↑ Click on the above
“Smart Manufacturing Home”
Follow us
Members can enter theMember Download Areato obtainrelated materials~
Introduction
Previously, we shared the main industrial control protocols and their ports from industrial giants such as Siemens, Schneider, Mitsubishi, and Rockwell:
Siemens, Schneider, Mitsubishi, RA: Analysis of Major Global Industrial Control Protocols and Ports
We have also created many original articles related to industrial protocols and communications:
Technical Interpretation of PROFINET, Ethernet/IP, and Other 7 Mainstream Industrial Ethernet Protocols
The most comprehensive compilation of various buses + protocols + standards + interfaces in the field of industrial communications—data acquisition and control
The most detailed summary and interpretation of industrial network communication technologies and protocols (fieldbus, industrial Ethernet, industrial wireless)
In the current context of deep integration of IT and OT, various protocols play a crucial role on both the OT and IT sides, such as the interpretation and password cracking of various industrial control protocols mentioned earlier:
Siemens, Schneider, Rockwell: The Journey of Breaking PLC Password Protection of Three Major Industrial Control Manufacturers
S7-1200+SCADA: Detailed Explanation of Siemens S7 Protocol and Data Read/Write
TIAV17+S7-1200: Analysis of the Latest Siemens S7CommPlus Protocol
Today, we will discuss how industrial control systems and industrial networks are attacked by hackers.
 Application Areas of Industrial Control Systems01 Overall Attack Strategies on Industrial Control Systems
Application Areas of Industrial Control Systems01 Overall Attack Strategies on Industrial Control Systems
Attack Objectives
Highly targeted and purposeful attacks typically aim to damage industrial control devices, cause factory shutdowns, disrupt processes, increase defect rates, and even lead to severe consequences such as fires and explosions. In modern factories, most on-site production equipment is operated by control systems (e.g., PLC – Programmable Logic Controller, CNC lathes, DCS – Distributed Control System). Therefore, attackers aim to achieve their goals by directly or indirectly attacking or influencing the control systems. The following will use factory PLCs as examples to illustrate hackers’ attack strategies on industrial control systems.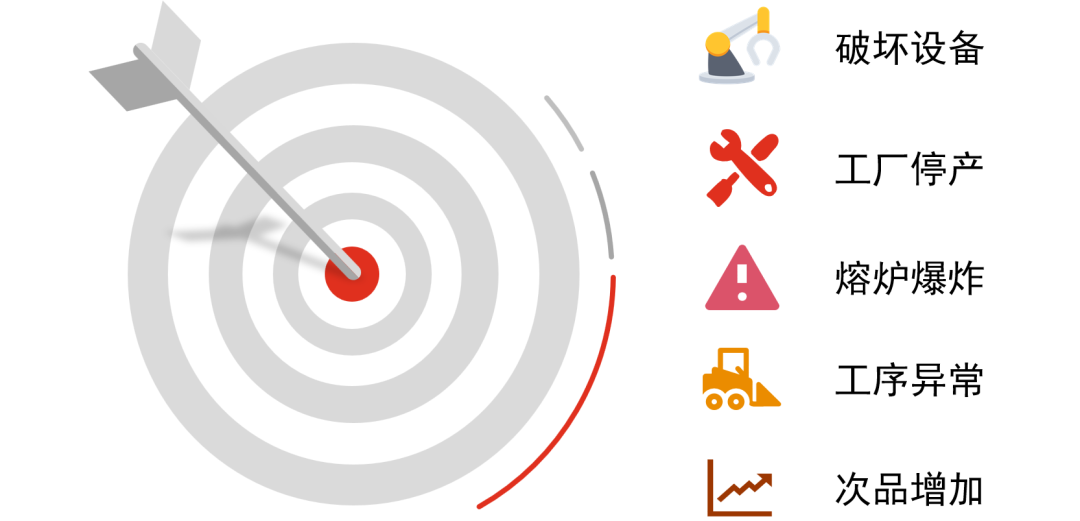 Examples of Hacker Attack Targets
Examples of Hacker Attack Targets
Attack Scenarios
Targeted Direct Attacks
Directly attacking a PLC refers to exploiting vulnerabilities in the PLC or bypassing security authentication through password cracking methods to successfully control the PLC and modify instructions to achieve attack objectives. Currently, many PLCs are located on internal networks and cannot be accessed directly via the internet. In this scenario, direct attacks are generally achieved through physical contact with the PLC or by connecting to the PLC via the internal office network. As factories become more intelligent and devices become interconnected, many PLC systems connected to the internet will make it easier for hackers to launch direct attacks on PLCs.
Targeted Indirect Attacks
Indirectly attacking a PLC involves gaining control of the monitoring system above the PLC (such as HMI, IPC, SCADA, etc.) and sending malicious instructions to the PLC through the monitoring system or interfering with the normal communication between the monitoring system and the PLC to achieve attack objectives. Indirect attack scenarios usually occur when attackers cannot directly access the control systems or have limited knowledge of the factory’s internal PLC systems, thus turning to attack IT components and monitoring layer systems that are more familiar to many attackers. For example, an attacker first gains control of an IPC (Industrial Computer), analyzes the transmission patterns between the IPC and PLC, constructs malicious instructions, and transmits them to the PLC via the IPC, indirectly affecting the normal operation of the PLC or disrupting the monitoring and early warning of production status.
Non-targeted Attacks
Non-targeted attacks, also known as scattergun attacks, refer to malicious programs exploiting common vulnerabilities in systems or networks, indiscriminately infecting systems and spreading within the internal network, affecting normal production order. Although such attack scenarios do not target industrial control systems, the current weak security measures in industrial control environments have allowed scattergun attacks to succeed worldwide. Scattergun attacks typically involve viruses or malicious programs; for example, attackers exploit employees’ weak security awareness by sending phishing emails, infecting the recipient’s computer, and then rapidly spreading through the office network due to the network’s vulnerabilities, eventually reaching the production network and infecting systems with common vulnerabilities, such as IPCs, affecting production or causing damage.
Attack Vectors
Attack vectors for industrial control systems generally include internal and external initiations. Internal initiation can be further divided into penetration from the office network to the factory network and attacks initiated on-site in the workshop; external initiation includes targeted attacks (such as APT) and scattergun attacks.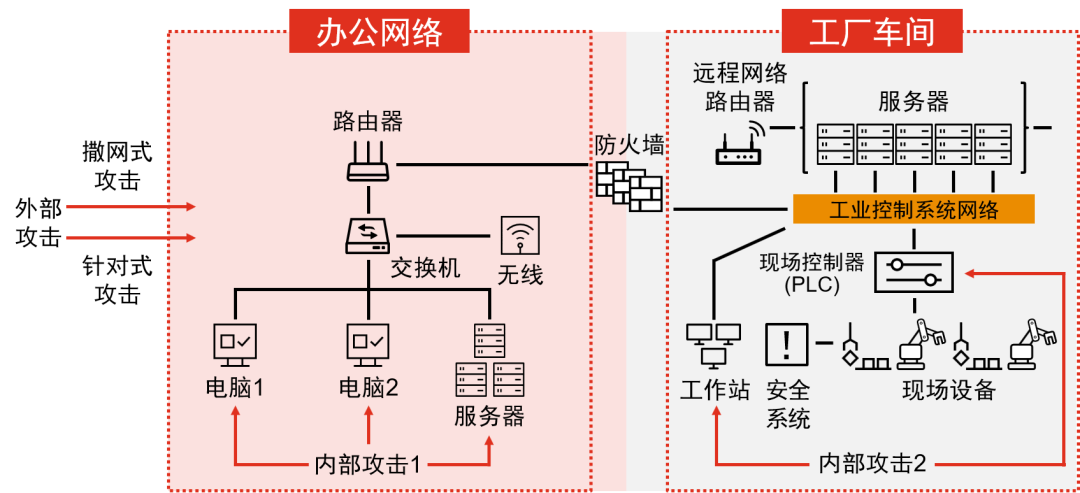 Attack Pathways in Industrial Control Environments
Attack Pathways in Industrial Control Environments
Internal Initiation
Starting from the Office Network
-
Within the office network environment, use tools like nmap to scan and obtain subnet and asset information, especially the ports of conventional industrial control systems and IT systems, such as Siemens 102, Modbus 502, EthernetIP 44818, 445, 3389, etc.;
-
Exploit vulnerabilities in the identified systems, including sniffing, privilege bypass or escalation, replay attacks, password guessing, command injection, EternalBlue vulnerability exploitation, and password guessing;
-
After successfully gaining control of the system, attempt to use that host as a springboard to penetrate other systems using methods like Pass the Hash, looking for industrial control-related systems such as PLCs, IPCs, and SCADAs to achieve attack objectives;
-
If unsuccessful, turn to social engineering methods to further obtain relevant information (such as high-privilege accounts, etc.);
-
At the same time, consider ways to enter the factory workshop for on-site attack methods;
-
Some integrated control systems’ central control platforms or web applications of SCADA-like configuration control systems in the internal network may be easily hijacked to elevate privileges to engineer stations.
Starting from the Workshop
Launching attacks on industrial control systems from within the workshop is the most direct method, with diverse means and choices:
-
Upon entering the workshop, carefully observe the situation to locate IPCs or control systems, preparing for subsequent attack attempts.
Attack Attempt One:
-
The primary target is the control system (e.g., PLC), looking for devices that are unlocked or have exposed network interfaces;
-
Attempt to understand basic information about the control system, such as the brand and version used;
-
Try to connect to the control system on-site using a computer, exploiting weak passwords and other vulnerabilities to attempt malicious instruction injection, privilege bypass, replay attacks, etc.
Attack Attempt Two:
-
Attempt to attack the IPC or HMI running on-site, for example, by inserting a malicious USB drive into the running IPC to implant malicious programs;
-
Directly operate on IPCs or HMIs without set permissions, such as modifying control system instructions for malicious operations.
External Initiation
Targeted Attacks
APT attacks are typical externally initiated targeted attacks, and the attack process includes
-
Collecting information about the target enterprise to initially understand its basic situation;
-
Using search engines like Google and Baidu to find exposed domain names or servers on the internet;
-
Using crawling techniques to obtain all links, subdomains, and C-segments of the website as much as possible;
-
Attempting to exploit high-risk vulnerabilities in web applications, such as malicious file uploads, command execution, SQL injection, cross-site scripting, and account privilege escalation;
-
Attempting to obtain a web shell on the website and then escalate to server privileges;
-
Using that server as a springboard to penetrate the internal network, transitioning to an internal attack mode;
-
Searching for external email usernames from the internet, and sending phishing emails targeted at these users based on the characteristics of the enterprise, using the compromised computer as a springboard to penetrate the internal environment, transitioning to an internal attack mode;
-
Using forged access cards or disguising as visitors or interviewees, or tailgating internal employees to physically enter the enterprise, transitioning to an internal attack mode.
Scattergun Attacks
- Using search engines like Google and Baidu to find exposed domain names of enterprises on the internet, and if exploitable vulnerabilities are found, transitioning to targeted attacks;
- Using social engineering to collect as many employee emails as possible and sending bulk phishing emails;
- Using the Shodan search engine to launch attacks on exposed industrial control systems on the internet, transitioning to internal attacks upon success.
Cyber Kill Chain

Generally, attackers usually start their attempts with low-cost scattergun attack methods, such as sending phishing emails. When the victim clicks on the malicious link or program attached to the phishing email, the “Pandora’s Box” is opened, and the attacker will attempt to compromise the victim’s device and use it as a springboard to penetrate the enterprise’s internal network. If the industrial control network fails to effectively isolate from the office network, attackers can scan and analyze relevant industrial control assets after entering the office network. Currently, many industrial control environments in factories have weak defenses against network attacks, often having weak passwords, improper permission settings, shared accounts and passwords, lack of patch and vulnerability management, and insufficient network isolation and protection, leading to high-risk vulnerabilities that attackers can exploit to conduct widespread, unimpeded attacks on industrial control assets within the enterprise’s industrial control network, ultimately resulting in industrial data leaks, equipment damage, process abnormalities, increased defect rates, fires and explosions, and even threats to employee safety, forming a complete hacker attack chain.
02 Can Industrial Control Systems Effectively Resist Attacks?
The ability of industrial control systems to effectively repel hacker attacks depends on the preparations and measures taken by both attackers and defenders. Currently, attackers are more actively researching vulnerabilities and attack methods of industrial control systems, while enterprises are focusing more on efficient production and digital transformation, with relatively lagging attention and investment in industrial control security; coupled with the obsolescence and non-standardization of industrial control systems, there are many vulnerabilities exposed to attackers, as illustrated below:

Organization and Personnel
Unclear Security Responsibilities
Insufficient attention from management, unclear security responsibilities between departments, and no clear security department or position.
Weak Security Awareness
Employees have relatively weak security awareness regarding industrial control systems, especially production or frontline employees. Traditional enterprises often rely on “security by obscurity,” believing that strict physical security and access management can ensure safety, and that the absence of security incidents indicates safety, which often leads enterprises to neglect network security construction and fail to remedy hidden dangers in a timely manner.
Management and Supervision
“Experience-based” Management
Many enterprises lack security design and considerations for industrial control systems, which is a common phenomenon. Appropriate security measures can effectively compensate for this, but many enterprises have not established effective security policies and measures, relying solely on personal experience and historical practices for management.
Absence of Emergency Response Mechanisms
Lack of emergency response mechanisms, making it impossible to quickly organize personnel and deploy response measures to control the further spread of incidents and resolve issues and restore production in the shortest time possible.
Lack of Proper Password Policies
Failure to set appropriate password policies and management, such as weak passwords, shared passwords, multiple hosts or devices sharing a single password, and sharing passwords with third-party suppliers, increasing the risk of password leakage.
Lack of Security Audit Logs
After a security incident occurs, it is impossible to trace and analyze the source and cause of the incident to prevent similar situations from happening again.
Network and Architecture
“Gentleman-style” Network Isolation
Lack of effective isolation between internal office networks and factory networks, without dividing security domains for protection, leading to attacks or viruses from the office network spreading to the factory network, causing production impacts.
Unsafe Communication Protocols
Industrial control protocols are non-standardized and mostly have security vulnerabilities, such as CAN, DNP3.0, Modbus, IEC60870-5-101.
Unsafe Remote Access
To facilitate remote debugging by maintenance engineers and suppliers, security measures and monitoring for remote access have not been deployed, making such remote access functions one of the most exploited vulnerabilities by attackers.
Complex Structures
The structure of industrial control systems is more complex compared to IT environments, with more attack surfaces. A typical industrial control environment generally consists of the following components: controllers (PLC, CNC lathes, DCS), SCADA systems, industrial computers, industrial software, HMI, networks, switches, routers, industrial databases, etc. Any issue or problem in any link or component can lead to the entire industrial control system being attacked.
Hosts and Devices
Authentication and Authorization
For convenience in daily use, important control systems have not set passwords, set weak passwords, or shared passwords, and passwords are posted on-site, making these “conveniences” greatly facilitate attackers’ intrusions.
Antivirus Software
Failure to install antivirus protection software, not updating virus databases in a timely manner, and using unlicensed software.
Obsolescence of Operating Systems
In today’s factory environments, an increasing number of computer systems are used; however, the update and iteration cycle of industrial control systems is much longer than that of IT systems, resulting in many outdated computer systems in industrial control systems, such as Windows XP, Windows 2003, etc., which have numerous high-risk vulnerabilities that can be exploited.
Default Configurations
Many factories use default passwords, default paths, and enable unnecessary and unsafe ports and services during equipment installation.
Offline Device Management
For offline devices, it is often assumed to be safe, neglecting network security protection measures. However, as enterprises advance in digitalization or require network connections for business needs, such devices may become weak points and gaps in the security system.
Physical Protection
Hardware Debugging Interfaces
Racks of important control systems are not locked, or exposed debugging interfaces are not effectively protected.
Physical Ports
Failure to effectively manage or disable common interfaces such as USB, PS/2, etc., may pose risks of unauthorized device access, leading to virus infections or unauthorized program modifications.
Access by External Personnel
Poor control over personnel entering and exiting the workshop, especially external personnel, such as suppliers.
The vulnerabilities summarized above that can be exploited by attackers should be of concern to enterprises based on their business characteristics. In the short term, certain compensatory measures should be taken for high-risk vulnerabilities, and in the long term, a security management system for industrial control should be gradually established in line with business and digital development plans.

Smart Manufacturing Project – Complete Plan for Digital Factory Planning and Construction
2022-01-15

Complete Reference of China’s Smart Manufacturing Industry Map and Typical Scenarios | Industry Chain Panorama
2022-01-10
87 Pages of Classic Smart Manufacturing Methodology, Overall Solutions, and Practical Sharing
2022-01-05
81 Pages of Hardcore Advanced Industrial Network Technologies and Practices
2022-01-04

Siemens, Dassault, SAP, Central Control…: 2021 Industrial Software Panorama Research (81 Pages Download)
2021-12-25

166 Pages PPT to Understand the Basics of Smart Manufacturing Digitalization!
2021-12-06
193 Pages of Comprehensive Notes Analyzing the “Digital Transformation Methodology” PPT
2021-11-27

Complete Sorting of Smart Manufacturing + Industrial Internet Industry Chain! (2 Excellent PPTs)
2021-11-24
When PLC Meets “IT”: Detailed Explanation of 5 Ways MES and PLC Interact
2021-11-22
114 Pages of Digital Factory Planning, Construction, and Technical Practices
2021-11-15
