Skip to content
 0x01 Basic Knowledge
From wireless headphones to car audio systems, computer keyboards, and mice, almost everyone uses Low Energy Bluetooth (BLE) in their daily lives.
Despite the popularity of this standard, there seems to be a general lack of understanding of how it works and the meanings of certain terms. In this article, I will analyze some basic concepts and key terms.
BLE operates using radio waves within a short range in peripheral configurations, meaning a central device (phone) sends data to a peripheral device (wireless headphones).
For this to happen, the devices need to connect, which is achieved through the device broadcasting on three different channels that the connecting device regularly scans. There are several main types of connections in BLE: connection, pairing, and bonding, each with slightly different meanings:
A connection is an unencrypted one-time connection that provides a simple connection without any security features.
Pairing is a one-time connection where security features, including temporary security keys, are exchanged to ensure data security between two devices. However, this is only a temporary connection, so once Bluetooth is turned off or out of range, the device can freely connect to any other device.
Bonding is a more permanent solution, so once pairing is completed, the devices store the security keys and use them for all future communications, meaning that for every subsequent connection after the initial pairing, keys are not transmitted between devices.
When looking at BLE, several different tools can be used for enumeration, with the most popular tools being:
· Hciconfig – Configures Bluetooth interfaces
· Hcitool – Used for scanning and discovery
· Bleah – Can be used to enumerate Bluetooth devices
· Gatttool – Interacts with Bluetooth devices
· Bettercap – Interacts with Bluetooth devices
· Bluepy – A Python library for direct communication with BLE
To perform Bluetooth attacks, you only need a USB software dongle or a Raspberry Pi with a Bluetooth module.
When enumerating devices, several different headers typically appear:
Handle: A handle is the location in memory where data is stored.
Characteristic: A characteristic is a UUID that references the same location in memory as the handle.
Permissions: This provides information about the permissions for each handle, which are primarily:
Data: This is the data stored at that memory address, which can be a message or a piece of code.
To demonstrate some practical uses of Bluetooth terms, I wrote a BLE CTF challenge that explored some key functionalities of BLE and how to use them.
0x01 Basic Knowledge
From wireless headphones to car audio systems, computer keyboards, and mice, almost everyone uses Low Energy Bluetooth (BLE) in their daily lives.
Despite the popularity of this standard, there seems to be a general lack of understanding of how it works and the meanings of certain terms. In this article, I will analyze some basic concepts and key terms.
BLE operates using radio waves within a short range in peripheral configurations, meaning a central device (phone) sends data to a peripheral device (wireless headphones).
For this to happen, the devices need to connect, which is achieved through the device broadcasting on three different channels that the connecting device regularly scans. There are several main types of connections in BLE: connection, pairing, and bonding, each with slightly different meanings:
A connection is an unencrypted one-time connection that provides a simple connection without any security features.
Pairing is a one-time connection where security features, including temporary security keys, are exchanged to ensure data security between two devices. However, this is only a temporary connection, so once Bluetooth is turned off or out of range, the device can freely connect to any other device.
Bonding is a more permanent solution, so once pairing is completed, the devices store the security keys and use them for all future communications, meaning that for every subsequent connection after the initial pairing, keys are not transmitted between devices.
When looking at BLE, several different tools can be used for enumeration, with the most popular tools being:
· Hciconfig – Configures Bluetooth interfaces
· Hcitool – Used for scanning and discovery
· Bleah – Can be used to enumerate Bluetooth devices
· Gatttool – Interacts with Bluetooth devices
· Bettercap – Interacts with Bluetooth devices
· Bluepy – A Python library for direct communication with BLE
To perform Bluetooth attacks, you only need a USB software dongle or a Raspberry Pi with a Bluetooth module.
When enumerating devices, several different headers typically appear:
Handle: A handle is the location in memory where data is stored.
Characteristic: A characteristic is a UUID that references the same location in memory as the handle.
Permissions: This provides information about the permissions for each handle, which are primarily:
Data: This is the data stored at that memory address, which can be a message or a piece of code.
To demonstrate some practical uses of Bluetooth terms, I wrote a BLE CTF challenge that explored some key functionalities of BLE and how to use them.
 0x02 Practical Problem Solving
Challenge URL: https://github.com/hackgnar/ble_ctf , https://blog.yekki.co.uk/ble-hacking/
https://drive.google.com/open?id=1GsmSUYrEYa-dqCzcnEC4vBBolis90kh-
To reinforce some of the BLE knowledge learned previously, I will analyze it by solving this CTF challenge.
To run this CTF challenge, it needs to be written to an SD card and then inserted into a Raspberry Pi with a Bluetooth module.
The Pi starts running, connects to Raspbian, and then checks if the Bluetooth module is operational.
From here, we have the device’s MAC address:
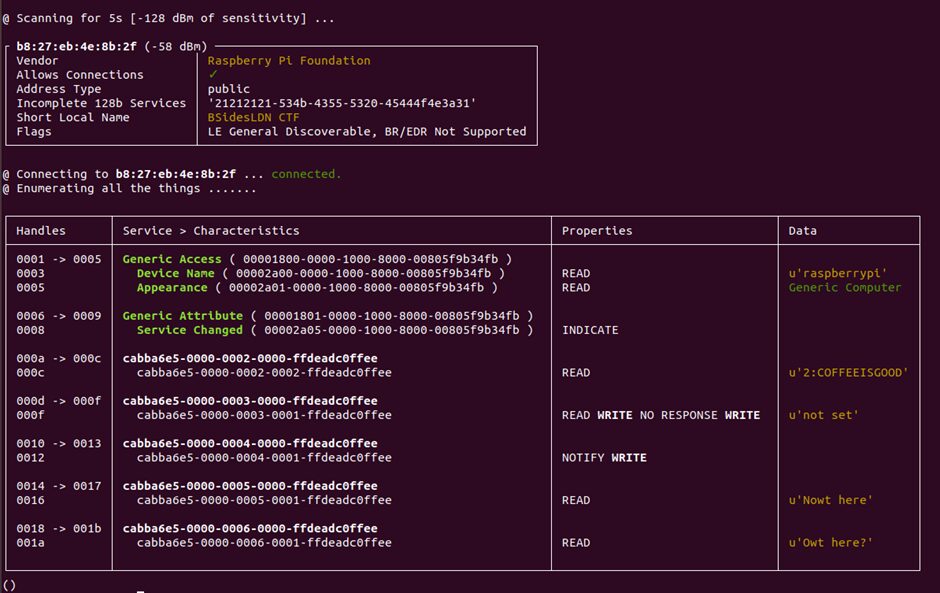
Using Bleah, we can enumerate the device and see its contents.
sudo bleah -b “B8:27:EB:4E:8B:2F” -e
We have some handles with data; my understanding is that these flags are “Digit: Code,” so we already have the second flag
But where is the first flag?
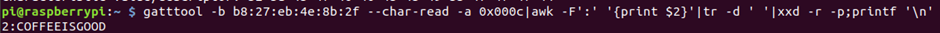
We can check closely by reading handle 0x000c
Handle values increase by 1, and when they are in hexadecimal, their value rises to 8, then to f, so it seems there are no gaps on the handle that hides flag 1.
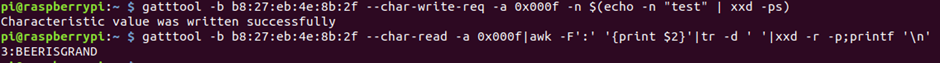
Since it has write attributes, let’s write some data into it and see if we can read it back.
gatttool -b b8:27:eb:4e:8b:2f –char-write-req -a 0x000f -n $(echo -n “test” | xxd -ps)
Write successful, so if we write back, we will get the flag!
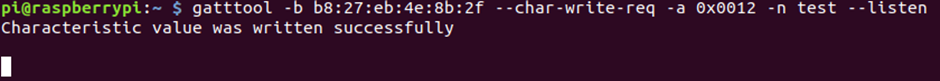
If we use –listenflag to write some data, we should read some data!
However, that is not the case!
No response, trying to change the input type:
gatttool -b b8:27:eb:4e:8b:2f –char-write-req -a 0x0012 -n $(echo -n “test” | xxd -ps) –listen
Read more about BLE notifications; there is a CCCD, which stands for Client Characteristic Configuration Descriptor. To receive notifications, we need to set this CCCD to receive notifications, for which we need to write the correct code 0100 to the CCCD handle, which in this case is 0x0013.
For this, I entered interactive gatttools:
Then connect to the device:
connect b8:27:eb:4e:8b:2f
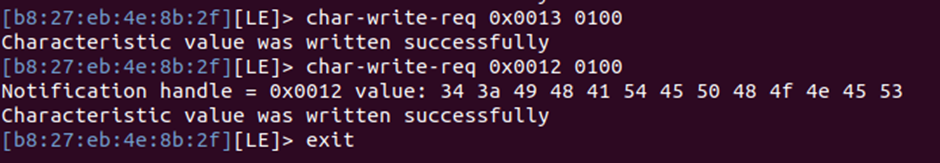
Once connected successfully, I wrote the code 0100 to the CCCD.
char-write-req 0x0013 0100
In interactive mode, it only has “operation,” “handler,” “data,” and then when writing to 0x0012, we get a response!
Using CyberChef to decode this, we get the fourth flag!
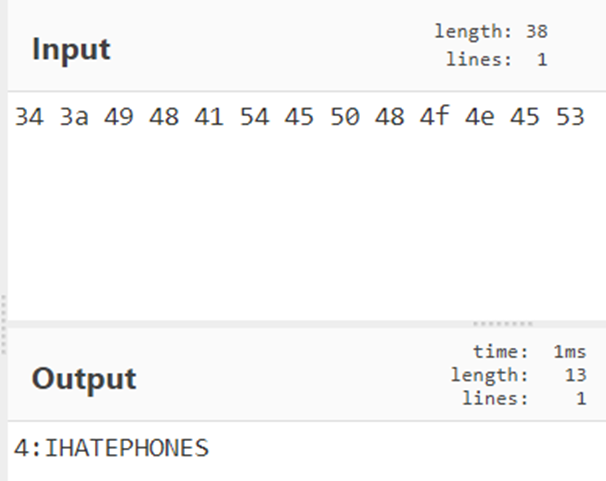
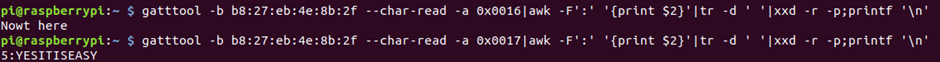
Looking at flag 5, it only has read permissions; reading 0x0016 will read known handles up to 0x0017.
gatttool -b b8:27:eb:4e:8b:2f –char-read -a 0x0017 | awk -F’:’ ‘{print $2}’| tr -d ‘ ‘| xxd -r -p; printf’\n’
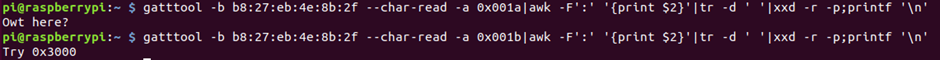
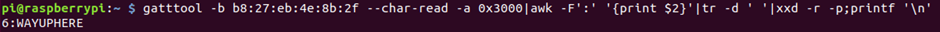
Flag 6 also only has read permissions; here we got a read response for Owt, and we have a new clue!
gatttool -b b8:27:eb:4e:8b:2f –char-read -a 0x3000 | awk -F’:’ ‘{print $2}’| tr -d ‘ ‘| xxd -r -p; printf’\n’
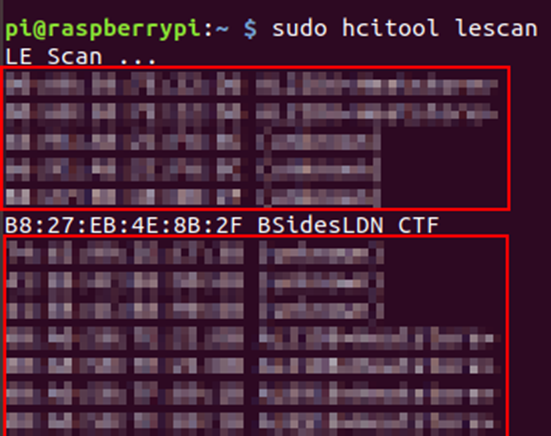
Therefore, we now need to find flag 1. Since there are no obvious gaps on the device in the handler, it cannot be stored there. Considering how Bluetooth works, before establishing a connection, the device must broadcast itself, which is what we saw at the beginning on lescan. However, is there any other data besides the device’s MAC address and name?
Just like scanning network traffic, traffic can be intercepted during scanning, so we can use Wireshark or tcpdump in this case.
Running tcpdump on the Bluetooth interface:
sudo tcpdump -i bluetooth1 -s 0
Then we run another lescan and observe the data!
0x02 Practical Problem Solving
Challenge URL: https://github.com/hackgnar/ble_ctf , https://blog.yekki.co.uk/ble-hacking/
https://drive.google.com/open?id=1GsmSUYrEYa-dqCzcnEC4vBBolis90kh-
To reinforce some of the BLE knowledge learned previously, I will analyze it by solving this CTF challenge.
To run this CTF challenge, it needs to be written to an SD card and then inserted into a Raspberry Pi with a Bluetooth module.
The Pi starts running, connects to Raspbian, and then checks if the Bluetooth module is operational.
From here, we have the device’s MAC address:
Using Bleah, we can enumerate the device and see its contents.
sudo bleah -b “B8:27:EB:4E:8B:2F” -e
We have some handles with data; my understanding is that these flags are “Digit: Code,” so we already have the second flag
But where is the first flag?
We can check closely by reading handle 0x000c
Handle values increase by 1, and when they are in hexadecimal, their value rises to 8, then to f, so it seems there are no gaps on the handle that hides flag 1.
Since it has write attributes, let’s write some data into it and see if we can read it back.
gatttool -b b8:27:eb:4e:8b:2f –char-write-req -a 0x000f -n $(echo -n “test” | xxd -ps)
Write successful, so if we write back, we will get the flag!
If we use –listenflag to write some data, we should read some data!
However, that is not the case!
No response, trying to change the input type:
gatttool -b b8:27:eb:4e:8b:2f –char-write-req -a 0x0012 -n $(echo -n “test” | xxd -ps) –listen
Read more about BLE notifications; there is a CCCD, which stands for Client Characteristic Configuration Descriptor. To receive notifications, we need to set this CCCD to receive notifications, for which we need to write the correct code 0100 to the CCCD handle, which in this case is 0x0013.
For this, I entered interactive gatttools:
Then connect to the device:
connect b8:27:eb:4e:8b:2f
Once connected successfully, I wrote the code 0100 to the CCCD.
char-write-req 0x0013 0100
In interactive mode, it only has “operation,” “handler,” “data,” and then when writing to 0x0012, we get a response!
Using CyberChef to decode this, we get the fourth flag!
Looking at flag 5, it only has read permissions; reading 0x0016 will read known handles up to 0x0017.
gatttool -b b8:27:eb:4e:8b:2f –char-read -a 0x0017 | awk -F’:’ ‘{print $2}’| tr -d ‘ ‘| xxd -r -p; printf’\n’
Flag 6 also only has read permissions; here we got a read response for Owt, and we have a new clue!
gatttool -b b8:27:eb:4e:8b:2f –char-read -a 0x3000 | awk -F’:’ ‘{print $2}’| tr -d ‘ ‘| xxd -r -p; printf’\n’
Therefore, we now need to find flag 1. Since there are no obvious gaps on the device in the handler, it cannot be stored there. Considering how Bluetooth works, before establishing a connection, the device must broadcast itself, which is what we saw at the beginning on lescan. However, is there any other data besides the device’s MAC address and name?
Just like scanning network traffic, traffic can be intercepted during scanning, so we can use Wireshark or tcpdump in this case.
Running tcpdump on the Bluetooth interface:
sudo tcpdump -i bluetooth1 -s 0
Then we run another lescan and observe the data!
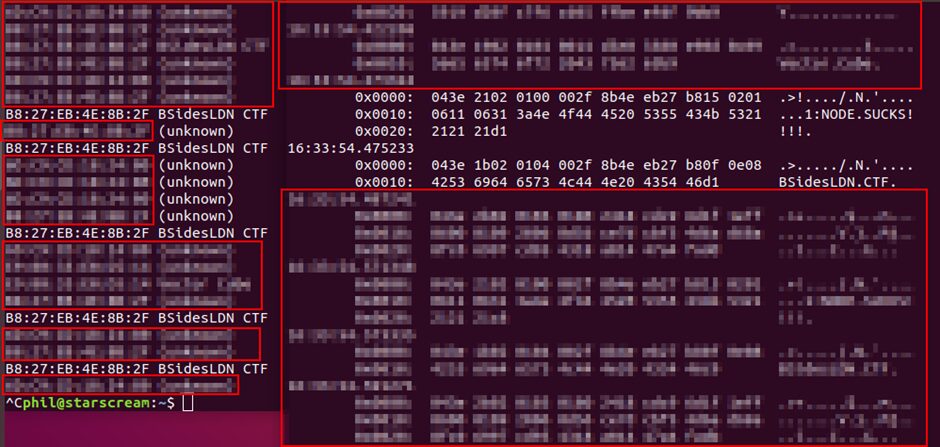 Thus, we have the first and last flag; solving such CTF challenges helps reinforce knowledge and further understand how BLE works!
Original text and link: https://www.4hou.com/posts/7Wgy
Thus, we have the first and last flag; solving such CTF challenges helps reinforce knowledge and further understand how BLE works!
Original text and link: https://www.4hou.com/posts/7Wgy

 0x01 Basic Knowledge
0x01 Basic Knowledge 0x02 Practical Problem Solving
0x02 Practical Problem Solving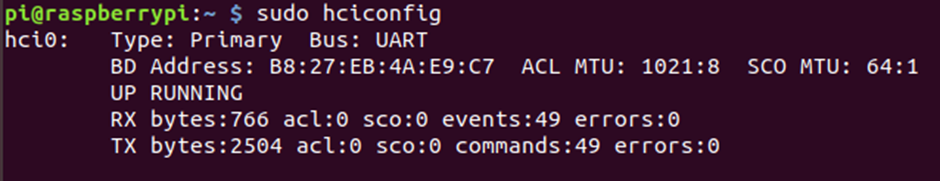
 Thus, we have the first and last flag; solving such CTF challenges helps reinforce knowledge and further understand how BLE works!
Thus, we have the first and last flag; solving such CTF challenges helps reinforce knowledge and further understand how BLE works!

 0x01 Basic Knowledge
0x01 Basic Knowledge 0x02 Practical Problem Solving
0x02 Practical Problem Solving










 Thus, we have the first and last flag; solving such CTF challenges helps reinforce knowledge and further understand how BLE works!
Thus, we have the first and last flag; solving such CTF challenges helps reinforce knowledge and further understand how BLE works!
