We welcome fintech professionals to actively submit articles!
Everyone is encouraged to express their opinions!
Submission email:
—— Financial Electronicization

Written by / China Everbright Bank Information Technology Department Comprehensive Intelligent Control Platform Project Team: Peng Xiao, Wang Gang, Li Anhuai, Dai Liang, Chen Yong
The data center is one of the core production sites of commercial banks, with high importance, and is also a personnel, equipment, and operation-intensive place, thus carrying inherent risks. On the other hand, conventional control methods are single, inefficient, and lack precision, leading to physical security control capabilities that cannot meet the needs of business development, with an expanding risk exposure and increasingly prominent operational security contradictions. Therefore, we urgently need to apply more advanced technologies to create a smarter control platform, enhance the efficiency and quality of physical access security, and achieve basic operation and maintenance with fewer or even no personnel.
Current Status and Goals of Physical Security Control in Data Centers
The data center is a personnel and equipment-intensive place, as well as a carrier of numerous operational activities. Strengthening the management of physical access security in data centers is one of the core tasks to ensure safe and stable operations. Due to limitations in technical means and basic conditions, the efficiency and quality of conventional physical security control are insufficient, and there is still a significant gap from refined management. This is specifically reflected in: poor comprehensive identification capabilities, such as the full identification of personnel identity, risk levels of operational personnel, and compliance of operational behaviors with baseline standards; weak real-time perception capabilities, such as the inability to perceive the entry of unauthorized personnel in real time, lingering in non-operational areas, and whether equipment is moved illegally; lack of effective control measures, with access control, video surveillance, and personnel accompaniment being common methods, slow response times, few and isolated disposal methods, poor execution effects, and high resource consumption; inability to trace back and audit, with behaviors not recorded, making it impossible to restore event scenarios, carry out post-evaluations, trace back and hold accountable, resulting in weak deterrence; overly simplistic security management methods that do not integrate with operational scenarios, unable to adapt and adjust based on different operational scenarios, leading to insufficient or excessive security.
To effectively manage physical access security, it is necessary to advance simultaneously from three dimensions: personnel, equipment, and operational behaviors. By enriching technical control means through processes, technologies, and platform construction; achieving system linkage through data interaction, digitizing offline behaviors; and introducing intelligent algorithms, enhancing the scientific nature of operational scheduling, achieving coordination between access security and operational scenarios, reaching the goals of precise identification, rich perception, timely control, and auditing, and realizing the integrated operation and maintenance concept of supervision and prevention in the field of physical security.
Overall Architecture and Functions of the Platform
Referring to the typical three-layer architecture of IoT systems: perception layer, network layer, and application layer, we designed the overall architecture of the comprehensive intelligent security control platform as shown below.
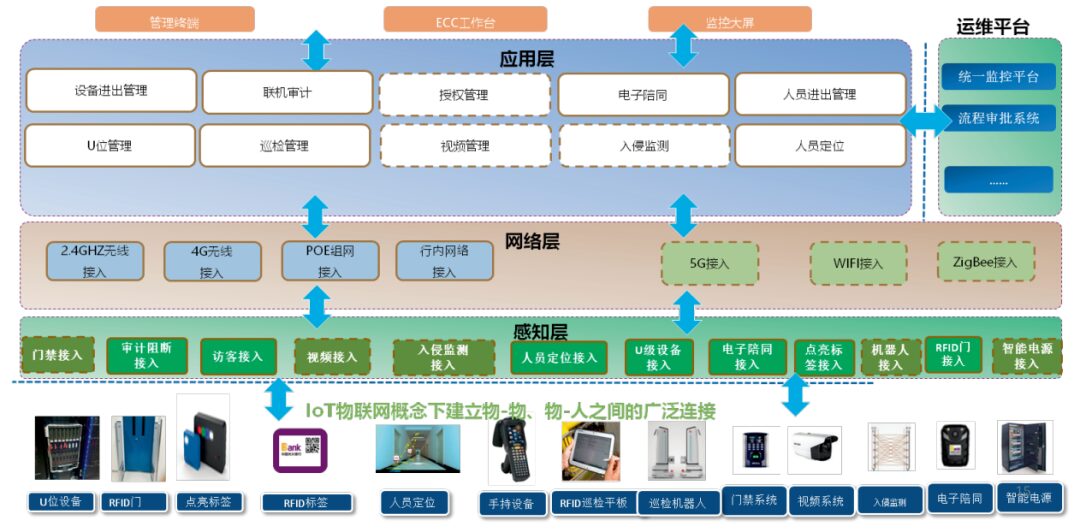
Figure: Overall Architecture of the Security Control Platform
The perception layer mainly consists of devices capable of sensing and identifying objects, emphasizing the “things” aspect of IoT. In this project, we extensively applied various IoT technologies, including identification technologies such as RFID and QR code recognition, sensor technologies such as temperature, humidity, heat, noise, and dust sensors, feature recognition technologies such as facial recognition, human-computer interaction technologies including OCR, TTS, and AR technologies, and location sensing technologies such as indoor positioning and SLAM. Moreover, we independently developed a wearable electronic accompaniment device, which combines personnel positioning for path guidance, real-time voice intercom, automatic warnings for abnormal behaviors, continuous operational recording, and remote operational guidance. Through the comprehensive application of various IoT technologies, we significantly enriched and enhanced the perception and control capabilities of operations within the data center, laying a solid technical foundation for refined control.
The network layer is primarily responsible for the communication function of sensing data and control information, transmitting the relevant data information obtained from the perception layer through various specific forms of networks, achieving functions such as information storage, analysis, processing, transmission, and management. In this project, we mainly applied 2.4GHz RFID networking, 4G wireless transmission networks, and reused the internal backbone transmission network, with potential future applications of 5G, Wifi, and NB-IOT network technologies.
The application layer mainly addresses information processing and human-computer interface issues. The primary business requirement of this platform is to refine operational activities according to scenarios across multiple data center spaces, apply automation more broadly, and achieve real-time linkage across systems through data and process-driven approaches, implementing refined control to enhance the efficiency and quality of physical security management.
Below, we introduce several typical scenarios: In personnel management, it is essential to accurately identify personnel identity and their risk levels. All internal and external personnel have their facial information collected, with full facial recognition for precise identity authentication, establishing a personnel security risk evaluation system, where the system automatically scores based on their operational behaviors and triggered alarm situations. High-risk personnel are directly blacklisted and are not allowed to operate on-site until they are unblocked. Through a positive feedback mechanism, everyone is guided to standardize operations. In permission management, static long-term authorizations are eliminated, and the comprehensive security control platform interfaces with the work order approval system, dynamically providing temporary authorizations based on production reasons by person, task, time, and area. After completion of the task, permissions are automatically revoked, significantly reducing the granularity of authorization. In operational behavior analysis, we promote the intelligent camera system, linking it with the internal biometric recognition platform to accurately identify VIP guests and blacklisted personnel, automatically analyzing behaviors such as intrusion, tailgating, and vandalism; deploying personnel positioning systems within the server room, setting electronic fences for operational areas, and real-time collecting personnel locations, generating alarms for boundary crossing or lingering in non-operational areas, with the platform automatically linking cameras for video monitoring. For remote operational guidance, we innovatively developed the “intelligent accompaniment device,” achieving intelligent navigation, remote intercom, automatic voice reminders, operational records, and video information feedback, enabling real-time understanding and remote guidance of maintenance operations. For equipment management, we use various RFID tags to establish equipment identity information, achieving full lifecycle management, real-time collecting the U-position information of equipment within cabinets, with RFID tags flashing automatically during maintenance to prevent incorrect plugging and unplugging; using intelligent inspection robots for continuous inspections to promptly detect equipment anomalies and abnormal conditions in the server room. In data processing and analysis, we digitize offline operational behaviors, employing big data analysis techniques to develop operational management models including personnel security risk evaluation, operational scheduling ranking, dynamic baselines for operational duration, and recommended accompaniment methods, providing technical means for proactively discovering and preventing anomalies, which in turn can guide and standardize operational behaviors. In business linkage, all underlying IoT terminal systems are connected with the comprehensive intelligent security control platform, driven by operational scenarios through data and business logic, achieving organic linkage of underlying systems, avoiding data silos, and ensuring efficiency in perception and disposal, such as linking work orders with access control and equipment RFID tags, linking access control with cameras, and linking personnel positioning with cameras and electronic accompaniment devices, allowing operational personnel in the ECC to observe the server room situation through video cameras at the first moment an alarm occurs and intervene through the accompaniment device.
Innovations and Application Promotion Effects of the Platform
In the field of physical access security in data centers, our comprehensive intelligent security control platform is relatively advanced in management concepts, architectural design, technical practices, and application promotion. Summarizing, it has the following innovative characteristics: taking operational scenarios as the entry point, driven by data and processes, achieving mutual linkage among multiple systems for collaborative operations, maximizing the effectiveness of technical means while ensuring that control strength matches and adapts to operational scenarios. Integrating various IoT technologies, establishing a unified framework for IoT technology applications, achieving unified collection, analysis, and control of personnel, equipment, and operational information. In the operational field, digitizing offline operations, employing big data analysis techniques, and developing a series of intelligent algorithms to improve the scientific level of security management. Comprehensive application of various technologies such as IoT, big data, and mobile internet, transitioning security control from “human defense” to “technical defense,” from personnel-intensive to advanced technology-intensive, achieving the “fewer” or even “无人化” development of data centers.
After more than two years of construction and promotion, the architecture of the comprehensive intelligent security control platform has become more complete, and its functions are basically complete, having achieved the access and management of key underlying systems such as access control, security cameras, visitor machines, personnel positioning systems, various RFID tags, and electronic accompaniment devices, realizing process integration with the internal process approval system, unified monitoring platform, etc., and has been comprehensively deployed in our production, disaster recovery, and development testing server rooms, achieving unified management standards, business processes, technical means, and basic data sharing for physical security control across multiple data centers. In the process of operation and maintenance, we continuously enrich application scenarios, improve control means, optimize operational models, and enhance actual effects. Through the platform’s proactive discovery and post-audit, we have also identified some violations, and through retrospective analysis and reporting of typical incidents, we help everyone enhance safety awareness, master operational norms, and clarify management requirements, improving the entire organization’s attention to physical access security, making the management system operate more smoothly, and preparing for future “fewer” personnel operations in server rooms in terms of technology and organization.
In the next steps, we will continue to promote from several aspects: first, continue to enrich the underlying perception and control systems, currently working on the construction and integration of inspection robots and intrusion detection systems. Second, continue to enrich the operational scenarios of the platform control, setting targeted control standards and processes based on different scenarios to drive organic linkage of perception and control layers for refined control. Third, increase analysis and application of basic data, designing more targeted sub-models to guide and standardize operational behaviors. Fourth, strengthen guidance and publicity, analyzing and holding accountable for typical violations, forming a complete closed-loop operational system, maintaining deterrence.
(Click to view exciting content)
● Case | Construction Practice of Information Security Operation Center
● Case | Distributed Database Application Practice of Taizhou Bank
● Case | The Safe and Controllable Path of Ganzhou Bank
● Case | Exploration and Practice of Distributed Architecture in Small and Medium Banks
● Case | New Infrastructure Promotes Insurance Cloud to New Heights
Statement Regarding Impersonation Charges
Since its inception, our publication has never charged any fees from contributors. Any act of charging contributors under the guise of publishing articles is fraudulent.
The official website of our publication is www.fcmag.com.cn.
The submission email of our publication is [email protected].
We will pursue legal responsibility for illegal acts impersonating our website and pages to protect the legitimate rights and interests of our publication and contributors. Report phone number for impersonating websites and pages: 010-88232443
The New Media Department of “Financial Electronicization”: Director / Kuang Yuan Editor / Pan Jing Fu Tiantian
