Understanding HTTPS: A Comprehensive Guide
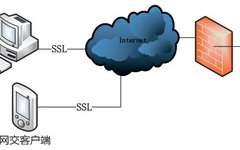
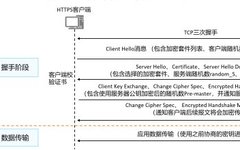
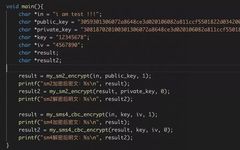
Before discussing HTTPS, let’s first talk about what HTTP is. HTTP is a protocol that we use when browsing the web. The data transmitted using the HTTP protocol is unencrypted, meaning it is in plain text, making it very insecure to transmit private information using HTTP. To ensure that this private data can be transmitted … Read more