Safety Assessment of Autonomous Driving Functions: Fault Injection Simulation Testing
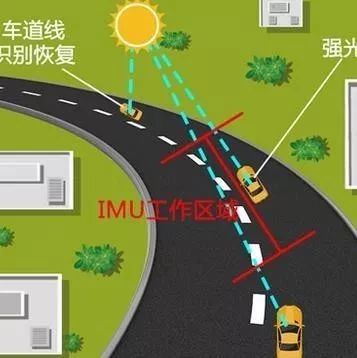
How to Know, How Can One Not Know Article from: Ranyun Automobile (ID: BC-Auto2018) As we entered 2018, the autonomous driving industry began to focus on commercialization issues. The application of any new technology, including autonomous driving, must meet two conditions: (1) a business model that creates value; (2) sufficient technological maturity. Regarding the first … Read more