
Global Technology Map
Innovation | Frontier | Science Popularization | Information

In recent years, the Central Committee of the Party and President Xi have placed great importance on the construction and development of self-controlled cybersecurity. The ZTE incident has also shown that self-control is the path for the development of China’s cybersecurity industry, and core technology is the national treasure. In March 2016, a disclosure by the U.S. Department of Commerce marked the beginning of the ZTE incident. After two years, on April 16, 2018, the U.S. Department of Commerce announced the immediate reactivation of sanctions against ZTE (Order Activating Suspended Denial Order), prohibiting ZTE from importing goods from the U.S. in any form. This also meant that the settlement agreement signed by ZTE in March 2017 was declared a failure. Being completely banned by the U.S. was undoubtedly catastrophic for ZTE, which heavily relied on imported chips and other components from the U.S.

The Lessons from the ZTE Incident
It is clear that there should be no illusions about introducing high-tech. We must recognize that:Key core technologies cannot be obtained, bought, or begged for. Whether for the U.S., China, or other countries, major national treasures must be in our own hands. We are in a globalized world, which provides cheaper solutions to problems, but also breeds laziness. When buying chips is easier and cheaper than producing them ourselves, a market orientation forms, and dependence on external technologies solidifies. While it may seem economically advantageous in the short term to use commercially available chips, once restrictions are imposed, we will find ourselves in trouble.
Statistics show that in 2017, China spent 1.364 trillion RMB on imported commercial chips, and over the past decade, China has spent more than 10 trillion RMB on chip imports, equivalent to one-eighth of China’s GDP in 2017. Moreover, the U.S. has consistently imposed embargoes on high-end military chips to China. Boeing was fined several hundred million dollars by the U.S. government for using military-grade chips in the planes it sold. The ZTE incident fully exposed our issues of being constrained in the supply chain, so we should carefully analyze the domestic industry situation, identify its “disadvantages” and “advantages,” and formulate corresponding strategies to enhance risk resistance.
Security Risks and Supply Chain Risks are Equally Serious
The ZTE incident has not fully exposed security risks. In fact, the dilemma of being constrained by core technologies not only brings supply chain risks but also security risks, both of which are equally serious. For example, potential security risks in desktop operating systems include being monitored, hijacked, attacked, “shut down” or “banned,” loss of certificate keys, inability to harden, patch, or support domestic CPUs, etc. (There are no industry standards, for reference only).
For instance, in June 2013, former CIA employee Edward Snowden disclosed the “Prism” incident of the NSA, which is a typical example of being monitored.
Regarding the security risk status of various commonly used desktop operating systems, the Win7 system has two risks: loss of certificate keys and inability to harden, as it does not include password management and trusted computing technology; the main risk of domestic Linux operating systems is being attacked by viruses and Trojans. Therefore, it can be concluded that promoting domestic operating systems is of great significance for enhancing security.
The Overall Situation of China’s Cybersecurity Field
General Secretary Xi Jinping stated during the 36th collective study session of the Political Bureau of the Central Committee on implementing the strategy of a strong cyber power: “Network information technology is the field with the most concentrated global R&D investment, the most active innovation, the widest application, and the greatest radiating and driving effect. It is the competitive high ground of global technological innovation.” President Xi emphasized the need to firmly grasp the “bull nose” of independent innovation in core technologies, to quickly break through frontier technologies in network development and key core technologies with international competitiveness, to accelerate the promotion of domestic self-controlled replacement plans, and to build a secure and controllable information technology system. We must reform the mechanism for the input-output of scientific research investment and the transformation of scientific research achievements, implement a strategic attack on core technology equipment in the field of network information, and promote significant breakthroughs in the R&D and application of high-performance computing, mobile communication, quantum communication, core chips, operating systems, etc.
China’s overall technological strength is lower than that of the U.S., but after decades of reform and opening up, a considerable foundation has been laid, and strength has been accumulated. In recent years, the development of China’s cybersecurity field has shown latecomer advantages such as new technology, rapid development, and significant talent contributions. Objectively speaking, the overall level of technology and industry in China’s cybersecurity field ranks second in the world, second only to the U.S.
According to the market capitalization ranking of global listed ICT companies, among the top 10 globally, the U.S. has 6 companies, while China has 3, namely Alibaba, Tencent, and Huawei (although Huawei is not listed, its valuation can rank in the top 10).
The Advantages and Disadvantages of China’s Cybersecurity Field
China’s disadvantages in the cybersecurity field are obvious, such as chips and basic software, which are easily constrained by others, but there are also some advantages.
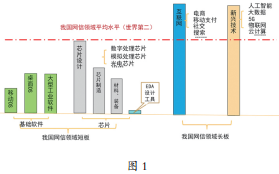
Two Major Disadvantages: One is Basic Software, and the Other is Chips.
The chip industry chain is long. China has been able to produce mid-to-low-end chips, but producing more precise chips requires greater investment. The second phase of national chip production may require an investment of over 200 billion, but it also needs market response and strong support from social capital. For example, China imports over 200 billion U.S. dollars worth of chips every year. If a significant portion of this huge market’s funding is used to support the development of domestic chips, then domestic chips will become unstoppable. Once China loses its market, U.S. high-tech companies will find it difficult to continue upgrading their products.
In the past, the Chinese market did not doubt the credibility of U.S. suppliers and did not consider the consequences of a potential supply cut from the U.S. However, the experience of ZTE has proven that U.S. supplies are not reliable. The global supply chain is fragile in the face of politics. The U.S. has begun to seriously consider how to curb China’s rise, and restrictions on high-tech exports to China have always been its trump card, which may expand in the future. China is the largest telecommunications market in the world, and the market is power. We have always hoped to exchange technology for the market, which is reasonable. The U.S. has rejected our approach, so we should directly use the market to support the R&D of our high-tech companies.
In terms of basic software, especially mobile and desktop operating systems, they have long been monopolized, and large industrial software is also our disadvantage. Large manufacturing, shipbuilding, aircraft, and engines all require large industrial software, but our technology in this area has not reached a certain height, which needs to be taken seriously. The state has invested a lot of funds in hardware, but it is unclear whether there is funding for software. The overall situation indicates that insufficient investment in software R&D is also a disadvantage.
In addition, we also see some advantages, or areas where the gap is relatively small. The first is the application of the Internet, and the second is emerging technologies. Foreigners acknowledge that domestic e-commerce, mobile payments, social networking, and search are ahead of foreign countries, which is our strength. In terms of emerging technologies, such as artificial intelligence, big data, 5G, the Internet of Things, and cloud computing, these are our current advantages.
Before the ZTE incident, some people were relatively optimistic and overestimated our cybersecurity field. After the ZTE incident, some became pessimistic, feeling that we are far behind developed countries. We should not be too pessimistic or too optimistic; we must objectively recognize our advantages and subjectively acknowledge our disadvantages and make up for them. By leveraging strengths and compensating for weaknesses, we can achieve a leapfrog development to catch up with developed countries through Internet applications and better development of the new generation of information technology.
We Must Firmly Control Core Technologies
General Secretary Xi Jinping has long proposed that “core technology is the national treasure.” He emphasized this at the cybersecurity work symposium in April 2016, warning that “the core technology of the Internet is our biggest ‘lifeline.’ Being constrained by core technology is our greatest hidden danger. Even if an Internet company is large in scale and high in market value, if its core components are heavily dependent on foreign sources, and the ‘lifeline’ of the supply chain is in the hands of others, it is like building a house on someone else’s foundation; no matter how big or beautiful it is, it may not withstand the wind and rain, and may even collapse at a blow.”

In terms of key core technologies, especially in the cybersecurity field, good technologies and good products are not only unavailable but also not visible in the market. Why? Because of the strong monopoly. How should we face such a severe situation? This requires us to firmly control core technologies and take the path of “domestic substitution” to achieve “security and controllability.”
General Secretary Xi Jinping proposed in a series of speeches on cybersecurity: “Accelerate the promotion of domestic self-controlled replacement plans and build a secure and controllable information technology system.” This is a major task in the cybersecurity field. Given the high monopoly in the cybersecurity field, if new domestic software and hardware cannot break the monopoly, they will ultimately perish; only those with the ability to replace monopolists can survive and grow in market competition. For a considerable period in the future, domestic substitution will become the new normal in China’s cybersecurity field.

Replacing the Wintel System with Domestic Desktop Systems
Specifically, it is to replace the Wintel architecture (Windows operating system + Intel architecture CPU) with the domestic desktop computer technology architecture “1+3”: domestic Linux operating system + 3 types of domestic CPUs (Shenwei / Feiteng / Loongson).
The Wintel computer technology system, composed of Microsoft’s Windows operating system and Intel’s CPU, currently monopolizes the global desktop computer field. Since IBM launched the PC personal computer in 1981 using Intel’s CPU, and Microsoft launched Windows 3.1 in 1992, the Wintel architecture has dominated the desktop computer field.
Wintel has gone through more than 20 years, and today, whether as a technology system or a business alliance, it has clearly entered a period of decline: in the fields of cloud computing and servers, data centers using open-source Linux operating systems and non-Intel CPUs are increasing, and in this field, Wintel has no advantage. Even in the desktop field, where Wintel has long held a monopoly, its market share is shrinking.
Statistics show that currently, Mac OS occupies 9.02% and Linux occupies 2.12% of the market share. Additionally, Google’s Chromebook has captured half of the market in U.S. education. The current push in China to replace Wintel will also accelerate this trend.
With the rapid development of the mobile ecosystem, the mobile ecosystem has become increasingly important, significantly reducing Wintel’s advantages in the ecosystem. Today, replacing the Wintel system is easier than ever.
Microsoft has repeatedly stated that it will stop technical support for Win7 in January 2020, forcing users to adopt the uncontrollable WIN10, which has failed security reviews and may pose all security risks of desktop operating systems. Therefore, government and critical sectors cannot use it, which also requires us to accelerate the promotion of replacing Windows operating systems with domestic Linux operating systems.
Currently, the replacement at the office level is not too difficult. The development process of software and hardware in the cybersecurity field generally goes through three stages: “unusable” – “usable” – “good to use.” Therefore, it is essential to emphasize market guidance (for example, through government procurement) to give these initially “unusable” domestic technologies opportunities for application, to discover problems during application, and to continuously improve, ultimately evolving from “unusable” to “usable” and “good to use.” The ongoing work of promoting the safe and reliable application of electronic document systems in party and government agencies essentially aims to replace the Wintel system with domestic computer technology systems. With the maturity of domestic software and hardware development, this goal can be achieved, which certainly requires further technological advancement in the future. In fact, the domestic desktop computer technology system has already reached a usable level, with some achieving a good level of usability.
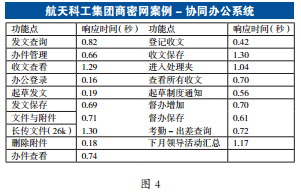
The Aerospace Science and Industry Corporation’s “Commercial Secret Network” is a typical example of implementing self-controlled substitution, adopting a cloud service model, with 40,000 users, and has been running stably for over two years. Its data center and terminals have basically achieved domestic production, with 28,000 domestic fixed terminals (domestic CPU + operating system) supporting domestic mobile terminals (domestic CPU + operating system). Its data center uses domestic application system servers and database servers. The measured performance indicators fully meet the requirements, reaching “usable” status, with user experience comparable to Wintel. It is currently continuing to improve towards “good to use.” Practice has proven that the goal of “accelerating the promotion of electronic document systems and achieving domestic substitution as soon as possible” is entirely achievable. If we can adopt advanced cloud service models like the “Commercial Secret Network,” this substitution can certainly be realized sooner.
However, the urgent issue to be resolved is the core of the domestic system—the Linux operating system should achieve resource integration. Currently, there are about ten Chinese companies of similar size each fighting their own battles, making it difficult to compete with Microsoft.
Replacing IOE with High-End Servers and Databases
Currently, there are conditions to implement the replacement of high-end servers and databases, which are core components of cloud computing data centers, historically monopolized by developed countries.
Now, data centers in industries such as finance in China have mainly transitioned from “IOE” to Intel x86 servers + Oracle databases. Recently, the Aerospace Super Server (including the Aerospace Kunlun database) has fully surpassed Intel’s mainstream servers in terms of cost-performance ratio, creating conditions for this replacement.
Compared to Intel servers, the Aerospace Super Server (including the Aerospace Kunlun database) supports 3,000 nodes, with actual tests showing 140 nodes and a performance acceleration ratio of 54%.
The Aerospace Kunlun Super Database passed the “Software Product Technical Appraisal Test” by the Ministry of Industry and Information Technology’s China Software Testing Center in August 2017, with a performance exceeding 10,000 TPS in the CAE benchmark test and a response time of less than 2 seconds. Reports from the China Software Testing Center show that its TPC-C benchmark test performance is 11.98 million tpmC, equivalent to the second highest level in the world according to TPC public data, 1.83 times that of Intel’s platinum 8-way servers. This is a self-controlled, domestically produced high-performance database that can be compatible with Oracle, completing the replacement of multiple Oracle systems with “0 code modification” and an average migration period of about two weeks. Therefore, using high-end servers and databases to replace “IOE” greatly benefits our cost-performance ratio and energy efficiency, and can truly replace IOE in all aspects.
Replacing Domestic ERP with SAP ERP
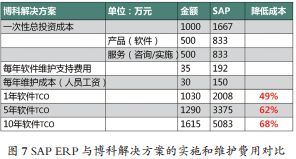
SAP is currently the largest ERP software company in the world, and its ERP (Enterprise Resource Planning) software name has become synonymous with ERP software. Nearly 80% of the Fortune 500 companies use SAP software, and almost 90% of large state-owned and private enterprises in China use SAP software, making it difficult to replace. However, SAP ERP is the “best practice” of management experience from the industrial era, which is not suitable for the AI and mobile Internet era.
The core application layer of SAP still uses ABAP technology from the 1970s, with a newly developed web-based Fiori interface at the display layer, and the underlying layer using HANA in-memory computing technology. The technology architecture is aging and inflexible, unable to meet the personalized business needs of enterprises, and the software’s extensibility is poor. Many domestic enterprises only use a few modules of SAP, such as financial accounting and management accounting. Moreover, the interface is not user-friendly, and the software maintenance costs are extremely high, which is clearly not suitable for Chinese enterprises.
After redefining enterprise management software, the domestic company Boke has developed corresponding solutions that we believe can reach a level of replacement. The corresponding platform does not require software personnel; business personnel can define interfaces and data relationships, automatically generate without coding, achieving very good efficiency, and users are very satisfied. This replacement process is also underway.
Similar cases include domestic enterprise software SaaS and mobile apps, which are significantly superior to SAP ERP’s mobile apps in terms of performance, user experience, and scenario-based functional design. Companies like Alibaba and Tencent have provided new application systems and technologies such as e-commerce, mobile payments, and digital marketing, surpassing SAP Cloud ERP, SAP Cloud Platform, and SAP HANA. Suning is a typical case of moving away from SAP: its original SAP ERP data has basically been emptied, and it has shifted to third-party big data platforms, completely abandoning SAP is only a matter of time.
Replacing Domestic Real-Time Operating Systems with VxWorks
Industrial real-time operating systems are core technologies for the industrial Internet, industrial control systems, etc., which relate to the safety of various industries. In the past, this field was monopolized by foreign operating systems such as VxWorks and QNX, posing significant information security and network security risks.
Chinese scientists began to independently develop the Yihui SylixOS from 2006, and after 12 years of development, it has been validated in multiple key areas. It is widely used in important fields such as aerospace, national defense, military industry, electric power, rail transit, industrial automation, and robotics.
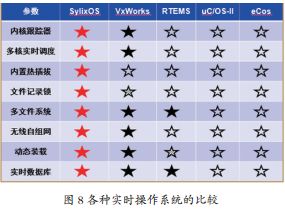
Yihui Information’s SylixOS is currently the only large real-time operating system in China with complete independent intellectual property rights. The Ministry of Industry and Information Technology’s Software Evaluation Center has assessed SylixOS’s kernel autonomy rate at 100%.

SylixOS is powerful and has excellent real-time performance. In June 2015, Tsinghua University completed a real-time performance evaluation of SylixOS. On the AM335X processor (Cortex-A8 800MHz) hardware platform, SylixOS, Linux, and RT-Linux operating systems were run, using the Hackbench tool to provide a stress environment and the Cyclictest tool for real-time testing. The results of 100,000 stress tests are as follows:
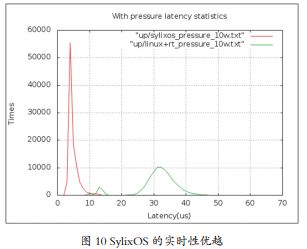
Currently, the conditions for replacing foreign VxWorks with Yihui SylixOS have basically matured, but there are still many obstacles to overcome, such as interference from some “disguised” non-self-controlled operating systems; some units lack awareness of network security and risk awareness; and some industries’ thresholds do not meet network security requirements. Therefore, the main obstacles to this replacement are non-technical.
How to Achieve Self-Control
General Secretary Xi recently pointed out: “The core of network security is technological security.” Self-controlled technology does not equal technological security, but non-self-controlled technology is certainly not secure, because only self-control can ensure technological security, and technological security is the guarantee of network security. Therefore, we should regard self-control as a necessary condition for achieving technological security and network security. The ZTE incident serves as a lesson from the past when there was no institutional guarantee for self-control. Here are three suggestions:
Multi-Dimensional Assessment
To achieve self-control, relevant departments have proposed implementing multi-dimensional assessment requirements, including self-controlled assessments: evaluating the self-control of products/services/systems, which can target core technology products such as CPUs and operating systems, as well as other software or hardware or services, and even an information system or information infrastructure; quality assessment: evaluating the functionality, performance, and other technical indicators of products/services/systems; security assessment: evaluating the security of products/services/systems, which may be combined with assessments of “equal protection” and “segmented protection.”
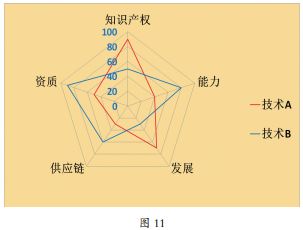
Here, we also propose a reference for self-controlled assessment considerations.
Figure 11 shows a general plan for self-controlled assessment, which is more suitable for CPU and OS products. If it is for cloud computing, big data, and other cloud services, in addition to assessing these indicators, it should also focus on evaluating whether the software and hardware used are self-controlled, whether the infrastructure is deployed domestically, whether sensitive information does not leave the country, whether user privacy information is not leaked, and whether it can defend against network attacks, among other contents. Of course, it should also meet the requirements for building a secure and controllable information technology system.
Call on Enterprises to Learn from Huawei and Have Backup Systems When Necessary
Huawei places great importance on self-control. As early as 2012, Huawei’s founder Ren Zhengfei stated in response to the question, “Why continue to develop terminal operating systems when there is no ecological space?” that we should try to use good foreign products, including high-end chips and operating systems, but we must have strategic backups. Enterprises should learn from Huawei and have backup systems when necessary to minimize or avoid incidents like ZTE.
Individuals: Support and Use Domestic Software and Hardware to Contribute to Self-Control
Domestic software and hardware must achieve good usability through continuous use and improvement. Therefore, as users, everyone should support and use domestic software and hardware, which contributes to self-control. Suggestions: ① Do not hold prejudices against domestic software and hardware, but be willing to accept them; ② When encountering problems during use, do not complain, but provide timely feedback; ③ Be willing to change certain usage habits to adapt. I believe that domestic self-controlled software and hardware will rapidly develop and mature with everyone’s support, better ensuring network security.

Author: Ni Guangnan
Source: Information Security and Communication Confidentiality Magazine
Selected from:
“Information Security and Communication Confidentiality” 2018 Issue 11
