Editor’s Note
Driven by the wave of digitalization, the construction of information infrastructure such as basic hardware, basic software, application software, and information security provides solid support for the “flow” of information security. This year, the “Government Work Report” proposed to “optimize the layout of national computing power resources and create a digital industry cluster with international competitiveness.” China Electronics Technology Group is fully promoting breakthroughs in key technologies, focusing on solving pain points in the industrial chain, and creating a product ecosystem that transforms sand into chips, from chips to the cloud, empowering the high-quality development of the digital industry.
Next-Generation Server CPU: Shenwei Wixin H8000
The latest generation of server CPU from China Electronics Technology Group, Shenwei Wixin H8000, achieves breakthroughs in high computing power and leads in overall performance domestically. Currently, the Wixin H8000 has been piloted in multiple fields, achieving deep adaptation with DeepSeek, successfully creating the first domestically produced integrated machine deployed with DeepSeek, establishing a foundation for full-stack innovative intelligent computing.

1
Unique Secret:Utilizes a self-developed instruction set architecture SW64, integrating 64 Core4 internally, doubling the number of cores on a single chip.
2
Core Competence:Achieves a security reliability evaluation level of Level 2.
3
Application Scenarios:Serves key industries such as government, energy, transportation, telecommunications, and finance.
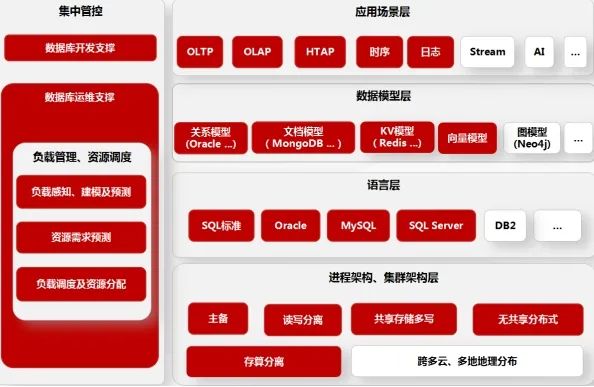
Kingbase Database
KingbaseES V9
KingbaseES V9 is an enterprise-level general-purpose database management system aimed at critical applications across all industries and customers, meeting core requirements for high reliability, high performance, high security, ease of management, ease of use, and scalability. The product has obtained national information security product certification and the Information Technology Product Security Level Evaluation Certificate (EAL4+), among other security qualifications.
1
Unique Secret:100% self-sourced core code, every line of code is controllable.
2
Core Competence:Whether it’s Oracle veterans, MySQL natives, SQL Server die-hards, or PostgreSQL enthusiasts, everything can be “migrated” seamlessly; the primary and backup partners never go offline, and read-write separation and shared storage are easily managed.
3
Applicable Scenarios:Online transaction processing, query-intensive data warehouses, massive time-series data storage and computation.
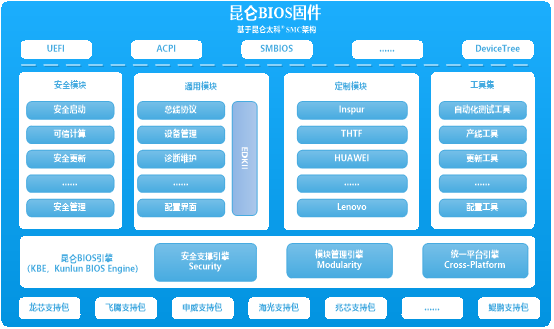
Kunlun BIOS Firmware
Kunlun BIOS firmware supports the latest domestic processors and architectures, providing comprehensive firmware solutions for various models including servers, terminals, mobile devices, and embedded devices.
1
Unique Secret:Quickly complete the development of new motherboard and new model versions, fully adapt to general, specialized, and customized hardware, meeting high-security field thresholds.
2
Application Scenarios:Covers applications in specialized, special equipment, and embedded devices.
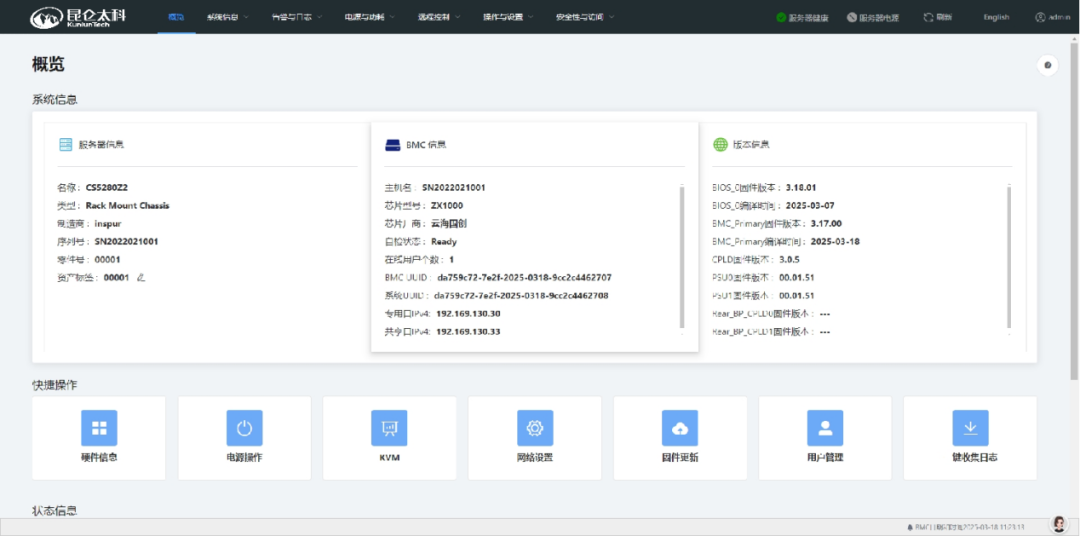
Kunlun BMC Firmware
Kunlun BMC firmware supports mainstream commercial BMC chips, providing fine-grained device monitoring, precise fault localization, and rich remote interfaces for servers.
1
Unique Secret:Precise detection and prediction of key component failures, protection of critical data during power outages, encryption storage of critical data, and support for rapid customization.
2
Application Scenarios:Applicable in government, finance, telecommunications, internet, and other fields.
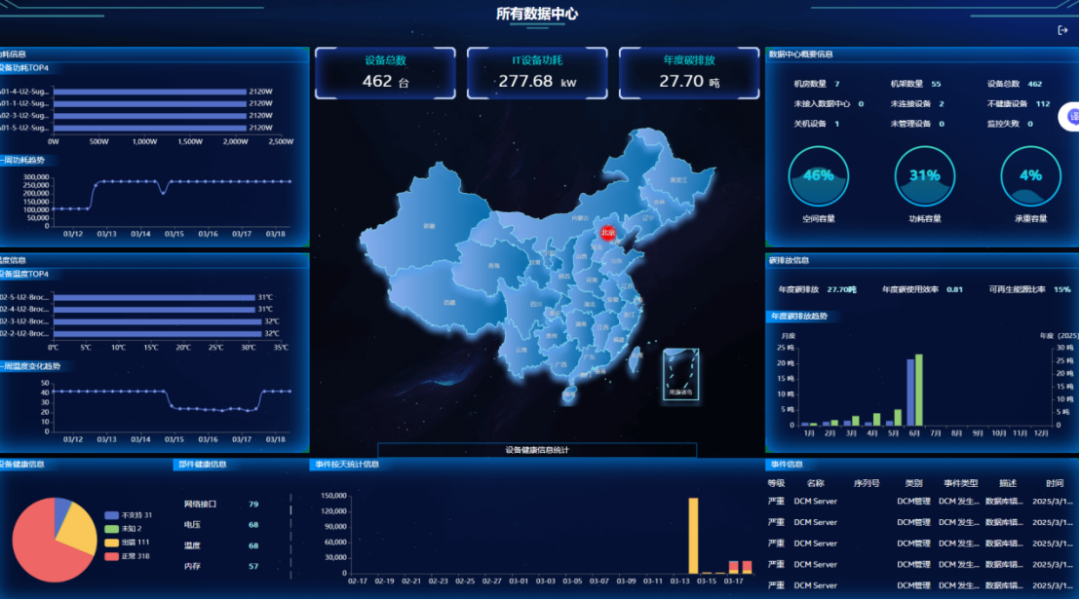
Kunlun Data Center Management System
An integrated intelligent monitoring management and green energy-saving control system for data center IT equipment.
1
Unique Secret:Asset management, health monitoring, energy consumption management, cooling optimization, and emergency response for data center IT equipment.
2
Core Competence:Quick deployment and application without affecting business operations, supporting green energy-saving and cost-reduction in data centers.
3
Application Scenarios:Applicable to all types of existing/new data centers.
Shouxin Integrated Security Control System
The integrated security control system is based on universal authentication and authorization technology, providing differentiated integrated security control capabilities for 5G mobile industry private networks and industry broadband. While enhancing the security of terminal access, it meets the refined management needs of industry customers for integrated network access.

1
Unique Secret:Ensures that integrated network security access is visible, controllable, manageable, and traceable.
2
Core Competence:Extremely simple installation, extremely simple activation, extremely simple usage, and extremely simple maintenance.
3
Application Scenarios:Applicable in government, judiciary, finance, industry, transportation, and public safety.
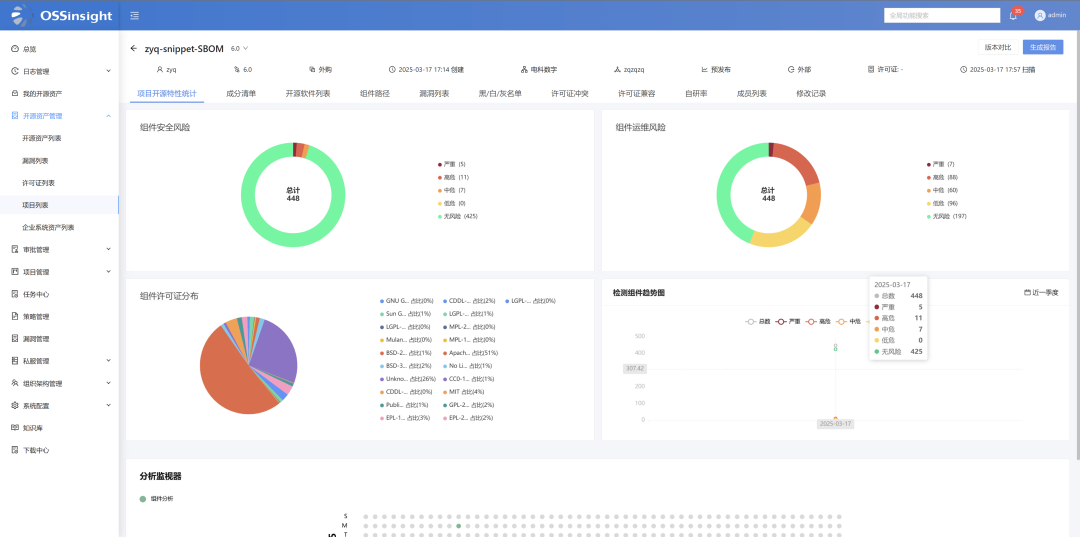
Digital Open Source Software Analysis and Governance Platform
The open source software analysis and governance platform focuses on open source software lifecycle management, building a governance system that integrates analysis, process approval, open source asset management, and risk identification and disposal. It intelligently reduces noise from vulnerabilities, accurately focuses on effective risks, and accelerates response processes with AI-driven repair suggestions, assisting enterprises in implementing open source governance standards and enhancing open source software management capabilities, safeguarding enterprises’ digital transformation and information security.
1
Unique Secret:Intelligent noise reduction for vulnerabilities, deep license detection, multi-dimensional binary detection, intelligent completion of vulnerability data, and full lifecycle management.
2
Core Competence:AI-enabled vulnerability explanation and scoring, intelligent repair suggestions, support for multiple programming languages, a complete knowledge base, automated processes, and multi-dimensional data statistics and visualization analysis.
3
Application Scenarios:Throughout the entire process of software development, delivery, launch, operation and maintenance, enterprise open source software governance, compliance risk control, vulnerability repair, and automated monitoring.
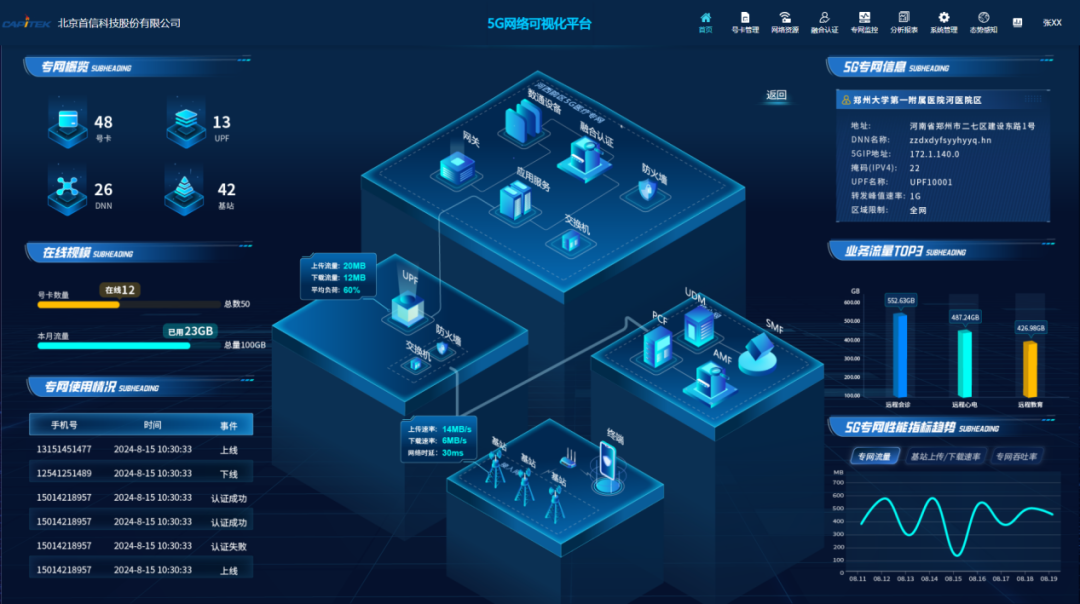
Shouxin5G Network Visualization Platform
A “tailor-made” 5G network visualization platform supports self-service operation, custom configuration, and self-maintenance management of SIM cards and devices under 5G private networks.
1
Unique Secret:Full-stack data aggregation capability, three-dimensional visualization and intelligent analysis capability, automated closed-loop operation and maintenance capability.
2
Core Competence:Focus on resource, performance, alarm, and other private network information visualization, simplifying configuration management processes, and cloud-network integration.
3
Application Scenarios:Domain model application construction mode, high-availability parallel task scheduling, efficient data synchronization in mobile networks, and strong security access interception.
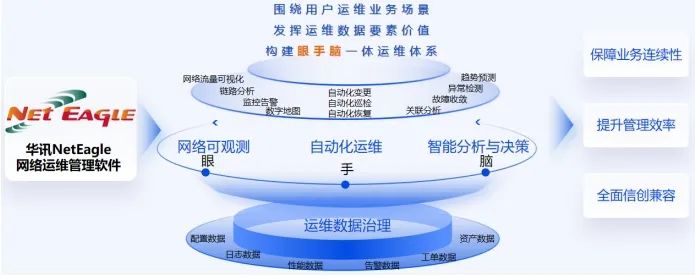
Smart IT Operation and Maintenance Network Management Software
Smart IT operation and maintenance network management software is a software platform for managing network infrastructure operations, assisting network operation and maintenance personnel in improving network service quality through standardized operation and maintenance management. It comprehensively observes network operating conditions through network device performance monitoring, port traffic monitoring, fault log analysis, and network health analysis, quickly locating and eliminating faults, ensuring stable network operation.
1
Core Competence:Network operational situation awareness, automated network operation and maintenance, AI large model-assisted decision-making, and operation and maintenance data visualization.
2
Application Scenarios:Automated management of the entire process of network configuration, network fault lifecycle management, and network operational health analysis.
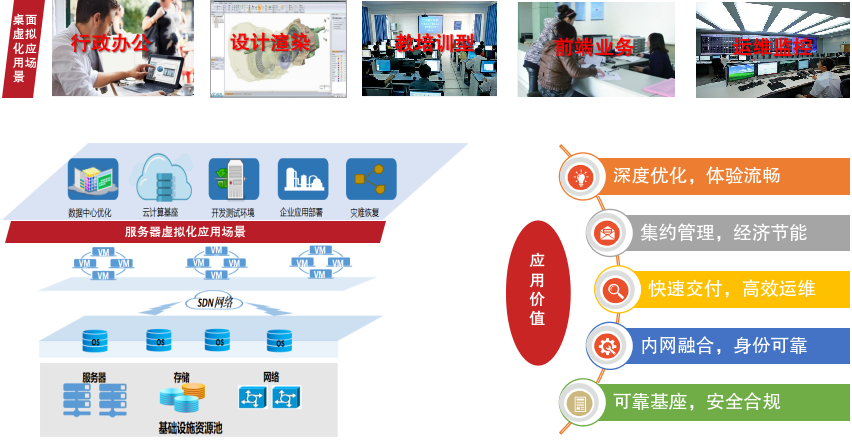
Virtualization System
The virtualization system deeply integrates encryption and security technologies, supporting pooled mixed management and intelligent scheduling of resources across various servers, storage, and network platforms, providing users with secure, manageable, and flexible virtualization solutions.
1
Unique Secret:Comprehensive security protection, high-performance graphics and image processing.
2
Core Competence:Unlimited clustering, second-level resource creation, economical and energy-saving, and compliant with security standards.
Security Suite System
The security suite system provides multi-dimensional integrated operation and maintenance management capabilities including asset management, policy management, data management, log auditing, and monitoring alarms.

1
Unique Secret:Real-time monitoring, auditing, and control, with no escape for violations; seamless integration of functions, centralized and efficient management, new and old integration, and heterogeneous compatibility.
2
Core Competence:Comprehensive, integrated, and multi-interactive, building a complete terminal security protection system.
Password Service Platform
Through a software development kit, it provides scenario-based password service capabilities, offering elastic expansion and scenario adaptation of password infrastructure and security services for cloud computing environments.
1
Unique Secret:Full-stack password service capabilities, multi-password device access, clustered password services, integrated regulatory systems, high-security systems, diverse product forms, and strong cross-industry application integration capabilities.
2
Core Competence:A triad of “password service + password regulation + password operation” for comprehensive password service assurance.
Integrated Security Gateway
The integrated security gateway is a dual-protocol product supporting both IPSec and SSL VPN protocols. Deployed at the network boundary, it provides confidentiality and integrity protection for user data transmission and identity authentication and access control for user application services, meeting high-security transmission requirements for user data at both the network and application layers.

1
Unique Secret:Three-dimensional encryption capabilities covering the link layer, network layer, transport layer, and application layer.
2
Core Competence:Ultra-high performance, with link load capabilities meeting the encryption transmission requirements of 100G backbone networks.
Source: China Electronics Technology Group