from online literature; please contact the author for removal if there is any infringement.
👇 Follow me to receive a wealth of Matlab e-books and mathematical modeling materials
🏆 Our team specializes in custom MATLAB simulations in various research fields, helping to realize research dreams:
🌈 Various intelligent optimization algorithm improvements and applications
Production scheduling, economic scheduling, assembly line scheduling, charging optimization, workshop scheduling, departure optimization, reservoir scheduling, three-dimensional packing, logistics site selection, cargo location optimization, bus scheduling optimization, charging pile layout optimization, workshop layout optimization, container ship loading optimization, pump combination optimization, medical resource allocation optimization, facility layout optimization, visual domain base station and drone site selection optimization, knapsack problem, wind farm layout, time slot allocation optimization, optimal distributed generation unit allocation, multi-stage pipeline maintenance, factory-center-demand point three-level site selection problem, emergency supply distribution center site selection, base station site selection, road lamp post arrangement, hub node deployment, transmission line typhoon monitoring devices, container scheduling, unit optimization, investment portfolio optimization, cloud server combination optimization, antenna linear array distribution optimization, CVRP problem, VRPPD problem, multi-center VRP problem, multi-layer network VRP problem, multi-center multi-vehicle VRP problem, dynamic VRP problem, two-layer vehicle routing planning (2E-VRP), electric vehicle routing planning (EVRP), hybrid vehicle routing planning, mixed flow shop problem, order splitting scheduling problem, bus scheduling optimization problem, flight shuttle vehicle scheduling problem, site selection path planning problem, port scheduling, port bridge scheduling, parking space allocation, airport flight scheduling, leak source localization
🌈 Time series, regression, classification, clustering, and dimensionality reduction in machine learning and deep learning
2.1 BP time series, regression prediction, and classification
2.2 ENS voice neural network time series, regression prediction, and classification
2.3 SVM/CNN-SVM/LSSVM/RVM support vector machine series time series, regression prediction, and classification
2.4 CNN|TCN|GCN convolutional neural network series time series, regression prediction, and classification
2.5 ELM/KELM/RELM/DELM extreme learning machine series time series, regression prediction, and classification
2.6 GRU/Bi-GRU/CNN-GRU/CNN-BiGRU gated neural network time series, regression prediction, and classification
2.7 Elman recurrent neural network time series, regression prediction, and classification
2.8 LSTM/BiLSTM/CNN-LSTM/CNN-BiLSTM long short-term memory neural network series time series, regression prediction, and classification
2.9 RBF radial basis function neural network time series, regression prediction, and classification
2.10 DBN deep belief network time series, regression prediction, and classification
2.11 FNN fuzzy neural network time series, regression prediction
2.12 RF random forest time series, regression prediction, and classification
2.13 BLS broad learning system time series, regression prediction, and classification
2.14 PNN pulse neural network classification
2.15 fuzzy wavelet neural network prediction and classification
2.16 Time series, regression prediction, and classification
2.17 Time series, regression prediction, and classification
2.18 XGBOOST ensemble learning time series, regression prediction, and classification
2.19 Transform various combinations of time series, regression prediction, and classification
Directions cover wind power prediction, photovoltaic prediction, battery life prediction, radiation source identification, traffic flow prediction, load forecasting, stock price prediction, PM2.5 concentration prediction, battery health status prediction, electricity consumption prediction, water body optical parameter inversion, NLOS signal identification, subway parking precision prediction, transformer fault diagnosis
🌈 In the field of image processing
Image recognition, image segmentation, image detection, image hiding, image registration, image stitching, image fusion, image enhancement, image compressed sensing
🌈 In the field of path planning
Traveling salesman problem (TSP), vehicle routing problem (VRP, MVRP, CVRP, VRPTW, etc.), UAV three-dimensional path planning, UAV collaboration, UAV formation, robot path planning, grid map path planning, multimodal transport problems, electric vehicle routing planning (EVRP), two-layer vehicle routing planning (2E-VRP), hybrid vehicle routing planning, ship trajectory planning, full path planning, warehouse patrol
🌈 In the field of UAV applications
UAV path planning, UAV control, UAV formation, UAV collaboration, UAV task allocation, UAV secure communication trajectory online optimization, vehicle collaborative UAV path planning
🌈 In the field of communication
Sensor deployment optimization, communication protocol optimization, routing optimization, target localization optimization, Dv-Hop localization optimization, Leach protocol optimization, WSN coverage optimization, multicast optimization, RSSI localization optimization, underwater acoustic communication, communication upload and download allocation
🌈 In the field of signal processing
Signal recognition, signal encryption, signal denoising, signal enhancement, radar signal processing, signal watermark embedding and extraction, EMG signals, EEG signals, signal timing optimization, ECG signals, DOA estimation, encoding and decoding, variational mode decomposition, pipeline leakage, filters, digital signal processing + transmission + analysis + denoising, digital signal modulation, bit error rate, signal estimation, DTMF, signal detection
🌈 In the field of power systems
Microgrid optimization, reactive power optimization, distribution network reconstruction, energy storage configuration, orderly charging, MPPT optimization, household electricity
🌈 In the field of cellular automata
Traffic flow, crowd evacuation, virus spread, crystal growth, metal corrosion
🌈 In the field of radar
Kalman filter tracking, trajectory association, trajectory fusion, SOC estimation, array optimization, NLOS identification
🌈 Workshop scheduling
Zero-wait flow shop scheduling problem (NWFSP) , permutation flow shop scheduling problem (PFSP) , hybrid flow shop scheduling problem (HFSP) , zero idle flow shop scheduling problem (NIFSP), distributed permutation flow shop scheduling problem (DPFSP), blocking flow shop scheduling problem (BFSP)
👇