Click above to easily subscribe to “China Computer Federation“!
Source: “China Computer Federation Communications” 2018 Issue 1 “Column”

The processor instruction set is the interface between hardware and software, serving as the cornerstone of the core hardware and software ecosystem, and its importance is self-evident. In 2011, the University of California, Berkeley, released the open instruction set RISC-V, quickly establishing an open-source hardware and software ecosystem. Many companies began integrating RISC-V into their products; for instance, Western Digital, the world’s largest hard drive manufacturer, recently announced that it would replace one billion processor cores embedded in various storage products each year with RISC-V. The Indian government has vigorously funded RISC-V-based processor projects, making RISC-V the de facto national instruction set of India. This article mainly discusses the author’s views on India’s initiatives and the development trend of RISC-V.
National Instruction Set
In 2012, China planned to establish a national standard for CPU instruction sets under the promotion of the Ministry of Industry and Information Technology. However, on one hand, several domestic companies chose different instruction sets for their domestic processors, leading to a lack of consensus; on the other hand, designing a completely new instruction set from scratch proved daunting, resulting in the gradual abandonment of the national instruction set initiative. Years later, the instruction sets being developed for domestic processors are diverse, including ARM, MIPS, PowerPC, SPARC, SW64, RISC-V, x86, and more, likely the most varied in the world. Among domestic processors, Loongson and Shenwei have been persistent in creating their own ecosystems; while ARM-based HiSilicon, Feiteng, Huaxintong, and x86-based Haiguang, Zhaoxin hope to leverage existing ecosystems to expand their markets. This apparent prosperity, however, seriously disperses the already scarce foundational software development resources, causing developers and enthusiasts of foundational software such as compilers and operating systems to be unable to optimize for all instruction sets due to limited energy, thus delaying the construction of an independent ecosystem. This situation also severely impacts undergraduate education in computer science¹. The current curriculum system lacks relevant standards, and many schools offer different courses that require students to use different instruction sets for experiments, leading students to focus on understanding various instruction set assembly languages while neglecting the essence of instruction set design and the relationship between instruction sets and processors/compilers/operating systems.
Let’s take a look at our neighbor, India. In 2011, India began implementing a processor strategy plan, funding 2-3 projects nationwide to develop processors. Professors G. S. Madhusudan and V. Kamakoti from the Indian Institute of Technology, Madras, launched the SHAKTI processor project with support from this plan, aiming to develop a processor compatible with IBM PowerPC. To obtain legal authorization, the SHAKTI project team negotiated with IBM but failed to reach an agreement. Meanwhile, the University of California, Berkeley, introduced the open instruction set RISC-V, with its prototype chip successfully taped out in January 2013². Consequently, in 2013, the SHAKTI project team resolutely abandoned PowerPC and fully embraced RISC-V—adjusting the project goal to develop six open-source processor cores based on the RISC-V instruction set. RISC-V encompasses various application areas, including 32-bit single-core microcontrollers, 64-core 64-bit high-performance processors, and secure processors. The temporary adjustment of the project goal not only went uncriticized but also received greater support from the government, with the adjusted SHAKTI project obtaining $90 million in funding³. In January 2016, the Centre for Development of Advanced Computing (C-DAC), which has long been engaged in supercomputer research, received $45 million from the Indian Ministry of Electronics and Information Technology, aiming to develop a 2GHz quad-core processor based on the RISC-V instruction set. In another government-supported project concerning a neuromorphic accelerator, RISC-V was also chosen as the main computing core. In recent years, as processor-related projects funded by the Indian government have begun to converge towards RISC-V, it has become the de facto national instruction set of India.
Comparing the initiatives of China and India regarding national instruction sets, I have grown more concerned about the future development of CPUs in China. This concern stems from my deep involvement in the RISC-V community and my understanding of this open instruction set. Here, I hope to interpret my concerns by introducing the origins, current status, and development trends of RISC-V, as well as my experiences serving on the program committee of the 7th RISC-V International Workshop. I hope more interested colleagues will pay attention to this topic, and I also hope that knowledgeable individuals will point out any biases or omissions in my views, proving that my worries are unfounded—this would indeed put my mind at ease.
Origins of RISC-V
In 2010, a research team at the University of California, Berkeley, was preparing to launch a new project and needed to choose a processor instruction set. They analyzed several instruction sets, including ARM, MIPS, SPARC, and x86, and found that these instruction sets not only became increasingly complex but also had intellectual property issues. Thus, the Berkeley research team temporarily formed a four-person group⁴ to undertake a three-month summer project—to design a completely new instruction set from scratch! The goal of this small project was to create a new instruction set that could accommodate processors of various sizes, from microcontrollers to supercomputers, support various implementations from FPGAs to ASICs, and even future devices, efficiently implement various microarchitectures, support extensive customization and acceleration features, and adapt well to existing software stacks and programming languages. Most importantly, it had to be stable—unchanging and enduring.
In May 2011, the first version of the instruction set was officially released. The design of this instruction set was very simple, adopting a base instruction set and an extended instruction set. The base instruction set contains fewer than 50 instructions but is sufficient to implement a processor with basic functions such as fixed-point operations and privileged modes. The extended instruction set provides some commonly used atomic operation instructions, floating-point operation instructions, etc., and users can customize it according to their needs. This instruction set retains the significant advantage of being “simple” while providing users with sufficient flexibility. When releasing this instruction set, the Berkeley research team made two significant decisions:
First, the new instruction set was named RISC-V (pronounced RISC-Five), indicating the fifth generation of RISC (Reduced Instruction Set Computer). Figure 1 shows the prototypes of the previous four generations and the fifth generation of RISC processors. Each generation of RISC processors was completed under the leadership of the same person, Professor David Patterson from the University of California, Berkeley. He, along with his student David Ditzel, coined the term “RISC” in their classic 1980 paper “The Case for the Reduced Instruction Set Computer.”
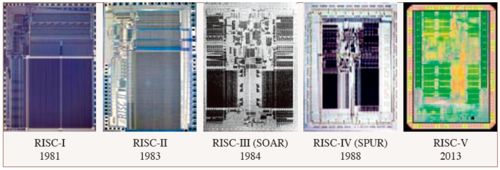
Figure 1 David Patterson leading the development of the fifth generation RISC processor
Second, the RISC-V instruction set was completely opened, using the BSD License open-source protocol. The Berkeley research team believed that the instruction set architecture (ISA), as a specification and description standard for the hardware-software interface, should not require paid licensing for use like ARM, PowerPC, x86, etc., but should be open and free. The BSD open-source protocol chosen for RISC-V grants users significant freedom, allowing them to modify and redistribute the open-source code, as well as develop and sell commercial software based on the open-source code.
Thus, a brand new open instruction set RISC-V was born—any company, university, research institution, or individual in the world can develop processors compatible with the RISC-V instruction set and integrate into the hardware and software ecosystem built on RISC-V without paying a dime for the instruction set. The Berkeley research team has high hopes for RISC-V, hoping it can be applied in various scenarios, from microcontrollers to supercomputers; they also hope it can become one of the de facto standards for operating systems worldwide through open-source, like Linux, ultimately becoming the de facto standard for processor instruction sets worldwide, laying a foundational contribution for the next 50 years of computer system design and innovation.
Growing Amidst Doubts
Although the goals are ambitious and the vision is beautiful, the first version of RISC-V did not receive attention and did not achieve the expected response; instead, it faced numerous doubts. On one hand, many academics believed that the RISC-V instruction set lacked technical innovation, and professors at Berkeley should not engage in such non-innovative academic work. Therefore, RISC-V-related work was also difficult to publish in top academic conferences like ISCA. On the other hand, the industry was also cautious about this new instruction set launched by academia, as for commercial processor design, merely having a free open instruction set is far from sufficient; many peripheral modules of processors (such as memory controllers) still require expensive IP licensing fees. Moreover, an open instruction set does not guarantee good performance; the performance of processors is related to the specific designs of some core modules (such as branch predictors, multi-level caches, and memory prefetchers), which is not significantly affected by the choice of instruction set. Therefore, designing high-performance processors based on RISC-V may still face patent barriers from existing processor manufacturers regarding the specific designs and engineering implementations of core modules.
In response to various doubts, the Berkeley research team took a cautious approach, implementing three major measures:
First, they advanced RISC-V directly from concept to prototype chip stage, using real data from prototype chips to address industry concerns about its performance. Since 2011, the research team designed and implemented a sequentially executing 64-bit processor core based on the RISC-V instruction set (codenamed Rocket), and conducted 12 tape-outs based on 45nm and 28nm processes. The Rocket chip has a clock frequency greater than 1GHz, with measured performance 10% higher than that of the ARM Cortex-A5, and area efficiency 49% higher, with dynamic power consumption per unit frequency only 43% of that of the Cortex-A5. These data indicate that the RISC-V Rocket processor core has competitive capabilities. The Berkeley research team also launched the open-source out-of-order execution core BOOM (Berkeley Out-of-Order Machine), and Figure 2 shows that its performance can reach the level of mid-range ARM processors. In 2015, the Berkeley research team took another step forward by establishing the startup SiFive to accelerate the commercialization of RISC-V. SiFive’s positioning is similar to that of Red Hat, which is based on the Linux open-source community, and Databricks, which is based on the Spark open-source community, providing users with high-performance processor IP cores and SoC chips integrated with peripheral component IP.
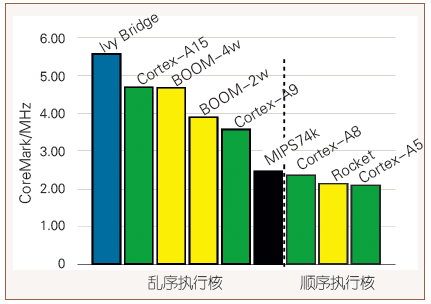
Figure 2 Performance comparison of RISC-V processor cores (yellow bars)
Second, they established the non-profit RISC-V Foundation in 2015, aiming to unite global efforts to build an open and collaborative hardware and software community, creating the RISC-V ecosystem. Within two years, over 100 organizations joined the RISC-V Foundation (as shown in Figure 3), including leading international companies such as Google, Huawei, IBM, Micron, NVIDIA, Qualcomm, Samsung, and Western Digital, as well as academic institutions like the University of California, Berkeley, MIT, Princeton University, ETH Zurich, Indian Institute of Technology, and the Institute of Computing Technology, Chinese Academy of Sciences. These companies and research institutions can participate in the evolution of instruction set specifications and the development of the hardware and software ecosystem through the RISC-V Foundation.
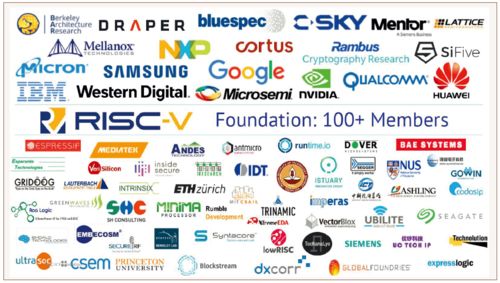
Figure 3 Overview of RISC-V Foundation members (7 members from China, including 1 from academia)
Third, they strengthened publicity efforts to expand international influence. Since 2015, the Berkeley research team has organized RISC-V technical workshops to establish a face-to-face technical exchange platform for RISC-V developers, users, and researchers. RISC-V workshops typically last three days and include around 40 technical reports covering RISC-V technology updates, software ecosystems, emerging applications, and cutting-edge research. The first RISC-V workshop was held in January 2015 (and has now been held 7 times). At each RISC-V workshop, attendees can always see a kind elder sitting in the front row, attending the workshop in its entirety. He is Professor David Patterson, the founder of the RISC architecture and the creator of the term RISC. In the field of computer architecture, Professor Patterson holds a high reputation, and his presence attracts many admirers. To expand the influence of RISC-V, even in his old age, he tirelessly travels around the world to promote it. In 2015 alone, he visited many prestigious universities, including Harvard, Princeton, Cornell, the University of Washington, the University of Illinois at Urbana-Champaign, UCLA, and UC Santa Barbara, giving dozens of lectures worldwide. His lecture was titled “Instruction Sets Want To Be Free: A Case for RISC-V.” His talks greatly enhanced people’s understanding of RISC-V.
The combination of measures implemented by the Berkeley research team quickly allowed RISC-V to grow into a highly participatory open-source community worldwide.
Development Prospects
What are the prospects for RISC-V? I am often asked this question. Here, I intend to share my observations and experiences as a member of the program committee for the 7th RISC-V International Workshop, introducing the current status and development prospects of RISC-V from the perspective of the workshop organizers.
In 2015, the first RISC-V workshop had 144 participants from 33 companies and 14 universities. However, in less than three years, the RISC-V workshop rapidly expanded into a medium-sized conference—the 7th RISC-V workshop held in November 2017 had reached 500 participants, including 138 companies and 35 universities and research institutions from around the world.
The program committee for the 7th RISC-V workshop consisted of 8 representatives from world-class companies and research institutions, as shown in Table 1. They were responsible for soliciting technical reports, reviewing submissions, and other tasks. Since my team’s project on the Labeled RISC-V architecture, presented at the 6th RISC-V workshop, received recognition and attention from international peers, I was fortunate to be selected for the program committee of the 7th RISC-V workshop, deeply participating in the organization of the workshop (Figure 4).
Table 1 Program Committee Members of the 7th RISC-V Workshop
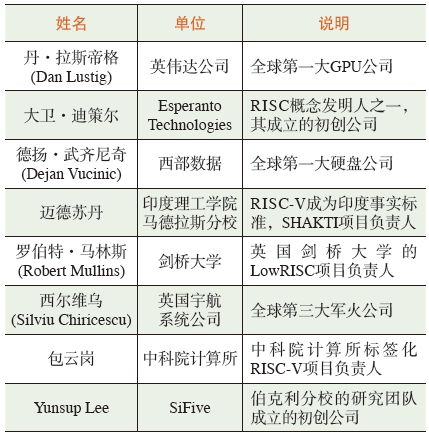

Figure 4 The Labeled RISC-V team with Professors Patterson and Asanovic from Berkeley⁵
This program committee began holding monthly conference calls in July 2017 to discuss the progress of the workshop organization. Ultimately, this workshop received about 80 submissions, mainly from companies and universities in Europe and the United States (about 90%), with a few submissions from China, South Korea, and India.
From the content of the submissions, it is evident that RISC-V is rapidly developing in various dimensions, and a new, vibrant hardware and software ecosystem is beginning to take shape: (1) The submitting organizations are diverse; in addition to large companies like Google, NVIDIA, and Western Digital, as well as universities like MIT and the University of Washington, many submissions come from startups, with Global Foundries even customizing optimizations specifically for RISC-V. (2) The application scenarios are diverse, including cutting-edge research funded by the U.S. Department of Defense’s DARPA, astronaut chip design for spacecraft, smart chips for the Internet of Things (IoT), security chips, and controllers for motherboard management in servers, GPUs, and hard drives. (3) The hardware and software ecosystem is gradually improving, with a significant proportion of work focusing on the design of RISC-V peripheral modules and toolchains, such as debugging toolchains and interrupt controllers. Another batch of work is focused on porting and optimizing software, including real-time operating systems, JVM, LLVM, Python, and other commonly used software tools for developers.
After review and discussion by the program committee, 47 submissions were ultimately accepted. The program committee recommended two keynote speeches: one from the host Western Digital, where Chief Technology Officer Martin Fink brought exciting news to the entire RISC-V community—every year, one billion processor cores used in Western Digital products will be replaced with RISC-V processor cores⁶. The other report was presented by DARPA project manager Linton G. Salmon, discussing the significance of open-source hardware IP for national defense. Although RISC-V has significant advantages, in the rational view of DARPA, it is still far from sufficient. Therefore, in recent years, DARPA has increased its investment in this area, funding five open-source hardware projects (PERFECT, CRAFT, SSITH, POSH, IDEA), some of which explicitly require development based on the RISC-V instruction set.
Returning to the initial question, I believe the RISC-V open-source community has passed the difficult initial stage and is entering a period of rapid development, with optimistic prospects. First, in the control field and IoT scenarios, an increasing number of products and application cases based on RISC-V will emerge; second, in the software open-source community, more and more software will be adapted and optimized for RISC-V, such as the recent announcement from the Linux community that the official Linux 4.15 kernel will support RISC-V; third, in foundational research, there will be an increasing number of cutting-edge research projects based on RISC-V, cultivating and delivering a batch of technical talents who deeply understand the RISC-V architecture to the open-source community. In fact, among the 47 reports at the 7th RISC-V workshop, 15 came from academia. Notably, at the first “Computer Architecture Research using RISC-V” workshop held at the top microarchitecture conference MICRO in October 2017⁷, RISC-V even surpassed machine learning themes to become the most attended workshop.
How Should China Respond?
Given the openness of RISC-V, more and more government projects in various countries are beginning to choose RISC-V, including the aforementioned Indian government, the U.S. DARPA, and the Israel Innovation Authority, which has also chosen to develop a processing platform based on RISC-V for national enterprises. So how should China respond to the surging RISC-V? In fact, RISC-V has already formed a considerable climate domestically:
1. Companies have begun actively participating in the RISC-V open-source community, with many companies developing products based on RISC-V. In the RISC-V Foundation, Taiwan’s Andes Technology is a founding member, Huawei is a platinum member, and there are several silver members such as MediaTek, Shanghai Jincheng Technology, Xi’an Youxi Technology, and Guangdong Gaoyun. Additionally, a number of startups are also paying attention to and using RISC-V.
2. A group of enthusiasts is actively participating in the construction of the RISC-V community. With strong support from NVIDIA and Shanghai Jiao Tong University, the 6th RISC-V workshop was held at Shanghai Jiao Tong University in May 2017, attracting nearly 300 participants. My team presented the Labeled RISC-V at this conference. Meanwhile, a group of RISC-V developers and enthusiasts have spontaneously formed domestic communities, with two active RISC-V WeChat groups gathering nearly a thousand enthusiasts. Guo Xiongfei from Jinglue Semiconductor, Song Wei from the University of Cambridge, and Huang Bowen from National Taiwan University have even launched a RISC-V biweekly newsletter⁸, collecting and organizing cutting-edge developments about RISC-V worldwide and translating them into Chinese to share with domestic RISC-V enthusiasts, with 12 issues already published.
3. Research institutions have begun conducting cutting-edge research based on RISC-V. Under the forward-looking suggestion of researcher Xu Zhiwei, the Institute of Computing Technology, Chinese Academy of Sciences, became one of the first five academic founding members when the RISC-V Foundation was established in 2015, alongside the University of California, Berkeley, MIT, ETH Zurich, and the Indian Institute of Technology, Madras. Currently, besides my team, there are also teams led by researcher Wang Yuantao and associate researcher Zhang Lei at the Institute of Computing Technology developing smart IoT chips based on RISC-V, achieving breakthroughs that were presented at the 7th RISC-V workshop. Some aerospace institutions have also long initiated pre-research projects based on RISC-V processors.
Although the number of companies and enthusiasts in China focusing on the RISC-V community is increasing, there is still significant room for improvement. On one hand, there are currently almost no contributors in the RISC-V open-source community from China, with most being users of RISC-V, lacking sufficient voice in the community and ecosystem development. On the other hand, the cutting-edge research based on RISC-V in the domestic academic community remains limited. My personal experience fully confirms that RISC-V is indeed a great platform for computer architecture research, likely to foster disruptive architectural innovations. In fact, many top universities worldwide have begun conducting architecture research based on RISC-V. Over the past seven RISC-V workshops, universities such as UC Berkeley, MIT, Princeton, Cornell, the University of Washington, the University of Cambridge, ETH Zurich, and the University of Texas at Austin have collectively published over 70 cutting-edge research works, while the academic community in mainland China has only produced five works (four from the Institute of Computing Technology, Chinese Academy of Sciences, and one from Shanghai Jiao Tong University).
Suggestions and Conclusion
The ambitious goals of the open instruction set RISC-V are admirable, and its growth story is quite inspiring. From the current development momentum, RISC-V is likely to become the de facto instruction set standard dominating the world, similar to Linux. Fortunately, it is open and free; however, regrettably, we currently have little voice in its development.
As more and more countries adopt RISC-V as the de facto national instruction set standard, a deeper question arises: Should China reconsider implementing a national instruction set standard? Should it be based on the open instruction set RISC-V, or should a new instruction set be designed? Here are my preliminary views on this issue:
First, as the world’s largest chip user, China has always hoped to strengthen its domestic chip industry. Various parties are making efforts, but differing approaches have led to the current state of “warlordism,” with the entire industry fragmented and severely dispersing foundational software development resources. This situation must be reversed to form a competitive chip industry internationally. Therefore, regarding the first question, the answer is affirmative—it is necessary to consider implementing a national instruction set standard.
Second, regarding which instruction set to choose, I believe there is no single answer; both basing it on RISC-V or redesigning a new instruction set are feasible. For the former, the RISC-V ecosystem has already been initially established, and we need to contribute more to the ecosystem to establish credibility and gain more voice. On the other hand, redesigning a new instruction set is also not unfeasible, as the open instruction set RISC-V provides us with two insights: (1) The instruction set can be separated from the specific design implementation of the chip. This forms the first feasibility condition—domestic chip manufacturers can adopt a unified, free open instruction set, but each manufacturer can have its own internal module implementations and apply for patents for protection. This way, a common software ecosystem can be built while maintaining independence among chip companies. Of course, there are some technical challenges that need to be studied in depth, such as how to implement different instruction sets with minimal microarchitecture changes (especially for privileged instructions). (2) If all parties have a common goal, promoting a completely new instruction set is not that difficult. In 2012, all parties in China believed that “designing a completely new instruction set from scratch is a daunting task,” but RISC-V grew from a summer project, which provides us with great encouragement and inspiration. The key is that all parties need to reach a consensus on goals, combined with the combination of measures taken by RISC-V and national policies, and I believe a new ecosystem based on a completely new instruction set can also be established.
The instruction set is fundamental to the entire information industry. Here, I hope to spark more attention and discussion among colleagues.
Author Introduction
Bao Yungang

Senior Member of CCF, CCF Council Member, Director of the Popularization Committee, Editorial Board Member of this journal
Researcher at the Institute of Computing Technology, Chinese Academy of Sciences
Research Direction: Computer Architecture and Computer System Performance Analysis

Footnotes
1 Thanks to Associate Professor Zhang Yu from the School of Computer Science and Technology, University of Science and Technology of China, for providing examples related to undergraduate education.
2 Tape-out refers to the process of manufacturing chips through a series of technological steps, similar to an assembly line. In the integrated circuit design field, tape-out refers to trial production, where a few chips are produced for testing after the circuit design is completed. If the tests pass, it is called a successful tape-out, and large-scale chip manufacturing can then proceed.
3 Krste Asanovic, Instruction Sets Want to be Free, 6th RISC-V Workshop, May 2017.
4 The four-person group consisted of Professors David Patterson and Krste Asanovic, along with PhD students Andrew Waterman and Yunsup Lee.
5 The second person from the right in Figure 4 is Professor Xu Wei from Tsinghua University, a student of Professor Patterson.
6 Martin Fink, RISC-V: Enabling a New Era of Open Data-Centric Computing Architectures, Keynote of 7th RISC-V Workshop, Nov. 2017.
7 The 1st Workshop on Computer Architecture Research using RISC-V. https://carrv.github.io/.
8 RISC-V Biweekly Newsletter, https://cnrv.io/.
China Computer Federation
WeChat ID: ccfvoice

Long press to recognize the QR code to follow us
CCF Recommendations
【Featured Articles】
-
YOCSEF 20th Anniversary Series Event—Latest Progress and Development Discussion of Domestic CPUs
Click “Read the original text”, to join CCF.