Sharing Ideas on Strong Network Cup S8 Rust Pwn Chat-With-Me Problem
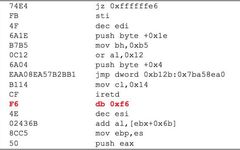
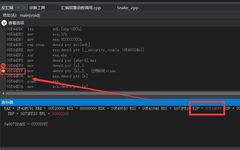
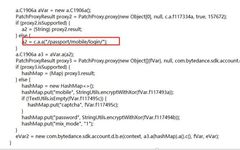
1 Problem-Solving Ideas The final number of solutions for this problem is 42, as the difficulty level is not high and generally meets expectations. The problem is coded in Rust, and it was decided to remove symbols without providing the source code the night before the competition. This not only made it very difficult for … Read more