Follow ★ our official account to get information first-hand.
In modern society, embedded devices are ubiquitous, from smart homes in our daily lives to various industries such as industrial control and medical devices, the applications of embedded devices are endless.
So, what are the differences between functional safety and information security in embedded devices, and how can we ensure their implementation in practical applications?

What is Functional Safety?
Functional safety primarily focuses on ensuring that devices can operate safely in the event of a fault or abnormal situation, preventing harm to the environment and personnel. It emphasizes the system’s fault tolerance and safety protection, typically achieved through redundant design, fault detection, and self-recovery mechanisms.
In critical fields such as automotive, industrial control, and medical devices, functional safety is crucial. For example, in the automotive sector, if an embedded system in a vehicle fails, it could lead to brake system failure, resulting in serious traffic accidents.
Functional safety is relatively easy to understand; its core lies in ensuring that the system can maintain a safe state or enter a safe failure mode even when faults occur in the expected operating environment. This involves not only hardware design but also software development, testing, and validation. To achieve functional safety, engineers need to conduct comprehensive risk assessments, identify potential hazardous scenarios, and take corresponding measures to mitigate risks, ensuring the system’s reliability and safety.
What is Information Security?
In contrast to functional safety, which focuses on ensuring the correctness of the system in the event of a fault, information security emphasizes protecting the data processed by devices during operation, preventing data leakage, tampering, and unauthorized access. Information security relates not only to the confidentiality of data but also to its integrity and availability.
In embedded devices, information security is particularly important because these devices often need to connect to networks, making them easy targets for hacker attacks. For example, smart home devices may leak users’ private information, and industrial control devices may be hacked, leading to production line shutdowns or equipment damage.
“
Current Events: In 2015, a recall incident due to an information security vulnerability occurred in a certain car model, marking a significant turning point in automotive information security. Two white-hat hackers successfully connected to the vehicle’s Internet of Things (IoT) system via wireless communication, subsequently breaching the CAN bus network connected to the IoT system, gaining the ability to send commands to the system.
This allowed them to control critical systems such as the engine, transmission, brakes, and steering of the car. Since this intrusion was conducted wirelessly rather than through physical interfaces like OBD, the incident sparked widespread public concern about automotive information security.
Heartbleed Vulnerability Incident Overview
The Heartbleed vulnerability was first disclosed to the public in April 2014 and is considered one of the most severe security vulnerability incidents of the century, affecting two-thirds of the websites globally. The issue arose from the widely used open-source network communication encryption protocol OpenSSL.
The principle is that when two parties using OpenSSL communication establish a secure connection, the client needs to continuously send heartbeat messages (such as fixed-length strings) to the server, which, upon receiving them, returns the same fixed-length string to confirm that the server is available.
The heartbeat message sent by the client to the server contains data length and the information to be transmitted. Theoretically, the server’s OpenSSL should return information consistent with the data length. However, due to a flaw (vulnerability) in the OpenSSL code, the client could retrieve data from the server that far exceeded its permissions, potentially including sensitive information such as credit card numbers and passwords.
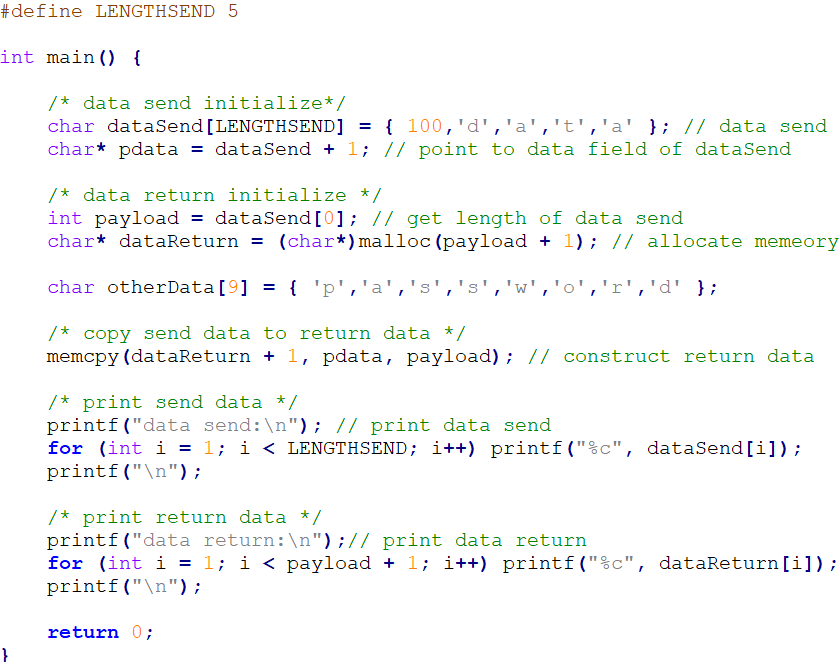
We use a simplified program (Note 1) to simulate this process. In the following program, at code 1, the heartbeat message sent by the client is constructed, but the data length information (100) is greater than the actual valid data (4, which is ‘data’). At code 2, similar to the OpenSSL protocol, the memcpy function is used to write data consistent with the data length information into the returned data packet.
 The program’s output is as follows; we see that the returned data contains information beyond the heartbeat packet data, which becomes the source of the security vulnerability.
The program’s output is as follows; we see that the returned data contains information beyond the heartbeat packet data, which becomes the source of the security vulnerability.
Source: MATLAB. Copyright belongs to the original author. If there is any infringement, please contact for deletion.
Common Functional Safety and Information Security Standards
In modern industrial and information technology fields, functional safety and information security have become crucial. To ensure the safety and reliability of systems and devices, a series of international standards and regulations have been established.
Functional Safety Standards
Functional safety primarily focuses on the ability of systems or devices to maintain a safe state in the event of a fault. Common functional safety standards include:
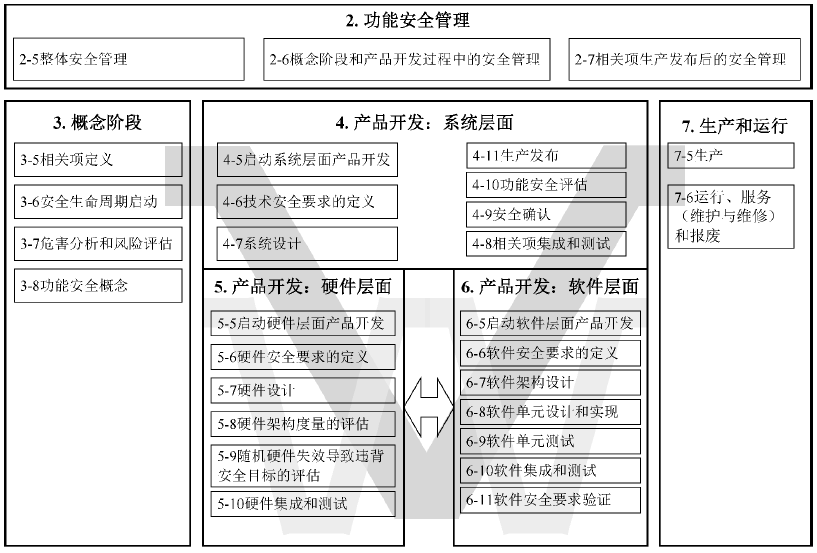
- ISO 26262: A functional safety standard for the automotive industry, covering the entire lifecycle from concept design to production, operation, service, and decommissioning.
- IEC 61508: An international standard applicable to electrical/electronic/programmable electronic safety-related systems, defining safety integrity levels (SIL) and providing safety requirements throughout the system lifecycle.
- EN 50126/8/9: Functional safety standards for railway applications, covering the design, implementation, and verification of railway signaling, control, and communication systems.
Information Security Standards
Information security focuses on protecting the confidentiality, integrity, and availability of information. Common information security standards include:
- ISO/IEC 27001: An international standard for information security management systems, providing requirements for establishing, implementing, maintaining, and continually improving an information security management system.
- ISO/IEC 27002: Provides specific information security controls and guidelines for ISO/IEC 27001, helping organizations select appropriate security controls.
- GDPR (General Data Protection Regulation): A data protection regulation established by the European Union aimed at protecting the privacy and security of personal data, applicable to all organizations processing personal data of EU residents.
- NIST SP 800 Series: Security standards and guidelines published by the National Institute of Standards and Technology, covering various aspects of information security, such as risk management and encryption technologies.
These standards and regulations provide guidance for functional safety and information security across different industries, ensuring that systems and devices meet the corresponding safety requirements during design, development, deployment, and operation.
Must-Read for Software Engineers
In the development of embedded systems, functional safety and information security are closely related and need to be considered from the design phase. Security should be integrated into the overall design of the system, following industry standards and conducting comprehensive risk assessments.
Functional safety requires redundant design, fault detection, and self-recovery mechanisms for the system, while information security necessitates measures such as encryption, authentication, and identity verification to protect the confidentiality and integrity of data. During the development process, thorough security validation and testing should be conducted, including functional safety validation and information security penetration testing, to promptly identify and fix potential vulnerabilities.

At the same time, security design needs to balance performance and security, avoiding system performance degradation due to excessive security measures. Furthermore, with the emergence of new technologies and attack methods, it is crucial to maintain attention to the security field and update protection strategies in a timely manner. Team members should also receive regular training to ensure a thorough understanding of security design, facilitating effective collaboration to ensure the security of the design throughout the system lifecycle.
Recommended Reading
|
01 |Join the Embedded Development Group |
|
02 |Embedded Resource Acquisition |
|
03 |Detailed Explanation of STM32 Interrupt Priorities |
|
04 |New Approach to Downloading Programs on STM32 – Using Serial Port to Download Programs |