链接:https://blog.csdn.net/2401_84578953/article/details/144244011?
☞The course by Liang Xu has completely exploded!☜
Everyone thinks that Linux is secure by default, and I generally agree (this is a controversial topic). Linux does indeed have a built-in security model. You need to enable it and customize it to achieve a more secure system. Linux is harder to manage, but correspondingly more flexible, with more configuration options.
For system administrators, making the system more secure against hackers and attacks has always been a challenge. This is our first article on topics like “how to make the Linux system more secure” or “hardening the Linux system.” This article will introduce 25 useful tips and tricks to help you enhance the security of your Linux system. We hope the following tips and tricks can assist you in strengthening your system’s security.
1. Physical Security of the System
Configure the BIOS to disable booting from CD/DVD, external devices, and floppy drives. Next, enable the BIOS password and also enable GRUB password protection to restrict physical access to the system.
2. Disk Partitioning
Using different partitions is important for potential disasters, as it ensures higher data security. By partitioning, data can be grouped and isolated. When an incident occurs, only the data in the problematic partition will be affected, while data in other partitions can be preserved. It is best to have the following partitions, and third-party programs should ideally be installed in a separate filesystem under /opt.

3. Minimal Package Installation, Minimal Vulnerabilities
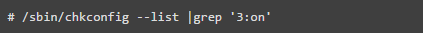
Do you really need to install all services? It is recommended not to install unnecessary packages to avoid vulnerabilities introduced by these packages. This minimizes risk, as a vulnerability in one service could compromise others. Identify and remove or stop unnecessary services to reduce system vulnerabilities. Use the ‘chkconfig’ command to list all services running at runlevel 3.
When you find an unnecessary service running, use the command below to stop it.

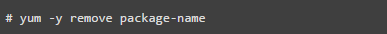
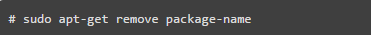
Use the RPM package manager, such as YUM or apt-get tools, to list all installed packages and use the command below to uninstall them.
4. Check Network Listening Ports
With the network command ‘netstat’, you will be able to see all open ports and the associated programs. Use the ‘chkconfig’ command mentioned above to disable unwanted network services in the system.

5. Use SSH (Secure Shell)
Telnet and rlogin protocols can only be used in plain text and do not use encrypted formats, which may lead to security vulnerabilities. SSH is a secure protocol that uses encryption for communication between the client and server.
Unless necessary, never log in directly as the root user. Use “sudo” to execute commands. Sudo is defined by the /etc/sudoers file, and you can also use the “visudo” tool to edit it, which will open the configuration file in the VI editor.
Additionally, it is recommended to change the default SSH port number 22 to another higher port number. Open the main SSH configuration file and make the following modifications to restrict user access.
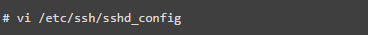
Disable root user login

Specific user access

Use SSH protocol version 2

6. Ensure the System is Up-to-Date
Always ensure that the system includes the latest patches, security fixes, and available kernels.

7. Lock Down Cron Jobs
Cron has its own built-in features that allow defining who can and cannot run tasks. This is controlled by two files: /etc/cron.allow and /etc/cron.deny. To lock down users using Cron, simply write their names into cron.deny, while to allow users to run cron, add their names to cron.allow. If you want to prohibit all users from using cron, you can add “ALL” as a line in cron.deny.

8. Disable USB Detection
In many cases, we want to restrict users from using USB to ensure system security and prevent data leakage. Create a file ‘/etc/modprobe.d/no-usb’ and use the command below to disable USB storage detection.

9. Enable SELinux
SELinux (Security-Enhanced Linux) is a mandatory access control security mechanism provided by the Linux kernel. Disabling SELinux means the system loses its security mechanism. Consider carefully before removing SELinux; if your system needs to be exposed to the network and accessed publicly, you need to pay more attention.
SELinux provides three basic operational modes:
-
Enforcing: This is the default mode, used to enable and enforce SELinux security policies.
-
Permissive: In this mode, SELinux does not enforce security policies, only warnings and logging. This mode is very useful for troubleshooting SELinux-related issues.
-
Disabled: SELinux is turned off.
You can use the command line ‘system-config-selinux’, ‘getenforce’, or ‘sestatus’ to browse the current SELinux status.

If it is in disabled mode, use the command below to enable SELinux
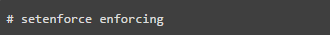
You can also toggle SELinux on or off through the configuration file ‘/etc/selinux/config’.
10. Remove KDE or GNOME Desktop
There is no need to run X Window desktops like KDE and GNOME on dedicated LAMP servers. You can remove or disable them to improve system security and performance. Open /etc/inittab and change the run level to 3 to disable these desktops. If you want to completely remove them from the system, you can use the command below:
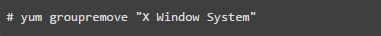
11. Disable IPv6
If you are not using the IPv6 protocol, it should be disabled, as most applications and policies will not utilize IPv6, and it is not essential for servers. You can add the following lines to the network configuration file to disable it.
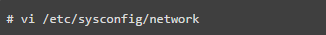

12. Restrict Users from Using Old Passwords
If you do not want users to continue using old passwords, this tip is very useful. The old password file is located at /etc/security/opasswd. You can implement this using the PAM module.
Open the ‘/etc/pam.d/system-auth’ file in RHEL / CentOS / Fedora.
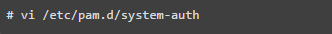
Open the ‘/etc/pam.d/common-password’ file in Ubuntu/Debian/Linux Mint.
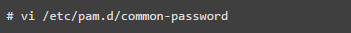
Add the following line in the ‘auth’ block.
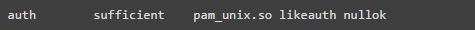
Add the following line in the ‘password’ block to prevent users from reusing their last 5 passwords.
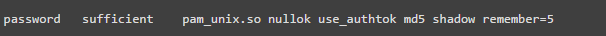
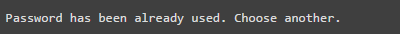
The server only records the last 5 passwords. If you try to use any of the last 5 old passwords, you will see an error message like the one below.
13. How to Check User Password Expiration?
In Linux, user passwords are stored in encrypted form in the ‘/etc/shadow’ file. To check if a user’s password has expired, you need to use the ‘chage’ command. It will display the last modification date of the password and details about the password expiration. This information is what the system uses to determine if a user must change their password.
To view the aging information of any existing user, such as expiration date and duration, use the command below.

To modify the aging of any user, use the command below.
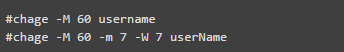
Parameters
-
-M sets the maximum number of days
-
-m sets the minimum number of days
-
-W sets the desired number of days
14. Manually Lock or Unlock User Accounts
The lock and unlock feature is very useful; you can lock an account for a week or a month instead of removing it from the system. You can lock a specific user with the command below.
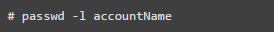
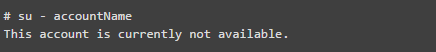
Note: The locked user is only visible to the root user. This lock is achieved by replacing the encrypted password with (!). If someone tries to use this account to log in, they will receive an error message similar to the one below.
To unlock a locked account, use the command below. This command will revert the password that was replaced with (!) back to its original state.
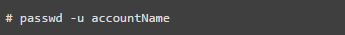
15. Strengthen Passwords
A significant number of users use weak passwords that can be cracked through dictionary or brute-force attacks. The ‘pam_cracklib’ module exists in PAM, which can enforce users to set complex passwords. Open the file below in an editor.

Add a line in the file using authentication parameters (lcredit, ucredit, dcredit, or ocredit corresponding to lowercase letters, uppercase letters, numbers, and other characters)
16. Enable Iptables (Firewall)
It is highly recommended to enable the Linux firewall to prevent unauthorized access. Use iptables rules to filter inbound, outbound, and forwarded packets. We can allow or deny access to specific UDP/TCP ports based on source and destination addresses.
17. Disable Ctrl+Alt+Delete Restart
In most Linux distributions, pressing ‘CTRL-ALT-DELETE’ will restart your system. This is not a good practice on production servers, as it may lead to accidental operations.
This configuration is in the ‘/etc/inittab’ file. If you open this file, you can see a similar paragraph. The default line has been commented out. We must comment it out. This specific key combination will cause the system to restart.
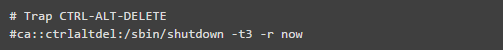
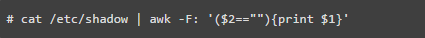
18. Check for Empty Password Accounts
Any account with an empty password means that any unauthorized user on the web can access it, which is a security threat for Linux servers. Therefore, ensure that all users have a complex password and that there are no privileged users. Empty password accounts are a security risk and can be easily compromised. You can use the command below to check for any empty password accounts.
19. Display SSH Warning Before Login
Using a legal and security warning during SSH authentication is a good practice.
20. Monitor User Behavior
If you have many users, it is essential to collect information about each user’s behavior and their process consumption. This can later assist in user analysis during performance optimization and security issue resolution. But how to monitor and collect user behavior information?
Two very useful tools, ‘psacct’ and ‘acct’, can be used to monitor user behavior and process consumption in the system. These tools run in the background and continuously log the behavior of each user and the resource consumption of various services like Apache, MySQL, SSH, FTP, etc.
21. Regularly Check Logs
Move logs to a dedicated log server to prevent intruders from easily altering local logs. Below are common default log files in Linux and their purposes:
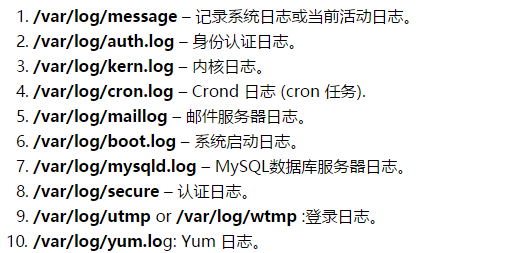
22. Important File Backup
In a production environment, it is necessary to back up important files and store them in a secure remote tape vault, remote site, or offsite hard drive for disaster recovery.
23. NIC Bonding
There are two types of NIC bonding modes that need to be used in bonding interfaces.
mode=0 – Round-robin mode
mode=1 – Active-backup mode
NIC bonding can help us avoid single points of failure. In NIC bonding, we bind two or more network cards together to provide a virtual interface, which sets the IP address and communicates with other servers. This way, if one NIC card goes down or is unavailable for other reasons, our network will remain available.
24. Keep /boot Read-Only
The Linux kernel and its related files are stored under /boot, which is writable by default. Setting it to read-only can reduce the risk of unauthorized modifications to important boot files.

Add the following line at the end of the file and save it
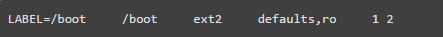
If you need to upgrade the kernel in the future, you will need to revert to read-write mode.
25. Ignore ICMP and Broadcast Requests
Add the following lines in /etc/sysctl.conf to block ping and broadcast requests.
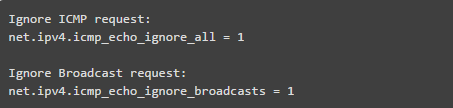
Run the line below to load the modifications or updates

The spring recruitment has begun! If everyone does not prepare adequately, it will be difficult to find a good job during the spring recruitment.
Here’s a job package for everyone, so you can prepare for the spring recruitment and find a good job!