One
Introduction
Often, programs run without an operating system, which is known as bare-metal operation and cannot run directly in Linux. Therefore, alternative methods must be used for analysis. Taking a CTF problem as an example, we will learn about analyzing bare-metal programs on the ARM architecture.
Two
Analysis
Program address:
https://dn.jarvisoj.com/challengefiles/confusedARM.hex.f4e616545ff1a18526b9d1c90ea648ff
This program is for the STM32F103X8, so the corresponding dataset can be found on this website: https://www.alldatasheet.com/.
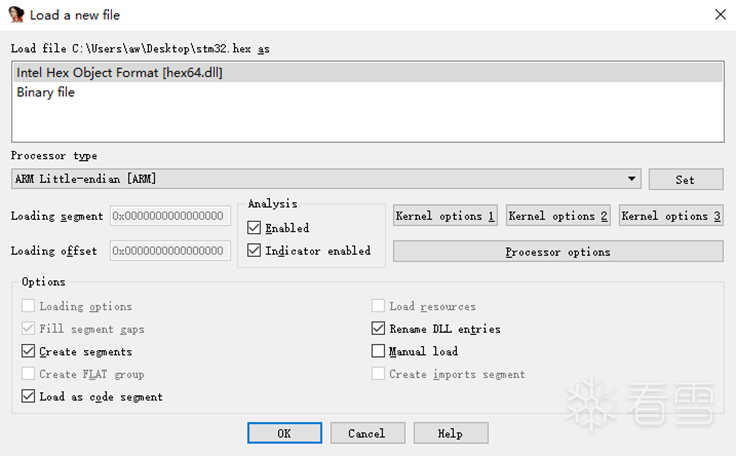
Open the program with IDA and set it to ARM little-endian:
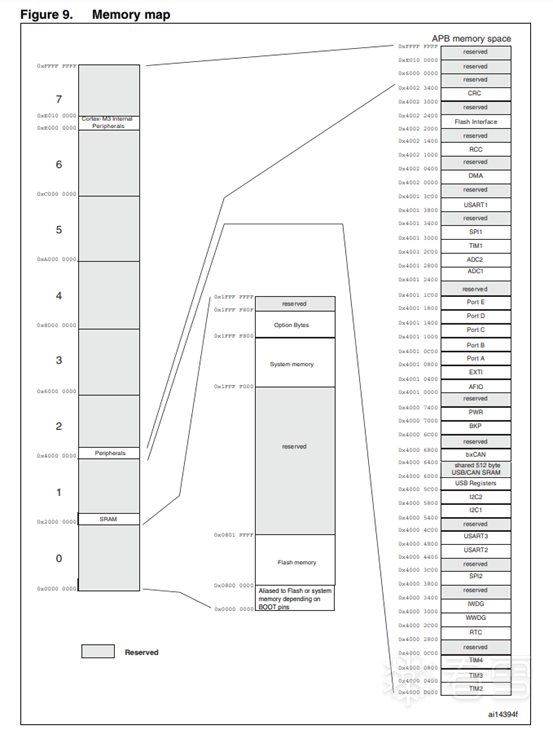
The memory mapping in the dataset is shown in the following image:
After opening, the initial data is as shown below:
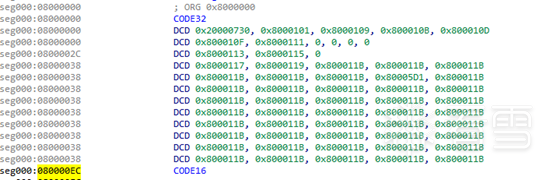
It can be seen that this data is not recognized as code. The first address 0x20000730 is known to be in the SRAM area according to the above memory mapping, followed by 0x8000101, which is located in the Flash memory area below the SRAM. The detailed memory mapping at the bottom of the memory mapping diagram is shown below:
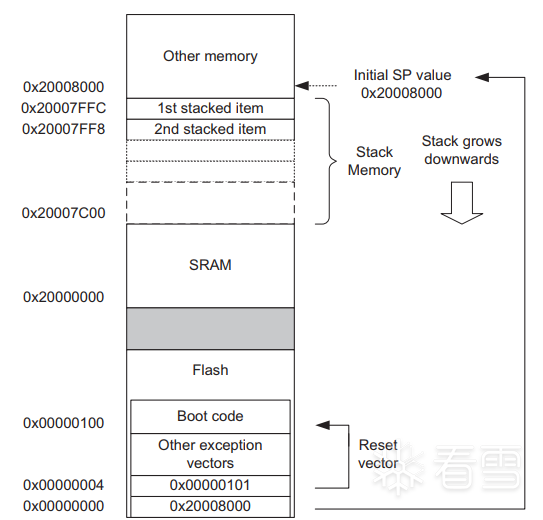
It can be seen that the Reset is at 0x00000004, pointing to 0x00000101, and the STM32 supports remapping, which maps the content starting from 0x08000000 to the base address 0x00000000. Checking the content of these two memory locations:
0x00000000:

0x08000000:

It can be seen that the contents of these two memory locations are the same.
This means that the second data point seen in IDA, 0x8000101, is the address executed by the reset, i.e., the reset address. At 0x8000101:
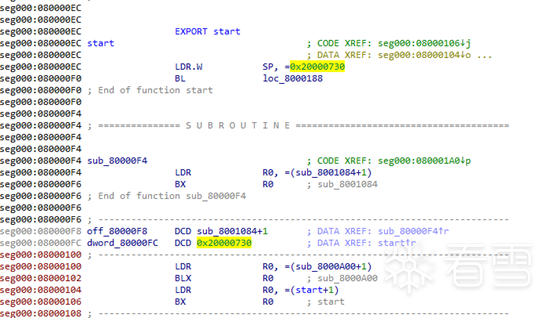
At the instruction at 0x8000104, there is a start, which is the stack pointer, meaning that 0x20000730 is the stack address, and 0x08000100 can basically be confirmed as the program’s entry address. At 0x080000f6, there is a significant jump that calls the function sub_8001084. Let’s take a look at sub_8001084:
The pseudocode is shown in the image below:
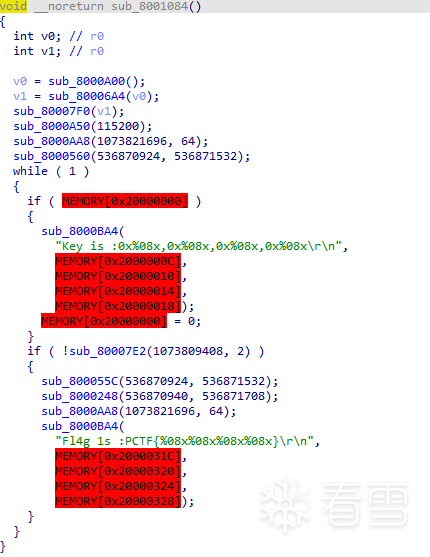
It can be seen that certain conditions must be met to output the flag. However, the red memory areas do not look good; you can create a segment by going to Edit -> Segments -> Create Segment to include these memory areas. Therefore, the function sub_8001084 is the main function.
Next, use MDK to dynamically debug the program. Before starting, download the corresponding package (https://www.keil.arm.com/packs/), create the project, and modify the configuration:
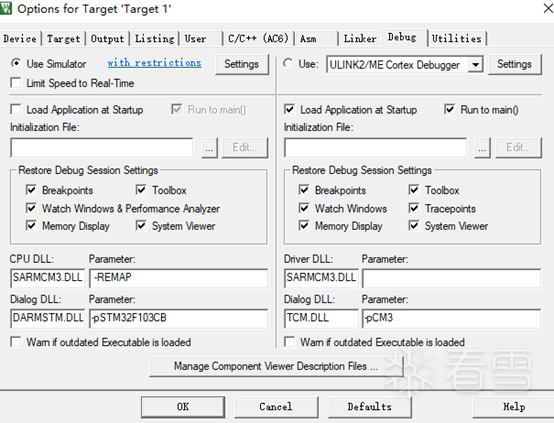
Press CTRL+F5 to start debugging, then load the source file in the command window below:
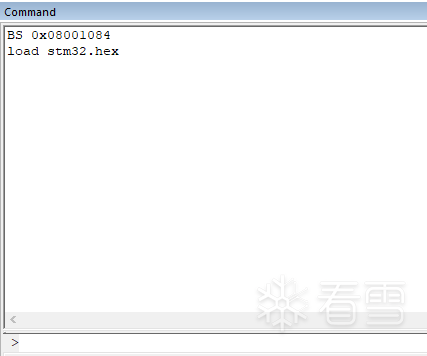
Then click the RST button in the upper left corner:

The program will automatically jump to 0x08000000 and break:
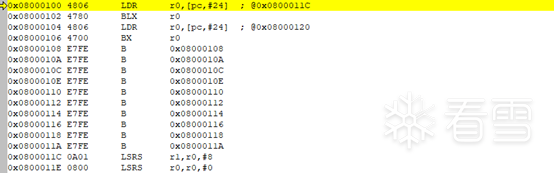
From the above, we know that the function entry point is at 0x08000000, and the main function is at 0x08001084. Directly run to 0x08001084:
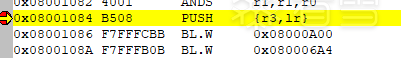
According to the pseudocode in the main function, the address of the encryption function’s key is: 0x2000000C, and the address of the decrypted flag is: 0x2000031C. In the main function, both sub_8000560 and sub_800055C operate on the key, so these two cannot be the decryption functions, leaving only sub_8000248 as a candidate.
So it seems that directly running the program should output the flag:
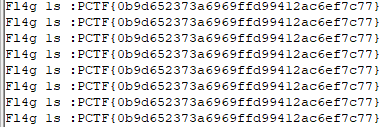
However, submitting the flag is incorrect.
It seems that the decryption function must be the problem. Running to address 0x080010EA where sub_8000248 is called:
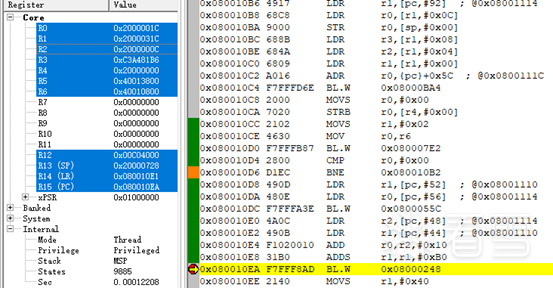
Based on the analysis of the function parameters above, the third parameter of sub_8000248 should be the decryption key. From the debugging, the address of the key passed to sub_8000248 is 0x2000000C, but before calling sub_8000248, the sub_800055C function processed the key. This means the key was passed incorrectly; it should be 0x2000026c instead. Therefore, modify the value of the R2 register in MDK to 0x2000026c:
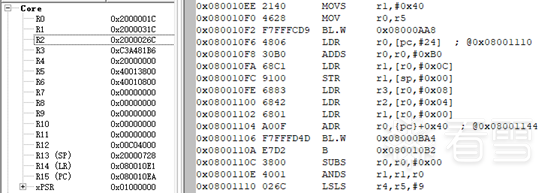
Then run, as this is a temporary modification, only the first flag is correctly output:

Of course, you could also directly patch the program by modifying the code in the program.
Three
Conclusion
First, we examined the dataset corresponding to the ARM architecture’s STM32 program to understand its memory mapping and used IDA for static analysis to find the entry point and main function. Then we used MDK for dynamic analysis to debug and identify the issues with its decryption algorithm, modifying it to achieve the correct results.
Reference Article
https://www.armbbs.cn/forum.php?mod=viewthread&tid=109321

Kanxue ID: mangovo
https://bbs.kanxue.com/user-home-979084.htm

# Previous Recommendations
1、Setting Up LLVM Environment on Windows
2、In-depth Study of Smali Syntax
3、Android Hardening and Unpacking Sharing
4、Initial Exploration of Flutter Reverse Engineering
5、A Simple Practice to Understand Stack Space Transfer
6、Record of Unpacking and Repairing a Certain Shield Mobile Game Hardening