Latest Linux News – June 8, 2025
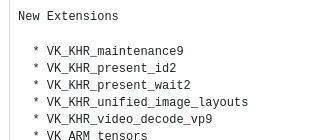
📚 Open Source Technology DailyExploring the Infinite Possibilities of Open Source2025/6/8⚡Linux 6.16 Introduces New Helper Function to Restrict Symbols to Specific Kernel ModulesLinux 6.16 merge window is about to close, and all updates to the kernel build system “Kbuild” have been merged today, with the release of Linux 6.16-rc1 expected tomorrow. The most notable feature … Read more