1. Http
HyperText Transfer Protocol, is the most widely used protocol on the Internet, a standard that all WWW files must follow. The data transmitted using the HTTP protocol is unencrypted, which means it is in plaintext, making it very insecure to transmit private information using the HTTP protocol.
Uses TCP port: 80
2. Https
Hyper Text Transfer Protocol over Secure Socket Layer, a secure version of the hypertext transfer protocol, was designed by Netscape to encrypt the data transmitted over the HTTP protocol, ensuring security during the session.
Uses TCP port default: 443
3. SSL Protocol Encryption Methods
The SSL protocol uses both symmetric and asymmetric encryption (public key encryption). When establishing a transmission link, SSL first uses the public key to asymmetrically encrypt the symmetric encryption key. Once the link is established, SSL uses symmetric encryption for the transmitted content.
-
Symmetric encryption is fast and can encrypt larger content, used to encrypt messages during the session.
-
Public key encryption is slower but provides better identity authentication technology, used to encrypt the symmetric encryption key.
4. One-Way Authentication
Before establishing a socket connection, HTTPS requires a handshake. The specific process is as follows: 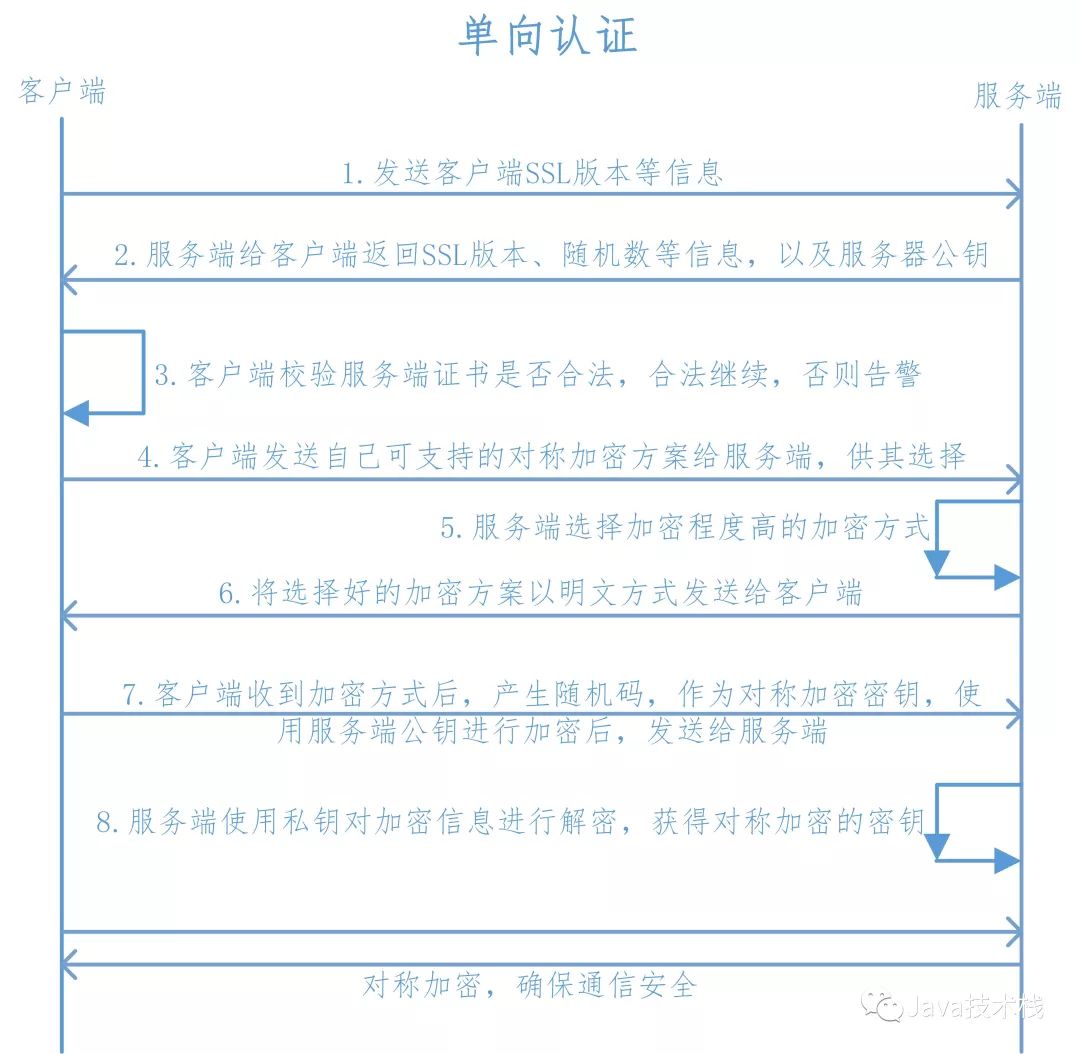
1. The client sends the SSL protocol version number, encryption algorithm types, random numbers, and other information to the server.
2. The server returns the SSL protocol version number, encryption algorithm types, random numbers, and also returns the server’s certificate, which is the public key certificate.
3. The client uses the information returned by the server to verify the legitimacy of the server, including:
-
Whether the certificate has expired
-
Whether the CA that issued the server certificate is reliable
-
Whether the returned public key can correctly decrypt the digital signature in the returned certificate
-
Whether the domain name on the server certificate matches the actual domain name of the server
If verification is successful, communication will continue; otherwise, communication will be terminated.
4. The client sends the symmetric encryption schemes it supports for the server to choose from.
5. The server selects the highest level of encryption from the encryption schemes provided by the client.
6. The server returns the chosen encryption scheme to the client in plaintext.
7. After receiving the encryption method returned by the server, the client generates a random code using that encryption method, which will be used as the symmetric encryption key during communication, and encrypts the random code using the public key returned by the server, sending the encrypted random code to the server.
8. The server receives the encrypted information returned by the client and uses its private key to decrypt it, obtaining the symmetric encryption key. In the subsequent session, both the server and client will use this password for symmetric encryption to ensure the security of the information during communication.
5. Two-Way Authentication
The principle of two-way authentication is basically similar to one-way authentication, except that in addition to the client needing to authenticate the server, the server also authenticates the client. The specific process is as follows: 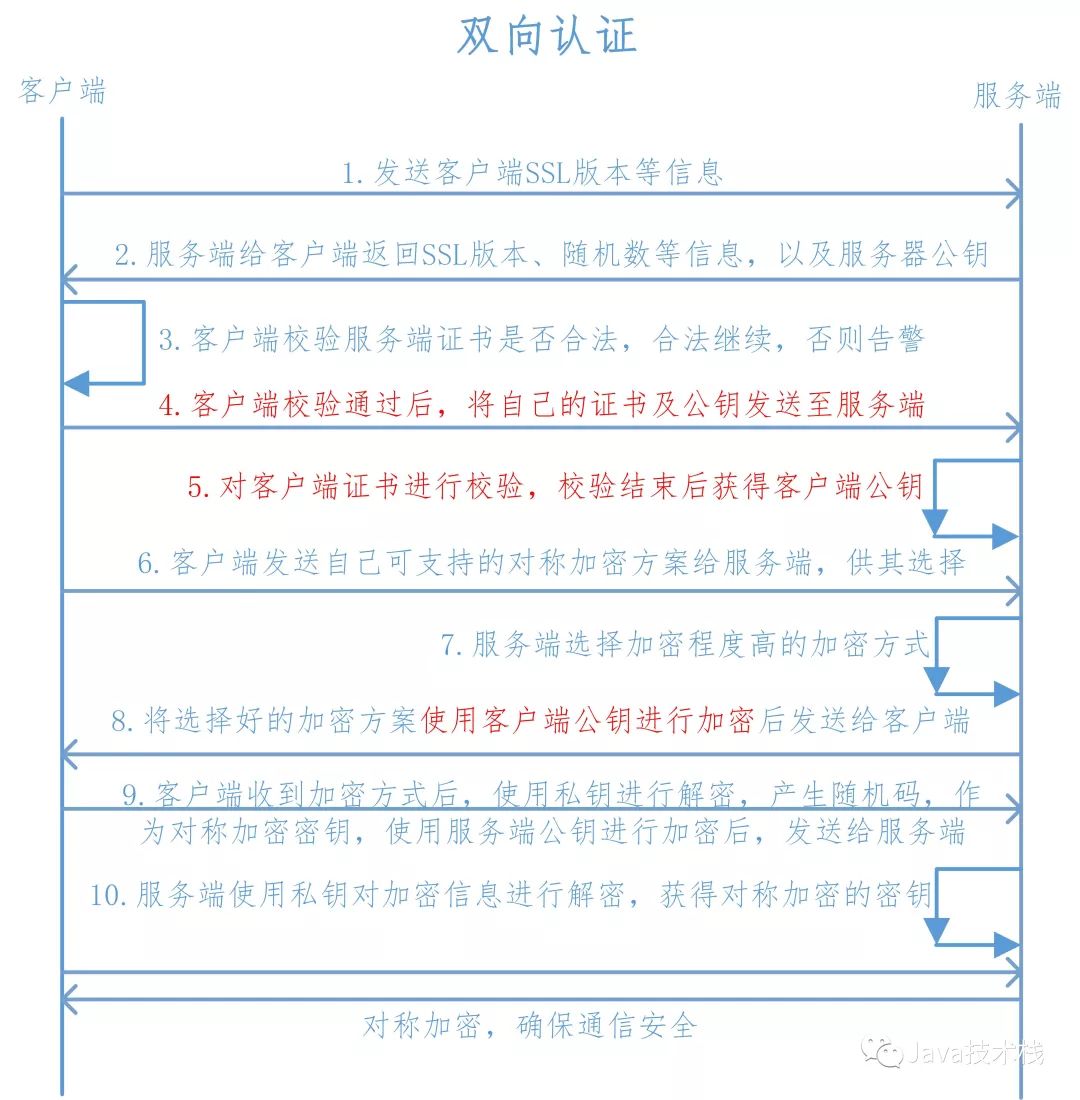
1. The client sends the SSL protocol version number, encryption algorithm types, random numbers, and other information to the server.
2. The server returns the SSL protocol version number, encryption algorithm types, random numbers, and also returns the server’s certificate, which is the public key certificate.
3. The client uses the information returned by the server to verify the legitimacy of the server, including:
-
Whether the certificate has expired
-
Whether the CA that issued the server certificate is reliable
-
Whether the returned public key can correctly decrypt the digital signature in the returned certificate
-
Whether the domain name on the server certificate matches the actual domain name of the server
If verification is successful, communication will continue; otherwise, communication will be terminated.
4. The server requests the client to send its certificate, and the client sends its certificate to the server.
5. The server verifies the client’s certificate, and upon successful verification, obtains the client’s public key.
6. The client sends the symmetric encryption schemes it supports for the server to choose from.
7. The server selects the highest level of encryption from the encryption schemes provided by the client.
8. The server encrypts the chosen encryption scheme using the public key obtained earlier and returns it to the client.
9. After receiving the encrypted scheme from the server, the client uses its private key to decrypt it to obtain the specific encryption method, then generates a random code for that encryption method to be used as the symmetric encryption key, encrypts it using the public key obtained from the server’s certificate, and sends it to the server.
10. After the server receives the message sent by the client, it uses its private key to decrypt it to obtain the symmetric encryption key. In the subsequent session, both the server and client will use this password for symmetric encryption to ensure the security of the information during communication.