This article is an excellent piece from the KX Forum
Author ID on KX Forum: xiaoduoduo
---------------MQTT PUBLISH- ------40bytes-------------------------------------------
| 30 26 00 14 68 6f 6d 65 2f 67 61 72 64 65 6e 2f |0&..home/garden/|
| 66 6f 75 6e 74 61 69 6e 31 32 33 34 35 36 37 38 |fountain12345678|
| 39 30 61 62 63 64 65 66 |90abcdef
static void process_mqtt_msg(mqtt_waf_msg *req)
{
......
/* decode mqtt variable length */
len = len_len = 0;
p = req->buf + 1;
eop = &req->buf[req->pos];
while (p < eop) {
lc = *((const unsigned char *) p++);
len += (lc & 0x7f) << 7 * len_len;
len_len++;
if (!(lc & 0x80)) break;
if (len_len > 4){
req->msg_state = MQTT_MSG_ERROR;
return;
}
}
.....
}
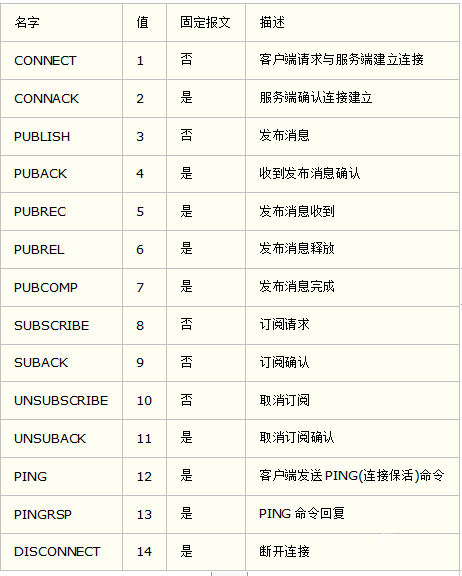
......switch (mqtt_msg_type)
{
case MQTT_CONNECT:
req->msg_state = mqtt_connect(req,p,end,&mm);
break;
case MQTT_CONNACK:
break;
case MQTT_PUBLISH:
req->msg_state = mqtt_publish(req,p,end,&mm);
break;
case MQTT_SUBSCRIBE:
req->msg_state = mqtt_subscribe(req,p,end,&mm);
break;
case MQTT_UNSUBSCRIBE:
req->msg_state = mqtt_unsubscribe(req,p,end,&mm);
......
>>>>
1. CONNECT to the Server
1. CONNECT to the Server
--------------MQTT CONNECT-----105bytes-----------------------------
| 10 67 00 04 4d 51 54 54 04 c2 00 3c 00 19 4d 51 |.g..MQTT...<..MQ|
| 54 54 5f 46 58 5f 43 6c 69 65 6e 74 5f 39 69 75 |TT_FX_Client_9iu|
| 79 38 37 36 35 35 35 00 12 69 6f 74 66 72 65 65 |y876555..iotfree|
| 74 65 73 74 2f 74 68 69 6e 67 30 00 2c 59 55 37 |test/thing0.,YU7|
| 54 6f 76 38 7a 46 57 2b 57 75 61 4c 78 39 73 39 |Tov8zFW+WuaLx9s9|
| 49 33 4d 4b 79 63 6c 69 65 39 53 47 44 75 75 4e |I3MKyclie9SGDuuN|
| 6b 6c 36 6f 39 4c 58 6f 3d |kl6o9LXo=
10 //CONNECT指令号
67 //长度103字节
00 04 //MQTT协议长度为4字节
4d 51 54 54 //MQTT固定字符串
04 //版本3.1.1
c2 //连接标记,是否由用户名/密码等
00 3c //心跳间隔时间60秒
00 19 //用户名长度25字节,后面是用户名
4d 51 54 54 5f 46 58 5f 43 6c 69 65 6e 74 5f 39 69 75 79 38 37 36 35 35 35
00 12 //密码18字节
69 6f 74 66 72 65 65 74 65 73 74 2f 74 68 69 6e 67 30//密码
00 2c //will message长度。
59 55 37 ......6f 3d//will message内容
>>>>
2. PUBLISH Message
2. PUBLISH Message
/*
---------------MQTT PUBLISH-------40bytes-----------------------------
| 30 26 00 14 68 6f 6d 65 2f 67 61 72 64 65 6e 2f |0&..home/garden/|
| 66 6f 75 6e 74 61 69 6e 31 32 33 34 35 36 37 38 |fountain12345678|
| 39 30 61 62 63 64 65 66 |90abcdef
*/
30 //PUBLISH指令号
26 //长度39字节
00 14 //TOPIC长度20字节
68 6f 6d 65 2f 67 61 72 64 65 6e 2f 66 6f 75 6e //TOPIC
31 32 33 34 35 36 37 38 39 30 61 62 63 64 65 66 //发布的消息
>>>>
3. SUBSCRIBE to Messages
3. SUBSCRIBE to Messages
---------------MQTT SUBSCRIBE------33bytes-----------------------------
| 82 1f 00 01 00 1a 68 6f 6d 65 2f 67 61 72 64 65 |......home/garde|
| 6e 2f 66 6f 75 6e 74 61 69 6e 64 65 6c 65 74 65 |n/fountaindelete|
| 00
82 //SUBSCRIBE指令
1f //长度31字节
00 01 //Message Identifier
00 1a //TOPIC长度26
68 6f 6d 65 2f 67 61 72 64 65 6e 2f 66 6f 75 6e 74 61 69 6e 64 65 6c 65 74 65 //TOPIC
00 //request QOS
>>>>
4. UNSUBSCRIBE Message
4. UNSUBSCRIBE Message
---------------MQTT UNSUBSCRIBE-------32bytes-----------------------------
| a2 1e 00 02 00 1a 68 6f 6d 65 2f 67 61 72 64 65 |......home/garde|
| 6e 2f 66 6f 75 6e 74 61 69 6e 64 65 6c 65 74 65 |n/fountaindelete|
a2 //SUBSCRIBE指令
1e //长度30字节
00 02 //Message Identifier
00 1a //TOPIC长度26
68 6f 6d 65 2f 67 61 72 64 65 6e 2f 66 6f 75 6e 74 61 69 6e 64 65 6c 65 74 65 //TOPIC


KX ID:xiaoduoduo
https://bbs.pediy.com/user-10578.htm
Recommended Articles++++
* Android App Multi-Opening Practice
* Linux Pwn from Beginner to Proficient (III)
* Discussing Bypass disable_function
* Memory Dump to Obtain Unity3D Game Related Code
* Android Reverse Engineering Introduction Practice – Skiing Adventure Payment Analysis