Abstract:The random access process, as an important procedure for achieving UE initial access and uplink synchronization, has been simplified and modified in NB-IoT based on the LTE system. By comparing with the random access process in the LTE system, an in-depth analysis of the currently supported contention-based random access process in NB-IoT is conducted, and a consistency testing platform based on TTCN-3 is established to verify the consistency of the random access process with the standards.
Chinese Citation Format: Chen Fatang, Zhou Shuqi, Zheng Hui. Analysis and implementation of NB-IoT random access process[J]. Application of Electronic Technique, 2018, 44(2): 75-79, 87.English Citation Format: Chen Fatang, Zhou Shuqi, Zheng Hui. Analysis and implementation of NB-IoT random access process[J]. Application of Electronic Technique, 2018, 44(2): 75-79, 87.
With the rapid development of Internet of Things communication technology, the rise of Low Power Wide Area (LPWA) technology has been spurred. LPWA technology mainly targets low power, wide coverage, long distance, and low bandwidth IoT services, with various types, among which representative technologies mainly include LoRa (Long Range), Sigfox based on unlicensed spectrum, and Narrow Band Internet of Things (NB-IoT) based on licensed spectrum.[1-3]
NB-IoT is a LPWA cellular solution introduced by 3GPP (3rd Generation Partnership Project) to support ultra-low complexity and low throughput IoT applications, featuring low cost, low power consumption, large connections, and wide coverage.[4-8] As an emerging wireless access technology in the cellular system, NB-IoT has made corresponding simplifications to the sub-layers of the protocol stack and key technical processes to meet the demands for delay-insensitive services with no minimum rate requirements, large transmission intervals, and low transmission frequencies, including the random access process used for achieving initial access to the network and uplink synchronization of User Equipment (UE). In the NB-IoT system, the purpose of using random access is similar to that in LTE, used for initial access and uplink synchronization when UE establishes a wireless link. However, due to the service demands targeted by NB-IoT, the initiation frequency of the random access process is very low. Therefore, it is necessary to design an access process scheme that supports its service needs for NB-IoT.
In NB-IoT, similar to LTE, UE performs the random access process in both idle and connected modes, but NB-IoT in R13 (Release 13) only supports contention-based random access and random access triggered by PDCCH order when downlink data arrives.[11] In addition, it does not support PUCCH channels and handover functions, so the related application scenarios that trigger random access in the NB-IoT system have been simplified to the following four:[12-13] (1) Initial access process in Radio Resource Control (RRC) idle state; (2) RRC connection re-establishment process; (3) In RRC connected state, when receiving downlink data (uplink out of sync); (4) In RRC connected state, when sending uplink data (uplink out of sync or triggering scheduling request).
Among the above application scenarios, only the first scenario is a random access process in idle mode, while the remaining three scenarios are random access processes in connected mode, and the random access triggered in all four scenarios is contention-based.
The contention-based random access process in NB-IoT is similar to that in LTE, consisting of four steps:[14-15] (1) UE sends random access preamble (Message 1); (2) UE receives random access response sent by the network (Message 2); (3) UE sends Msg3 (Message 3); (4) Contention resolution (Message 4). However, to support the characteristics of NB-IoT, each step of the random access process has been optimized accordingly, and the following will provide a detailed analysis of each step of the optimized random access process for NB-IoT.
2.1 Selection and Transmission of Random Access PRACH Resources and Preambles
In the NB-IoT system, before UE sends the random access preamble, it must first determine the PRACH resources. The selection of PRACH resources can be divided into two types: one is PRACH resources explicitly indicated by the eNB; the other is PRACH resources selected by the UE. Unlike LTE, the PRACH resources selected by the UE are based on their corresponding coverage levels, where NB-IoT defines three coverage levels: level 0, level 1, level 2, each with corresponding PRACH resource configuration parameters, which are delivered to the UE through system information blocks in SIB2-NB and provided in nprach-ParametersList, mainly including:[16] PRACH repetition times (determined by the parameter numRepetitionsPerPreambleAttempt), PRACH time-domain resources (including periodicity: nprach-Periodicity, starting subframe position: nprach-StartTime, etc.), and PRACH frequency-domain resources (including subcarrier offset: nprach-SubcarrierOffset, number of subcarriers: nprach-NumSubcarriers, etc.), as well as two parameters for preamble repeated transmission: maximum number of preamble attempts (maxNumPreambleAttemptCE) and maximum attempts for each preamble (numRepetitionsPerPreamblePreambleAttempt), while the coverage level of the UE is determined based on downlink measurements (e.g., Reference Signal Received Power (RSRP)) and its threshold parameters.
After determining the PRACH resources, the random access preamble is selected, and the selection of the preamble, like the determination of PRACH resources, can also be divided into eNB explicit indication and UE selection. The preamble explicitly indicated by the eNB differs from LTE; since NB-IoT currently does not support non-contention-based random access in R13, the preamble will only be explicitly indicated when random access is triggered by PDCCH order in the scenario mentioned in scenario 3. If the preamble is indicated by the eNB, the UE sets the preamble according to the subcarrier index specified by the eNB in the PDCCH order (ra-PreambleIndex) and the PRACH resources specified by the eNB for the current coverage level. That is, the preamble is set as nprach-SubcarrierOffset + (ra-PreambleIndex modulo nprach-NumSubcarriers), where nprach-SubcarrierOffset and nprach-NumSubcarriers are parameters of the PRACH resources specified by the eNB for the current coverage level. The preamble selected by the UE is also different from LTE; in the random access preamble sequence of NB-IoT, there is no distinction between Group A and Group B, and Zadoff-Chu sequences are not needed for generation. Instead, it consists of 5 symbols and contains 4 symbol groups made up of 5 symbols, with all symbol groups configured using a default all-1 method. Therefore, the preamble is first selected from the symbol groups and then from the selected symbol group, and the selected preamble will be a sequence of 1’s. The specific process of selecting random access resources is shown in Figure 1.
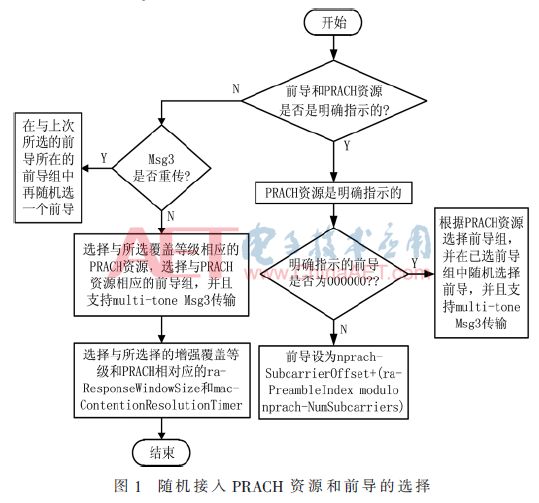
The process of selecting random access PRACH resources and preambles shown in Figure 1 differs from LTE. The Multi-tone shown in the figure is a transmission method for transmitting Msg3 (Message 3) during the random process. In the uplink of NB-IoT, it can be divided into two transmission methods: Single-tone and Multi-tone. However, in early NB-IoT field trials and deployments, some UE implementations may not support Multi-tone. Before scheduling uplink transmission, the eNB should know whether the NB-IoT UE supports Multi-tone transmission. Therefore, the UE should notify the eNB of its support for Multi-tone by sending the subcarrier index occupied by the preamble in random access Message 1, to facilitate network scheduling of uplink transmission in Msg3. To this end, a parameter nprach-SubcarrierMSG3-RangeStart is introduced in the frequency domain resources of PRACH, with parameter values of 0, 1/3, 2/3, 1. Through the formula: nprach-Subcarrier-Offset + (nprach-SubcarrierMSG3-RangeStart·nprachNum-Subcarriers), the NPRACH subcarriers in the frequency domain can be divided into two non-overlapping sets, allowing the UE to choose one set from which to send its random access preamble. However, in R13 NB-IoT, the UE typically always uses the Single-tone method to transmit the preamble, meaning the value of the nprach-SubcarrierMSG3-RangeStart parameter is always 1, indicating that Multi-tone is not supported when transmitting Msg3.
After the NB-IoT UE selects the PRACH resources and preamble, it needs to set the target preamble transmission power (PREAMBLE_RECEIVED_TARGET_POWER), which is also different from LTE. First, the target preamble transmission power value for LTE is derived from the formula used to calculate the target preamble transmission power for LTE, where DELTA_PREAMBLE takes the value of 0 for NB-IoT UE. Then, it is set based on the different coverage levels of the UE. When the coverage level is 0, the target preamble transmission power is set to: PREAMBLE_RECEIVED_TARGET_POWER – 10*log10(numRepetitionPerPreambleAtte-mpt), while for coverage levels 1 and 2, PREAMBLE_RECEIVED_TARGET_POWER is set to the corresponding maximum UE output power. After setting PREAMBLE_RECEIVED_TARGET_POWER, the preamble is transmitted using the selected PRACH resources corresponding to the coverage level, the corresponding RA-RATI, the preamble index or NB-IoT subcarrier index, and PREAMBLE_RECEIVED_TARGET_POWER with the required number of repetitions for the selected preamble group.
2.2 Random Access Response
Similarly, in NB-IoT, once the random access preamble is sent out, regardless of whether measurement gaps may occur, the MAC entity in the UE will monitor the PDCCH for the Random Access Response (RAR) identified by the random access radio network temporary identifier (RA-RNTI) defined by formula (1) during the RAR window opened for receiving the random access response. Due to the specific uplink transmission scheme in NB-IoT, to support the feature of repeated transmission, the position of the RAR window will differ from LTE, as it is related to the NPRACH repetition count, divided into two cases:
(1) When the NPRACH repetition count is greater than or equal to 64, the RAR window should be opened 41 subframes after the end of the last preamble repetition transmission, as shown in Figure 2.
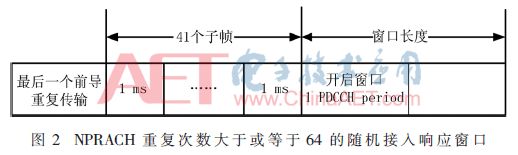
(2) When the NPRACH repetition count is less than 64, the RAR window should be opened 4 subframes after the end of the last preamble repetition transmission, as shown in Figure 3.
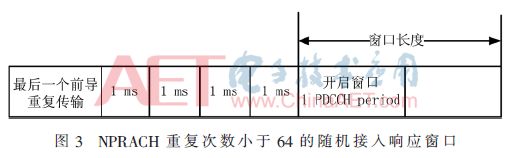
In NB-IoT, the length of the RAR window in Figures 2 and 3 has also been extended; it does not adopt the 10 ms RAR window in LTE but uses the PDCCH period (PDCCH period, PP) as the length unit of the RAR window, with unchanged values. The minimum definition of the RAR window remains 2 (this article sets the window to 2 PPs), and the maximum is set to 10. At the same time, a new RA-RNTI is defined with the following formula:
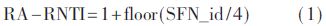
Where SFN_id is the index of the first radio frame of the specified PRACH, which corresponds to the index of the first radio frame for the preamble sent. In NB-IoT, the composition parameters of the MAC PDU received in the random access response are the same as those in LTE. However, it should be noted that for NB-IoT UE to meet its service needs, the backoff parameter value corresponding to the backoff identifier (BI) in the PDU composition parameters has been significantly increased, with a maximum value of 524,288 ms, which is the delay time for repeated transmission of the preamble. Since the UE uses the same preamble, and each subcarrier of the random access preamble group corresponds to a random access preamble, the random access preamble identifier (RAPID) used to determine whether the random access is successful only needs to correspond to the starting subcarrier index of the preamble. When the RAPID is consistent with the starting subcarrier index, it is considered that the random access response has been successfully received, and monitoring of the PDCCH is stopped. The reception process of the random access response is shown in Figure 4.
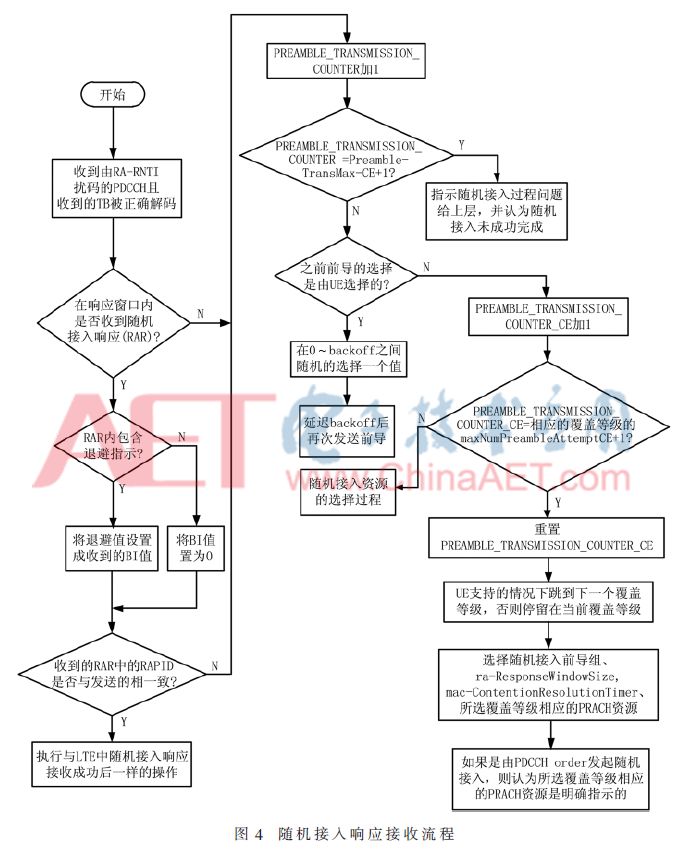
As shown in Figure 4, when the received RAPID does not match the sent one or when no RAR is received within the RAR window, the UE will perform preamble repeated transmission. However, in NB-IoT, since the UE has three coverage levels, a new parameter named PREAMBLE_TRANSMISSIN_COUNTER_CE has been introduced for the preamble repeated transmission counter corresponding to each coverage level. When the maximum number of allowed preamble transmissions is reached for the lower coverage level and RAR is not received or the received RAPID is inconsistent with the sent one, the UE will jump to the next higher coverage level. It will then determine the corresponding counter based on the maximum number of allowed preamble transmissions for the current coverage level. If the current coverage level is the highest, it will remain at the current coverage level and attempt to retransmit the preamble from the PRACH resources. Meanwhile, the parameter PREAMBLE_TRANSMISSION_COUNTER used for counting in LTE will serve as a total counter to determine whether the random access process in NB-IoT has been successful. If it reaches the maximum value, the NB-IoT UE will directly consider the random access unsuccessful.
2.3 Sending Message 3
In NB-IoT, Msg3 is also used for RRC connection establishment requests, but to reduce the signaling overhead between the UE and eNB when switching between idle and connected states, a Suspend-Resume process and a new RRC state[17], namely RRC-SUSPENDED, have been introduced. When the UE is transmitting data in the RRC-SUSPENDED state, it needs to send the Resume ID, which is used to enter the connected state, to the eNB via Msg3 during the random access process. Therefore, Msg3 in NB-IoT needs to have sufficient space to accommodate a 40-bit Resume ID, thus expanding the transmission block size of Msg3 to 88 bits. Additionally, as a control plane optimization scheme has been introduced in NB-IoT for transmitting small amounts of data, after contention resolution in random access, the UE can directly transmit service data in message 5. Therefore, a new data volume and power margin report is introduced, which is reported to the eNB in the form of a MAC control element in Msg3, enabling the eNB to allocate resources reasonably to the UE.
2.4 Contention Resolution
In NB-IoT, contention resolution is also a process aimed at resolving conflicts, and the specific implementation process of both is fundamentally similar. The difference is that after the NB-IoT UE sends Msg3, it needs to start a contention resolution timer, which, like the RAR window, does not adopt subframe as the length unit but uses the PDCCH period as its length unit. At the same time, its value is also adjusted accordingly, with a minimum defined length of 1 PP and a maximum defined length of 64 PPs. If contention resolution is not successful and the PREAMBLE_TRANSMISSION_COUNTER global counter reaches the maximum value, it will be considered that the random access has not been successfully completed in NB-IoT.
3 Testing and Result Analysis of Random Access Process
There are various ways to implement protocol testing, among which the TTCN-3 testing language is widely used for standard validity verification and protocol consistency testing. This paper establishes a consistency testing platform based on TTCN-3 for the random access process of NB-IoT and conducts consistency testing, generating simulation diagrams as shown in Figure 5.
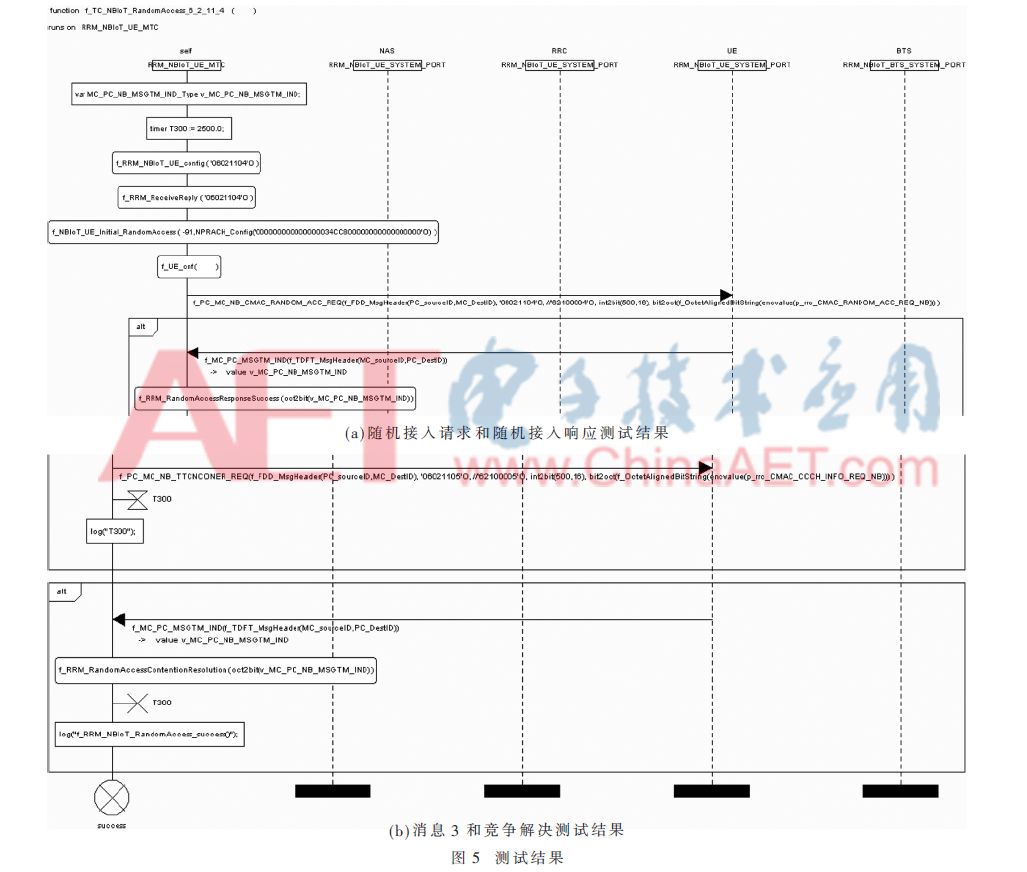
This test follows the consistency testing process of the NB-IoT random access specified in the standards, and finally determines whether the random access process test results are correct through the results output by the control log analysis module of the TTCN-3 platform. First, the communication between the NB-IoT UE and the base station is verified through the results of the functions f_RRM_NBIoT_UE_config(‘06021104’O) and f_RRM_ReceiveReply(‘-06021104’O) in Figure 5(a). After communication is verified, the function f_NBIoT_UE_Initial_RandomAccess() is used to initialize the NB-IoT UE, ensuring it enters state 2A-NB, configures the corresponding coverage level based on RSRP, and configures the NPRACH resources according to the configured coverage level. Then, the four steps of random access are validated. At the same time, it is determined whether the random access response and contention resolution are successful, which are judged by the success and failure outputs in the log of functions f_R-RM_RandomAccessResponseSuccess() in Figure 5(a) and f_RRM_RandomAccessContentionResolution() in Figure 5(b). When the random access response is successfully received, it is known from the log output that the timer T300 has been started, with a value of 2,500 ms; after the NB-IoT UE initiates Msg3, T300 is immediately started, as shown in Figure 5(b). If contention resolution is received without timing out T300, the timer is closed, and the log output f_RRM_NBIoT_RandomAccess_sucess() indicates that the random access process is successfully completed, and the NB-IoT UE enters the connected state. This test result meets the consistency requirements of protocol testing.
This article briefly introduces NB-IoT based on licensed spectrum, considering the importance of random access for UE’s initial access and uplink synchronization, and the corresponding optimizations made in NB-IoT. Currently, in R13, NB-IoT only supports contention-based random access, thus a detailed analysis of the four steps of the optimized contention-based random access process is conducted, and a consistency testing platform based on TTCN-3 is established and tested.
References
[1] RAZA U, KULKARNI P, SOORIYABANDARA M. Low power wide area networks: An overview[J]. IEEE Communications Surveys & Tutorials, 2017, 19(2): 855-873.
[2] ANTEUR M, DESLANDES V, THOMAS N, et al. Ultra narrow band technique for low power wide area communications[C]. GLOBECOM 2015-2015 IEEE Global Communications Conference. IEEE, 2014: 1-6.
[3] RICO-ALVARINO A, VAJAPEYAM M, XU H, et al. An overview of 3GPP enhancements on machine to machine communications[J]. IEEE Communications Magazine, 2016, 54(6): 14-21.
[4] Technical Specification Group GSM/EDGE Radio Access Network; Cellular system support for ultra-low complexity and low throughput Internet of Things (CIoT); Release 13[S]. 3GPP TR 45.820, 2016.
[5] RATASUK R, MANGALVEDHE N, GHOSH A. Overview of LTE enhancements for cellular IoT[C]. IEEE, International Symposium on Personal, Indoor, and Mobile Radio Communications. IEEE, 2015: 2293-2297.
[6] MANGALVEDHE N, RATASUK R, GHOSH A. NB-IoT deployment study for low power wide area cellular IoT[C]. IEEE, International Symposium on Personal, Indoor, and Mobile Radio Communications. IEEE, 2016: 1-6.
[7] GOZALVEZ J. New 3GPP standard for IoT [Mobile Radio][J]. IEEE Vehicular Technology Magazine, 2016, 11(1): 14-20.
[8] OH S M, SHIN J S. An efficient small data transmission scheme in the 3GPP NB-IoT system[J]. IEEE Communications Letters, 2017, 21(3): 660-663.
[9] Technical Specification Group Services and System Aspects; Study on architecture enhancements for Cellular Internet of Things; Release 13[R]. 3GPP TR 23.720, 2016.
[10] WANG Y P E, LIN X, ADHIKARY A, et al. A primer on 3GPP narrowband Internet of Things[J]. IEEE Communications Magazine, 2017, 55(3): 117-123.
[11] RATASUK R, MANGALVEDHE N, ZHANG Y, et al. Overview of narrowband IoT in LTE Rel-13[C]. IEEE Conference on Standards for Communications and Networking. IEEE, 2016: 1-7.
[12] Evolved Universal Terrestrial Radio Access (EUTRA) and Evolved Universal Terrestrial Radio Access Network (EUTRAN); Overall description; Release 13[S]. 3GPP TS 36.300 V13.4.0, 2016.
[13] 戴博,袁弋非,余媛芳. 窄带物联网(NB-IoT)标准与关键技术[M]. 北京:人民邮电出版社,2016.
[14] ERICSSON. Narrowband IoT–Random access design[R]. RAN1 #83, R1-157424, Anaheim, US, 2016.
[15] Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA); Medium Access Control (MAC) protocol specification; Release 13[S]. 3GPP TS 36.321 V13.3.0, 2016.
[16] Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA); Physical channels and modulation; Release 13[S]. 3GPP TS 36.211 V13.3.0, 2016.
文献[17]略
Author Information:
Chen Fatang, Zhou Shuqi, Zheng Hui
Chongqing University of Posts and Telecommunications, Chongqing Key Laboratory of Mobile Communication Technology, Chongqing 400065