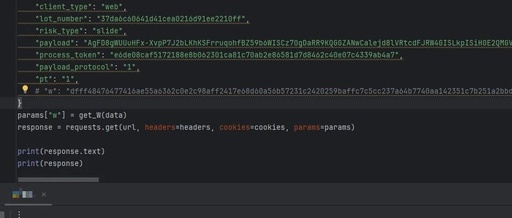
Embedded Development: How to Prevent Device Cloning?
Table of Contents: Introduction I. Conventional Devices 1. Patent Protection 2. Code Encryption 3. Authorization Verification 4. Continuous Updates and Improvements II. Embedded Devices 1. Polishing Key Chip Logos 2. Disabling Debug Serial Ports 3. Flash Read Protection Settings 4. Encrypting and Obfuscating Key Information III. Cracking the Junzheng T Series Program 1. Locating the … Read more